Overview
Add rules to the policy to allow traffic through the firewall.
If you created a basic Block all traffic access control policy when you registered the firewall, then you need to add rules to the policy to allow traffic through the firewall. The access control policy can include multiple rules that are evaluated in order.
This procedure creates an access control rule to allow all traffic from the inside zone to the outside zone.
Procedure
| 1. | Choose , and click Edit ( |
|
| 2. | Click Add Rule, and set the following parameters. 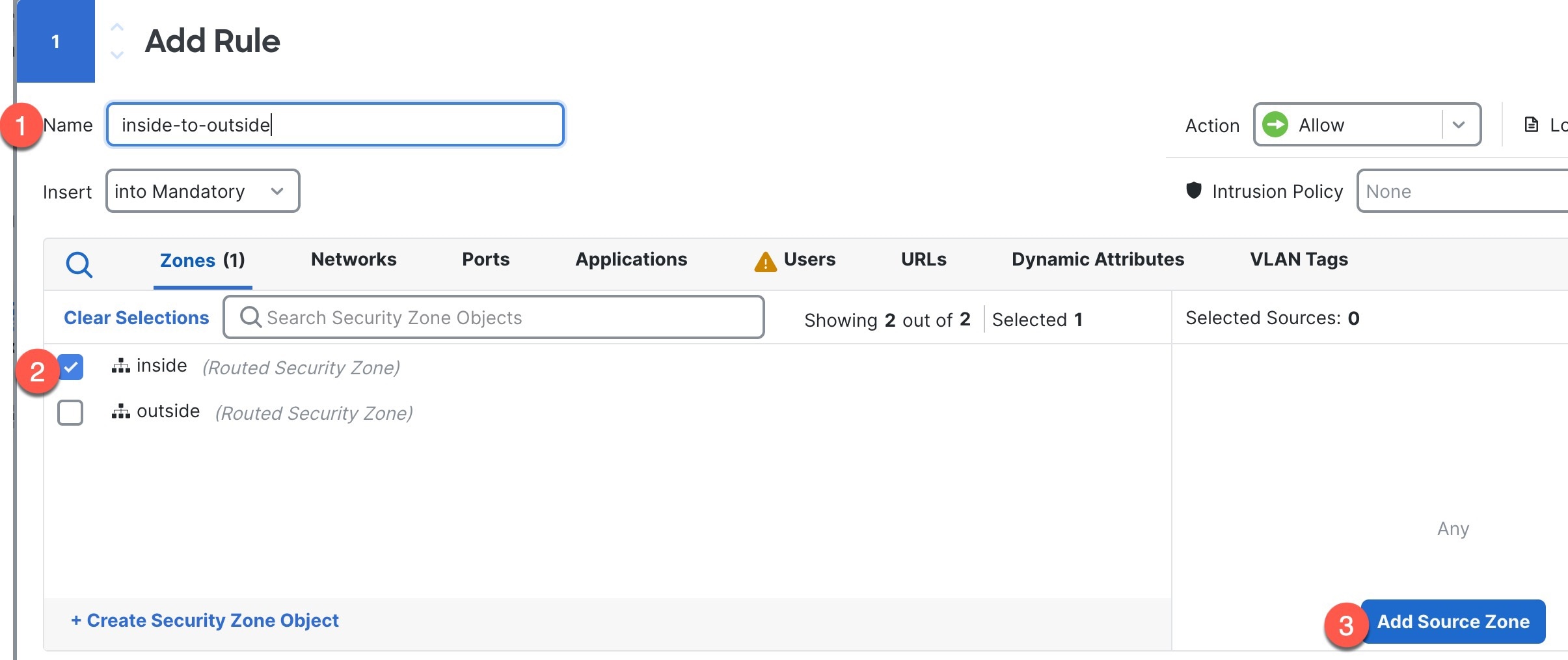
1. Name this rule, for example, inside-to-outside. 2. Select the inside zone from Zones 3. Click Add Source Zone. 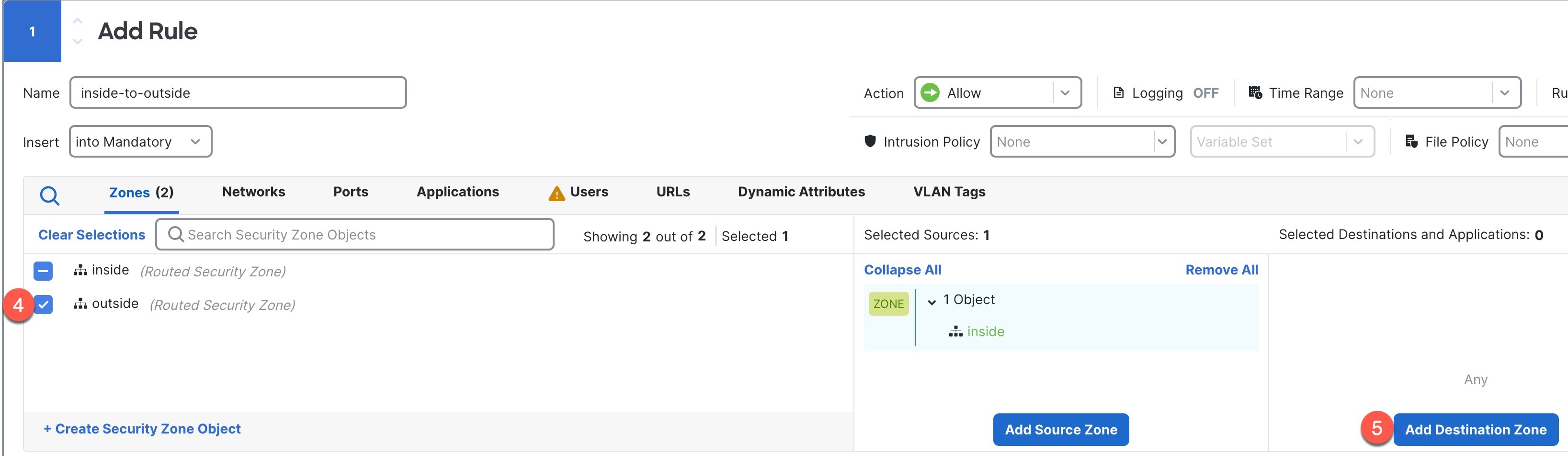
4. Select the outside zone from Zones. 5. Click Add Destination Zone. Leave the other settings as is. |
|
| 3. | (Optional) Customize associated policies by clicking on the policy type in the packet flow diagram. Prefilter, Decryption, Security Intelligence, and Identity policies are applied before an access control rule. Customizing these policies is not required, but after you know your network's needs, they let you improve network performance by either fastpathing trusted traffic (bypassing processing) or blocking traffic so no further processing is required. 
|
|
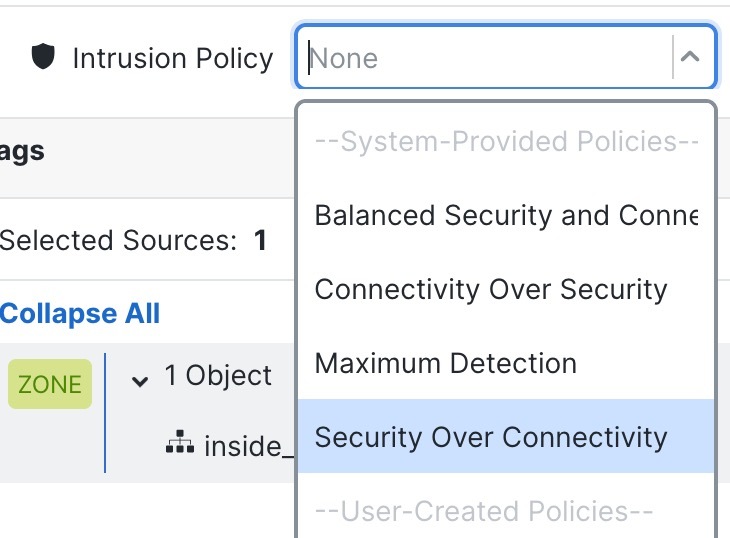
| 4. | (Optional) Add an Intrusion policy that is applied after the access control rule. The Intrusion policy is a defined set of intrusion detection and prevention configurations that inspects traffic for security violations. The Firewall Management Center includes many system-provided policies you can enable as-is or that you can customize. This step enables a system-provided policy. |
|
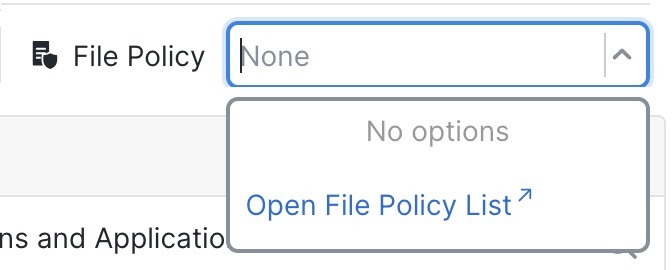
| 5. | (Optional) Add a File policy that is applied after the access control rule. |
|
| 6. | Click Apply. The rule is added to the Rules table. |
|
| 7. | Click Save. |