Requirements and prerequisites for advanced settings
Model support
Any
Supported domains
Any
User roles
-
Admin
-
Access Admin
-
Network Admin
-
You can define custom user roles to differentiate between the intrusion configuration in access control policy and rules and the rest of the access control policy and rules. Using these permissions, you can separate the responsibilities of your network administration team and your intrusion administration teams. The existing pre-defined user roles that included the Modify Access Control Policy permission support all sub-permissions; you need to create your own custom roles if you want to apply granular permissions. The granular permissions are:
-
and choose the allows the selection of intrusion policy, variable set, and file policy in a rule, the configuration of the advanced options for network analysis and intrusion policies, the configuration of the Security Intelligence policy for the access control policy, and intrusion actions in the policy default action. If a user has this option only, the user can modify no other part of the policy or rule.
-
Modify Remaining Access Control Policy Configuration controls the ability to edit all other aspects of the policy.
-


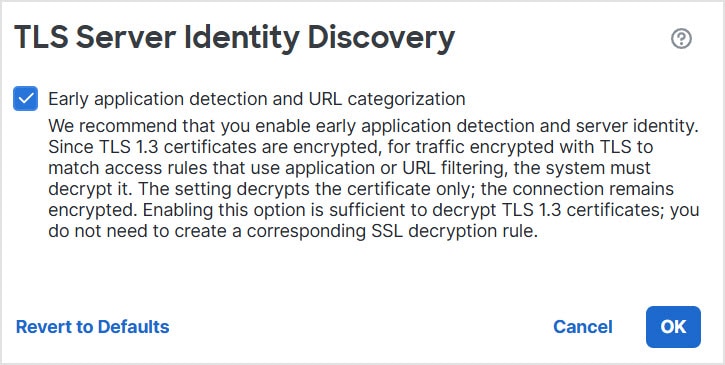
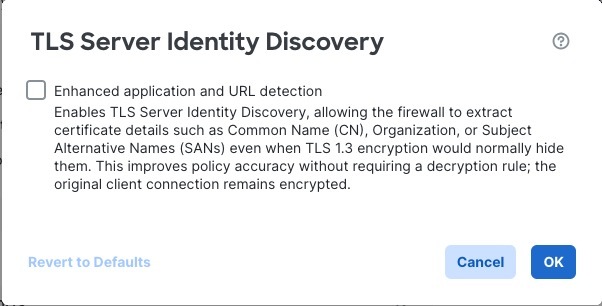

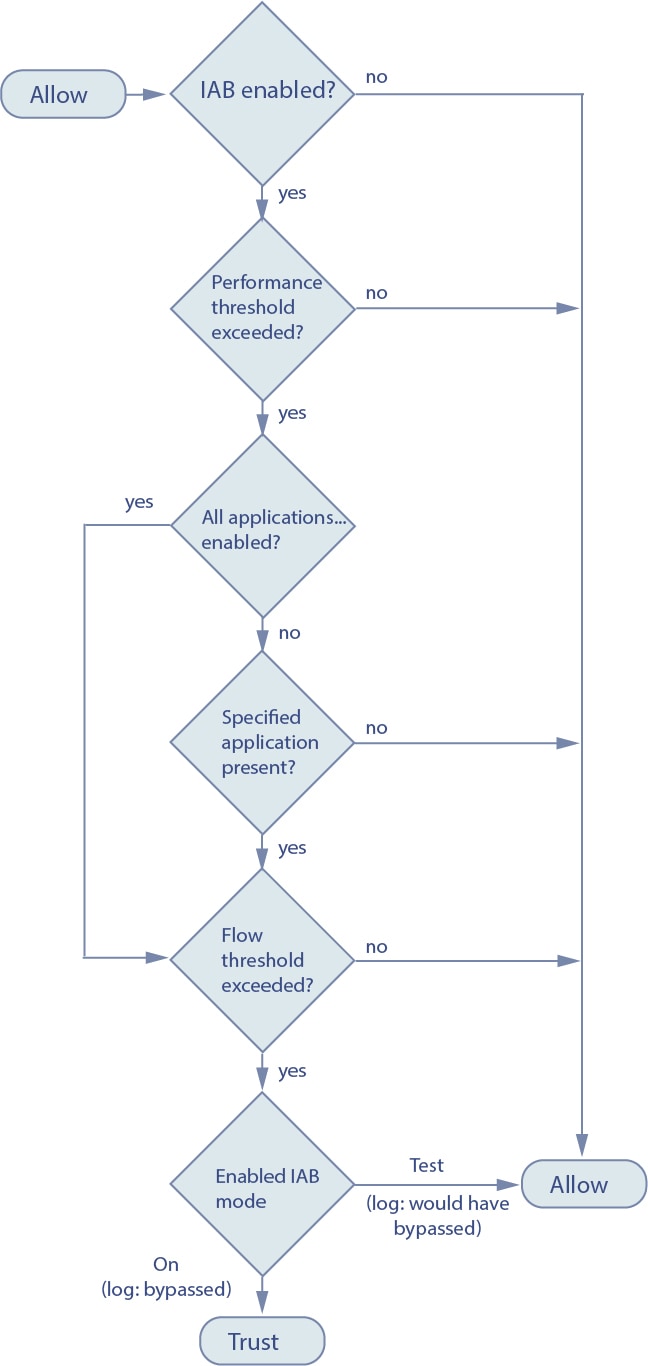
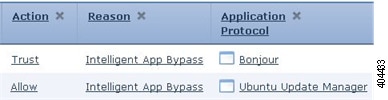
 Feedback
Feedback