- Preface
- Product Overview
- Configuring the Router for the First Time
- Configuring a Supervisor Engine 720
- Configuring a Route Switch Processor 720
- Configuring NSF with SSO Supervisor Engine Redundancy
- ISSU and eFSU on Cisco 7600 Series Routers
- Configuring RPR and RPR+ Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring a Supervisor Engine 32
- Configuring LAN Ports for Layer 2 Switching
- Configuring Flex Links
- Configuring EtherChannels
- Configuring VTP
- Configuring VLANs
- Configuring Private VLANs
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling
- Configuring L2TPv3
- Configuring STP and MST
- Configuring Optional STP Features
- Configuring Layer 3 Interfaces
- Configuring GTP-SLB IPV6 Support
- IP Subscriber Awareness over Ethernet
- Configuring UDE and UDLR
- Configuring Multiprotocol Label Switching on the PFC
- Configuring IPv4 Multicast VPN Support
- Configuring Multicast VPN Extranet Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast PFC3 and DFC3 Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping for IPv6 Multicast Traffic
- Configuring IGMP Snooping for IPv4 Multicast Traffic
- Configuring PIM Snooping
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VRF aware 6RD Tunnels
- Configuring VLAN ACLs
- Private Hosts (Using PACLs)
- Configuring IPv6 PACL
- IPv6 First-Hop Security Features
- Configuring Online Diagnostics
- Configuring Denial of Service Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Traffic Storm Control
- Unknown Unicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC QoS Statistics Data Export
- Configuring MPLS QoS on the PFC
- Configuring LSM MLDP based MVPN Support
- Configuring IEEE 802.1X Port-Based Authentication
- Configuring IEEE 802.1ad
- Configuring Port Security
- Configuring UDLD
- Configuring NetFlow and NDE
- Configuring Local SPAN, RSPAN, and ERSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Web Cache Services Using WCCP
- Using the Top N Utility
- Using the Layer 2 Traceroute Utility
- Configuring Bidirectional Forwarding and Detection over Switched Virtual Interface
- Configuring Call Home
- Configuring IPv6 Policy Based Routing
- Using the Mini Protocol Analyzer
- Configuring Resilient Ethernet Protocol
- Configuring Synchronous Ethernet
- Configuring Link State Tracking
- Configuring BGP PIC Edge and Core for IP and MPLS
- Configuring VRF aware IPv6 tunnels over IPv4 transport
- ISIS IPv4 Loop Free Alternate Fast Reroute (LFA FRR)
- Multicast Service Reflection
- Y.1731 Performance Monitoring
- Online Diagnostic Tests
- Acronyms
- Cisco IOS Release 15S Software Images
- Index
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 31, 2014
Chapter: Configuring Optional STP Features
- Understanding How PortFast Works
- Understanding How BPDU Guard Works
- Understanding How PortFast BPDU Filtering Works
- Understanding How UplinkFast Works
- Understanding How BackboneFast Works
- Understanding How EtherChannel Guard Works
- Understanding How Root Guard Works
- Understanding How Loop Guard Works
- Enabling PortFast
- Enabling PortFast BPDU Filtering
- Enabling BPDU Guard
- Enabling UplinkFast
- Enabling BackboneFast
- Enabling EtherChannel Guard
- Enabling Root Guard
- Enabling Loop Guard
Configuring Optional STP Features
This chapter describes how to configure optional STP features.

Note For complete syntax and usage information for the commands used in this chapter, refer to the Cisco 7600 Series Routers Command References at this URL:
http://www.cisco.com/en/US/products/hw/routers/ps368/prod_command_reference_list.html
This chapter consists of these sections:
- Understanding How PortFast Works
- Understanding How BPDU Guard Works
- Understanding How PortFast BPDU Filtering Works
- Understanding How UplinkFast Works
- Understanding How BackboneFast Works
- Understanding How EtherChannel Guard Works
- Understanding How Root Guard Works
- Understanding How Loop Guard Works
- Enabling PortFast
- Enabling PortFast BPDU Filtering
- Enabling BPDU Guard
- Enabling UplinkFast
- Enabling BackboneFast
- Enabling EtherChannel Guard
- Enabling Root Guard
- Enabling Loop Guard

Note![]() For information on configuring the spanning tree protocol (STP), see Chapter20, “Configuring STP and MST”
For information on configuring the spanning tree protocol (STP), see Chapter20, “Configuring STP and MST”
Understanding How PortFast Works
STP PortFast causes a Layer 2 LAN port configured as an access port to enter the forwarding state immediately, bypassing the listening and learning states. You can use PortFast on Layer 2 access ports connected to a single workstation or server to allow those devices to connect to the network immediately, instead of waiting for STP to converge. Interfaces connected to a single workstation or server should not receive bridge protocol data units (BPDUs). When configured for PortFast, a port is still running the spanning tree protocol. A PortFast enabled port can immediately transition to the blocking state if necessary (this could happen on receipt of a superior BPDU). PortFast can be enabled on trunk ports. PortFast can have an operational value that is different from the configured value.

Understanding How BPDU Guard Works
When enabled on a port, BPDU Guard shuts down a port that receives a BPDU. When configured globally, BPDU Guard is only effective on ports in the operational PortFast state. In a valid configuration, PortFast Layer 2 LAN interfaces do not receive BPDUs. Reception of a BPDU by a PortFast Layer 2 LAN interface signals an invalid configuration, such as connection of an unauthorized device. BPDU Guard provides a secure response to invalid configurations, because the administrator must manually put the Layer 2 LAN interface back in service. BPDU Guard can be configured at the interface level. When configured at the interface level, BPDU Guard shuts the port down as soon as the port receives a BPDU, regardless of the PortFast configuration.

Note![]() When enabled globally, BPDU Guard applies to all interfaces that are in an operational PortFast state.
When enabled globally, BPDU Guard applies to all interfaces that are in an operational PortFast state.
Understanding How PortFast BPDU Filtering Works
PortFast BPDU filtering allows the administrator to prevent the system from sending or even receiving BPDUs on specified ports.
When configured globally, PortFast BPDU filtering applies to all operational PortFast ports. Ports in an operational PortFast state are supposed to be connected to hosts, that typically drop BPDUs. If an operational PortFast port receives a BPDU, it immediately loses its operational PortFast status. In that case, PortFast BPDU filtering is disabled on this port and STP resumes sending BPDUs on this port.
PortFast BPDU filtering can also be configured on a per-port basis. When PortFast BPDU filtering is explicitly configured on a port, it does not send any BPDUs and drops all BPDUs it receives.

When you enable PortFast BPDU filtering globally and set the port configuration as the default for PortFast BPDU filtering (see the “Enabling PortFast BPDU Filtering” section), then PortFast enables or disables PortFast BPDU filtering.
If the port configuration is not set to default, then the PortFast configuration will not affect PortFast BPDU filtering. Table 21-1 lists all the possible PortFast BPDU filtering combinations. PortFast BPDU filtering allows access ports to move directly to the forwarding state as soon as the end hosts are connected.
|
|
|
|
|
|---|---|---|---|
Enable1 |
|||
|
1.The port transmits at least 10 BPDUs. If this port receives any BPDUs, then PortFast and PortFast BPDU filtering are disabled. |
Understanding How UplinkFast Works
UplinkFast provides fast convergence after a direct link failure and achieves load balancing between redundant Layer 2 links using uplink groups. An uplink group is a set of Layer 2 LAN interfaces (for each VLAN), only one of which is forwarding at any given time. Specifically, an uplink group consists of the root port (which is forwarding) and a set of blocked ports, except for self-looping ports. The uplink group provides an alternate path in case the currently forwarding link fails.

Note![]() UplinkFast is most useful in wiring-closet switches. This feature may not be useful for other types of applications.
UplinkFast is most useful in wiring-closet switches. This feature may not be useful for other types of applications.
Figure 21-1 shows an example topology with no link failures. Switch A, the root bridge, is connected directly to Switch B over link L1 and to Switch C over link L2. The Layer 2 LAN interface on Switch C that is connected directly to Switch B is in the blocking state.
Figure 21-1 UplinkFast Example Before Direct Link Failure
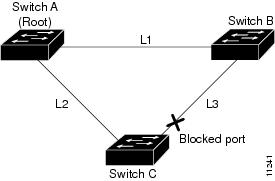
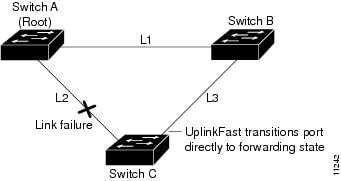
If Switch C detects a link failure on the currently active link L2 on the root port (a direct link failure), UplinkFast unblocks the blocked port on Switch C and transitions it to the forwarding state without going through the listening and learning states, as shown in Figure 21-2. This switchover takes approximately one to five seconds.
Figure 21-2 UplinkFast Example After Direct Link Failure
Understanding How BackboneFast Works
BackboneFast is initiated when a root port or blocked port on a network device receives inferior BPDUs from its designated bridge. An inferior BPDU identifies one network device as both the root bridge and the designated bridge. When a network device receives an inferior BPDU, it indicates that a link to which the network device is not directly connected (an indirect link) has failed (that is, the designated bridge has lost its connection to the root bridge). Under normal STP rules, the network device ignores inferior BPDUs for the configured maximum aging time, as specified by the STP max-age command.
The network device tries to determine if it has an alternate path to the root bridge. If the inferior BPDU arrives on a blocked port, the root port and other blocked ports on the network device become alternate paths to the root bridge. (Self-looped ports are not considered alternate paths to the root bridge.) If the inferior BPDU arrives on the root port, all blocked ports become alternate paths to the root bridge. If the inferior BPDU arrives on the root port and there are no blocked ports, the network device assumes that it has lost connectivity to the root bridge, causes the maximum aging time on the root to expire, and becomes the root bridge according to normal STP rules.
If the network device has alternate paths to the root bridge, it uses these alternate paths to transmit a new kind of Protocol Data Unit (PDU) called the Root Link Query PDU. The network device sends the Root Link Query PDU out all alternate paths to the root bridge. If the network device determines that it still has an alternate path to the root, it causes the maximum aging time to expire on the ports on which it received the inferior BPDU. If all the alternate paths to the root bridge indicate that the network device has lost connectivity to the root bridge, the network device causes the maximum aging times on the ports on which it received an inferior BPDU to expire. If one or more alternate paths can still connect to the root bridge, the network device makes all ports on which it received an inferior BPDU its designated ports and moves them out of the blocking state (if they were in the blocking state), through the listening and learning states, and into the forwarding state.
Figure 21-3 shows an example topology with no link failures. Switch A, the root bridge, connects directly to Switch B over link L1 and to Switch C over link L2. The Layer 2 LAN interface on Switch C that connects directly to Switch B is in the blocking state.
Figure 21-3 BackboneFast Example Before Indirect Link Failure

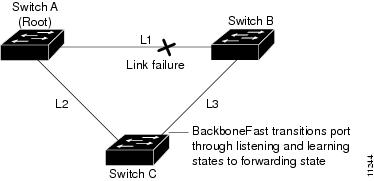
If link L1 fails, Switch C cannot detect this failure because it is not connected directly to link L1. However, because Switch B is directly connected to the root bridge over L1, it detects the failure and elects itself the root and begins sending BPDUs to Switch C indicating itself as the root. When Switch C receives the inferior BPDUs from Switch B, Switch C infers that an indirect failure has occurred. At that point, BackboneFast allows the blocked port on Switch C to move immediately to the listening state without waiting for the maximum aging time for the port to expire. BackboneFast then transitions the Layer 2 LAN interface on Switch C to the forwarding state, providing a path from Switch B to Switch A. This switchover takes approximately 30 seconds, twice the Forward Delay time if the default Forward Delay time of 15 seconds is set. Figure 21-4 shows how BackboneFast reconfigures the topology to account for the failure of link L1.
Figure 21-4 BackboneFast Example After Indirect Link Failure
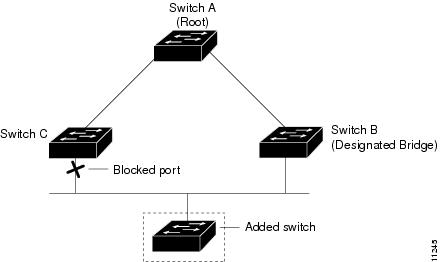
If a new network device is introduced into a shared-medium topology as shown in Figure 21-5, BackboneFast is not activated because the inferior BPDUs did not come from the recognized designated bridge (Switch B). The new network device begins sending inferior BPDUs that indicate that it is the root bridge. However, the other network devices ignore these inferior BPDUs and the new network device learns that Switch B is the designated bridge to Switch A, the root bridge.
Figure 21-5 Adding a Network Device in a Shared-Medium Topology
Understanding How EtherChannel Guard Works
EtherChannel guard detects a misconfigured EtherChannel where interfaces on the Cisco 7600 series router are configured as an EtherChannel while interfaces on the other device are not or not all the interfaces on the other device are in the same EtherChannel.
In response to misconfiguration detected on the other device, EtherChannel guard puts interfaces on the Cisco 7600 series router into the errdisabled state.
Understanding How Root Guard Works
The STP root guard feature prevents a port from becoming root port or blocked port. If a port configured for root guard receives a superior BPDU, the port immediately goes to the root-inconsistent (blocked) state.
Understanding How Loop Guard Works
Loop guard helps prevent bridging loops that could occur because of a uni-directional link failure on a point-to-point link. When enabled globally, the loop guard applies to all point-to-point ports on the system. Loop guard detects root ports and blocked ports and ensures that they keep receiving BPDUs from their designated port on the segment. If a loop guard enabled root or blocked port stop a receiving BPDUs from its designated port, it transitions to the loop-inconsistent blocking state, assuming there is a physical link error on this port. The port recovers from this loop-inconsistent state as soon as it receives a BPDU.
You can enable loop guard on a per-port basis. When you enable loop guard, it is automatically applied to all of the active instances or VLANs to which that port belongs. When you disable loop guard, it is disabled for the specified ports. Disabling loop guard moves all loop-inconsistent ports to the listening state.
If you enable loop guard on a channel and the first link becomes unidirectional, loop guard blocks the entire channel until the affected port is removed from the channel. Figure 21-6 shows loop guard in a triangle router configuration.
Figure 21-6 Triangle Switch Configuration with Loop Guard
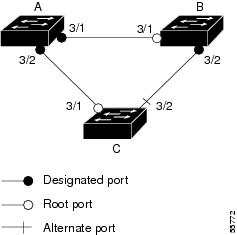
Figure 21-6 illustrates the following configuration:
- Switches A and B are distribution switches.
- Switch C is an access router.
- Loop guard is enabled on ports 3/1 and 3/2 on Switches A, B, and C.
Enabling loop guard on a root router has no effect but provides protection when a root router becomes a nonroot router.
When using loop guard, follow these guidelines:
- You cannot enable loop guard on PortFast-enabled ports.
- You cannot enable loop guard if root guard is enabled.
Loop guard interacts with other features as follows:
- Loop guard does not affect the functionality of UplinkFast or BackboneFast.
- Enabling loop guard on ports that are not connected to a point-to-point link will not work.
- Root guard forces a port to be always designated as the root port. Loop guard is effective only if the port is a root port or an alternate port. You cannot enable loop guard and root guard on a port at the same time.
- Loop guard uses the ports known to spanning tree. Loop guard can take advantage of logical ports provided by the Port Aggregation Protocol (PAgP). However, to form a channel, all the physical ports grouped in the channel must have compatible configurations. PAgP enforces uniform configurations of root guard or loop guard on all the physical ports to form a channel.
These caveats apply to loop guard:
–![]() Spanning tree always chooses the first operational port in the channel to send the BPDUs. If that link becomes unidirectional, loop guard blocks the channel, even if other links in the channel are functioning properly.
Spanning tree always chooses the first operational port in the channel to send the BPDUs. If that link becomes unidirectional, loop guard blocks the channel, even if other links in the channel are functioning properly.
–![]() If a set of ports that are already blocked by loop guard are grouped together to form a channel, spanning tree loses all the state information for those ports and the new channel port may obtain the forwarding state with a designated role.
If a set of ports that are already blocked by loop guard are grouped together to form a channel, spanning tree loses all the state information for those ports and the new channel port may obtain the forwarding state with a designated role.
–![]() If a channel is blocked by loop guard and the channel breaks, spanning tree loses all the state information. The individual physical ports may obtain the forwarding state with the designated role, even if one or more of the links that formed the channel are unidirectional.
If a channel is blocked by loop guard and the channel breaks, spanning tree loses all the state information. The individual physical ports may obtain the forwarding state with the designated role, even if one or more of the links that formed the channel are unidirectional.

Note You can enable UniDirectional Link Detection (UDLD) to help isolate the link failure. A loop may occur until UDLD detects the failure, but loop guard will not be able to detect it.
Enabling PortFast

To enable PortFast on a Layer 2 access port, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface { type 2 slot/port } | { port-channel port_channel_number } |
||
Enables PortFast on a Layer 2 access port connected to a single workstation or server. |
||
Router# show running interface { type 1 slot/port } | { port-channel port_channel_number } |
|
2.type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
This example shows how to enable PortFast on Fast Ethernet interface 5/8:
This example shows how to verify the configuration:
To enable the default PortFast configuration, perform this task:
|
|
|
|
|---|---|---|
This example shows how to enable the default PortFast configuration:
Enabling PortFast BPDU Filtering
These sections describe how to configure PortFast BPDU filtering.
To enable PortFast BPDU filtering globally, perform this task:
|
|
|
|
|---|---|---|
BPDU filtering is set to default on each port. This example shows how to enable PortFast BPDU filtering on the port and verify the configuration in PVST+ mode:

Note![]() For PVST+ information, see Chapter20, “Configuring STP and MST”
For PVST+ information, see Chapter20, “Configuring STP and MST”
To enable PortFast BPDU filtering on a nontrunking port, perform this task:
|
|
|
|
|---|---|---|
This example shows how to enable PortFast BPDU filtering on a nontrunking port:
Enabling BPDU Guard
To enable BPDU Guard globally, perform this task:
|
|
|
|
|---|---|---|
This example shows how to enable BPDU Guard:
This example shows how to verify the configuration:
Enabling UplinkFast
UplinkFast increases the bridge priority to 49152 and adds 3000 to the STP port cost of all Layer 2 LAN interfaces on the Cisco 7600 series router, decreasing the probability that the router will become the root bridge. The max_update_rate value represents the number of multicast packets transmitted per second (the default is 150 packets per second). UplinkFast cannot be enabled on VLANs that have been configured for bridge priority. To enable UplinkFast on a VLAN with bridge priority configured, restore the bridge priority on the VLAN to the default value by entering a no spanning-tree vlan vlan_ID priority command in global configuration mode.

Note![]() When you enable UplinkFast, it affects all VLANs on the Cisco 7600 series router. You cannot configure UplinkFast on an individual VLAN.
When you enable UplinkFast, it affects all VLANs on the Cisco 7600 series router. You cannot configure UplinkFast on an individual VLAN.
To enable UplinkFast, perform this task:
|
|
|
|
|---|---|---|
Router(config)# spanning-tree uplinkfast [ max-update-rate max_update_rate ] |
||
This example shows how to enable UplinkFast with an update rate of 400 packets per second:
This example shows how to verify that UplinkFast is enabled:
Enabling BackboneFast

Note![]() BackboneFast operates correctly only when enabled on all network devices in the network. BackboneFast is not supported on Token Ring VLANs. This feature is supported for use with third-party network devices.
BackboneFast operates correctly only when enabled on all network devices in the network. BackboneFast is not supported on Token Ring VLANs. This feature is supported for use with third-party network devices.
To enable BackboneFast, perform this task:
|
|
|
|
|---|---|---|
This example shows how to enable BackboneFast:
This example shows how to verify that BackboneFast is enabled:
Enabling EtherChannel Guard
To enable EtherChannel guard, perform this task:
|
|
|
|
|---|---|---|
Router(config)# no spanning-tree etherchannel guard misconfig |
||
This example shows how to enable EtherChannel guard:
This example shows how to verify the configuration:
To display the interfaces that are in the errdisable state, enter the show interface status err-disable command.
After the misconfiguration has been cleared, interfaces in the errdisable state might automatically recover. To manually return a port to service, enter a shutdown and then a no shutdown command for the interface.
Enabling Root Guard
To enable root guard, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface { type 3 slot/port } | { port-channel port_channel_number } |
||
| Router# show running interface { type 1 slot/port } | { port-channel port_channel_number } |
|
3.type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
To display ports that are in the root-inconsistent state, enter the show spanning-tree inconsistentports command.
Enabling Loop Guard
To enable loop guard globally on the router, perform this task:
|
|
|
|
|---|---|---|
This example shows how to enable loop guard globally:
To enable loop guard on a port, perform this task:
|
|
|
|
|---|---|---|
Router(config)# interface { type 4 slot/port } | { port-channel port_channel_number } |
||
|
4.type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
This example shows how to enable loop guard:
This example shows how to verify the configuration:
 Feedback
Feedback