Configure and Test the Connection Between Connector and Catalyst 9800 Controller
Before you begin
-
Deploy a connector OVA and activate it using a token from Cisco Spaces.
-
Note down the IP address of a Catalyst 9800 controller that is reachable from the Cisco Spaces: Connector.
-
On the Catalyst 9800 controller CLI, enter the config mode and enable AAA with local authentication using the aaa authorization exec default local and aaa authentication login default local commands.
On the Catalyst 9800 controller CLI, run the following command in the enable mode: show run | sec aaaFrom the output that is displayed, copy the configuration for aaa authorization exec default. In the config mode, append the configuration for local authentication to the copied configuration and configure the appended configuration.
For instance, if the output displays aaa authorization exec default group dnac-network-tacacs-group, the appended configuration is aaa authorization exec default group dnac-network-tacacs-group local. This ensures that the existing configuration is not overwritten.
 Note |
Any certificate imported to the controller for Wireless Management Interface(WMI) that has been signed with a signature algorithm weaker than SHA-256 is not supported. Verify your certificate before adding the controller using the show wireless management trustpoint command.
|
Procedure
|
Step 1 |
Login to Cisco Spaces. |
|||||||||||||||
|
Step 2 |
In the Cisco Spaces dashboard, choose Setup > Wireless Networks. |
|||||||||||||||
|
Step 3 |
Expand the Connect via Spaces Connector area using the respective drop-down arrow to display a list of steps. |
|||||||||||||||
|
Step 4 |
To test the connectivity from the Connector to an existing Catalyst 9800 controller, click View Controllers in the Step 3 Area.
|
|||||||||||||||
|
Step 5 |
To add a new Catalyst 9800 controller, click Add Controllers from the Step 3 Area. 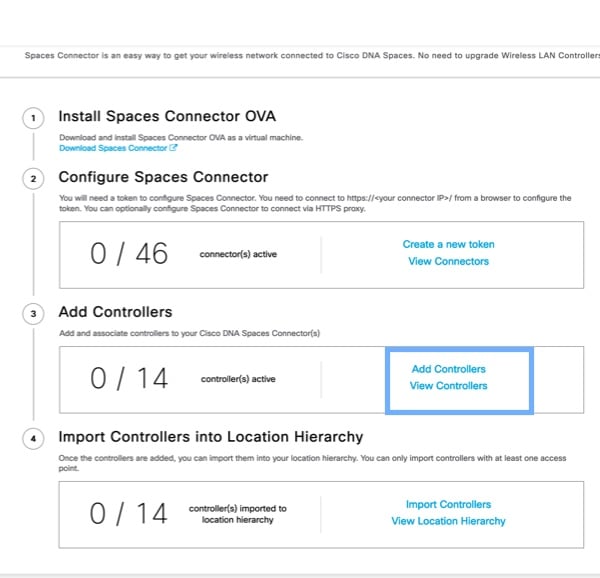
|
|||||||||||||||
|
Step 6 |
From the Connector drop-down list, choose a Connector. |
|||||||||||||||
|
Step 7 |
Enter the Controller IP address, Controller Name, and from the Controller Type drop-down list, choose Catalyst WLC to connect to a Cisco Catalyst 9800 Series Wireless Controllers.
|
|||||||||||||||
|
Step 8 |
Do one of the following:
|
|||||||||||||||
|
Step 9 |
(Optional) Run the PING and SSH functionalities to test the reachability to the Catalyst 9800 controller and the credentials by clicking Test Connectivity. Note that Test Connectivity is available only for an active Connector. 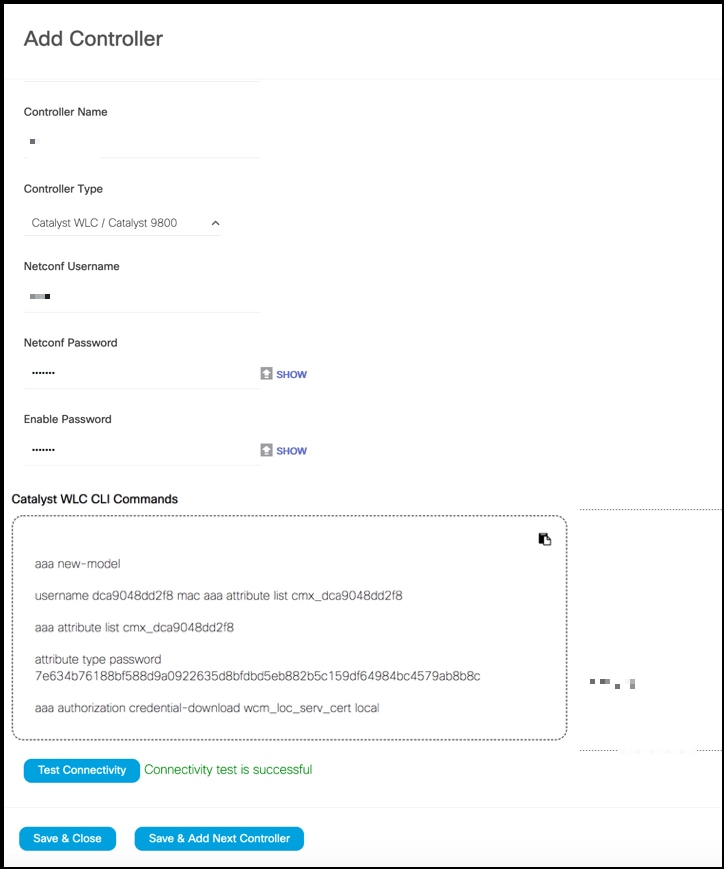
|
|||||||||||||||
|
Step 10 |
Click Save, and then click Close. 
|
You can multiple Catalyst 9800 controllers to a Connector.
 Feedback
Feedback