Connectivity Issues Between Connector and Cisco Spaces
Procedure
|
Step 1 |
Log in to the connector GUI. |
||||||||||
|
Step 2 |
In the connector left navigation pane, click Troubleshoot and do one of the following:
|
||||||||||
|
Step 3 |
Click Run New Test to initiate troubleshooting the connectivity. |
||||||||||
|
Step 4 |
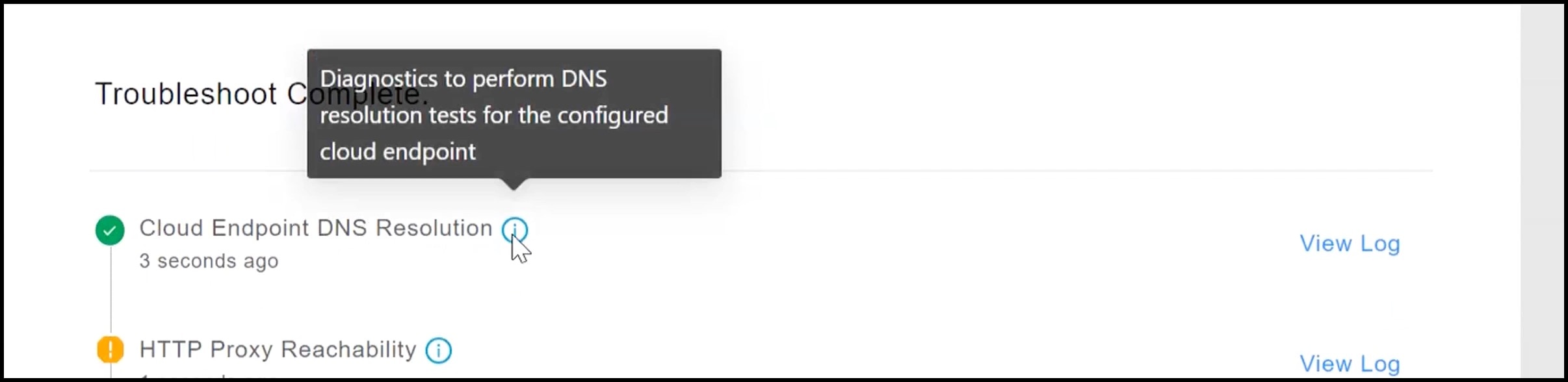
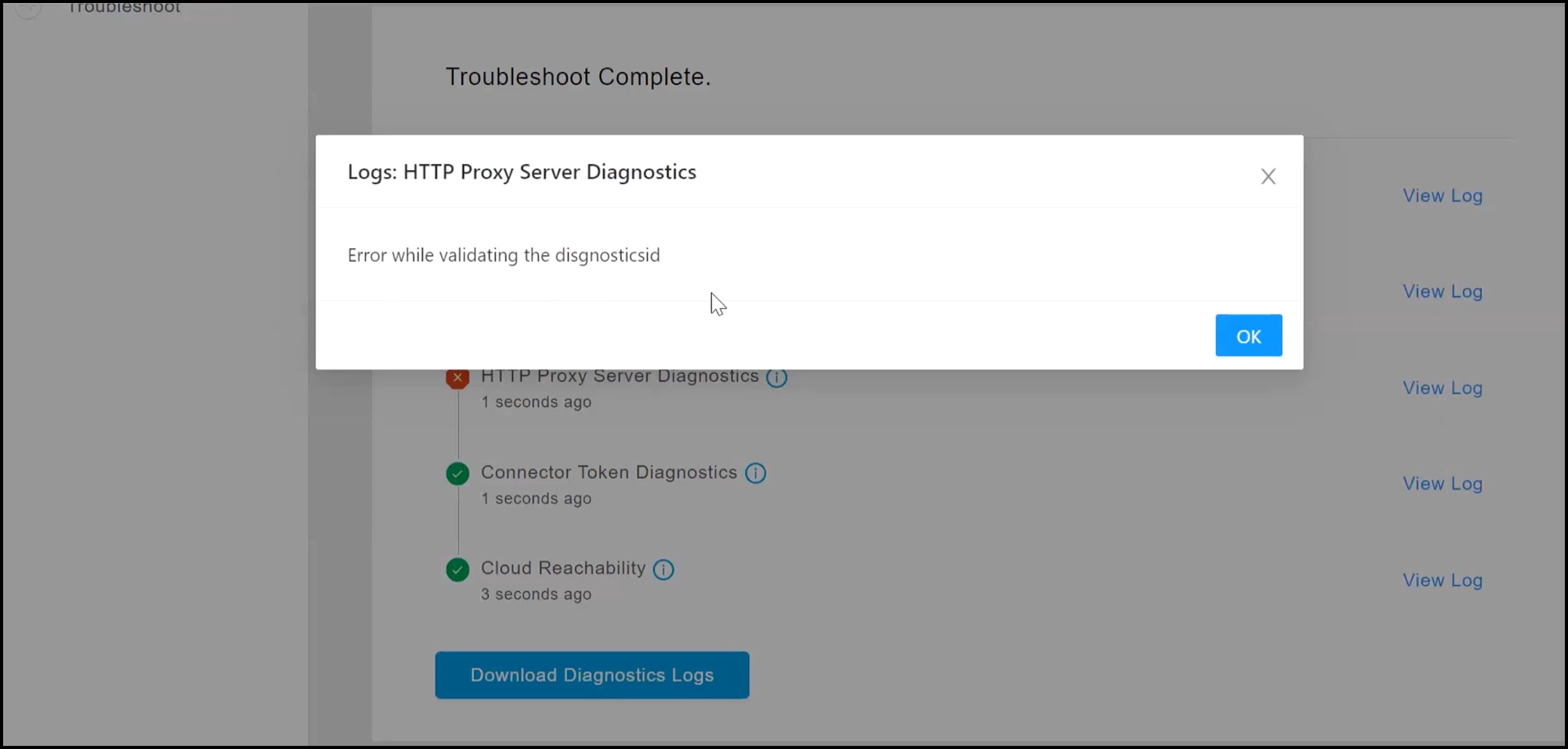
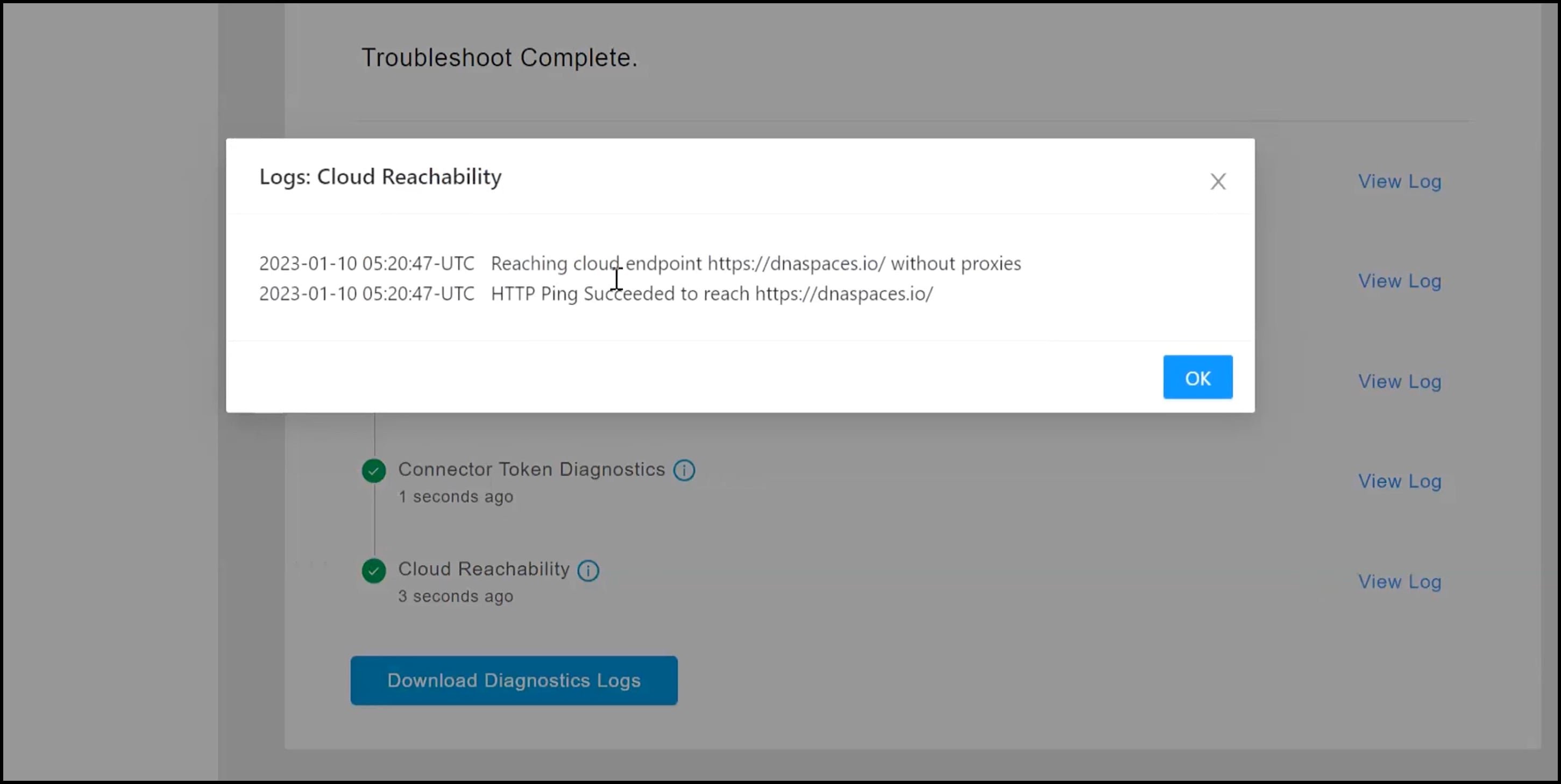
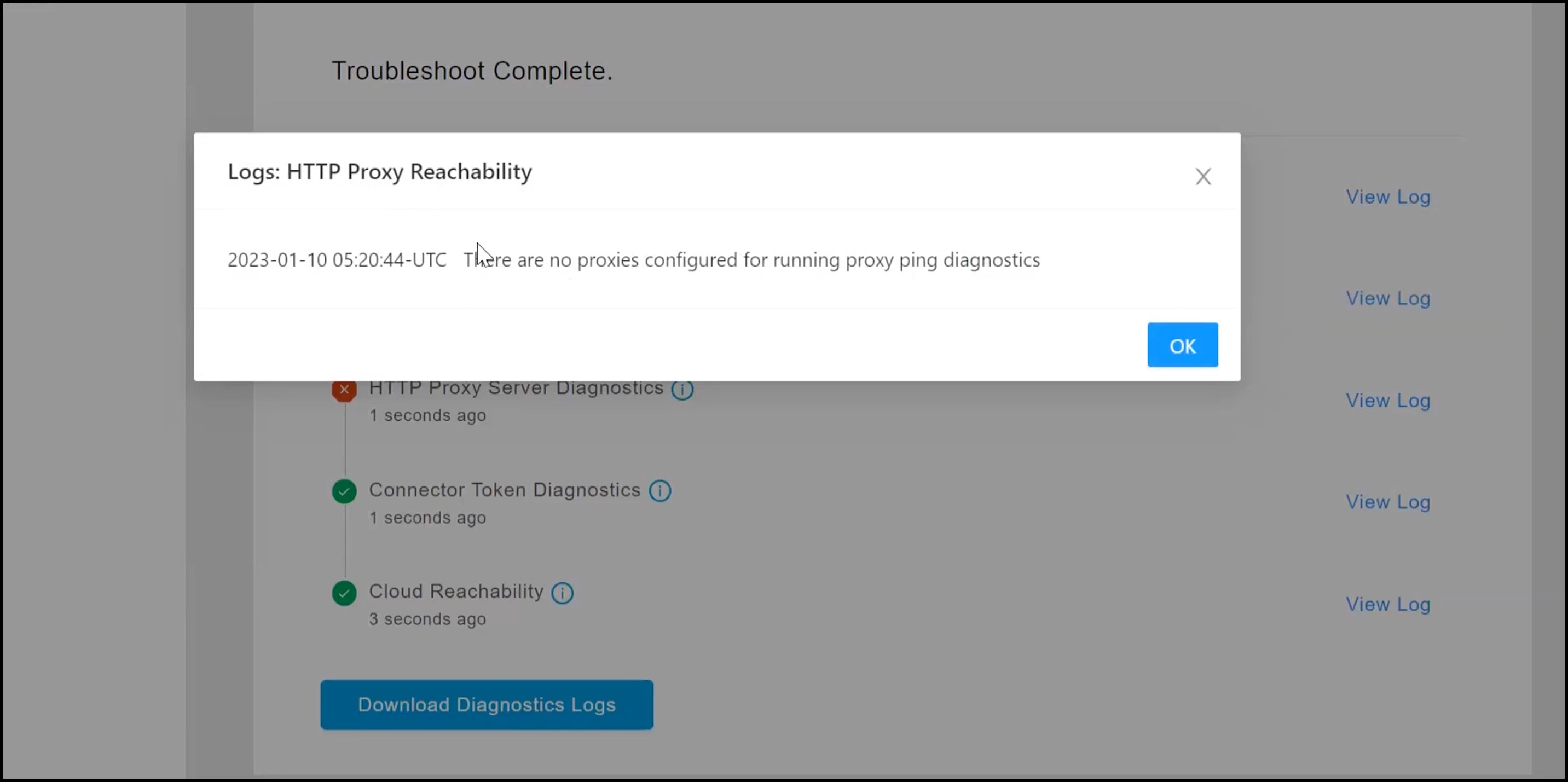
Observe the running tests for the following:
|
||||||||||
|
Step 5 |
Click Download Diagnostic Logs to download a text file with details of logs, including diagnostic information. 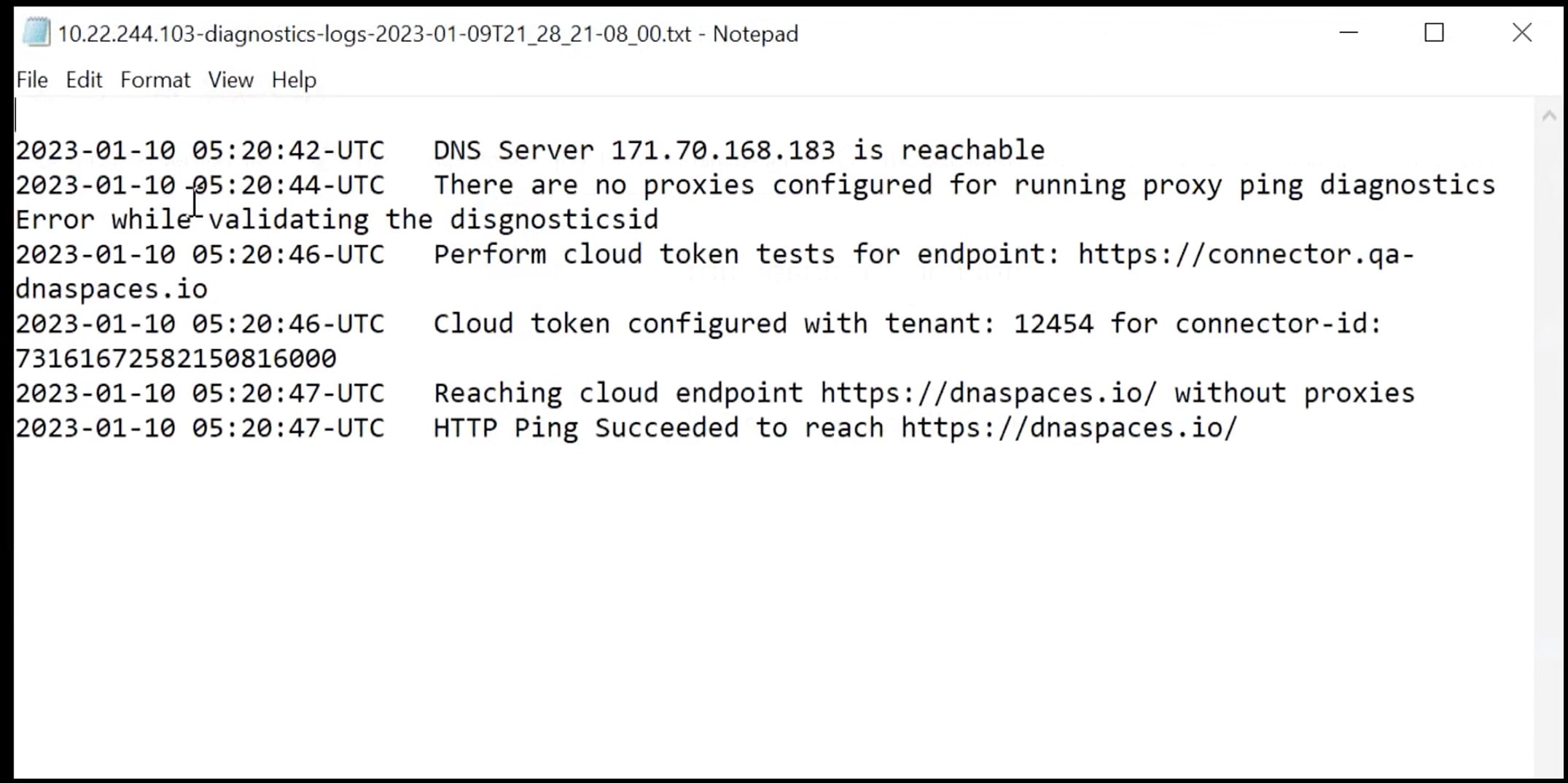
|
 Feedback
Feedback