- Preface
- Product Overview
- Configuring the Router for the First Time
- Configuring a Supervisor Engine 720
- Configuring a Route Switch Processor 720
- Configuring NSF with SSO Supervisor Engine Redundancy
- ISSU and eFSU on Cisco 7600 Series Routers
- Configuring RPR and RPR+ Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring a Supervisor Engine 32
- Configuring LAN Ports for Layer 2 Switching
- Configuring Flex Links
- Configuring EtherChannels
- Configuring VTP
- Configuring VLANs
- Configuring Private VLANs
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling
- Configuring L2TPv3
- Configuring STP and MST
- Configuring Optional STP Features
- Configuring Layer 3 Interfaces
- Configuring GTP-SLB IPV6 Support
- IP Subscriber Awareness over Ethernet
- Configuring UDE and UDLR
- Configuring Multiprotocol Label Switching on the PFC
- Configuring IPv4 Multicast VPN Support
- Configuring Multicast VPN Extranet Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast PFC3 and DFC3 Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping for IPv6 Multicast Traffic
- Configuring IGMP Snooping for IPv4 Multicast Traffic
- Configuring PIM Snooping
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VRF aware 6RD Tunnels
- Configuring VLAN ACLs
- Private Hosts (Using PACLs)
- Configuring IPv6 PACL
- IPv6 First-Hop Security Features
- Configuring Online Diagnostics
- Configuring Denial of Service Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Traffic Storm Control
- Unknown Unicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC QoS Statistics Data Export
- Configuring MPLS QoS on the PFC
- Configuring LSM MLDP based MVPN Support
- Configuring IEEE 802.1X Port-Based Authentication
- Configuring IEEE 802.1ad
- Configuring Port Security
- Configuring UDLD
- Configuring NetFlow and NDE
- Configuring Local SPAN, RSPAN, and ERSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Web Cache Services Using WCCP
- Using the Top N Utility
- Using the Layer 2 Traceroute Utility
- Configuring Bidirectional Forwarding and Detection over Switched Virtual Interface
- Configuring Call Home
- Configuring IPv6 Policy Based Routing
- Using the Mini Protocol Analyzer
- Configuring Resilient Ethernet Protocol
- Configuring Synchronous Ethernet
- Configuring Link State Tracking
- Configuring BGP PIC Edge and Core for IP and MPLS
- Configuring VRF aware IPv6 tunnels over IPv4 transport
- ISIS IPv4 Loop Free Alternate Fast Reroute (LFA FRR)
- Multicast Service Reflection
- Y.1731 Performance Monitoring
- Online Diagnostic Tests
- Acronyms
- Cisco IOS Release 15S Software Images
- Index
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 31, 2014
Chapter: Configuring Layer 2 Protocol Tunneling
Configuring Layer 2 Protocol Tunneling
This chapter describes how to configure Layer 2 protocol tunneling on the Cisco 7600 series routers.

Note ●![]() For complete syntax and usage information for the commands used in this chapter, refer to the Cisco 7600 Series Routers Command References at this URL:
For complete syntax and usage information for the commands used in this chapter, refer to the Cisco 7600 Series Routers Command References at this URL:
http://www.cisco.com/en/US/products/hw/routers/ps368/prod_command_reference_list.html
- The WS-X6548-GE-TX, WS-X6548V-GE-TX, WS-X6148-GE-TX, and WS-X6148V-GE-TX switching modules do not support Layer 2 protocol tunneling.
Understanding How Layer 2 Protocol Tunneling Works
Layer 2 protocol tunneling allows Layer 2 protocol data units (PDUs) (CDP, STP, and VTP) to be tunneled through a network. This section uses the following terminology:
- Edge router—The router connected to the customer router and placed on the boundary of the service provider network (see Figure 18-1).
- Layer 2 protocol tunnel port—A port on the edge router on which a specific tunneled protocol can be encapsulated or deencapsulated. The Layer 2 protocol tunnel port is configured through CLI commands.
- Tunneled PDU—A CDP, STP, or VTP PDU.
Without Layer 2 protocol tunneling, tunnel ports drop STP and VTP packets and process CDP packets. This handling of the PDUs creates different spanning tree domains (different spanning tree roots) for the customer switches. For example, STP for a VLAN on router 1 (see Figure 18-1) builds a spanning tree topology on switches 1, 2, and 3 without considering convergence parameters based on switches 4 and 5. To provide a single spanning tree domain for the customer, a generic scheme to tunnel BPDUs was created for control protocol PDUs (CDP, STP, and VTP). This process is referred to as Generic Bridge PDU Tunneling (GBPT).
Figure 18-1 Layer 2 Protocol Tunneling Network Configuration
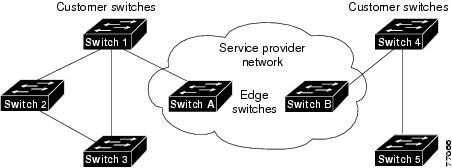
GBPT provides a scalable approach to PDU tunneling by software encapsulating the PDUs in the ingress edge switches and then multicasting them in hardware. All switches inside the service provider network treat these encapsulated frames as data packets and forward them to the other end. The egress edge router listens for these special encapsulated frames and deencapsulates them; they are then forwarded out of the tunnel.
The encapsulation involves rewriting the destination media access control (MAC) address in the PDU. An ingress edge router rewrites the destination MAC address of the PDUs received on a Layer 2 tunnel port with the Cisco proprietary multicast address (01-00-0c-cd-cd-d0). The PDU is then flooded to the native VLAN of the Layer 2 tunnel port. If you enable Layer 2 protocol tunneling on a port, PDUs of an enabled protocol are not sent out. If you disable Layer 2 protocol tunneling on a port, the disabled protocols function the same way they were functioning before Layer 2 protocol tunneling was disabled on the port.
Configuring Support for Layer 2 Protocol Tunneling

Note ●![]() Encapsulated PDUs received by an 802.1Q tunnel port are transmitted from other tunnel ports in the same VLAN on the router.
Encapsulated PDUs received by an 802.1Q tunnel port are transmitted from other tunnel ports in the same VLAN on the router.
–![]() See the “Configuring Jumbo Frame Support” section.
See the “Configuring Jumbo Frame Support” section.
–![]() Take note of the modules listed in the “Configuring Jumbo Frame Support” section that do not support jumbo frames.
Take note of the modules listed in the “Configuring Jumbo Frame Support” section that do not support jumbo frames.
To configure Layer 2 protocol tunneling on a port, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface type 1 slot/port |
||
Router(config-if)# l2protocol-tunnel [ cdp | drop-threshold [ packets | shutdown-threshold [ packets ]| stp | vtp ] |
Configures the Layer 2 port as a Layer 2 protocol tunnel port for the protocols specified. |
|
Router(config-if)# no l2protocol-tunnel [ cdp | drop-threshold | shutdown-threshold | stp | vtp ] |
||
Router# show l2protocol-tunnel [ interface type 1 slot/port | summary ] |
|
1.type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
When you configure a Layer 2 port as a Layer 2 protocol tunnel port, note the following information:
- Optionally, you may specify a drop threshold for the port. The drop threshold value, from 1 to 4096, determines the number of packets to be processed for that protocol on that interface in one second. When the drop threshold is exceeded, PDUs for the specified protocol are dropped for the remainder of the 1-second period. If a shutdown threshold is not specified, the value is 0 (shutdown threshold disabled).
- Optionally, you may specify a shutdown threshold for the port. The shutdown threshold value, from 1 to 4096, determines the number of packets to be processed for that protocol on that interface in one second. When the shutdown threshold is exceeded, the port is put in errdisable state. If a shutdown threshold is not specified, the value is 0 (shutdown threshold disabled).

Note![]() Refer to the Cisco 7600 Series Router Cisco IOS Command Reference for more information about the l2ptguard keyword for the following commands:
Refer to the Cisco 7600 Series Router Cisco IOS Command Reference for more information about the l2ptguard keyword for the following commands:
• errdisable detect cause
• errdisable recovery cause
This example shows how to configure Layer 2 protocol tunneling and shutdown thresholds on port 5/1 for CDP, STP, and VTP, and verify the configuration:
This example shows how to display counter information for port 5/1:
This example shows how to clear the Layer 2 protocol tunneling configuration from port 5/1:
Router(config-if)# no l2protocol-tunnel shutdown-threshold cdp 10
Router(config-if)# no l2protocol-tunnel shutdown-threshold stp 10
Router(config-if)# no l2protocol-tunnel shutdown-threshold vtp 10
Router(config-if)# no l2protocol-tunnel cdp
Router(config-if)# no l2protocol-tunnel stp
Router(config-if)# no l2protocol-tunnel vtp
This example shows how to clear Layer 2 protocol tunneling port counters:
Layer 2 Protocol Tunneling on EVC
Effective with Cisco IOS Release 15.3(1)S, the layer 2 protocol tunneling is supported on EVC. L2PT on EVC allows layer 2 PDUs (CDP, STP, and VTP) to be tunneled through an EVC. An ingress edge router rewrites the destination MAC address of the PDUs received on a layer 2 tunnel EVC with the Cisco proprietary multicast address (01-00-0c-cd-cd-d0). The PDU is then flooded to the bridge-domain VLAN of the layer 2 tunnel EVC port.
Restrictions for Layer 2 Protocol Tunneling on EVC
- Cisco IOS Release 15.3(1)S supports EVC on physical interfaces. Support on port-channel EVC will be introduced in the release 15.1(3)S1.
- Supports only CDP, VTP, MST (STP). Tagged protocols such as PVST and RPVST are not supported.
- Supported only on ES+ line cards.
- Only one customer per port is supported. This is because CDP, STP, and VTP are untagged, and it is not possible to distinguish packets from different customers.
- You can tunnel 1000 BPDUs per second without severely impacting the router performance.
- Configuration is allowed only on bridge domain.
- Configuration is allowed only on encapsulation default or encapsulation untagged.
- When l2protocol tunnel or l2protocol tunnel stp is configured, all the variants of STP BPDUs that ingress on the interface which has this service instance configured will be tunneled. Therefore, any features that rely on these BPDUs ingressing on this interface will not function. For instance, MST will not function for the service instances on this interface.
- You can specify (optional) a drop threshold globally using the l2protocol-tunnel global drop-threshold pps command. The drop threshold value(100-20000) determines the number of packets that should be processed for all the protocols configured on the switch. When the drop threshold exceeds, the PDUs for the protocols are dropped. This command impacts all the L2PT configurations on switch ports and EVC ports.

Note![]() When the Layer 2 protocol tunneling EVC receives an encapsulated packet, it goes to error-disabled state and remains in that state. You should either manually enable the EVC or configure automatic recovery to bring the EVC status up. You can configure the automatic recovery timer using errdisable recovery cause l2proto-tunnel time_value command to automatically bring the EVC service instance status to up once the timer expires.
When the Layer 2 protocol tunneling EVC receives an encapsulated packet, it goes to error-disabled state and remains in that state. You should either manually enable the EVC or configure automatic recovery to bring the EVC status up. You can configure the automatic recovery timer using errdisable recovery cause l2proto-tunnel time_value command to automatically bring the EVC service instance status to up once the timer expires.
Configuring Layer 2 Protocol Tunneling on EVC
SUMMARY STEPS
3.![]() interface gigabitethernet slot/port or interface tengigabitethernet slot/port
interface gigabitethernet slot/port or interface tengigabitethernet slot/port
5.![]() service instance id { ethernet [ service-name ]}
service instance id { ethernet [ service-name ]}
6.![]() encapsulation default
encapsulation default
or
encapsulation untagged
DETAILED STEPS
Configuration Examples
This example shows the configuration on Switch A. See Figure 18-1:
This example shows the configuration on Switch B. See Figure 18-1:
Verification
This example shows how to verify the configuration:
This example shows the output on a line card:
Troubleshooting Tips
|
|
|
|---|---|
You can enable debugging from the Switch Processor (SP). Use these commands for debugging: debug l2pt error : Enables L2PT error debugs. |
 Feedback
Feedback