- Preface
- Product Overview
- Configuring the Router for the First Time
- Configuring a Supervisor Engine 720
- Configuring a Route Switch Processor 720
- Configuring NSF with SSO Supervisor Engine Redundancy
- ISSU and eFSU on Cisco 7600 Series Routers
- Configuring RPR and RPR+ Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring a Supervisor Engine 32
- Configuring LAN Ports for Layer 2 Switching
- Configuring Flex Links
- Configuring EtherChannels
- Configuring VTP
- Configuring VLANs
- Configuring Private VLANs
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling
- Configuring L2TPv3
- Configuring STP and MST
- Configuring Optional STP Features
- Configuring Layer 3 Interfaces
- Configuring GTP-SLB IPV6 Support
- IP Subscriber Awareness over Ethernet
- Configuring UDE and UDLR
- Configuring Multiprotocol Label Switching on the PFC
- Configuring IPv4 Multicast VPN Support
- Configuring Multicast VPN Extranet Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast PFC3 and DFC3 Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping for IPv6 Multicast Traffic
- Configuring IGMP Snooping for IPv4 Multicast Traffic
- Configuring PIM Snooping
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VRF aware 6RD Tunnels
- Configuring VLAN ACLs
- Private Hosts (Using PACLs)
- Configuring IPv6 PACL
- IPv6 First-Hop Security Features
- Configuring Online Diagnostics
- Configuring Denial of Service Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Traffic Storm Control
- Unknown Unicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC QoS Statistics Data Export
- Configuring MPLS QoS on the PFC
- Configuring LSM MLDP based MVPN Support
- Configuring IEEE 802.1X Port-Based Authentication
- Configuring IEEE 802.1ad
- Configuring Port Security
- Configuring UDLD
- Configuring NetFlow and NDE
- Configuring Local SPAN, RSPAN, and ERSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Web Cache Services Using WCCP
- Using the Top N Utility
- Using the Layer 2 Traceroute Utility
- Configuring Bidirectional Forwarding and Detection over Switched Virtual Interface
- Configuring Call Home
- Configuring IPv6 Policy Based Routing
- Using the Mini Protocol Analyzer
- Configuring Resilient Ethernet Protocol
- Configuring Synchronous Ethernet
- Configuring Link State Tracking
- Configuring BGP PIC Edge and Core for IP and MPLS
- Configuring VRF aware IPv6 tunnels over IPv4 transport
- ISIS IPv4 Loop Free Alternate Fast Reroute (LFA FRR)
- Multicast Service Reflection
- Y.1731 Performance Monitoring
- Online Diagnostic Tests
- Acronyms
- Cisco IOS Release 15S Software Images
- Index
- Understanding VACLs
- Configuring VACLs
- VACL Configuration Overview
- Defining a VLAN Access Map
- Configuring a Match Clause in a VLAN Access Map Sequence
- Configuring an Action Clause in a VLAN Access Map Sequence
- Applying a VLAN Access Map
- Verifying VLAN Access Map Configuration
- VLAN Access Map Configuration and Verification Examples
- Configuring a Capture Port
- Configuring VACL Logging
Configuring VLAN ACLs
This chapter describes how to configure VLAN ACLs (VACLs) on Cisco 7600 series routers.

Note ●![]() For complete syntax and usage information for the commands used in this chapter, refer to the Cisco 7600 Series Routers Command References at this URL:
For complete syntax and usage information for the commands used in this chapter, refer to the Cisco 7600 Series Routers Command References at this URL:
http://www.cisco.com/en/US/products/hw/routers/ps368/prod_command_reference_list.html
- OAL and VACL capture are incompatible. Do not configure both features on the router. With OAL configured (see the “Optimized ACL Logging with a PFC3” section), use SPAN to capture traffic.
Understanding VACLs
These sections describe VACLs:
VACL Overview
VACLs can provide access control for all packet s that are bridged within a VLAN or that are routed into or out of a VLAN or a WAN interface for VACL capture. Unlike regular Cisco IOS standard or extended ACLs that are configured on router interfaces only and are applied on routed packets only, VACLs apply to all packets and can be applied to any VLAN or WAN interface. VACLS are processed in hardware. VACLs use Cisco IOS ACLs. VACLs ignore any Cisco IOS ACL fields that are not supported in hardware.
You can configure VACLs for IP, IPX, and MAC-Layer traffic. VACLs applied to WAN interfaces support only IP traffic for VACL capture.
When you configure a VACL and apply it to a VLAN, all packets entering the VLAN are checked against this VACL. If you apply a VACL to the VLAN and an ACL to a routed interface in the VLAN, a packet coming in to the VLAN is first checked against the VACL and, if permitted, is then checked against the input ACL before it is handled by the routed interface. When the packet is routed to another VLAN, it is first checked against the output ACL applied to the routed interface and, if permitted, the VACL configured for the destination VLAN is applied. If a VACL is configured for a packet type and a packet of that type does not match the VACL, the default action is deny.

Note ●![]() TCP Intercepts and Reflexive ACLs take precedence over a VACL action if these are configured on the same interface.
TCP Intercepts and Reflexive ACLs take precedence over a VACL action if these are configured on the same interface.
- VACLs and CBAC cannot be configured on the same interface.
- IGMP packets are not checked against VACLs.
Bridged Packets
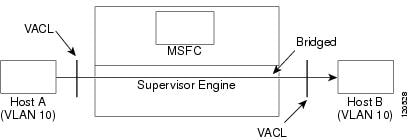
Figure 38-1 shows a VACL applied on bridged packets.
Figure 38-1 Applying VACLs on Bridged Packets
Routed Packets
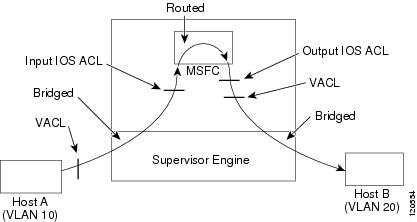
Figure 38-2 shows how ACLs are applied on routed and Layer 3-switched packets. For routed or Layer 3-switched packets, the ACLs are applied in the following order:
Figure 38-2 Applying VACLs on Routed Packets
Multicast Packets
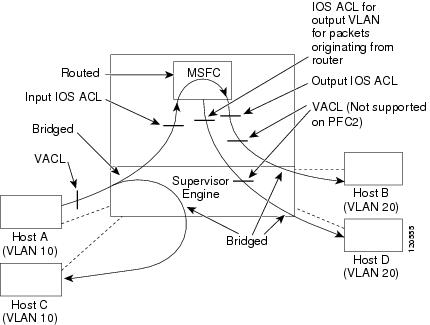
Figure 38-3 shows how ACLs are applied on packets that need multicast expansion. For packets that need multicast expansion, the ACLs are applied in the following order:
1.![]() Packets that need multicast expansion:
Packets that need multicast expansion:
2.![]() Packets after multicast expansion:
Packets after multicast expansion:
3.![]() Packets originating from router—VACL for output VLAN
Packets originating from router—VACL for output VLAN
Figure 38-3 Applying VACLs on Multicast Packets
Configuring VACLs
These sections describe how to configure VACLs:
- VACL Configuration Overview
- Defining a VLAN Access Map
- Configuring a Match Clause in a VLAN Access Map Sequence
- Configuring an Action Clause in a VLAN Access Map Sequence
- Applying a VLAN Access Map
- Verifying VLAN Access Map Configuration
- VLAN Access Map Configuration and Verification Examples
- Configuring a Capture Port
VACL Configuration Overview
VACLs use standard and extended Cisco IOS IP and IPX ACLs, and MAC Layer-named ACLs (see the “Configuring MAC ACLs” section) and VLAN access maps.
ed to VLANs or to WAN interfaces for VACL capture. VACLs attached to WAN interfaces support only standard and extended Cisco IOS IP ACLs.
Each VLAN access map can consist of one or more map sequences, each sequence with a match clause and an action clause. The match clause specifies IP, IPX, IPv6 or MAC ACLs for traffic filtering and the action clause specifies the action to be taken when a match occurs. When a flow matches a permit ACL entry, the associated action is taken and the flow is not checked against the remaining sequences. When a flow matches a deny ACL entry, it will be checked against the next ACL in the same sequence or the next sequence. If a flow does not match any ACL entry and at least one ACL is configured for that packet type, the packet is denied.
To use access control for both bridged and routed traffic, you can use VACLs alone or a combination of VACLs and ACLs. You can define ACLs on the VLAN interfaces to use access control for both the input and output routed traffic. You can define a VACL to use access control for the bridged traffic.
The following caveats apply to ACLs when used with VACLs:
- Packets that require logging on the outbound ACLs are not logged if they are denied by a VACL.
- VACLs are applied on packets before NAT translation. If the translated flow is not subject to access control, the flow might be subject to access control after the translation because of the VACL configuration.
The action clause in a VACL can be forward, drop, capture, or redirect. Traffic can also be logged. VACLs applied to WAN interfaces do not support the redirect or log actions.

Note ●![]() VACLs have an implicit deny at the end of the map; a packet is denied if it does not match any ACL entry, and at least one ACL is configured for the packet type.
VACLs have an implicit deny at the end of the map; a packet is denied if it does not match any ACL entry, and at least one ACL is configured for the packet type.
- If an empty or undefined ACL is specified in a VACL, any packets will match the ACL and the associated action is taken.

Note ●![]() All the IP address related restrictions such as address compression that apply to RACL and PACL also apply to VACL.
All the IP address related restrictions such as address compression that apply to RACL and PACL also apply to VACL.
Defining a VLAN Access Map
To define a VLAN access map, perform this task:
|
|
|
|---|---|
Defines the VLAN access map. Optionally, you can specify the VLAN access map sequence number. |
|
When defining a VLAN access map, note the following information:
- To insert or modify an entry, specify the map sequence number.
- If you do not specify the map sequence number, a number is automatically assigned.
- You can specify only one match clause and one action clause per map sequence.
- Use the no keyword with a sequence number to remove a map sequence.
- Use the no keyword without a sequence number to remove the map.

Note![]() While defining the VLAN access-map, you should use only single word as the access- map name and white spaces are not allowed in the access-map name. For example, you can use map_name to name the access-map, but you should not use multiple words such as map name. Effective from Cisco IOS release 12.2(33)SRE8, the length of the VLAN access-map name should not exceed 25 characters.
While defining the VLAN access-map, you should use only single word as the access- map name and white spaces are not allowed in the access-map name. For example, you can use map_name to name the access-map, but you should not use multiple words such as map name. Effective from Cisco IOS release 12.2(33)SRE8, the length of the VLAN access-map name should not exceed 25 characters.
See the “VLAN Access Map Configuration and Verification Examples” section.
Configuring a Match Clause in a VLAN Access Map Sequence
To configure a match clause in a VLAN access map sequence, perform this task:
When configuring a match clause in a VLAN access map sequence, note the following information:
- You can select one or more ACLs.
- VACLs attached to WAN interfaces support only standard and extended Cisco IOS IP ACLs.
- Use the no keyword to remove a match clause or specified ACLs in the clause.
- For information about named MAC-Layer ACLs, refer to the “Configuring MAC ACLs” section.
- For information about Cisco IOS ACLs, refer to the Cisco IOS Security Configuration Guide, Release 12.2, “Traffic Filtering and Firewalls,” at this URL:
http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfacls.html
See the “VLAN Access Map Configuration and Verification Examples” section.
Sample Configuration for Match Clause
The following example shows the configuration of an IPV6 based match.
Configuring an Action Clause in a VLAN Access Map Sequence
To configure an action clause in a VLAN access map sequence, perform this task:
When configuring an action clause in a VLAN access map sequence, note the following information:
- You can set the action to drop, forward, forward capture, or redirect packets.
- VACLs applied to WAN interfaces support only the forward capture action. VACLs applied to WAN interfaces do not support the drop, forward, or redirect actions.
- Forwarded packets are still subject to any configured Cisco IOS security ACLs.
- The capture action sets the capture bit for the forwarded packets so that ports with the capture function enabled can receive the packets. Only forwarded packets can be captured. For more information about the capture action, see the “Configuring a Capture Port” section.
- VACLs applied to WAN interfaces do not support the log action.
- When the log action is specified, dropped packets are logged in software. Only dropped IP packets can be logged.
- The redirect action allows you to specify up to five interfaces, which can be physical interfaces or EtherChannels. You cannot specify packets to be redirected to an EtherChannel member or a VLAN interface.
- The redirect interface must be in the VLAN for which the VACL access map is configured.
- With a PFC3, if a VACL is redirecting traffic to an egress SPAN source port, SPAN does not copy the VACL-redirected traffic.
- SPAN and RSPAN destination ports transmit VACL-redirected traffic.
- Use the no keyword to remove an action clause or specified redirect interfaces.
See the “VLAN Access Map Configuration and Verification Examples” section.
Applying a VLAN Access Map
To apply a VLAN access map, perform this task:
|
|
|
|---|---|
Router(config)# vlan filter map_name { vlan-list vlan_list | interface type 1 number 2 } |
Applies the VLAN access map to the specified VLANs or WAN interfaces. |
Router(config)# no vlan filter map_name [ vlan-list vlan_list | interface type 1 number 2 ] |
Removes the VLAN access map from the specified VLANs or WAN interfaces. |
|
2.number = slot/port or slot/port_adapter/port; can include a subinterface or channel group descriptor |
When applying a VLAN access map, note the following information:
- You can apply the VLAN access map to one or more VLANs or WAN interfaces.
- The vlan_list parameter can be a single VLAN ID or a comma-separated list of VLAN IDs or VLAN ID ranges ( vlan_ID – vlan_ID).
- If you delete a WAN interface that has a VACL applied, the VACL configuration on the interface is also removed.
- You can apply only one VLAN access map to each VLAN or WAN interface.
- VACLs applied to VLANs are active only for VLANs with a Layer 3 VLAN interface configured. Applying a VLAN access map to a VLAN without a Layer 3 VLAN interface creates an administratively down Layer 3 VLAN interface to support the VLAN access map.
- VACLs applied to VLANs are inactive if the Layer 2 VLAN does not exist or is not operational.
- You cannot apply a VACL to a secondary private VLAN. VACLs applied to primary private VLANs also apply to secondary private VLANs.
- Use the no keyword to clear VLAN access maps from VLANs or WAN interfaces.
See the “VLAN Access Map Configuration and Verification Examples” section.
Verifying VLAN Access Map Configuration
To verify VLAN access map configuration, perform this task:
|
|
|
|---|---|
Verifies VLAN access map configuration by displaying the content of a VLAN access map. |
|
Router# show vlan filter [ access-map map_name | vlan vlan_id | interface type 3 number 4 ] |
Verifies VLAN access map configuration by displaying the mappings between VACLs and VLANs. |
|
4.number = slot/port or slot/port_adapter/port; can include a subinterface or channel group descriptor |
VLAN Access Map Configuration and Verification Examples
Assume IP-named ACL net_10 and any_host are defined as follows:
This example shows how to define and apply a VLAN access map to forward IP packets. In this example, IP traffic matching net_10 is forwarded and all other IP packets are dropped due to the default drop action. The map is applied to VLAN 12 to 16.
This example shows how to define and apply a VLAN access map to drop and log IP packets. In this example, IP traffic matching net_10 is dropped and logged and all other IP packets are forwarded:
This example shows how to define and apply a VLAN access map to forward and capture IP packets. In this example, IP traffic matching net_10 is forwarded and captured and all other IP packets are dropped:
Configuring a Capture Port
A port configured to capture VACL-filtered traffic is called a capture port.

Note![]() To apply IEEE 802.1Q or ISL tags to the captured traffic, configure the capture port to trunk unconditionally (see the “Configuring the Layer 2 Switching Port as an ISL or 802.1Q Trunk” section and the “Configuring the Layer 2 Trunk Not to Use DTP” section).
To apply IEEE 802.1Q or ISL tags to the captured traffic, configure the capture port to trunk unconditionally (see the “Configuring the Layer 2 Switching Port as an ISL or 802.1Q Trunk” section and the “Configuring the Layer 2 Trunk Not to Use DTP” section).
To configure a capture port, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface {{ type 5 slot/port } |
||
Router(config-if)# switchport capture allowed vlan { add | all | except | remove } vlan_list |
(Optional) Filters the captured traffic on a per-destination-VLAN basis. The default is all. |
|
Clears the configured destination VLAN list and returns to the default value (all). |
||
|
5.type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
When configuring a capture port, note the following information:
- You can configure any port as a capture port.
- The vlan_list parameter can be a single VLAN ID or a comma-separated list of VLAN IDs or VLAN ID ranges ( vlan_ID – vlan_ID).
- To encapsulate captured traffic, configure the capture port with the switchport trunk encapsulation command (see the “Configuring a Layer 2 Switching Port as a Trunk” section) before you enter the switchport capture command.
- For unencapsulated captured traffic, configure the capture port with the switchport mode access command (see the “Configuring a LAN Interface as a Layer 2 Access Port” section) before you enter the switchport capture command.
- The capture port supports only egress traffic. No traffic can enter the router through a capture port.
- LI overrides VACL Capture.
- VACL Capture and OAL are mutually exclusive features.
- When the VACL capture is configured on an egress interface with another egress feature that requires software processing of the traffic, packets of the overlapping traffic may be captured twice.
This example shows how to configure a Fast Ethernet interface 5/1 as a capture port:
This example shows how to display VLAN access map information:
This example shows how to display mappings between VACLs and VLANs. For each VACL map, there is information about the VLANs that the map is configured on and the VLANs that the map is active on. A VACL is not active if the VLAN does not have an interface.
Configuring VACL Logging
When you configure VACL logging, IP or IPv6 packets that are denied generate log messages in these situations:
- When the first matching packet is received
- For any matching packets received during the last 5-minute interval
- If the threshold is reached before the 5-minute interval
Log messages are generated on a per-flow basis. A flow is defined as packets with the same IP addresses and Layer 4 (UDP or TCP) port numbers. When a log message is generated, the timer and packet count is reset.
These restrictions apply to VACL logging:
- Because of the rate-limiting function for redirected packets, VACL logging counters may not be accurate.
- Only denied IP packets are logged.
To configure VACL logging, use the action drop log command action in VLAN access map submode (see the “Configuring VACLs” section for configuration information) and perform this task in global configuration mode to specify the global VACL logging parameters:
This example shows how to configure global VACL logging in hardware:
Displaying IPv6 VACL Logging
To display the contents of the IPv6 VACL log table, use the following command:
show vlan access-log v6flow protocol {{src_addr src_mask} | any | {host {hostname | host_ip}}} {{dst_addr dst_mask} | any | {host {hostname | host_ip}}}[vlan vlan_id]
The following examples shows sample outputs for the command.
 Feedback
Feedback