- Preface
- Product Overview
- Configuring the Router for the First Time
- Configuring a Supervisor Engine 720
- Configuring a Route Switch Processor 720
- Configuring NSF with SSO Supervisor Engine Redundancy
- ISSU and eFSU on Cisco 7600 Series Routers
- Configuring RPR and RPR+ Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring a Supervisor Engine 32
- Configuring LAN Ports for Layer 2 Switching
- Configuring Flex Links
- Configuring EtherChannels
- Configuring VTP
- Configuring VLANs
- Configuring Private VLANs
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling
- Configuring L2TPv3
- Configuring STP and MST
- Configuring Optional STP Features
- Configuring Layer 3 Interfaces
- Configuring GTP-SLB IPV6 Support
- IP Subscriber Awareness over Ethernet
- Configuring UDE and UDLR
- Configuring Multiprotocol Label Switching on the PFC
- Configuring IPv4 Multicast VPN Support
- Configuring Multicast VPN Extranet Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast PFC3 and DFC3 Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping for IPv6 Multicast Traffic
- Configuring IGMP Snooping for IPv4 Multicast Traffic
- Configuring PIM Snooping
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VRF aware 6RD Tunnels
- Configuring VLAN ACLs
- Private Hosts (Using PACLs)
- Configuring IPv6 PACL
- IPv6 First-Hop Security Features
- Configuring Online Diagnostics
- Configuring Denial of Service Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Traffic Storm Control
- Unknown Unicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC QoS Statistics Data Export
- Configuring MPLS QoS on the PFC
- Configuring LSM MLDP based MVPN Support
- Configuring IEEE 802.1X Port-Based Authentication
- Configuring IEEE 802.1ad
- Configuring Port Security
- Configuring UDLD
- Configuring NetFlow and NDE
- Configuring Local SPAN, RSPAN, and ERSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Web Cache Services Using WCCP
- Using the Top N Utility
- Using the Layer 2 Traceroute Utility
- Configuring Bidirectional Forwarding and Detection over Switched Virtual Interface
- Configuring Call Home
- Configuring IPv6 Policy Based Routing
- Using the Mini Protocol Analyzer
- Configuring Resilient Ethernet Protocol
- Configuring Synchronous Ethernet
- Configuring Link State Tracking
- Configuring BGP PIC Edge and Core for IP and MPLS
- Configuring VRF aware IPv6 tunnels over IPv4 transport
- ISIS IPv4 Loop Free Alternate Fast Reroute (LFA FRR)
- Multicast Service Reflection
- Y.1731 Performance Monitoring
- Online Diagnostic Tests
- Acronyms
- Cisco IOS Release 15S Software Images
- Index
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 31, 2014
Chapter: Private Hosts (Using PACLs)
- Overview
- Configuration Guidelines and Limitations
- Configuring Private Hosts
- Command Reference
- private-hosts
- private-hosts mac-list
- private-hosts mode
- private-hosts promiscuous
- private-hosts vlan-list
- show fm private-hosts
- show private-hosts access-lists
- show private-hosts configuration
- show private-hosts interface configuration
- show private-hosts mac-list
- debug fm private-hosts
- debug private-hosts
Private Hosts (Using PACLs)
This chapter describes the Private Hosts feature, which is being introduced for the Cisco 7600 series router in Cisco IOS Release 12.2SRB. This chapter contains the following sections:
Overview
The Private Hosts feature provides Layer 2 (L2) isolation between the hosts in a VLAN. You can use Private Hosts as an alternative to the Private VLAN isolated-trunks feature, which is currently not available on the Cisco 7600 router.
Service Providers (SPs) worldwide face increasing demand to provide their customers with triple-play services (voice, video, and data) over a single physical interface (copper or fiber). Typically, triple-play services are delivered over three different VLANs for each user, even though the VLAN for video traffic is often shared by multiple end users.
The key benefits of the Private Hosts feature are the ability to:
- Isolate traffic among hosts (subscribers) that share the same VLAN ID
- Reuse VLAN IDs across different subscribers, which improves VLAN scalability by making better use of the 4096 VLANs allowed
- Prevent MAC spoofing to prevent denial of service (DOS) attacks
The Private Hosts feature uses port-based access control lists (PACLs) to provide Layer 2 isolation between hosts on trusted ports within a purely Layer 2 domain. The PACLs isolate the hosts by imposing Layer 2 forwarding constraints on the router ports.

Note![]() In Release 12.2SRB, PACLs are supported only as part of Private Hosts; you cannot configure your own PACLs. Instead, the router creates and applies PACLs based on your Private Hosts configuration.
In Release 12.2SRB, PACLs are supported only as part of Private Hosts; you cannot configure your own PACLs. Instead, the router creates and applies PACLs based on your Private Hosts configuration.
The sections that follow provide more detail about the following Private Hosts concepts:
- Isolating Hosts in a VLAN
- Restricting Traffic Flow (Using Private Hosts Port Mode and PACLs)
- Port ACLs
Isolating Hosts in a VLAN
Typically, triple-play services (voice, video, and data) are delivered over three different VLANs for each user, even though the VLANs for the same set of services could be shared among multiple end users. For example, if 10 end users all receive the same set of services, Private Hosts can be used to deliver the services to all of 10 end users over a single set of VLANs. However, to allow VLAN sharing, the service provider must be able to isolate traffic between the users (hosts) at Layer 2.
The Private Hosts feature provides Layer 2 isolation among hosts (end users) in a VLAN. By isolating the hosts, a service provider can use a single set of VLANs to deliver the same set of broadband or metro Ethernet services to multiple end users while ensuring that none of the hosts in the VLAN can communicate directly with each other. For example, VLAN 10 can be used for voice traffic, VLAN 20 for video traffic, and VLAN 30 for data traffic.
When the Cisco 7600 router is used as a DSLAM Gigabit Ethernet (GE) aggregator, the DSLAM is connected to the router through a trunk port that can carry data for multiple VLANs. The service provider uses a single physical port and a single set of VLANs to deliver the same set of services to different end users (isolated hosts). A separate VLAN is used for each service (voice, video, and data).
Figure 39-1 shows an example of triple-play services being delivered from the Cisco 7600 router to multiple end users attached to a DSLAM. In the figure note that:
- A single trunk link (between the router and the DSLAM) carries traffic for all three VLANs.
- Virtual circuits deliver the VLAN traffic from the DSLAM to individual end users.
Figure 39-1 VC to VLAN Mapping
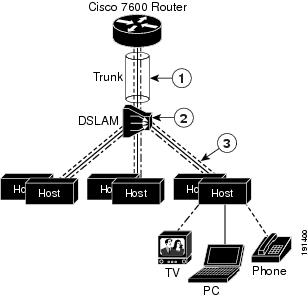
|
|
|
DSLAM maps voice, video, and data traffic between VLANs and VCs. |
|
|
|
Individual VCs carry voice, video, and data traffic between DSLAM and each host. |
Restricting Traffic Flow (Using Private Hosts Port Mode and PACLs)
The Private Hosts feature uses PACLs to restrict the type of traffic that is allowed to flow through each of the ports configured for Private Hosts. A port’s mode (specified when you enable Private Hosts on the port) determines what type of PACL is applied to the port. Each type of PACL restricts the traffic flow for a different type of traffic (for example, from content servers to isolated hosts, from isolated hosts to servers, and traffic between isolated hosts).
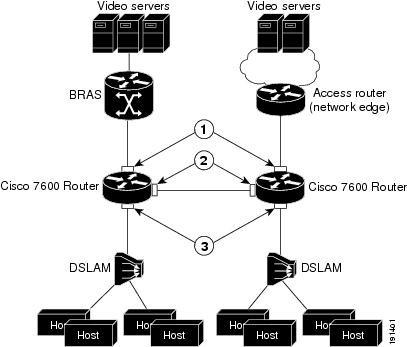
The following list describes the port modes used by the Private Hosts feature (see Figure 39-2):
- Isolated—Ports connected to the DSLAMs that the end users (isolated hosts) are connected to. The hosts on the VLANs on these ports need to be isolated from each other. Hosts connected through these ports are allowed to pass unicast traffic to upstream devices only.
- Promiscuous—Ports that face the core network or the Broadband Remote Access Server (BRAS) devices and multicast servers that are providing the broadband services.
- Mixed—Ports that interconnect Cisco 7600 routers. These ports can act as either an isolated port or a promiscuous port, depending on Spanning Tree Protocol (STP) topology changes. These ports allow unicast traffic to upstream devices (such as BRAS and multicast servers) only.
The following list summarizes how the Private Hosts feature restricts traffic flow:
- Broadcast traffic at the ingress of the service provider network is redirected to BRAS and multicast servers (such as video servers).
- All unicast traffic between access routers (Cisco 7600 routers connected to each other) is blocked except for traffic directed toward BRAS and multicast servers.
- The unknown unicast flood blocking (UUFB) feature is used to block unknown unicast traffic on DSLAM-facing ports.
Figure 39-2 shows the different types of port modes (isolated, promiscuous, and mixed) used in a Private Hosts configuration.
Figure 39-2 Private Hosts Port Types (Modes)
Port ACLs
The Private Hosts software creates several types of port ACLs (PACLs) to impose Layer 2 forwarding constraints on router ports. Each type of PACL restricts traffic flow for a particular type of traffic (for example, from content servers to isolated hosts, from isolated hosts to servers, and traffic between isolated hosts).
The software creates PACLs for the different types of Private Hosts ports based on the MAC addresses of the content servers providing broadband services and the VLAN IDs of the isolated hosts to deliver those services to. You specify the mode in which each Private Hosts port is to operate and the software applies the appropriate PACL to the port based on the port’s mode (isolated, promiscuous, or mixed).
Following are examples of the different types of PACLs that are used by the Private Hosts feature.
Following is an example of a PACL for isolated ports:
Following is an example of a PACL for promiscuous ports:
Following is an example of a PACL for mixed-mode ports:
Configuration Guidelines and Limitations
Observe the following guidelines and limitations as you configure the Private Hosts feature on Cisco 7600 routers:
- Software and hardware requirements:
- Cisco IOS Release 12.2SRB or later
- RSP720 (with PFC3C or PFC3CXL), Sup720 (with PFC3B or PFC3BXL), or Sup32
- Supported on line cards with Fast Ethernet or Gigabit Ethernet (GE) interfaces that can be configured as switch ports (for example, SIP-600, ESM-20, and 67xx LAN cards).
(Note that the SIP-400 and Enhanced FlexWAN do not support Private Hosts.) - Private Hosts and Private VLANs cannot both be configured on the same port (interface). Both features can co-exist on the router, but each feature must be configured on different ports.
- Private Hosts is an end-to-end feature. You must enable the feature on all of the routers between the DSLAMs and upstream devices like BRAS and multicast servers.
- Currently, only trusted ports can be configured as isolated ports.
- Supported on Layer 2 interfaces that are configured as switchports (802.1q or ISL trunk ports).
- Supported on port-channel interfaces (Etherchannel, FastEtherchannel, and GigabitEtherchannel). You must enable Private Hosts on the port-channel interface; you cannot enable the feature on member ports.
- LAN based features such as DAI and DHCP-snooping will not co-exist functionally on the Private Host’s port because the Private Host feature enforces a mac-based lookup at the switchport and not vlan-based. In other words, the Private Host’s vlan-list and the DAI or DHCP snooping vlan list should be mutually exclusive and should not overlap on the Private Host’s switchport.
The following protocol-independent MAC ACL restrictions also apply:
–![]() VLAN interfaces with no IP address
VLAN interfaces with no IP address
–![]() Physical LAN ports that support EoMPLS
Physical LAN ports that support EoMPLS
–![]() Logical LAN subinterfaces that support EoMPLS
Logical LAN subinterfaces that support EoMPLS
- Protocol-independent MAC ACL filtering applies MAC ACLs to all ingress traffic types (for example, IPv4 traffic, IPv6 traffic, and MPLS traffic, in addition to MAC-layer traffic).
- Ingress traffic that is permitted or denied by a protocol-independent MAC ACL is processed by egress interfaces as MAC-layer traffic. You cannot apply egress IP ACLs to traffic permitted or denied by a MAC ACL on an interface configured for protocol-independent MAC ACL filtering.
- Do not configure protocol-independent MAC ACL filtering on VLAN interfaces where you have configured an IP address.
- Do not configure protocol-independent MAC ACL filtering with microflow policing when the permitted traffic would be bridged or Layer 3 switched in hardware by the PFC3.
- Protocol-independent MAC ACL filtering supports microflow policing when the permitted traffic is routed in software by the MSFC.
The following limitations are applicable when you apply a private host to a port with only a subset of configured VLANS:
Table 39-1 PACL Scenarios and Limitations
- The following protocol-independent MAC ACL restrictions also apply from release 12.2(33) SRD4 onwards:
–![]() The Private Host feature prevents any traffic on the VLAN, which has Private Host configured, from passing directly between any two subscribers that share the VLAN.
The Private Host feature prevents any traffic on the VLAN, which has Private Host configured, from passing directly between any two subscribers that share the VLAN.
–![]() You can configure the system where one VLAN on the system operates with Private Host and cross-connect connectivity.
You can configure the system where one VLAN on the system operates with Private Host and cross-connect connectivity.
–![]() If one VLAN is configured for cross-connect and Private Host, then the configured VLAN’s cross-connect is in promiscuous mode. However, you cannot apply a ACL on the configured cross-connect when traffic is relayed from the core side.
If one VLAN is configured for cross-connect and Private Host, then the configured VLAN’s cross-connect is in promiscuous mode. However, you cannot apply a ACL on the configured cross-connect when traffic is relayed from the core side.
–![]() There is no change in scale or performance when you apply the MAC ACL restrictions.
There is no change in scale or performance when you apply the MAC ACL restrictions.
–![]() Private Host limits VPLS support for only one VLAN. If the Private Host VLAN-list already has a VPLS VLAN (VLAN with cross-connect), the addition of another VPLS VLAN is blocked. Similarly, if any VLAN in the VLAN-list has cross-connect configured, the configuration of cross-connect on another VLAN in the VLAN-list is blocked.
Private Host limits VPLS support for only one VLAN. If the Private Host VLAN-list already has a VPLS VLAN (VLAN with cross-connect), the addition of another VPLS VLAN is blocked. Similarly, if any VLAN in the VLAN-list has cross-connect configured, the configuration of cross-connect on another VLAN in the VLAN-list is blocked.

Note![]() In Release 12.2SRB, PACLs are supported only as part of Private Hosts; you cannot configure your own PACLs. Instead, the router creates and applies PACLs based on your Private Hosts configuration.
In Release 12.2SRB, PACLs are supported only as part of Private Hosts; you cannot configure your own PACLs. Instead, the router creates and applies PACLs based on your Private Hosts configuration.
The following configuration guidelines and limitations apply to access control lists (ACLs):
- 12.2 (33) SRD4 release of the Private Hosts feature uses Protocol Independent MAC ACLs.
Do not apply IP-based ACLs to any port configured for Private Hosts or you will break the Private Hosts feature (because the router will not be able to apply a Private Hosts MAC ACL to the port). - VLAN ACLs (VACLs) and port ACLs cannot both be applied to the same interface.
- Routing ACLs (RACLs) and PACLs cannot both be applied to the same interface. However, you can apply ACLs to separate interfaces.
- You can apply an ACL based IPv4 port feature on a trunk port, but it will work only if the trunk port is configured in prefer port mode. Use the access-group mode prefer port command to configure the trunk port in prefer port mode.
The following guidelines and limitations apply to VLANs:
- You can enable IGMP snooping on VLANs that use trunk ports configured for Private Hosts.
- You cannot enable IP multicast on a VLAN that uses a trunk port that is configured for Private Hosts.
- Because PACLs operate in override mode on trunk ports, you cannot apply VLAN-based features to switchports.
- The Multicast VLAN Registration (MVR) feature can co-exist with Private Hosts as long as the multicast source exists on a promiscuous port.
Interaction with Other Features
The following list describes how the Private Hosts feature interacts with other features that are configured on the router:
- Private Hosts feature does not affect Layer 2 based services such as MAC limiting, unicast flood protection (UFP), or unknown unicast flood blocking (UUFB).
- Private Hosts feature does not affect IGMP snooping. However, if IGMP snooping is globally disabled, IGMP control packets will be subject to ACL checks. To permit IGMP control packets, the Private Hosts software adds a multicast permit statement to the PACLs for isolated hosts. Note that this behavior occurs automatically and no user intervention is required.
- Port security can be enabled on isolated ports to provide added security to those ports.
- When enabled on promiscuous or mixed-mode ports, the port security feature may restrict a change in source port for upstream devices (such as BRAS or multicast servers).
- When enabled on an access port, 802.1 x is not affected by the Private Hosts.
Spoofing Protection
The Private Hosts feature prevents MAC address spoofing but does not validate the customer MAC or IP address. To prevent MAC address spoofing the Private Hosts feature:
Multicast Operation
Multicast traffic that originates from upstream devices (such as BRAS or multicast servers) is always permitted. In addition, the Private Hosts PACLs are not applied to multicast control packets (such as IGMP query and join requests). This behavior allows isolated hosts to participate in multicast groups, respond to IGMP queries, and receive traffic from any groups of interest.
Multicast traffic that originates from a host is dropped by the Private Hosts PACLs. However, if other hosts need to receive multicast traffic originating from a host, Private Hosts does the following adds a multicast permit entry to the PACLs.
Configuring Private Hosts
The following sections provide information about configuring the Private Hosts feature on a Cisco 7600 series router and instructions for configuring the feature:
Configuration Summary
This section provides a summary of the steps to perform to configure the Private Hosts feature on Cisco 7600 routers. Detailed configuration instructions follow in the next section.
1.![]() Determine which router ports (interfaces) to use for the Private Hosts feature. You can configure the feature on switchports (802.1q or ISL trunk ports) or port-channel interfaces (Etherchannel, FastEtherchannel, and GigabitEtherchannel). Note that Private Hosts must be enabled on the port-channel interface; you cannot enable the feature on member ports.
Determine which router ports (interfaces) to use for the Private Hosts feature. You can configure the feature on switchports (802.1q or ISL trunk ports) or port-channel interfaces (Etherchannel, FastEtherchannel, and GigabitEtherchannel). Note that Private Hosts must be enabled on the port-channel interface; you cannot enable the feature on member ports.
2.![]() Configure each port (interface) for normal, non-Private Hosts service. Note that you can configure the VLANs at this point or later.
Configure each port (interface) for normal, non-Private Hosts service. Note that you can configure the VLANs at this point or later.
3.![]() Determine which VLAN or set of VLANs will be used to deliver broadband services to end-users. The Private Hosts feature will provide Layer 2 isolation among the hosts in these VLANs.
Determine which VLAN or set of VLANs will be used to deliver broadband services to end-users. The Private Hosts feature will provide Layer 2 isolation among the hosts in these VLANs.
4.![]() Identify the MAC addresses of all Broadband Remote Access Servers (BRAS) and multicast servers that are being used to provide broadband services to end-users (isolated hosts).
Identify the MAC addresses of all Broadband Remote Access Servers (BRAS) and multicast servers that are being used to provide broadband services to end-users (isolated hosts).

Note![]() If a server is not connected directly to the router, determine the MAC address of the core network device that provides access to the server.
If a server is not connected directly to the router, determine the MAC address of the core network device that provides access to the server.
5.![]() (Optional) If you plan to offer different types of broadband services to different sets of isolated hosts, create multiple MAC and VLAN lists.
(Optional) If you plan to offer different types of broadband services to different sets of isolated hosts, create multiple MAC and VLAN lists.
- Each MAC address list identifies a server or set of servers providing a particular type of service.
- Each VLAN list identifies the isolated hosts where that service to be delivered.
6.![]() Configure promiscuous ports and specify a MAC and VLAN list to identify the server and receiving hosts for a particular type of service.
Configure promiscuous ports and specify a MAC and VLAN list to identify the server and receiving hosts for a particular type of service.

Note![]() You can specify multiple MAC and VLAN combinations to allow for different types of services to be delivered to different sets of hosts. For example, the BRAS at xxxx.xxxx.xxxx could be used to deliver a basic set of services over VLANs 20, 25, and 30, and the BRAS at yyyy.yyyy.yyyy could be used to deliver a premium set of services over VLANs 5, 10, and 15.
You can specify multiple MAC and VLAN combinations to allow for different types of services to be delivered to different sets of hosts. For example, the BRAS at xxxx.xxxx.xxxx could be used to deliver a basic set of services over VLANs 20, 25, and 30, and the BRAS at yyyy.yyyy.yyyy could be used to deliver a premium set of services over VLANs 5, 10, and 15.
7.![]() Globally enable Private Hosts.
Globally enable Private Hosts.
8.![]() Enable Private Hosts on individual ports (interfaces) and specify the mode in which the port is to operate. To determine port mode, you need to know whether the port faces upstream (toward content servers or core network), faces downstream (toward DSLAM and isolated hosts), or is connected to another Cisco 7600 router (typically, in a ring topology). See Restricting Traffic Flow (Using Private Hosts Port Mode and PACLs).
Enable Private Hosts on individual ports (interfaces) and specify the mode in which the port is to operate. To determine port mode, you need to know whether the port faces upstream (toward content servers or core network), faces downstream (toward DSLAM and isolated hosts), or is connected to another Cisco 7600 router (typically, in a ring topology). See Restricting Traffic Flow (Using Private Hosts Port Mode and PACLs).
After you enable the feature on individual ports, the router is ready to run the Private Hosts feature. The Private Hosts software uses the MAC and VLAN lists you defined to create the isolated, promiscuous, and mixed-mode PACLs for your configuration. The software then applies the appropriate PACL to each Private Hosts port based on the port’s mode.
Detailed Configuration Steps
Perform the following steps to configure the Private Hosts feature. Note that these steps assume that you have already configured the Layer 2 interfaces that you plan for Private Hosts. See the “Command Reference” section for detailed descriptions of the commands listed in the following table.

Note![]() You can configure Private Hosts only on switchports (802.1q or ISL trunk ports) or Etherchannel ports. In addition, you must enable Private Hosts on all of the routers between the DSLAMs and upstream devices.
You can configure Private Hosts only on switchports (802.1q or ISL trunk ports) or Etherchannel ports. In addition, you must enable Private Hosts on all of the routers between the DSLAMs and upstream devices.
|
|
|
|
|---|---|---|
Router(config)# private-hosts mac-list mac-list-name mac-address [ remark device-name | comment ] Router(config)# private-hosts mac-list BRAS_list 0000.1111.1111 remark BRAS_SanJose |
Creates a list of MAC addresses that identify the BRAS and multicast servers providing broadband services, where:
Specify the MAC address of every content server being used to deliver services. If you plan to offer different types of services to different sets of hosts, create a separate MAC list for each server or set of servers providing a particular service. Note If a server is not directly connected to the router, specify the MAC address of the core network device that provides access to the server. |
|
Router(config)# private-hosts vlan-list vlan-ids |
Creates a list of the VLANs ( vlan-ids) whose hosts need to be isolated so that the hosts can receive broadband services. Create separate VLAN lists if you plan to offer particular services to different sets of hosts. Otherwise, all of the broadband services will be delivered to all isolated hosts. |
|
Router(config)# private-hosts promiscuous mac-list-name [ vlan-list vlan-ids ] Router(config)# private-hosts promiscuous BRAS_list vlan-list 1,2,3 |
Identifies the content servers for broadband services and the end users (isolated hosts) to deliver the services to, where:
Note You can issue this command multiple times to configure multiple MAC and VLAN combinations, each defining the server and receiving hosts for a particular type of service. |
|
Selects the switchport (802.1Q or ISL trunk port) or Etherchannel port to enable for Private Hosts. |
||
Router(config-if)# private-hosts mode { promiscuous | isolated | mixed } |
Enables Private Hosts on the port. Use one of the following keywords to define the mode that the port is to operate in:
Note You must perform this step on each port being used for Private Hosts. |
|
Exits interface and global configuration modes and returns to privileged EXEC mode. Private Hosts configuration is complete. |
Configuration Examples
The following example shows the interface configuration of a Private Hosts isolated port:
The following example shows the interface configuration of a Private Hosts promiscuous port:
Command Reference
This section documents the commands related to the Private Hosts feature introduced in release 12.2(33) SRD4:
- private-hosts
- private-hosts mac-list
- private-hosts mode
- private-hosts promiscuous
- private-hosts vlan-list
- show fm private-hosts
- show private-hosts access-lists
- show private-hosts configuration
- show private-hosts interface configuration
- show private-hosts mac-list
- debug fm private-hosts
- debug private-hosts
private-hosts
To globally enable the Private Hosts feature, use the private-hosts command in global configuration mode. Use the no form of the command to disable the feature.
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Usage Guidelines
Use this command to enable Private Hosts on the router. Then, use the private-hosts mode command to enable Private Hosts on individual interfaces (ports).
Examples
The following command example globally enables the Private Hosts feature on the router:
Related Commands
private-hosts mac-list
Identifies the content servers that provide broadband services to isolated hosts and create a MAC address list, use the private-hosts mac-list command in global configuration mode. To delete an address from the MAC address list and remove that device from the list of content servers providing services for the Private Hosts feature, use the no form of the command.
private-hosts mac-list mac-list-name mac-address [ remark device-name | comment ]
no private-hosts mac-list mac-list-name mac-address
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Usage Guidelines
This command creates a list of MAC addresses that identify the content servers being used to provide broadband services to isolated hosts in the Private Hosts configuration.
Use this command to specify the MAC address of every content server that provides broadband services for the Private Hosts feature. A content server is any Broadband Remote Access Server (BRAS), multicast server, or video server that provides services to the isolated hosts in your network.
You can assign all the content servers to a single MAC address list, or you can create multiple MAC address lists, each identifying the content server providing a particular type of broadband service or set of services. When you configure the promiscuous ports for Private Hosts, you specify a MAC address list and VLAN list to identify the server and receiving hosts for broadband services.

Note![]() The MAC address list is automatically deleted when the last address in the list is deleted.
The MAC address list is automatically deleted when the last address in the list is deleted.
Examples
This example creates a MAC address list named BRAS_list that identifies the MAC address of the upstream BRAS. The optional remark indicates that the BRAS is in San Jose.
Related Commands
|
|
|
|---|---|
Displays a list of the MAC addresses that identify the content servers that are providing broadband defined for Private Hosts. |
private-hosts mode
To enable Private Hosts on an interface (port) and specify the mode in which the port is to operate, use the private-hosts mode command in interface configuration mode. Use the no form of the command to disable Private Hosts on the port.
private-hosts mode { promiscuous | isolated | mixed }
Syntax Description
Defaults
This command is disabled by default.
The default for mode is promiscuous.
Command Modes
Interface configuration (switchport or port-channel)
Command History
|
|
|
|---|---|
Usage Guidelines
Before you use this command, you must globally enable the Private Hosts feature on the router by issuing the private-hosts command.
Use this command to enable the Private Hosts feature on individual ports and to define the mode of operation for the port. A port’s mode determines which type of PACL is assigned to the port in order to restrict the type of traffic that is allowed to pass through the port. Each type of PACL restricts the traffic flow for a different type of traffic (for example, from content servers to isolated hosts, from isolated hosts to servers, and traffic between isolated hosts). Use the show private-hosts interface configuration command to display the mode assigned to Private Hosts ports.
Examples
The following command example enables Private Hosts on an interface (port) and configures the port for isolated mode:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for individual interfaces. |
private-hosts promiscuous
To identify the content servers and receiving hosts that provide broadband services, use the private-hosts promiscuous command in global configuration mode. Use the no form of the command to remove a promiscuous ports setting.
private-hosts promiscuous mac-list-name [ vlan vlan-ids ]
no private-hosts promiscuous mac-list-name
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Usage Guidelines
The MAC address list and the VLAN list define the content servers and receiving hosts that provide broadband services. If no VLAN list is specified, the system uses the global VLAN list created with the private-hosts vlan-list command.
You can issue this command multiple times to specify multiple combinations of MAC and VLAN lists, each defining the server and receiving hosts for a particular type of service. For example, the BRAS at xxxx.xxxx.xxxx could be used to deliver a basic set of services over VLANs 20, 25, and 30, and the BRAS at yyyy.yyyy.yyyy could be used to deliver a premium set of services over VLANs 5, 10, and 15.
Examples
The following command example configures the broadband services provided by content servers defined in the BRAS_list address list, to be delivered to isolated hosts in VLANs 10, 12, 15, and 200 through 300:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for the router. |
|
Displays Private Hosts configuration information for individual interfaces. |
private-hosts vlan-list
Identifies the VLANs whose hosts need to be isolated from each other (so that the VLANs can be used to deliver broadband services), use the private-hosts vlan-list command in global configuration mode. Use the no form of the command to remove a VLAN from the list of VLANs requiring host isolation.
private-hosts vlan-list vlan-ids
no private-hosts vlan-list vlan-ids
Syntax Description
A list of the VLANs whose hosts need to be isolated from each other. Use commas to separate individual VLANs or specify a range of VLANs (for example, 1,3,5,20-25). |
Defaults
Command Modes
Command History
|
|
|
|---|---|
Usage Guidelines
This command creates a list of VLANs whose hosts need to be isolated through the Private Hosts feature. The VLAN list should include all of the VLANs that are being used to deliver broadband services to multiple end-users (isolated hosts).
If you plan to deliver different types of broadband services to different sets of hosts, you can create multiple VLAN lists and multiple MAC address lists. When you configure promiscuous ports, you can specify different combinations of MAC and VLAN lists to identify content servers and receiving hosts for each type of service.
If you do not specify a VLAN list when you configure promiscuous ports, the system uses the global VLAN list created by this command.

Note![]() The Private Hosts feature isolates the hosts in all VLANs included in the VLAN lists; therefore, VLAN lists should include only those VLANs that are being used to deliver broadband services.
The Private Hosts feature isolates the hosts in all VLANs included in the VLAN lists; therefore, VLAN lists should include only those VLANs that are being used to deliver broadband services.
Examples
This command configures the Private Hosts feature to isolate the hosts in VLANs 10, 12, 15, and 200 through 300:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for the router. |
show fm private-hosts
To display information about the Private Hosts feature manager, use the show fm private-hosts command in privileged EXEC mode.
show fm private-hosts { all | interface intf }
Syntax Description
Displays the feature manager information for all of the interfaces that are configured for Private Hosts. |
|
Specifies the interface where the feature manager information is displayed. |
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for the router. |
|
Displays Private Hosts configuration information for individual interfaces. |
show private-hosts access-lists
To display the access lists for a Private Hosts configuration, use the show private-hosts access-lists command in privileged EXEC mode.
show private-hosts access-lists
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows how to display the Private Hosts access lists for the customized configuration:
Related Commands
show private-hosts configuration
To display information about the Private Hosts configuration on the router, use the show private-hosts configuration command in privileged EXEC mode.
show private-hosts configuration
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for individual interfaces. |
show private-hosts interface configuration
To display information about the Private Hosts configuration on individual interfaces (ports), use the show private-hosts interface configuration command in privileged EXEC mode.
show private-hosts interface configuration
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
Displays Private Hosts configuration information for the router. |
show private-hosts mac-list
To display the contents of the MAC address lists defined for Private Hosts, use the show private-hosts mac-list command in privileged EXEC mode.
show private-hosts mac-list [ list-name ]
Syntax Description
(Optional) The name of the MAC address list whose contents you want to display. |
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
Creates a MAC address list that identifies a content server that is being used to provide broadband services to isolated hosts. |
debug fm private-hosts
To enable debug messages for the Private Hosts feature manager, use the debug fm private-hosts command in privileged EXEC mode.
debug fm private-hosts { all | vmr | unusual | events }
Syntax Description
Enables debug messages for all Private Hosts errors and events. |
|
Enables debug messages for the Multicast VLAN Registration (MVR) feature. |
|
Enables debug messages for unexpected Private Hosts behavior. |
|
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
debug private-hosts
To enable debug messages for the Private Hosts feature, use the debug private-hosts command in privileged EXEC mode.
debug private-hosts { all | events | acl | api }
Syntax Description
Defaults
Command Modes
Command History
|
|
|
|---|---|
Examples
The following example shows sample command output:
Related Commands
|
|
|
|---|---|
Enables debug messages for the Private Hosts feature manager. |
 Feedback
Feedback