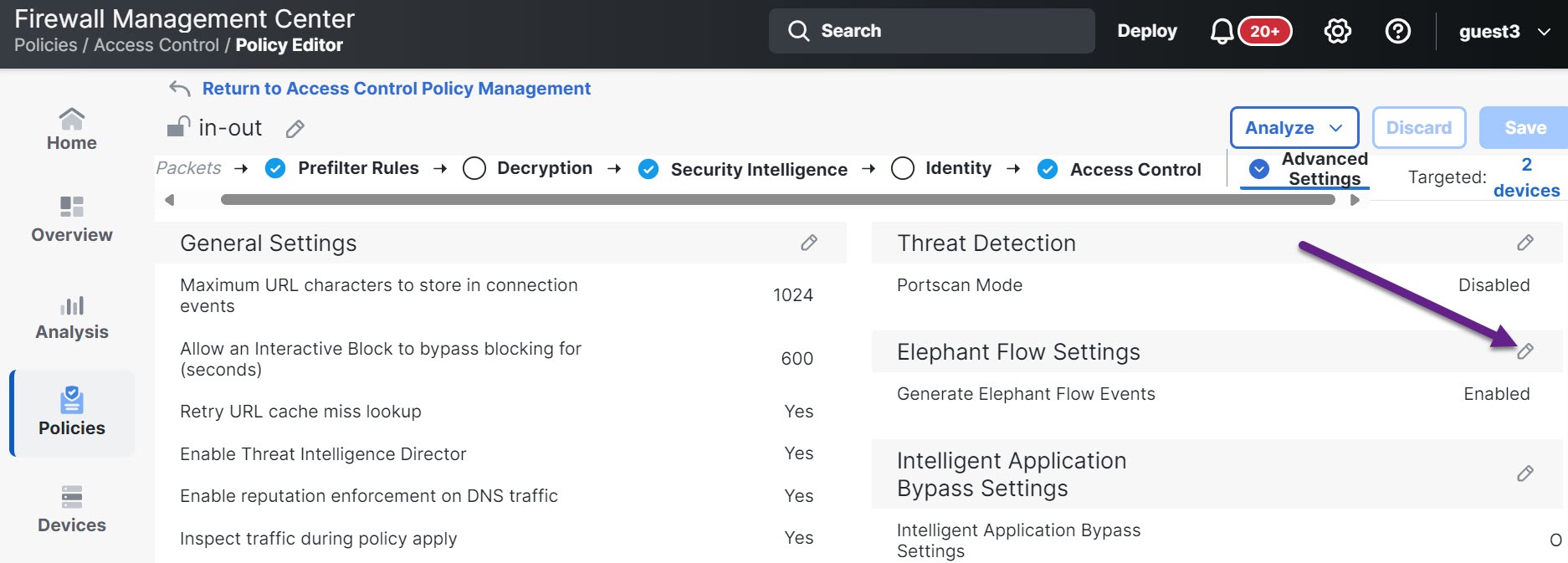
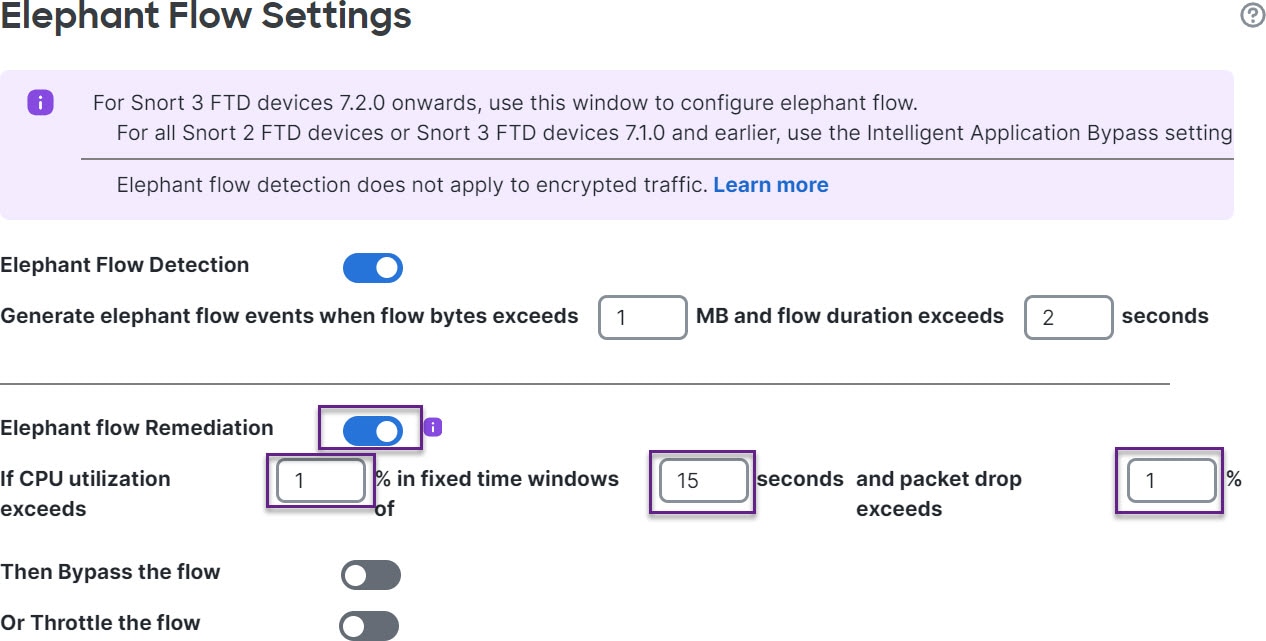
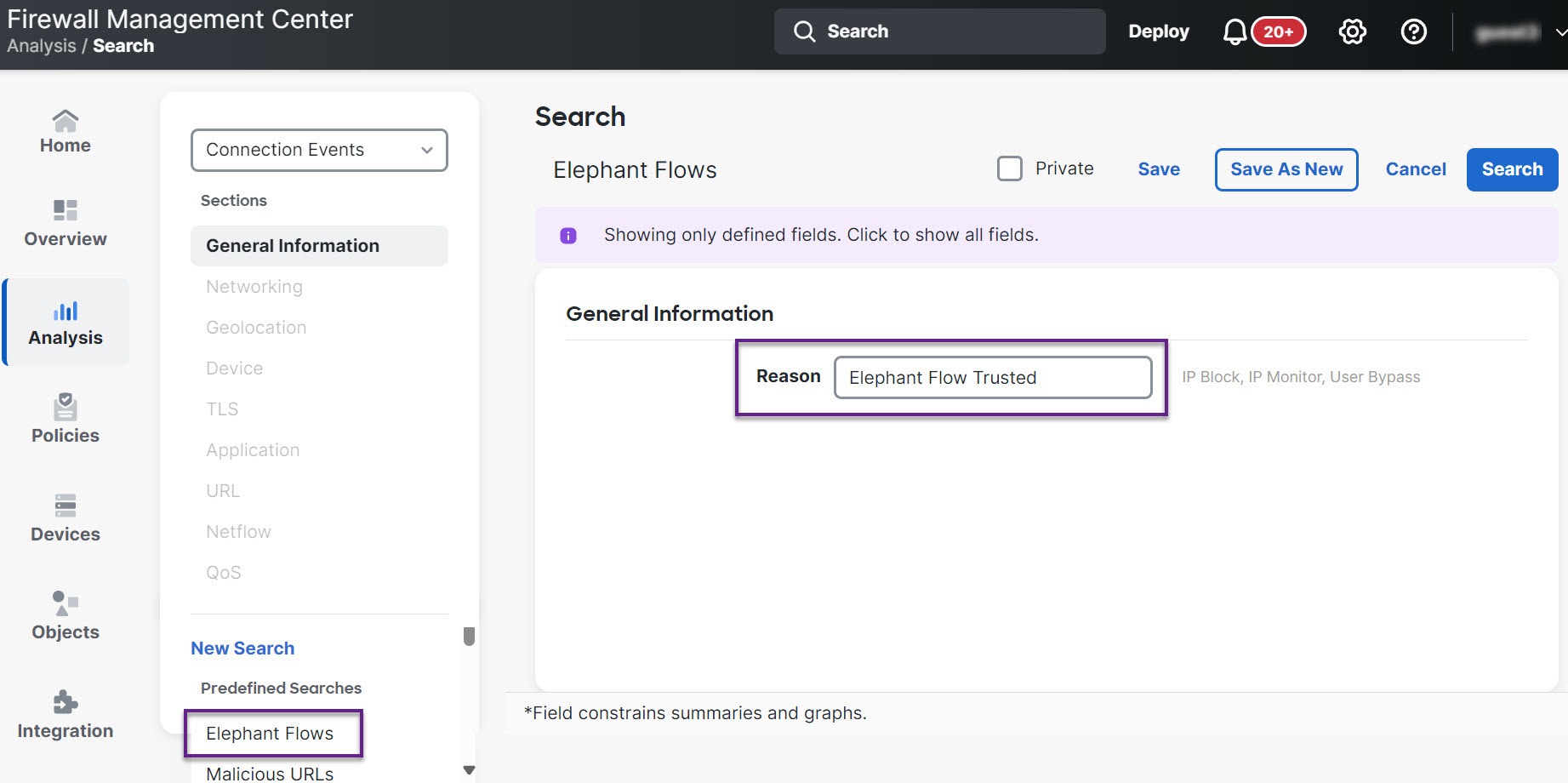
About Elephant Flow Detection and Remediation
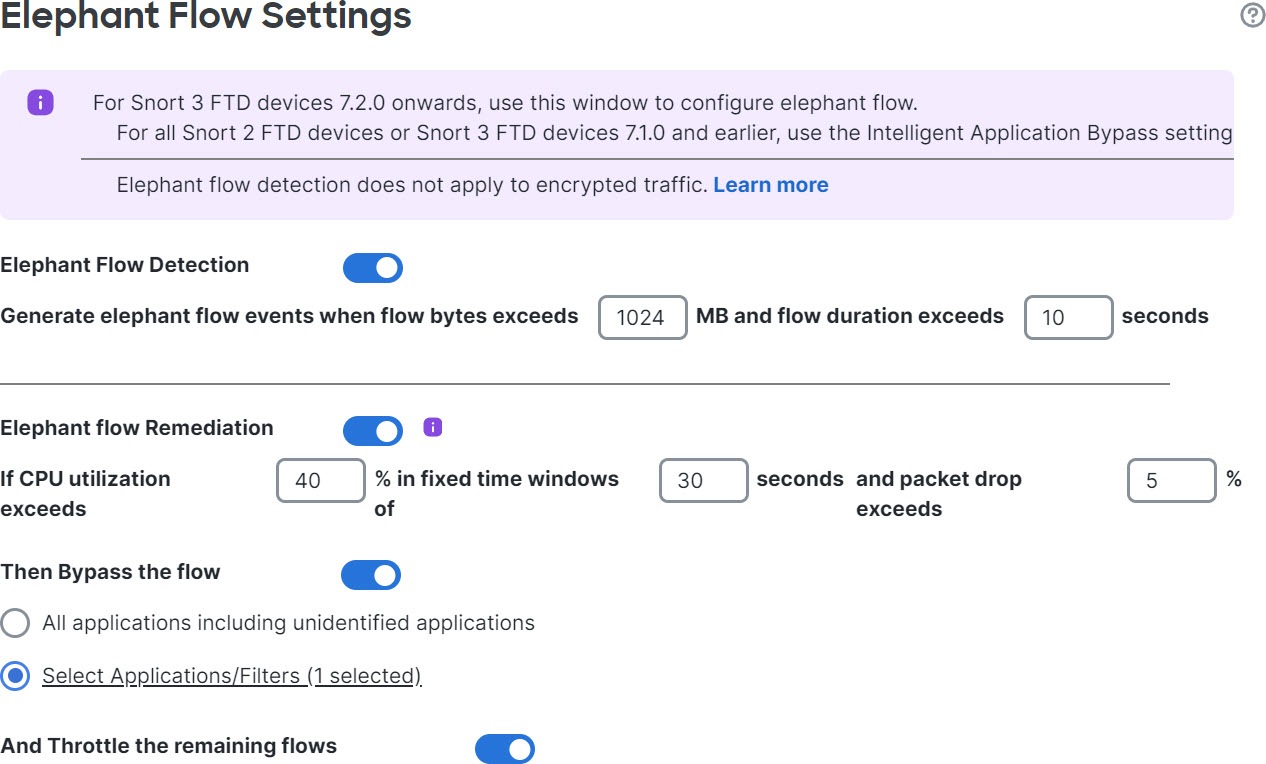
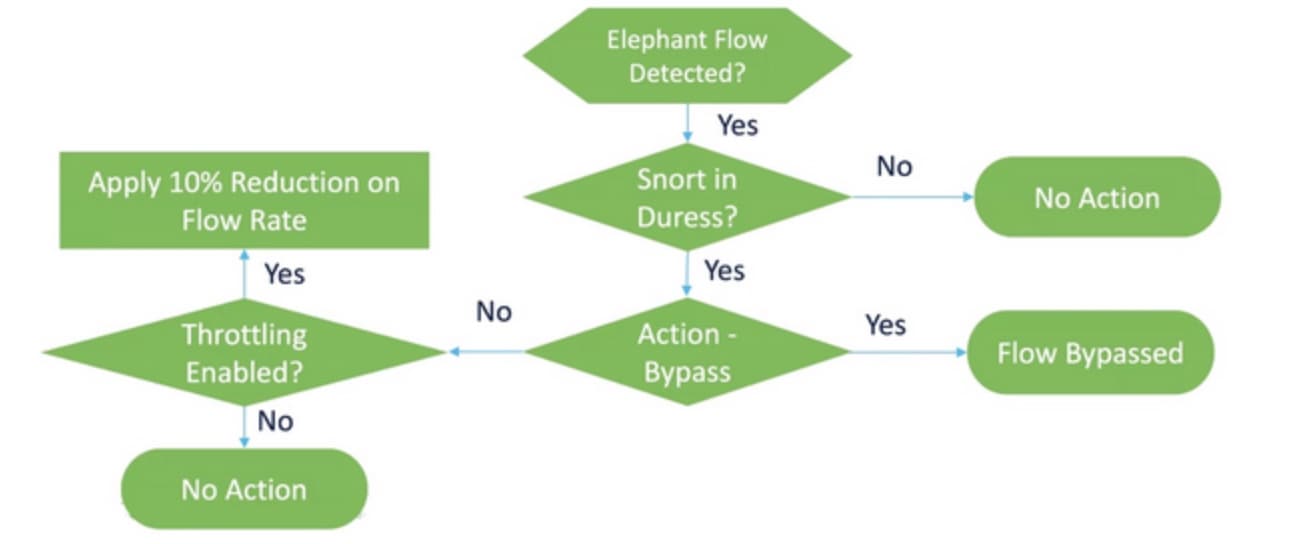
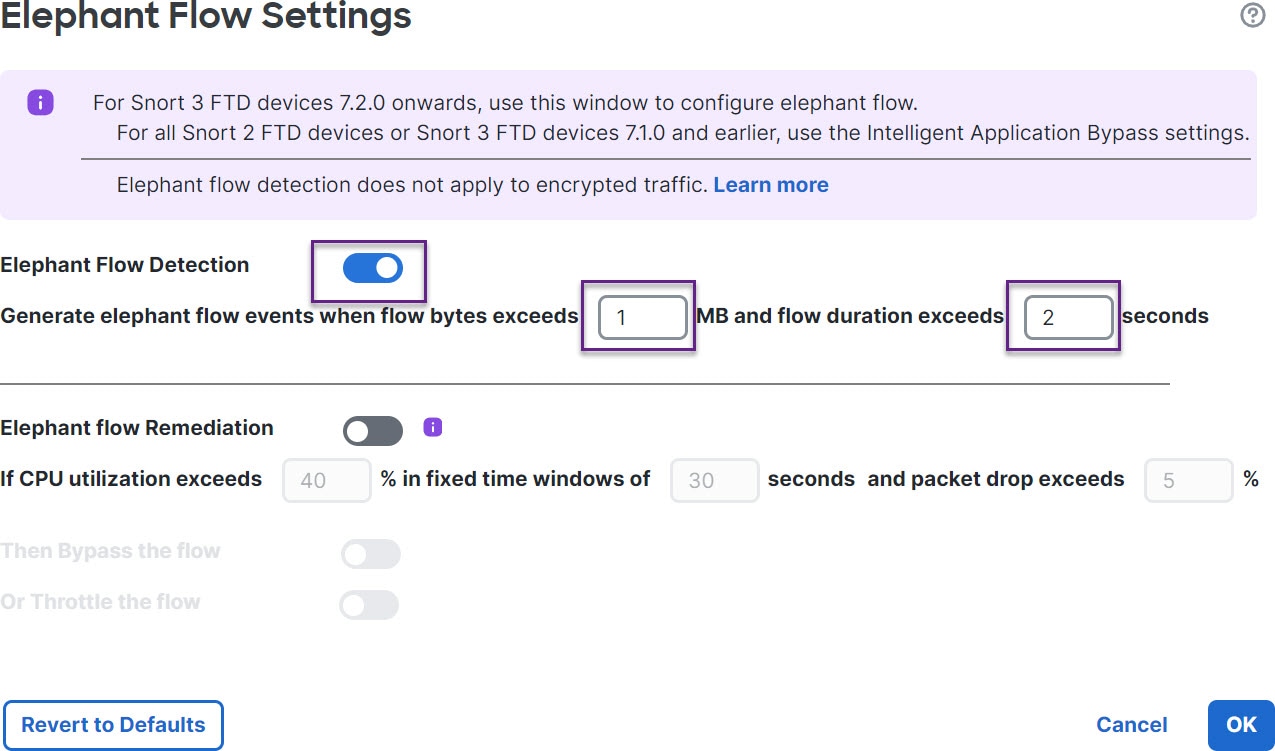
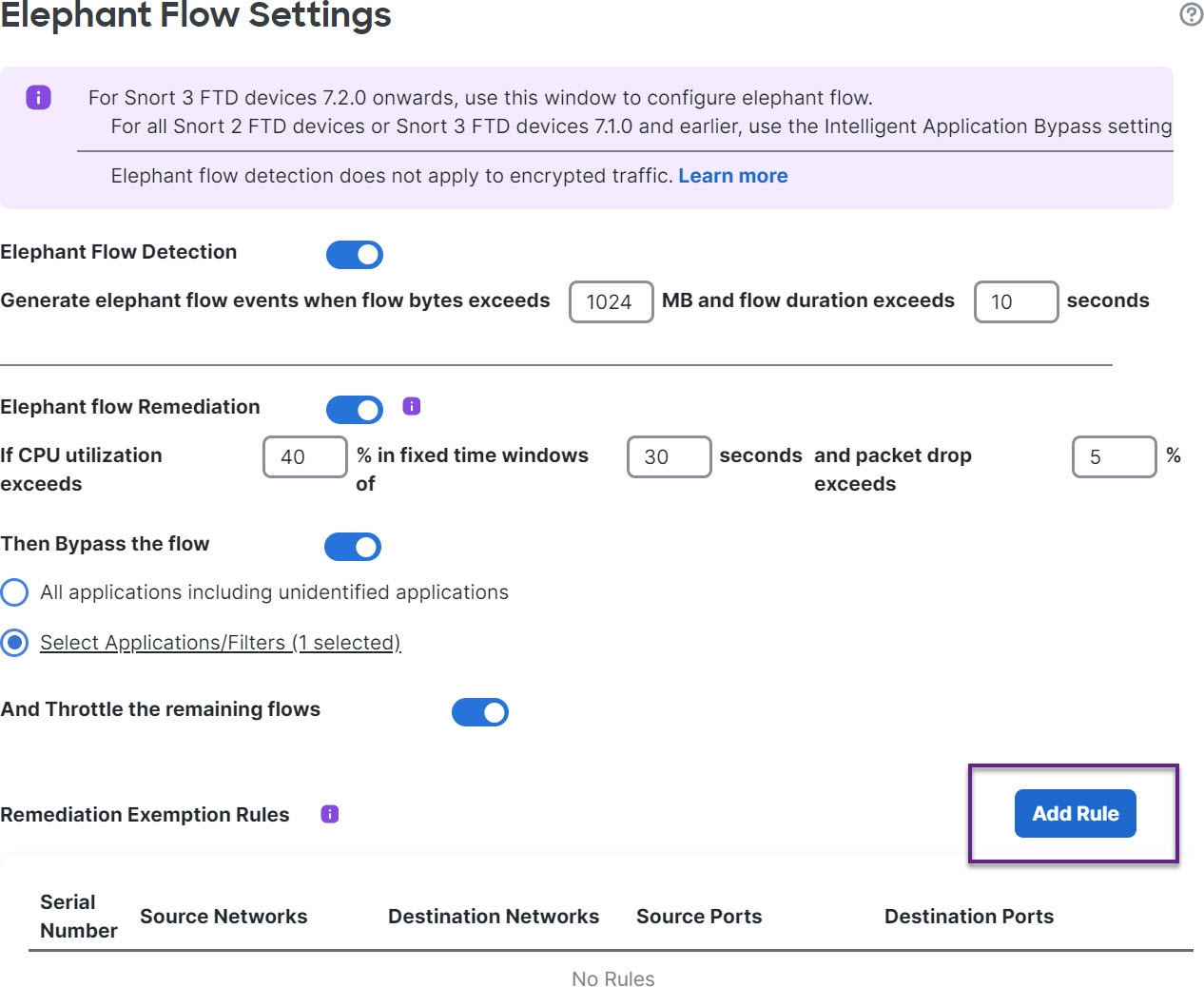
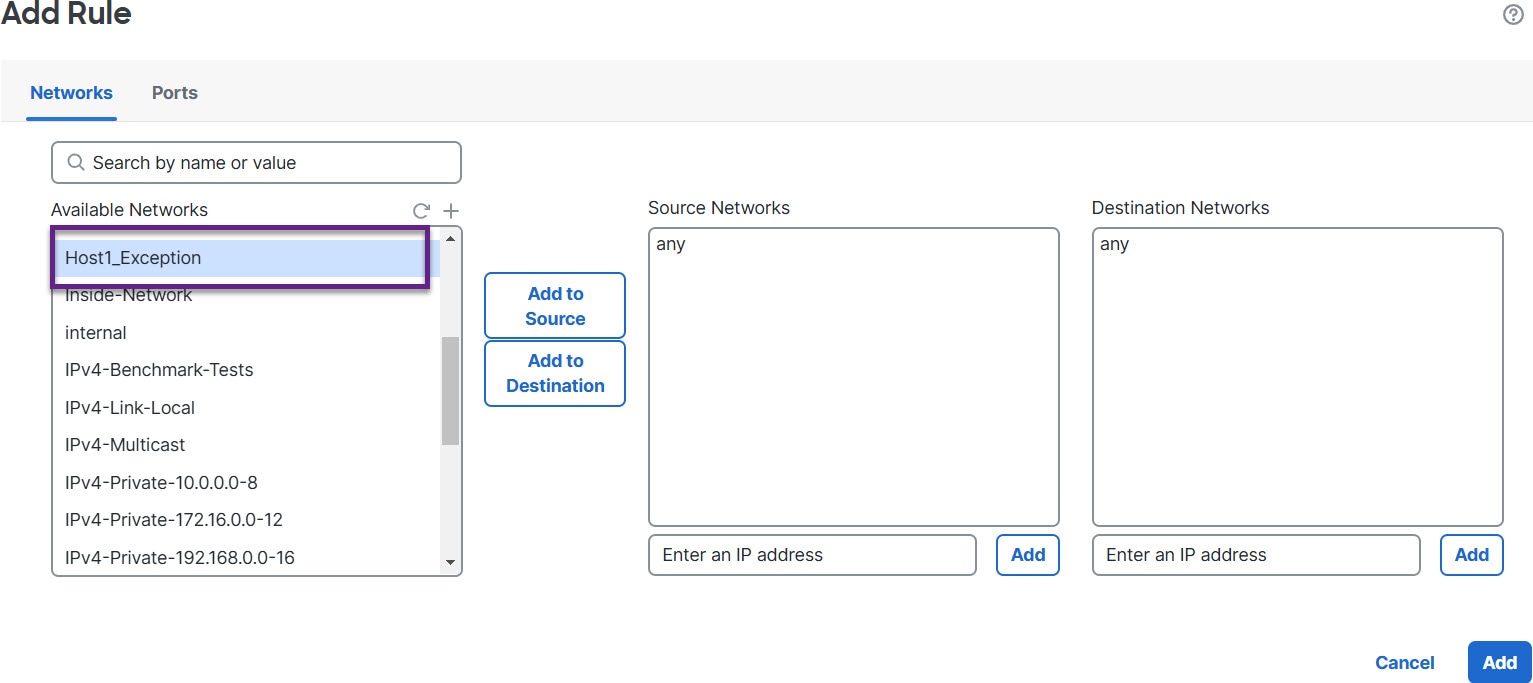
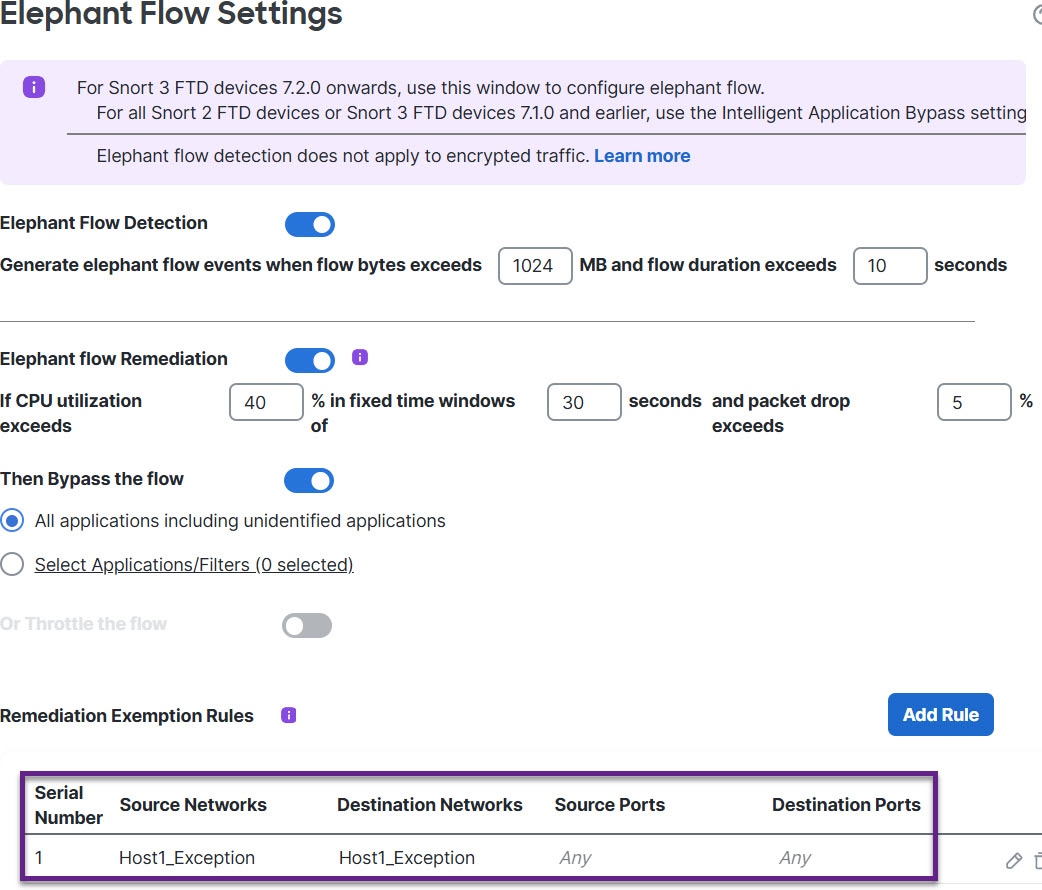
You can use the elephant flow detection feature to detect and remediate elephant flows. The following remediation actions can be applied:
-
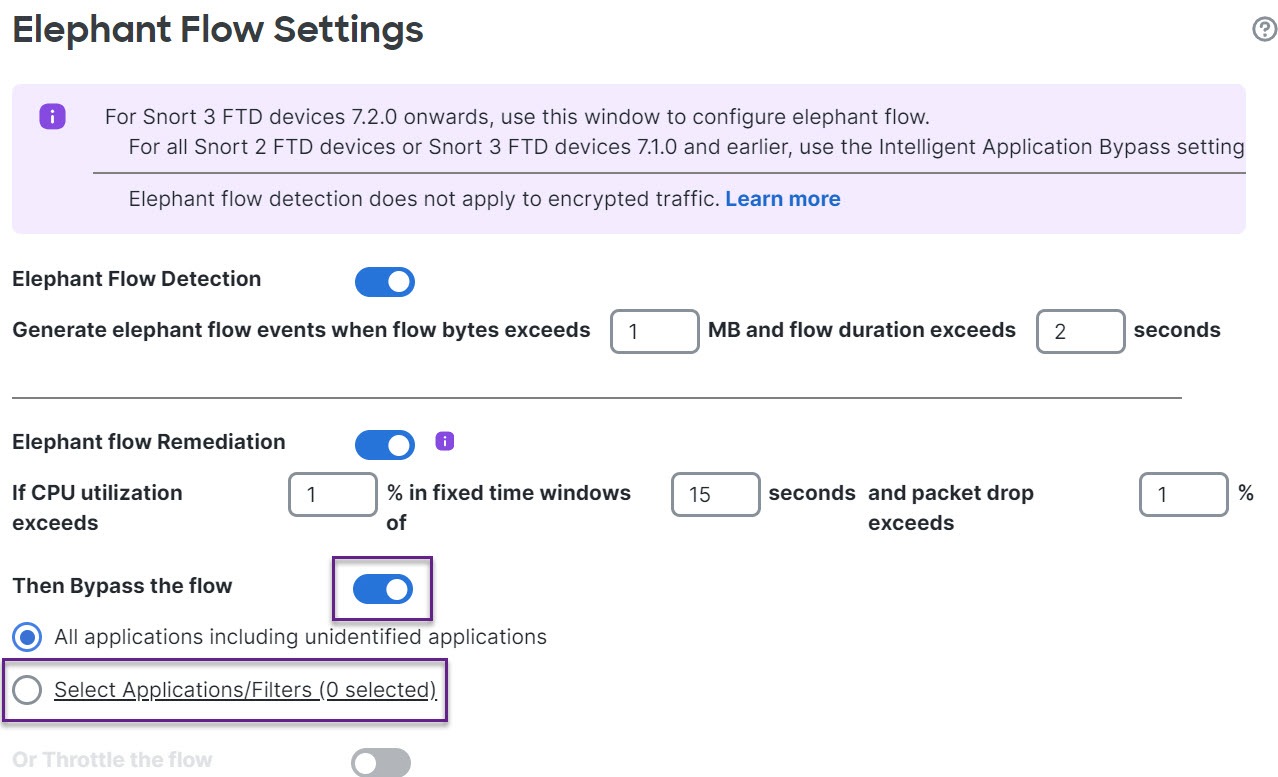
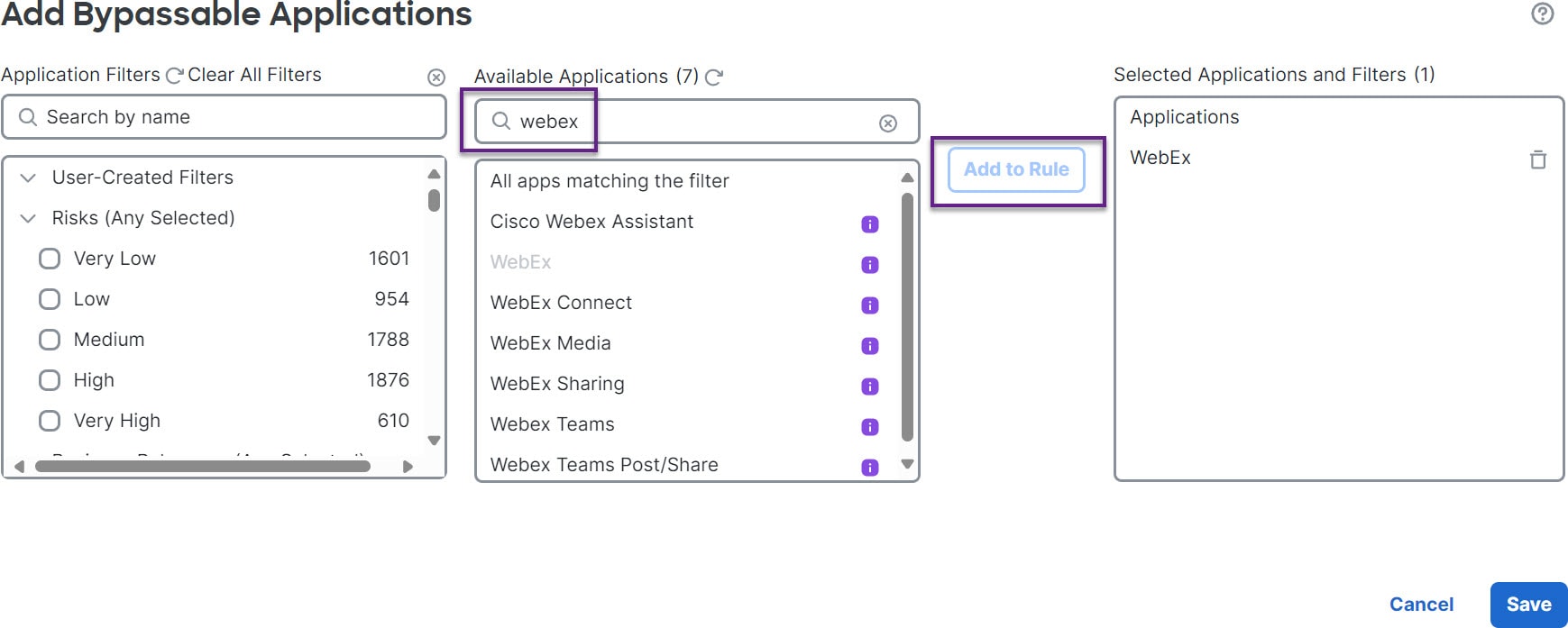
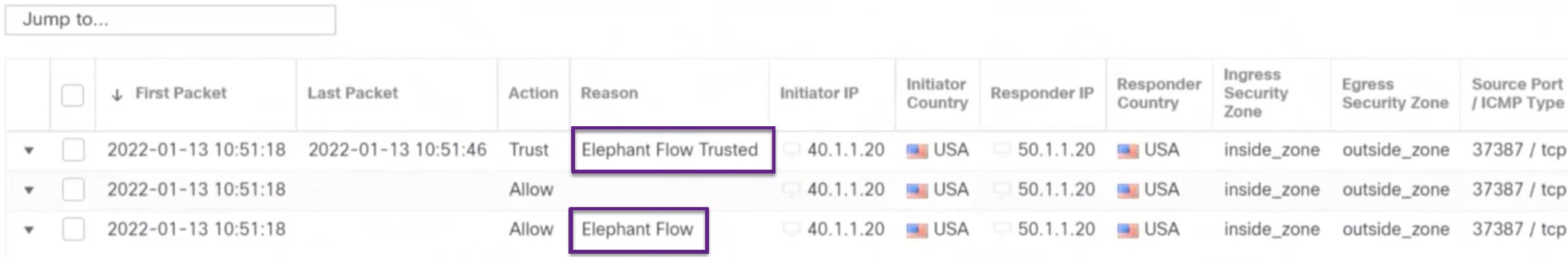
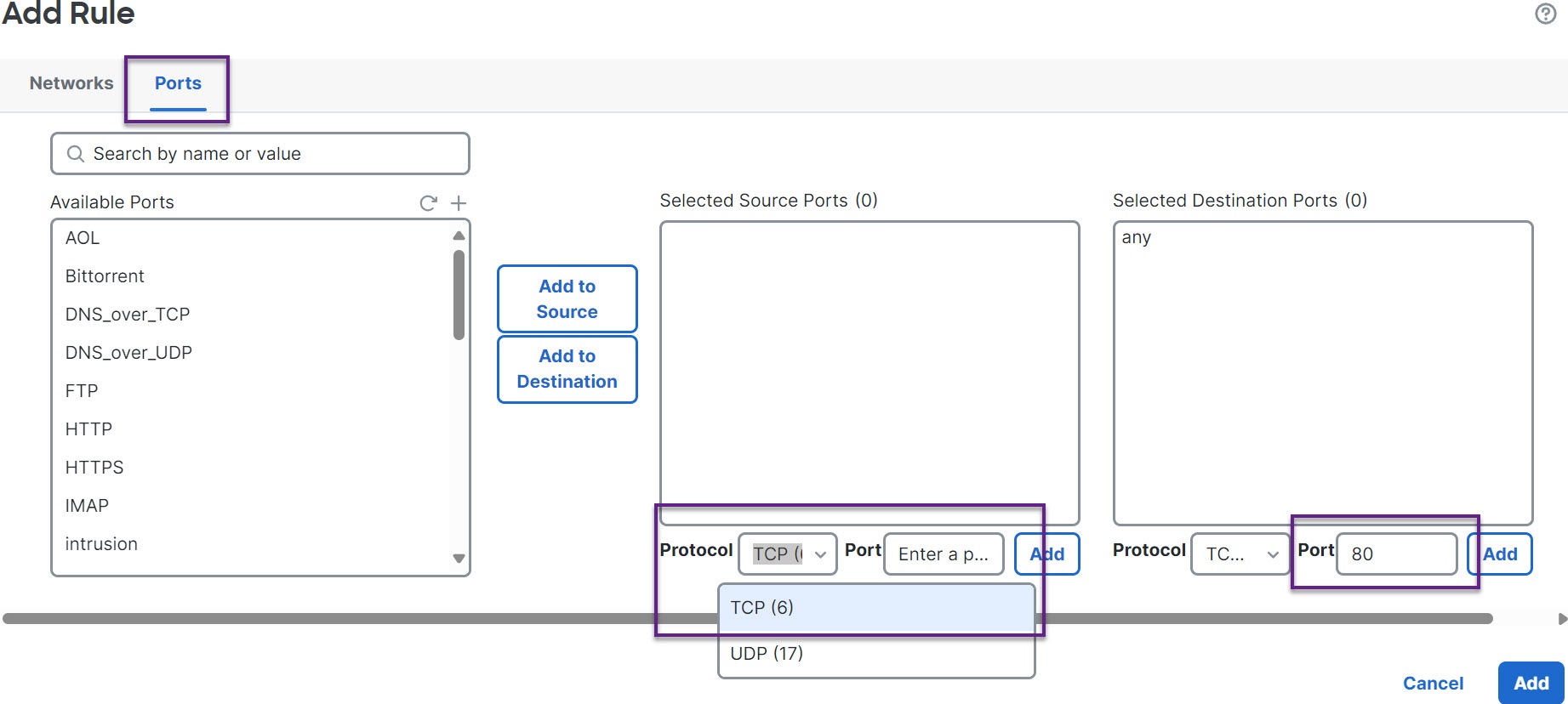
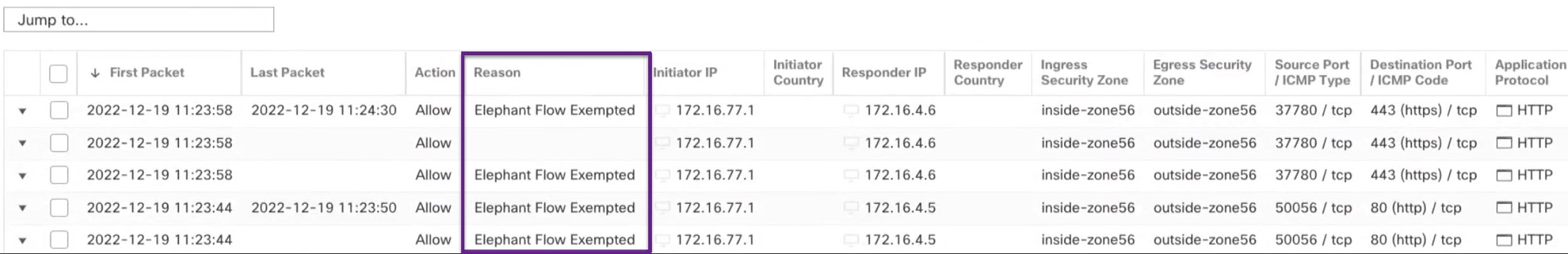
Bypass elephant flow–You can configure elephant flow to bypass Snort inspection. If this is configured, Snort does not receive any packet from that flow.
-
Throttle elephant flow–You can apply rate-limit to the flow and continue to inspect flows. The flow rate is calculated dynamically and 10% of the flow rate is reduced. Snort sends the verdict (QoS flow with 10% less flow rate) to the firewall engine. If you choose to bypass all applications including unidentified applications, you cannot configure the throttle action (rate-limit) for any flow.
 Note |
For the elephant flow detection to work, Snort 3 must be the detection engine. |

 Feedback
Feedback