Overview
Provides instructions for configuring a Threat Defense (FTD) device as a branch site spoke in a route-based site-to-site VPN using Firewall Management Center (FMC).
Procedure
| 1. | In the Spoke Nodes section, click +. The Add Endpoint dialog box is displayed. |
|
| 2. | Choose NGFWBR1 as the hub from the Device drop-down list.
|
|
| 3. | Click + next to the Static Virtual Tunnel Interface drop-down list to add a new static VTI. The Add Virtual Tunnel Interface dialog box appears with the following pre-populated default configurations.
Click OK to save the SVTI. A message is displayed that confirms the VTI is created successfully. Click OK. The Static Virtual Tunnel Interface is set to outside_static_vti_1(169.254.20.1). |
|
| 4. | Expand Advanced Settings to view the default settings. Both checkboxes must be checked. |
|
| 5. | Click OK. NGFWBR1 is successfully configured as the spoke node. 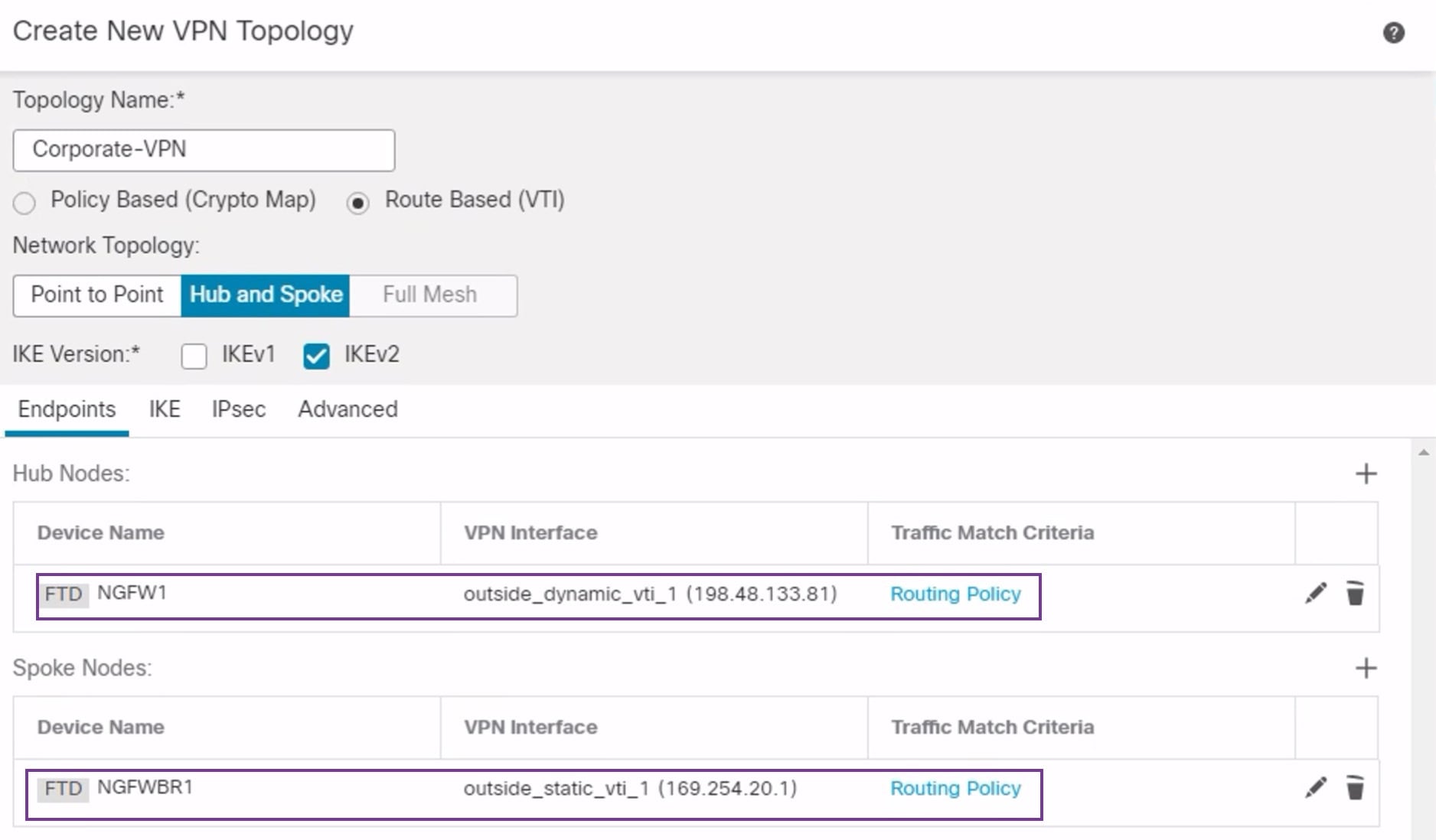
|