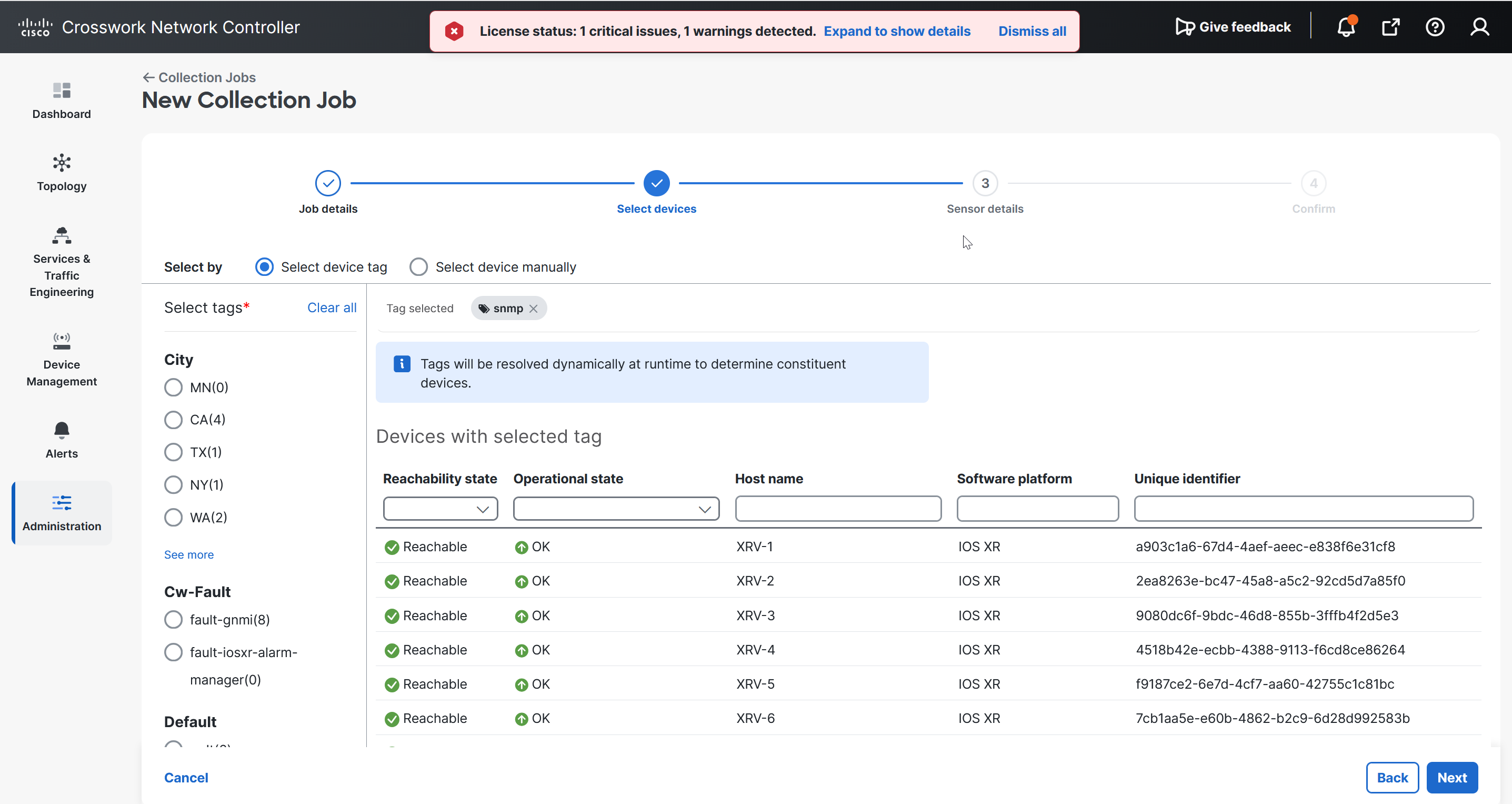
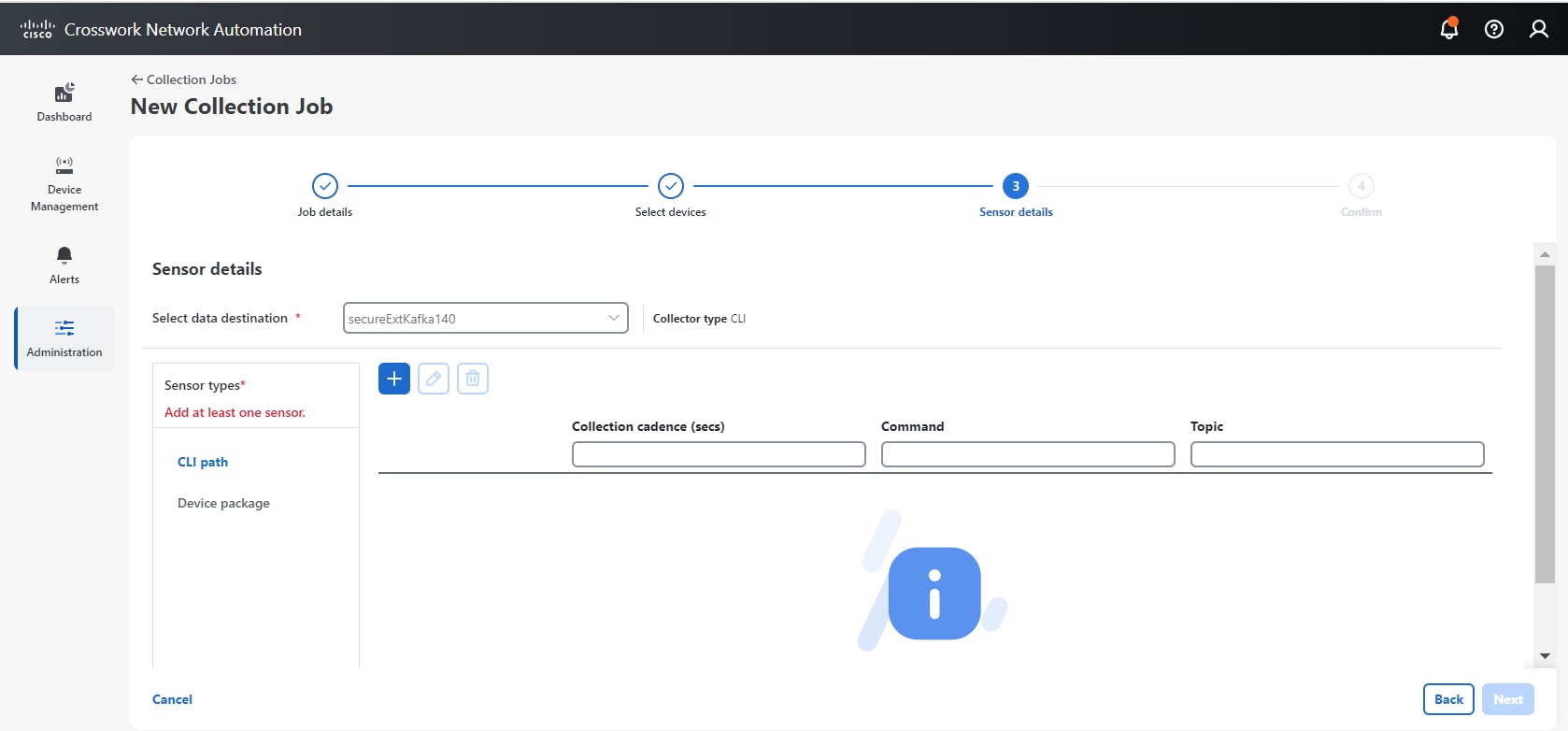
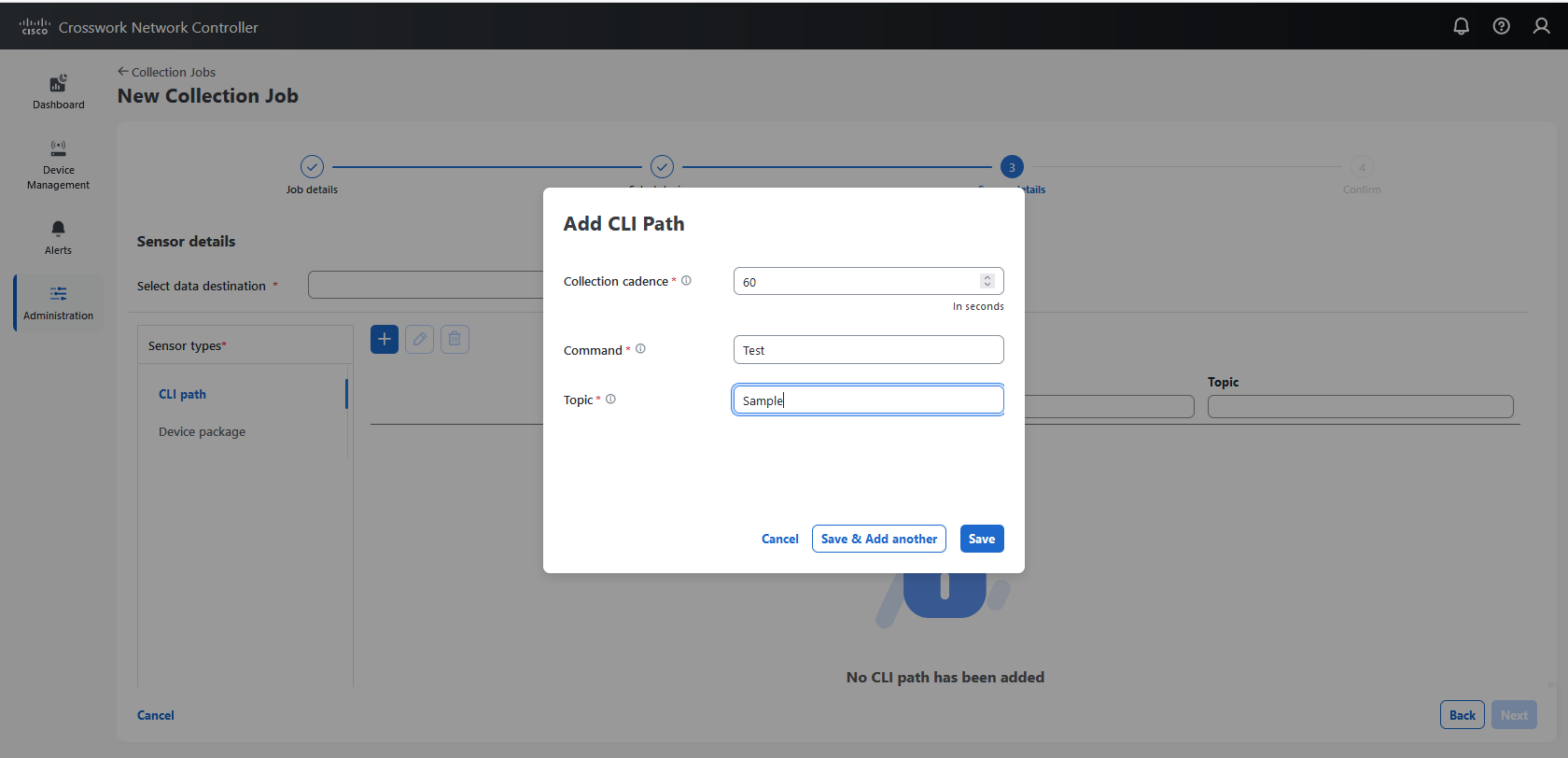
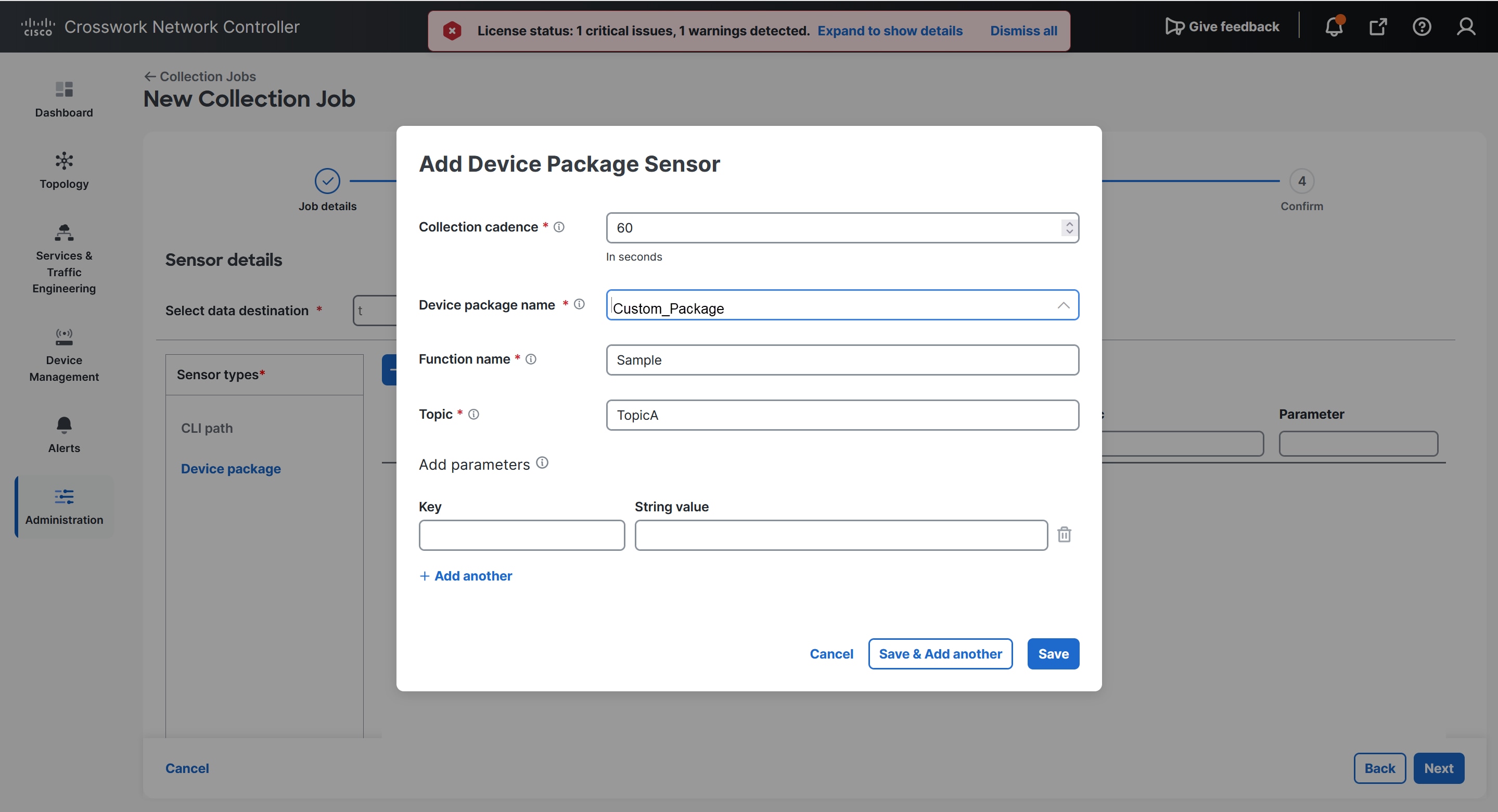
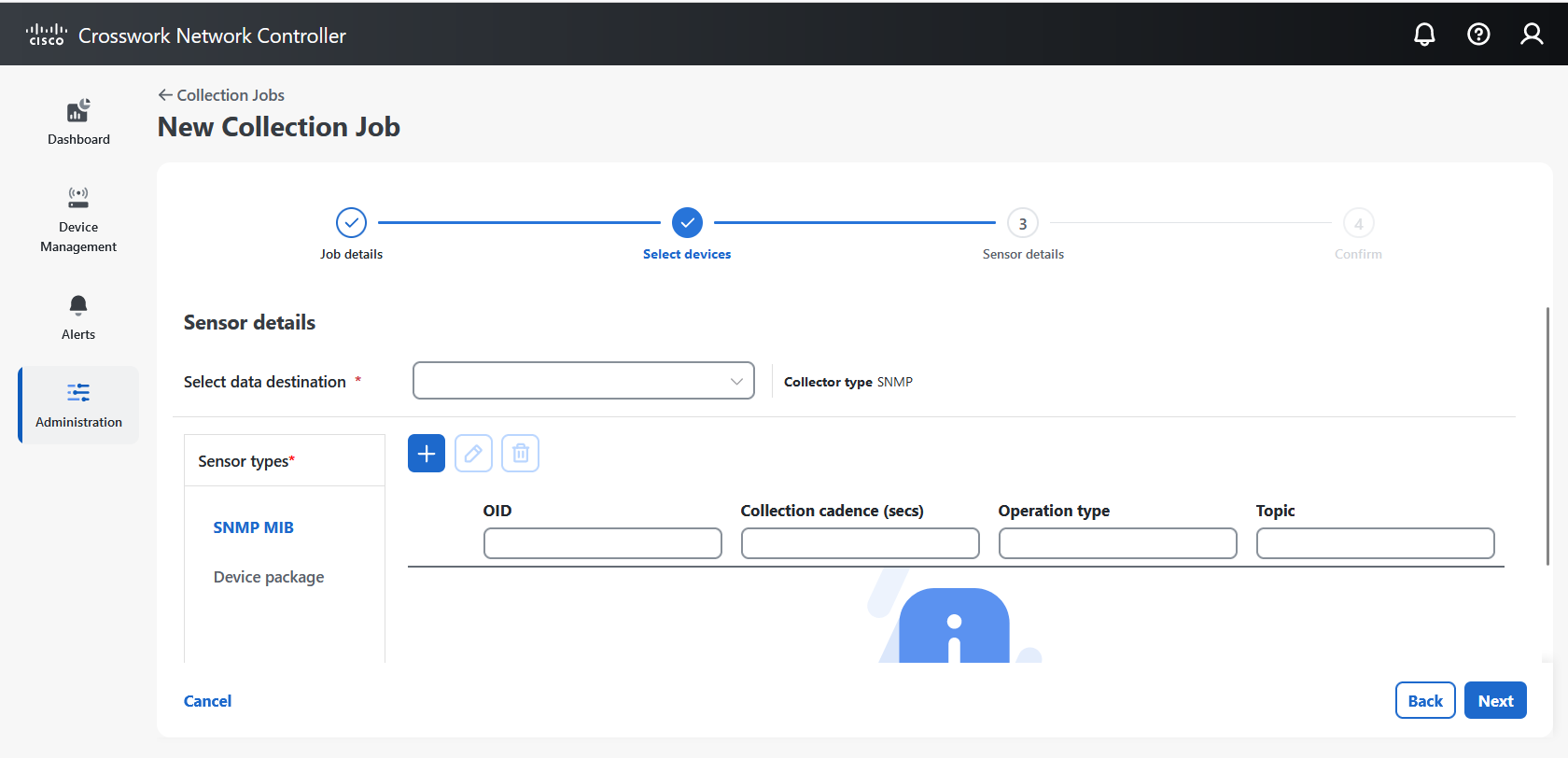
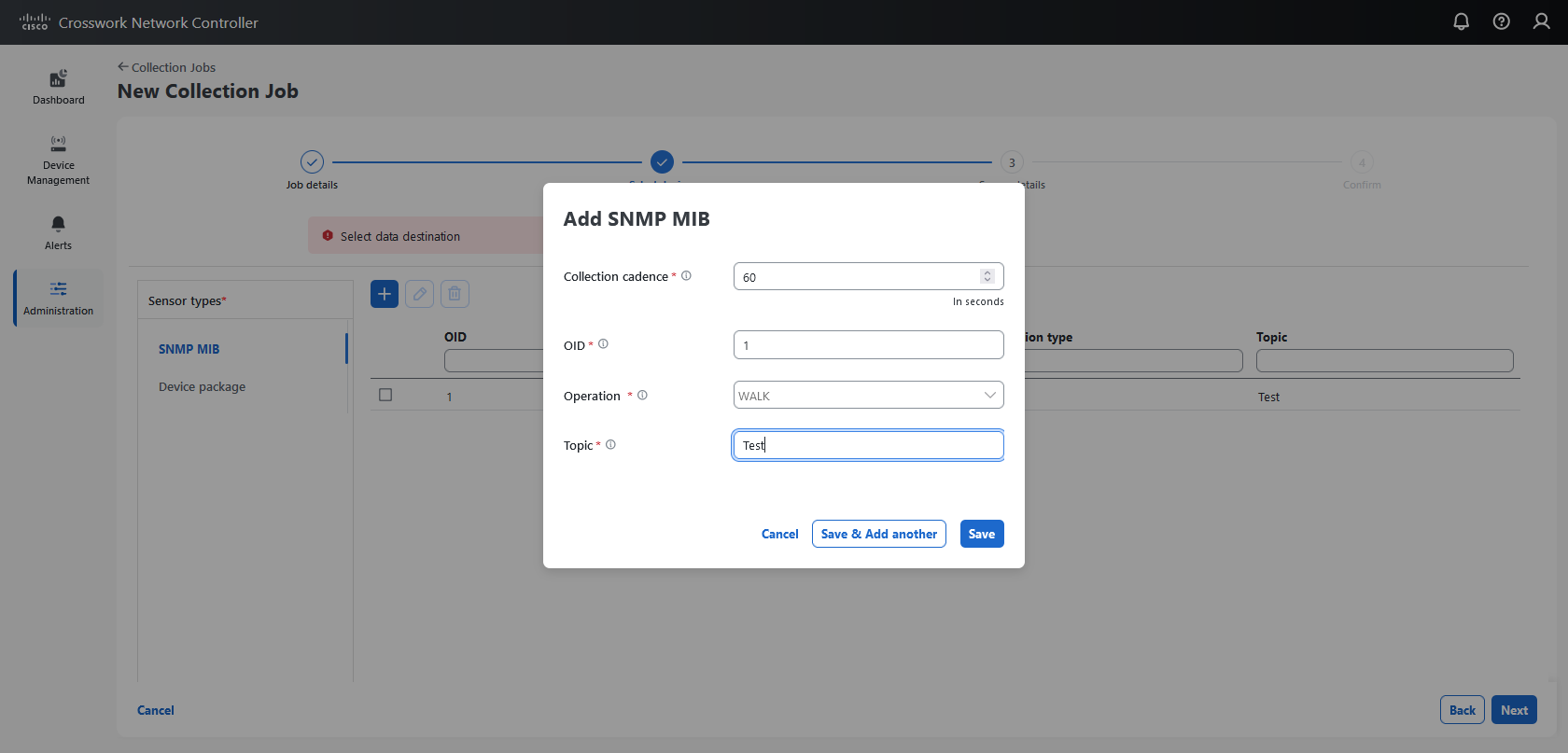
Enabling SNMP traps to forward to external applications
We recommend enabling only the necessary traps on the device. You can identify trap types in the received data by matching
OIDs (OBJECT_IDENTIFIER), for example oid
1.3.6.1.6.3.1.1.4.1.0 and strValue associated to the oid in the OidRecords. The application matches the OID of interest to determine the trap type.
These are sample values and a sample payload to forward traps to external applications:
Table 11. Non-YANG and OID traps
| Trap type |
OID value |
|
Link Up
|
1.3.6.1.6.3.1.1.4.1.0 = 1.3.6.1.6.3.1.1.5.4 |
|
Link Down
|
1.3.6.1.6.3.1.1.4.1.0 = 1.3.6.1.6.3.1.1.5.3 |
|
Syslog
|
1.3.6.1.6.3.1.1.4.1.0 = 1.3.6.1.4.1.9.9.41.2.0.1 |
|
Cold start
|
1.3.6.1.6.3.1.1.4.1.0 = 1.3.6.1.6.3.1.1.5.1 |
{
"nodeIdStr": "BF5-XRV9K1.tr3.es",
"nodeIdUuid": "C9tZ5lJoSJKf5OZ67+U5JQ==",
"collectionId": "133",
"collectionStartTime": "1580931985267",
"msgTimestamp": "1580931985267",
"dataGpbkv": [
{
"timestamp": "1580931985267",
"name": "trapsensor.path",
"snmpTrap": {
"version": "V2c",
"pduType": "TRAP",
"v2v3Data": {
"agentAddress": "172.70.39.227",
"oidRecords": [
{
"oid": "1.3.6.1.2.1.1.3.0",
"strValue": "7 days, 2:15:17.02"
},
{
"oid": "1.3.6.1.6.3.1.1.4.1.0", // This oid is the Object Identifier.
"strValue": "1.3.6.1.6.3.1.1.5.3" // This is the value that determines the kind of trap.
},
{
"oid": "1.3.6.1.2.1.2.2.1.1.8",
"strValue": "8"
},
{
"oid": "1.3.6.1.2.1.2.2.1.2.8",
"strValue": "GigabitEthernet0/0/0/2"
},
{
"oid": "1.3.6.1.2.1.2.2.1.3.8",
"strValue": "6"
},
{
"oid": "1.3.6.1.4.1.9.9.276.1.1.2.1.3.8",
"strValue": "down"
}
]
}
}
}
],
"collectionEndTime": "1580931985267",
"collectorUuid": "YmNjZjEzMTktZjFlOS00NTE5LWI4OTgtY2Y1ZmQxZDFjNWExOlRSQVBfQ09MTEVDVE9S",
"status": {
"status": "SUCCESS"
},
"modelData": {},
"sensorData": {
"trapSensor": {
"path": "1.3.6.1.6.3.1.1.5.4"
}
},
"applicationContexts": [
{
"applicationId": "APP1",
"contextId": "collection-job-snmp-traps"
}
]
}
A sample payload illustrates trap forwarding with relevant OID records and their corresponding string values.
{
"collection_job": {
"application_context": {
"context_id": "collection-job1",
"application_id": "APP1"
},
"collection_mode": {
"lifetime_type": "APPLICATION_MANAGED",
"collector_type": "SNMP_COLLECTOR"
},
"job_device_set": {
"device_set": {
"devices": {
"device_ids": [
"c70fc034-0cbd-443f-ad3d-a30d4319f937",
"8627c130-9127-4ed7-ace5-93d3b4321d5e",
"c0067069-c8f6-4183-9e67-1f2e9bf56f58"
]
}
}
},
"sensor_input_configs": [
{
"sensor_data": {
"snmp_sensor": {
"snmp_mib": {
"oid": "1.3.6.1.2.1.1.3.0",
"snmp_operation": "SCALAR"
}
}
},
"cadence_in_millisec": "60000"
},
{
"sensor_data": {
"snmp_sensor": {
"snmp_mib": {
"oid": "1.3.6.1.2.1.31.1.1",
"snmp_operation": "TABLE"
}
}
},
"cadence_in_millisec": "60000"
}
],
"sensor_output_configs": [
{
"sensor_data": {
"snmp_sensor": {
"snmp_mib": {
"oid": "1.3.6.1.2.1.1.3.0",
"snmp_operation": "SCALAR"
}
}
},
"destination": {
"destination_id": "4c2ab662-2670-4b3c-b7d3-b94acba98c56",
"context_id": "topic1_461cb8aa-a16a-44b8-b79f-c3daf3ea925f"
}
},
{
"sensor_data": {
"snmp_sensor": {
"snmp_mib": {
"oid": "1.3.6.1.2.1.31.1.1",
"snmp_operation": "TABLE"
}
}
},
"destination": {
"destination_id": "4c2ab662-2670-4b3c-b7d3-b94acba98c56",
"context_id": "topic2_e7ed6300-fc8c-47ee-8445-70e543057f8a"
}
}
]
}
}

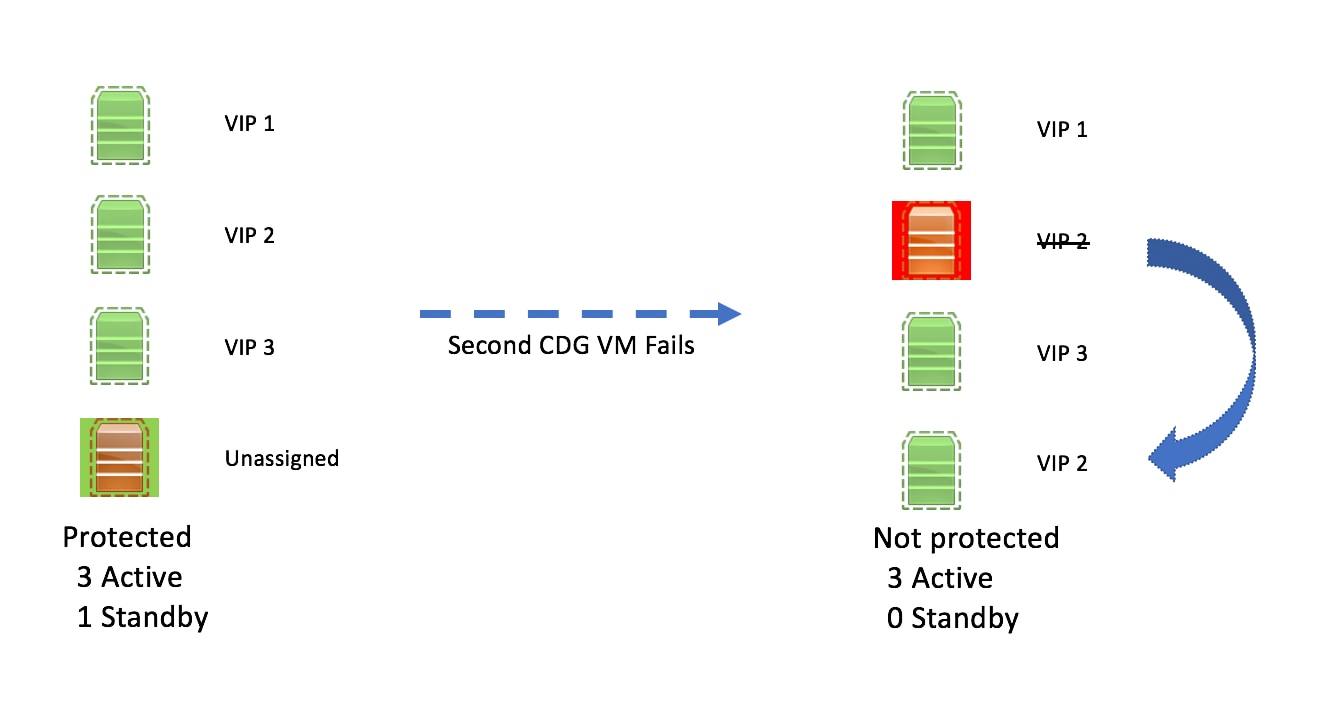
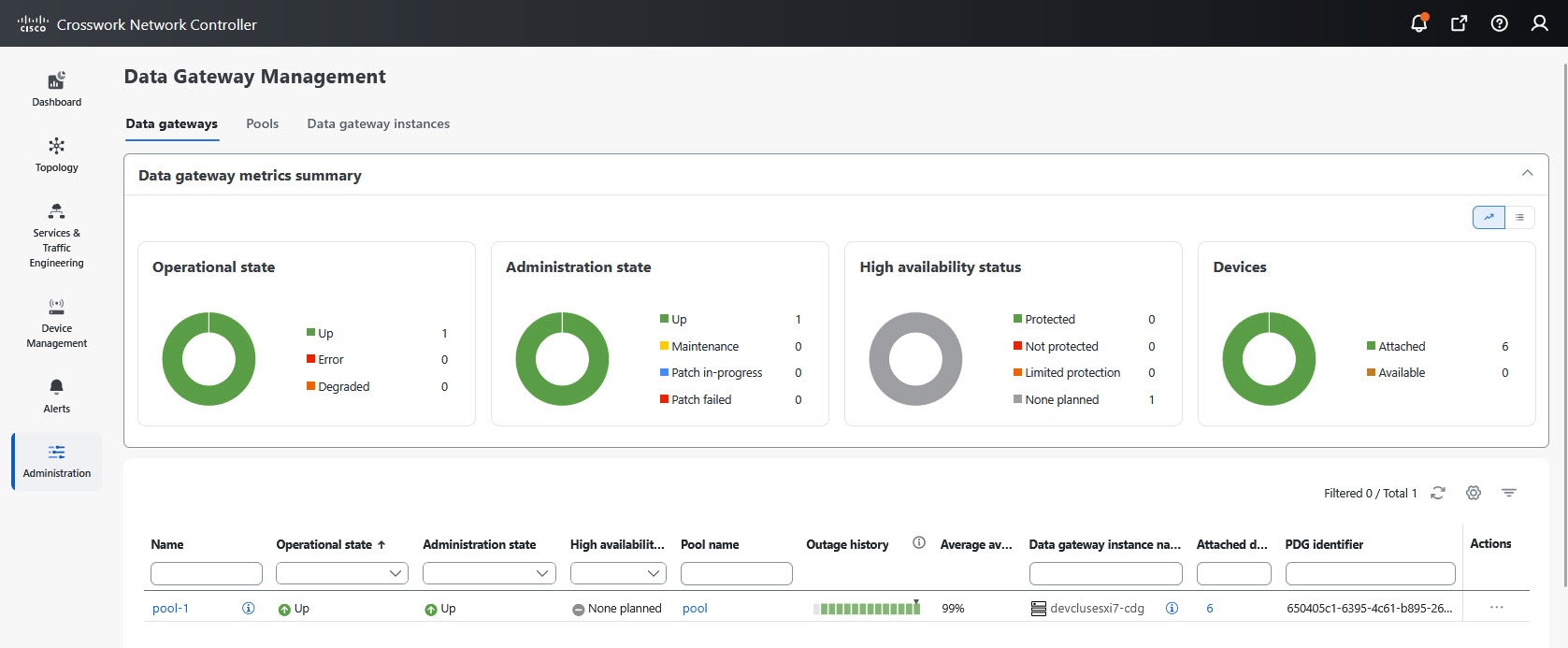
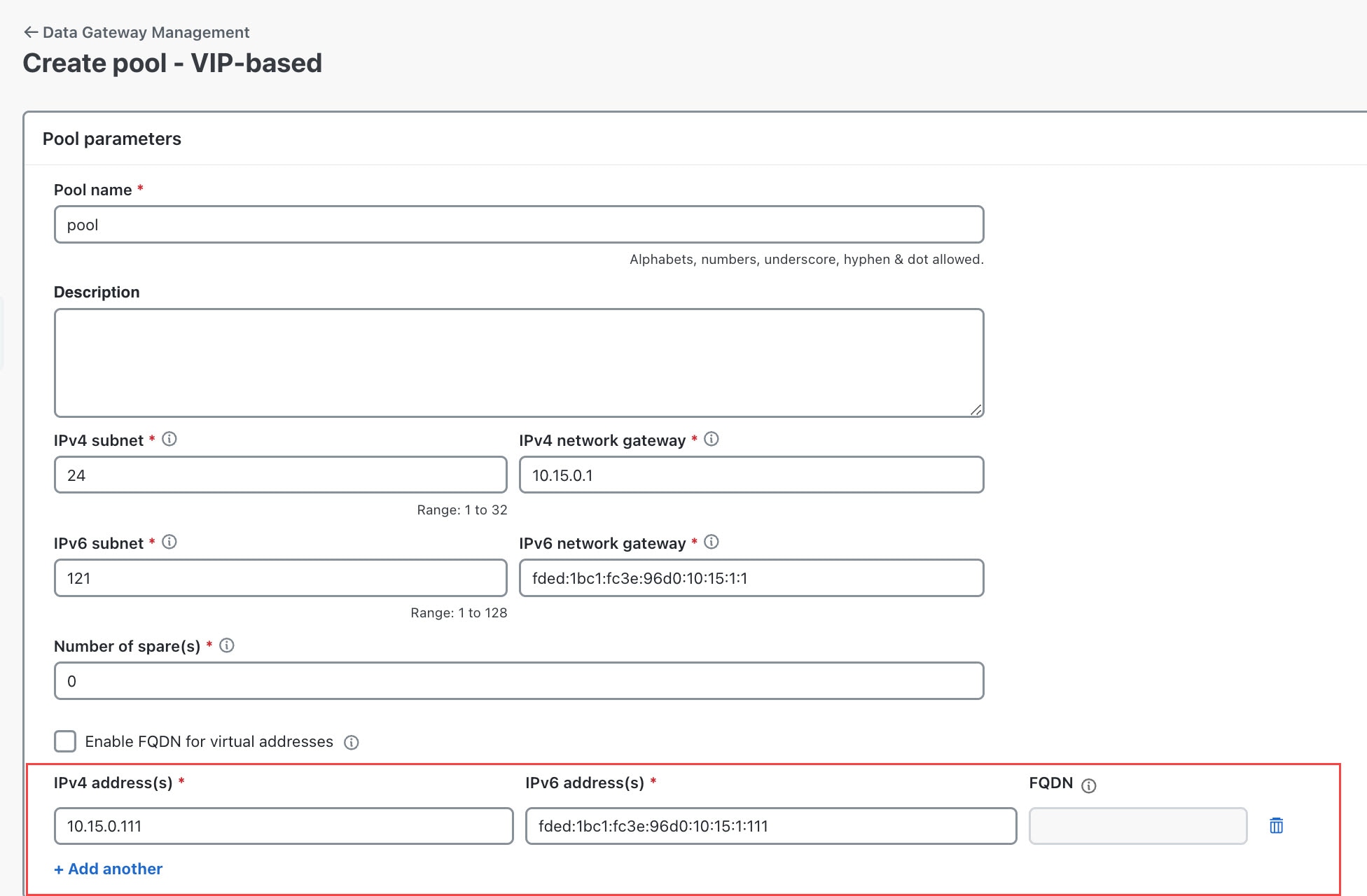
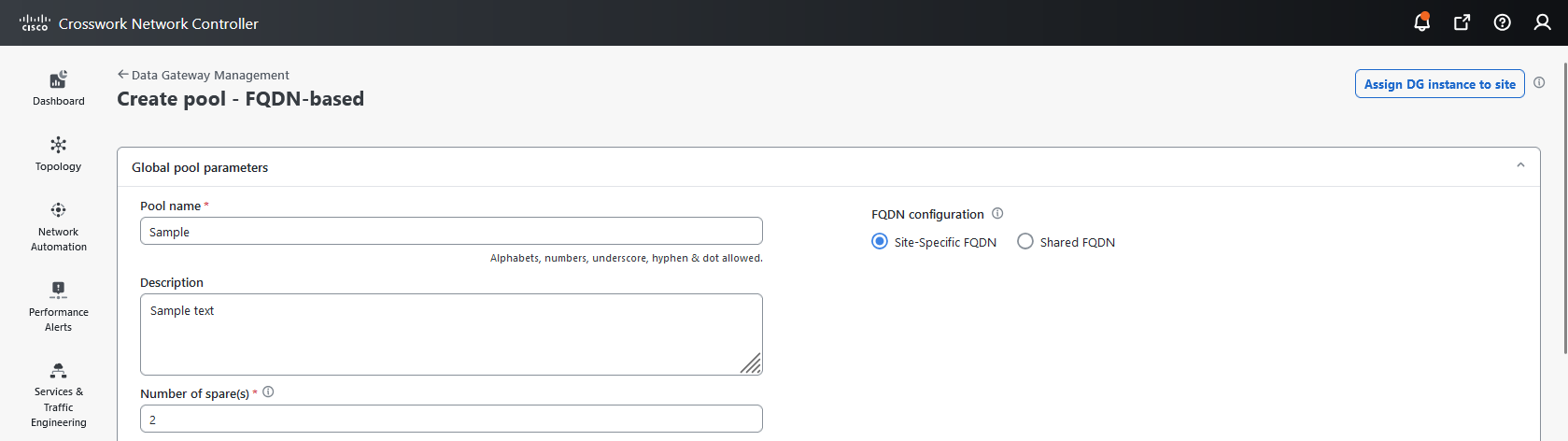
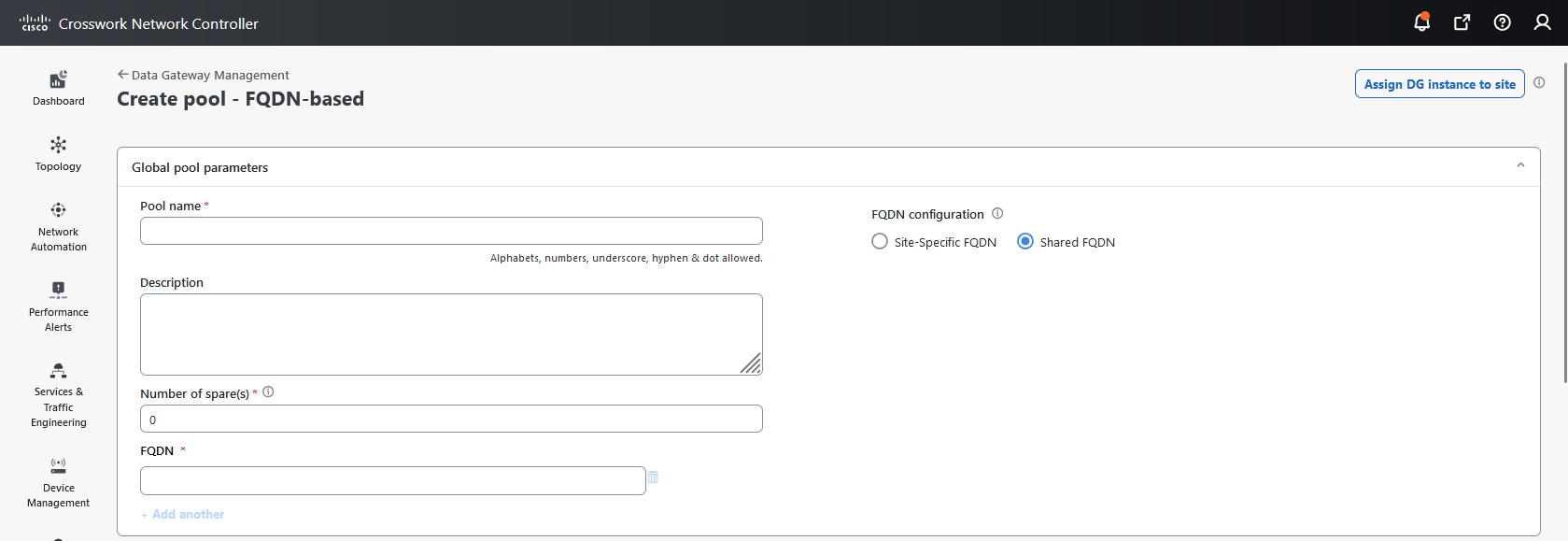
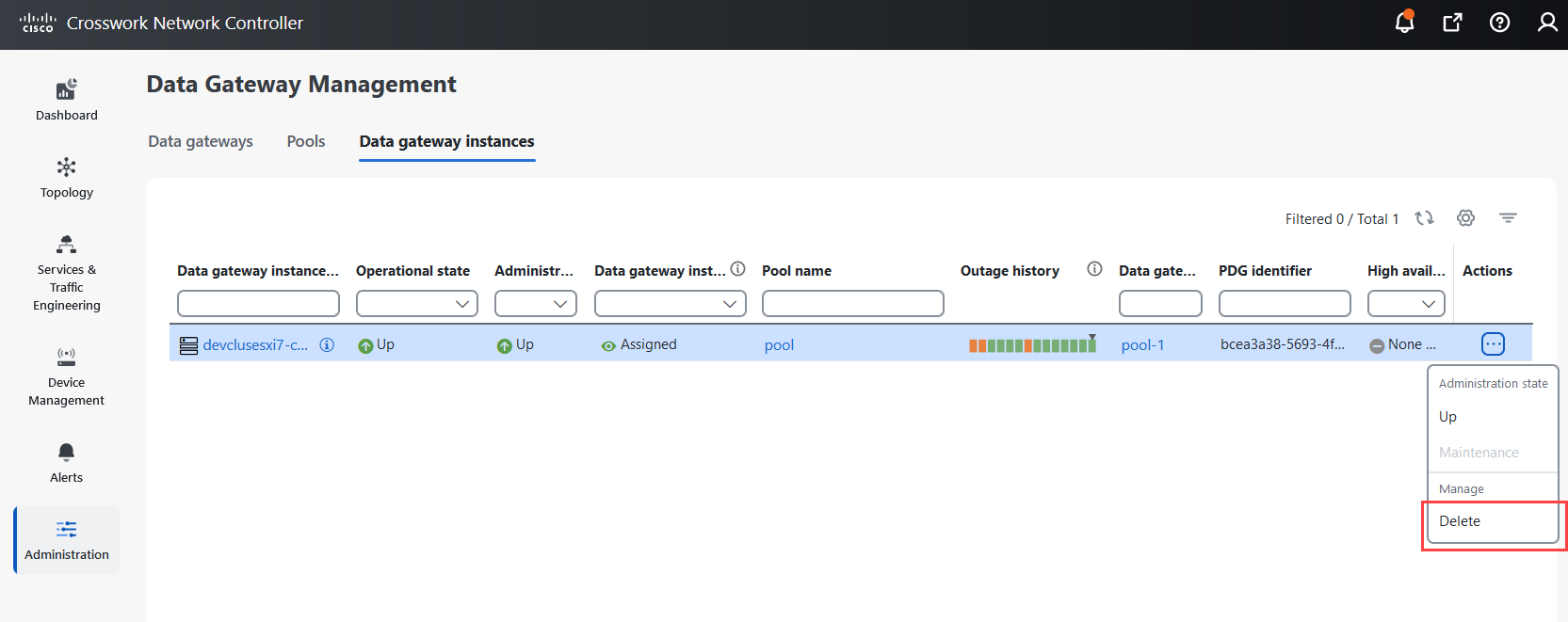
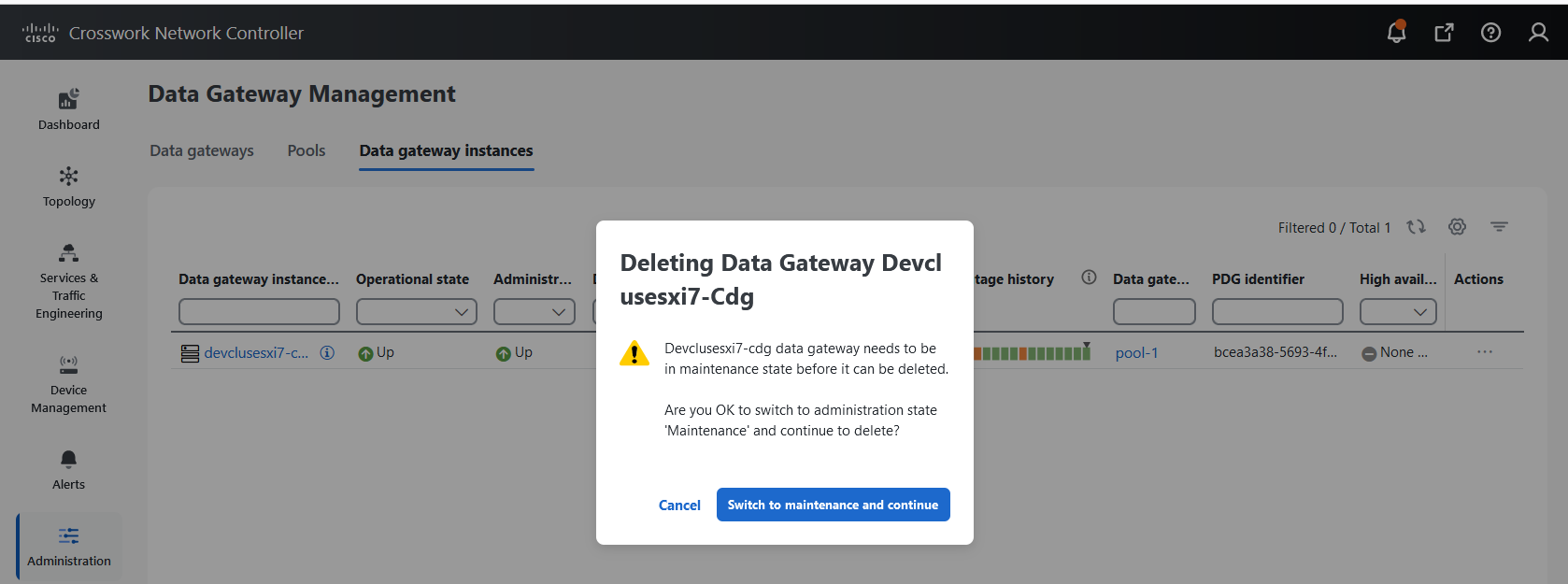
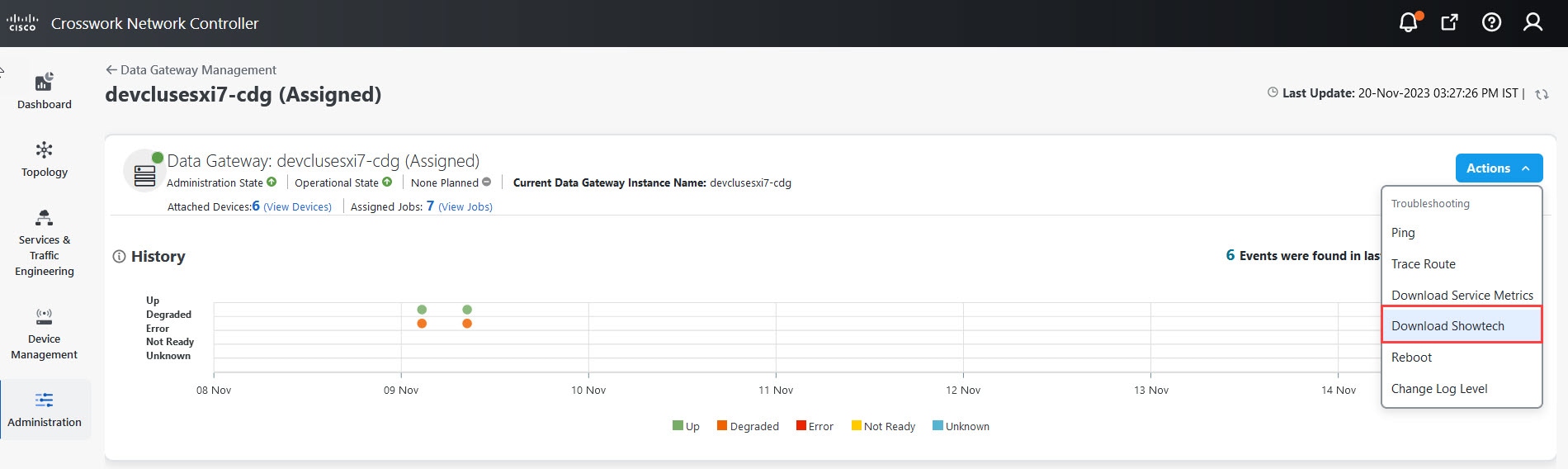
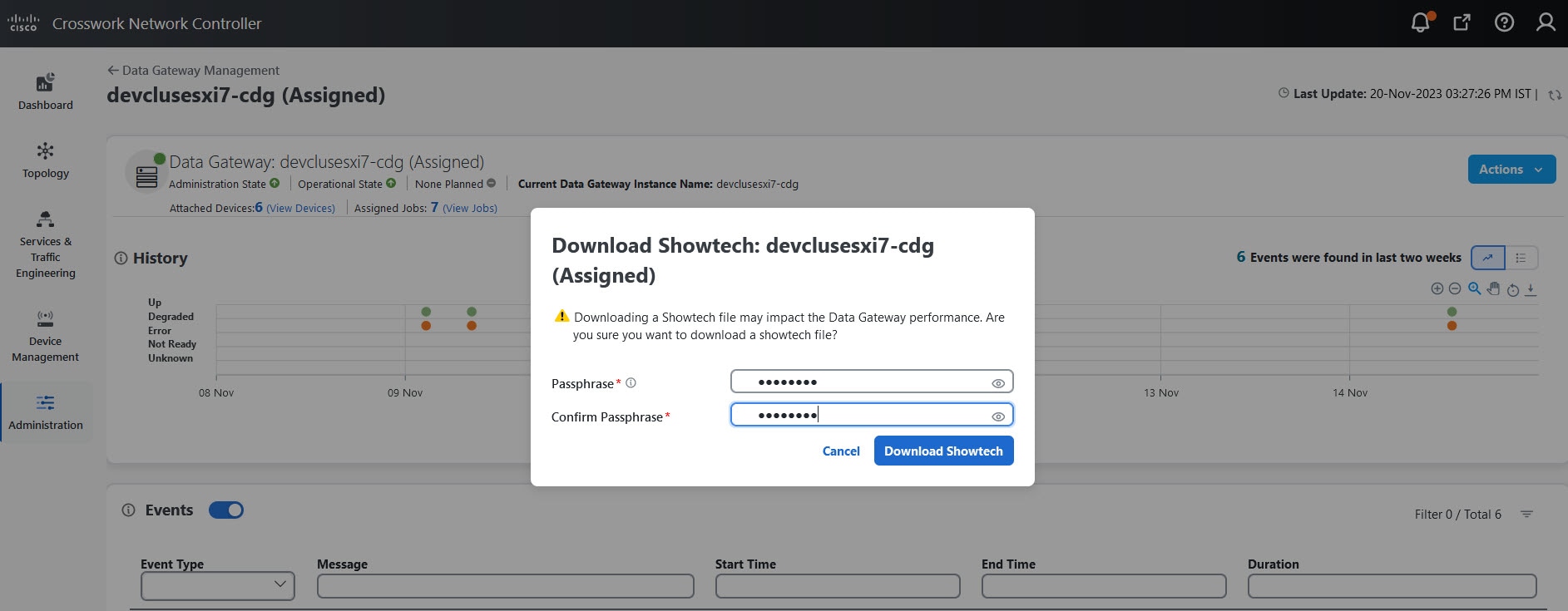
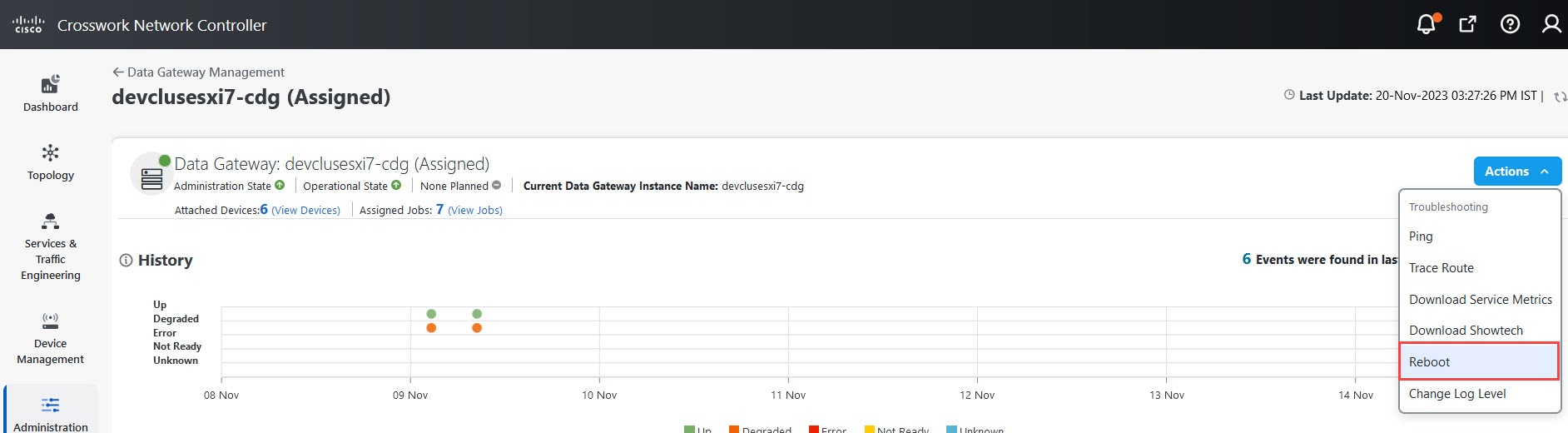
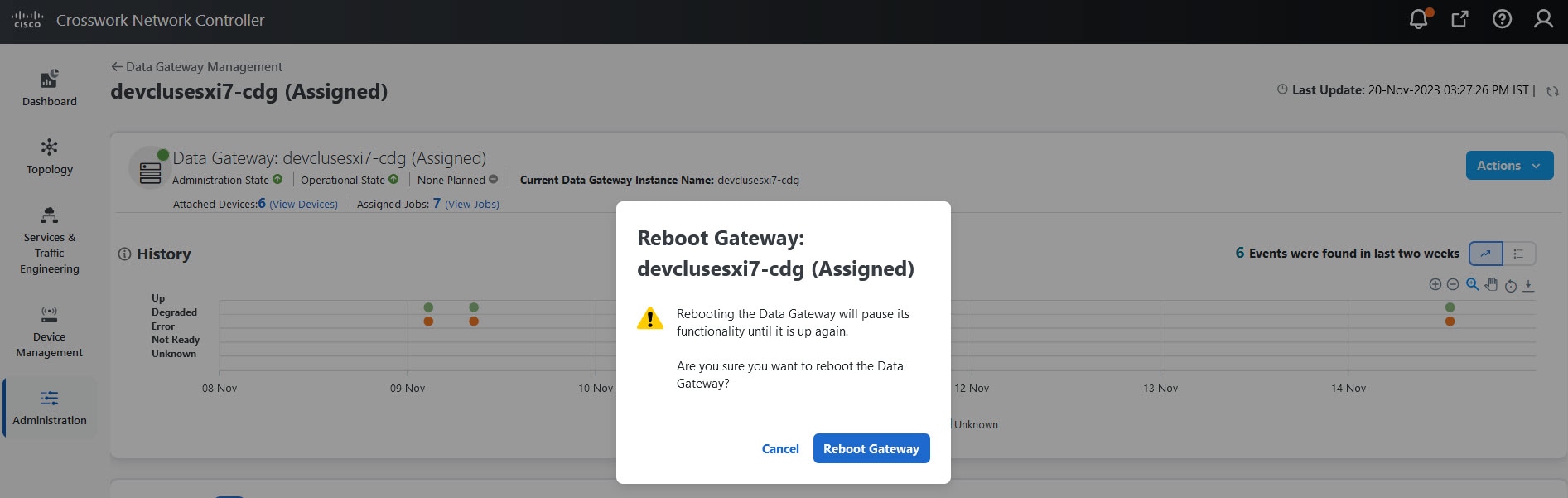
 to view the actions that you can perform on the pool:
to view the actions that you can perform on the pool:
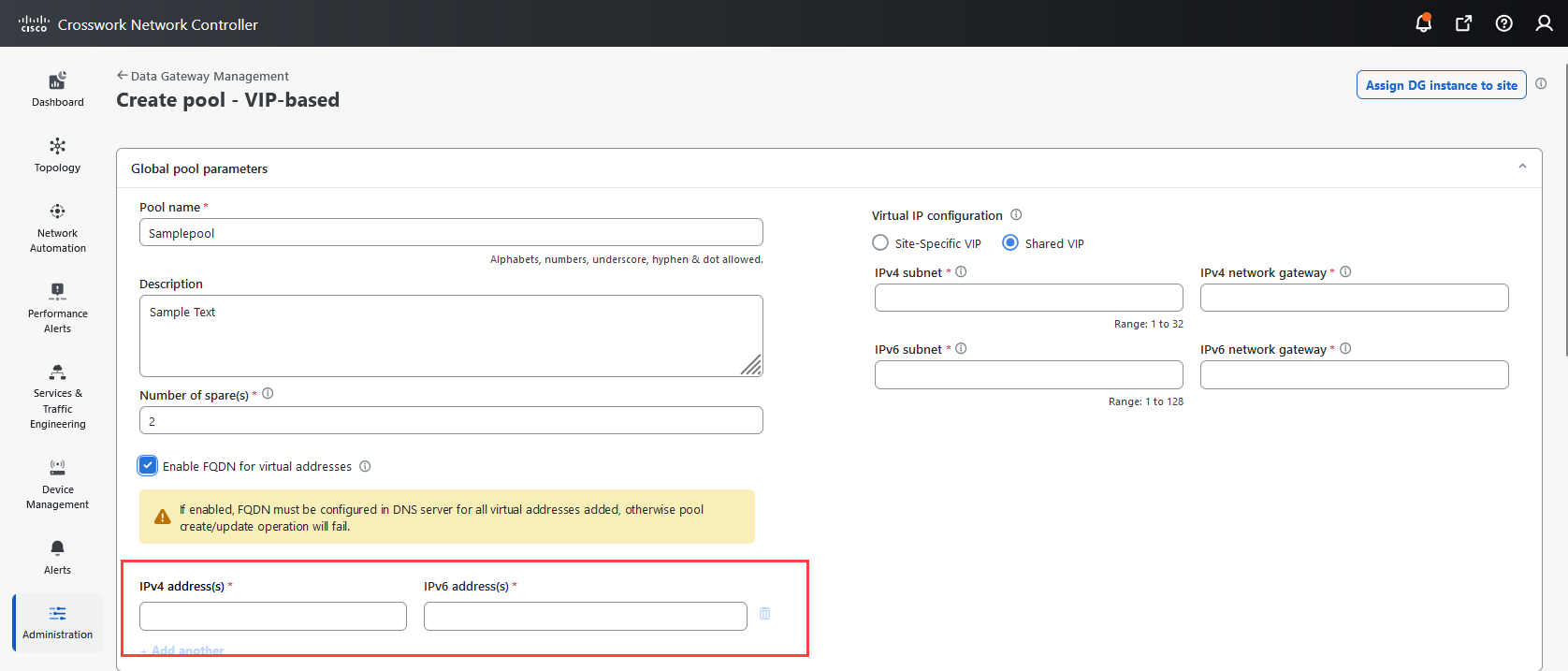

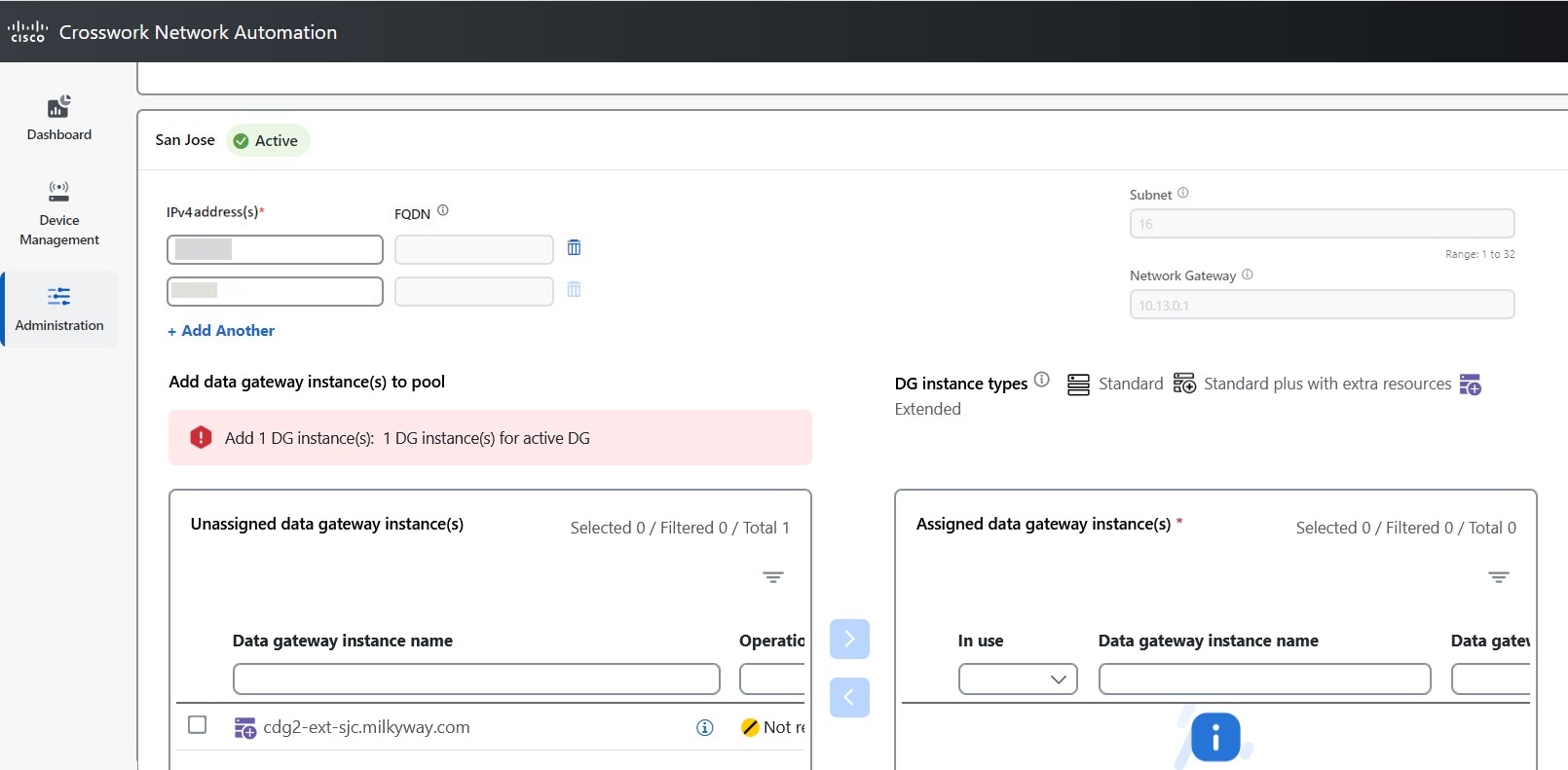
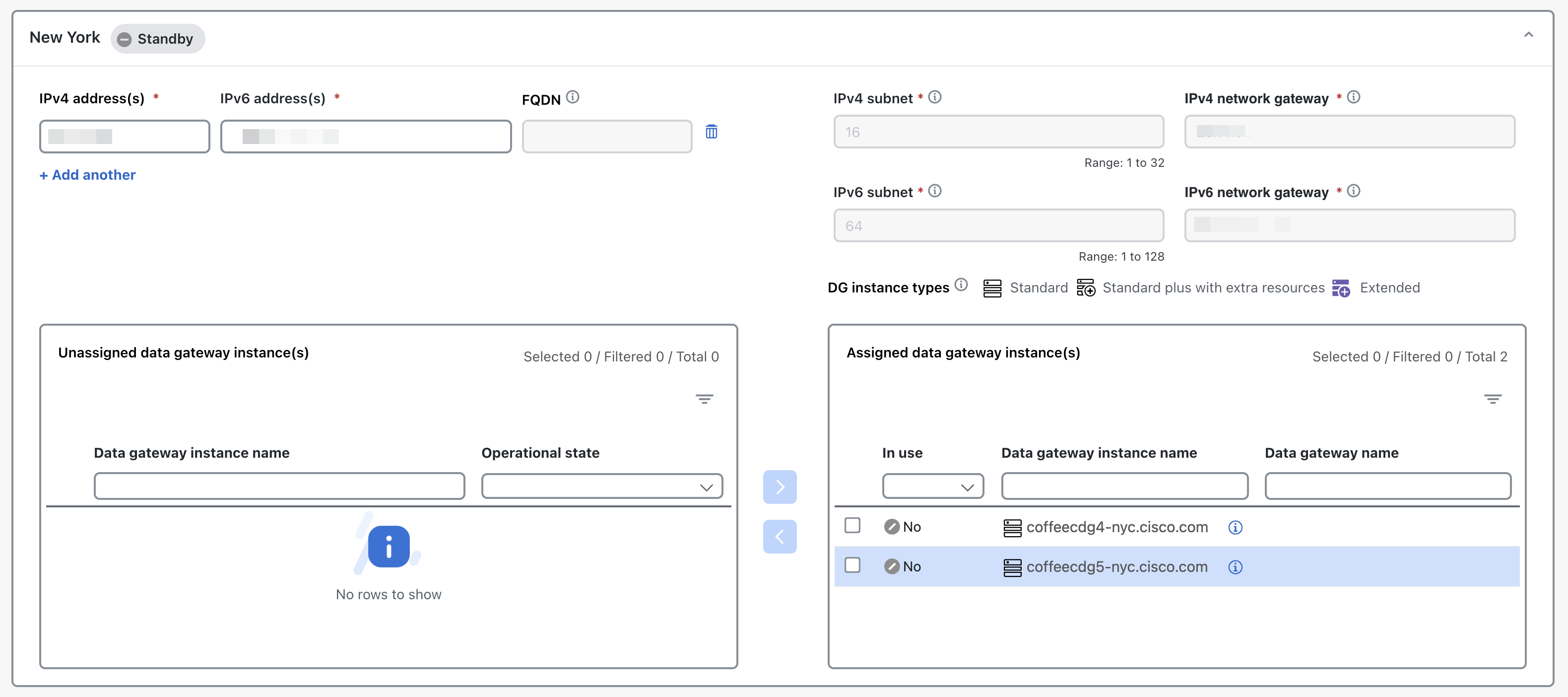
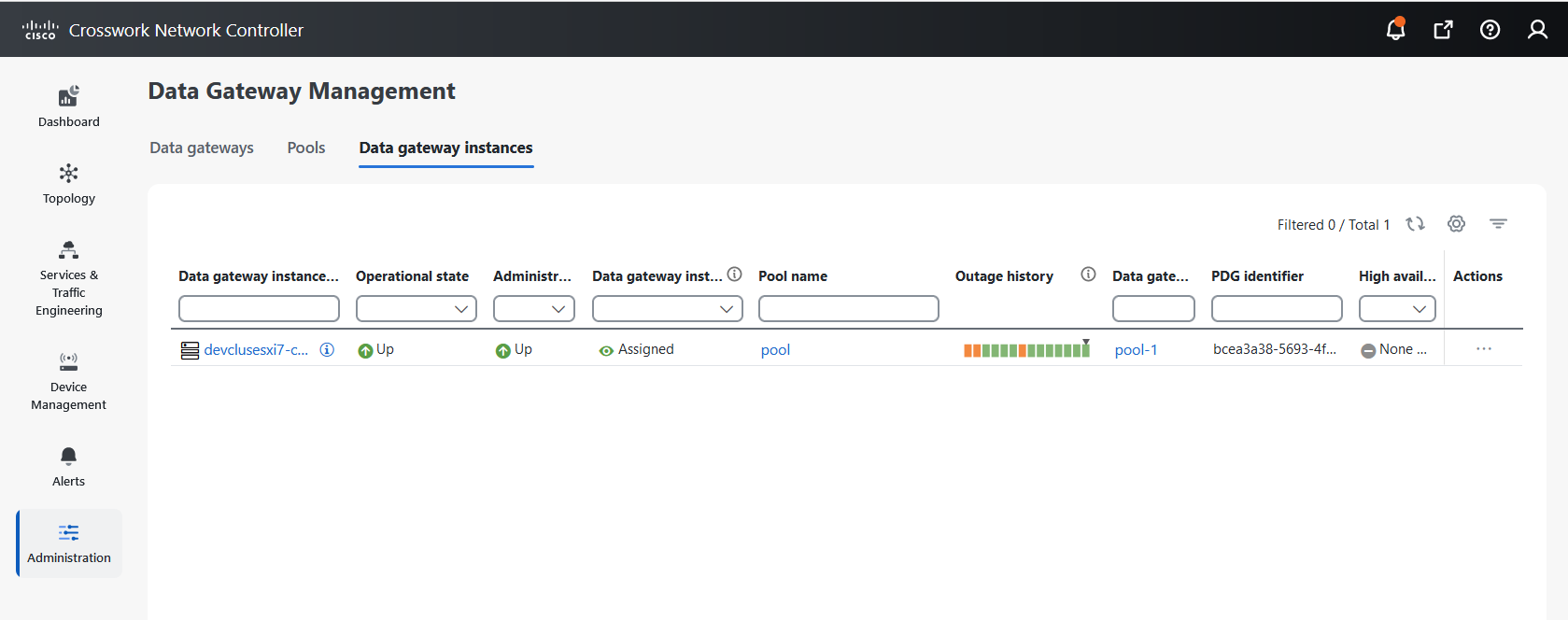
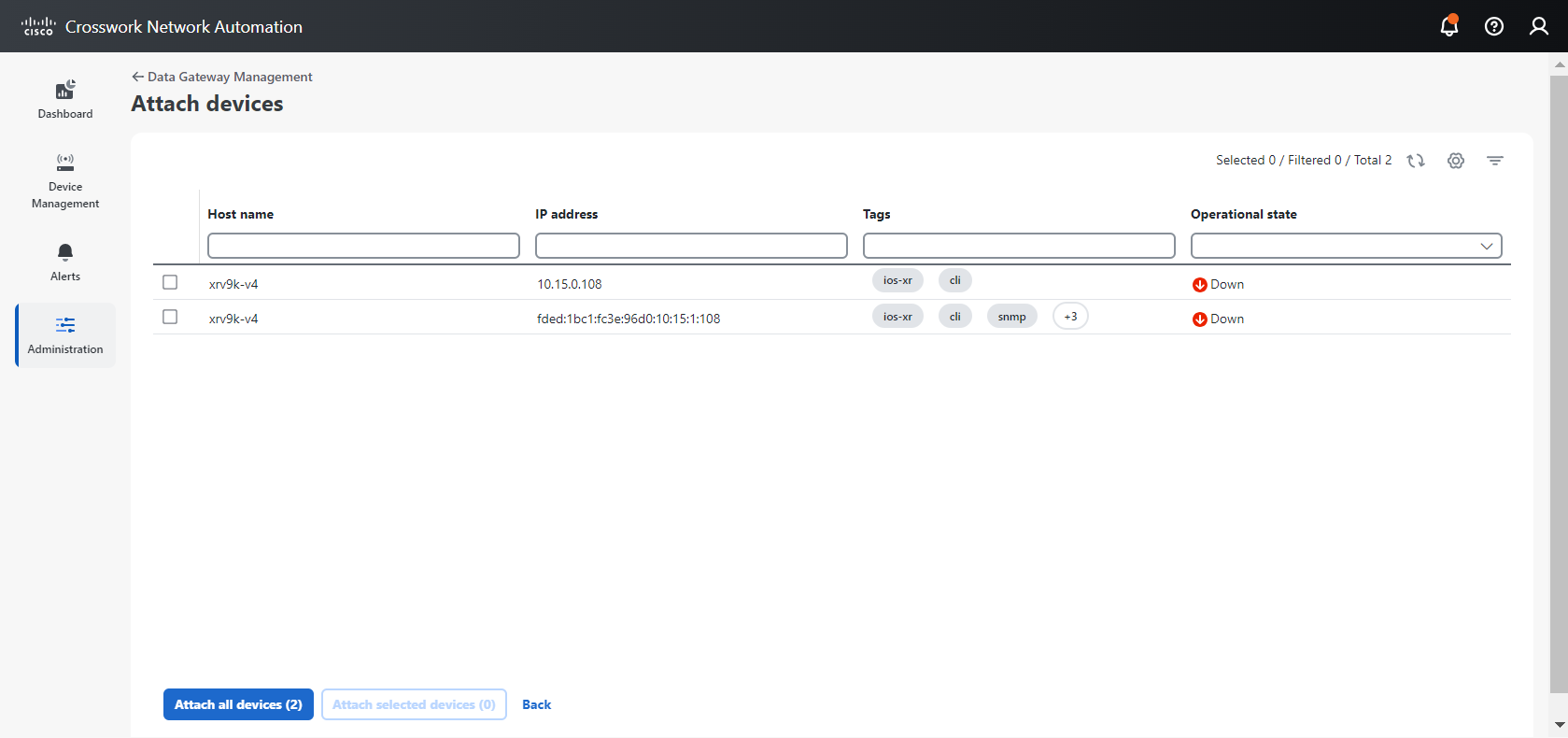
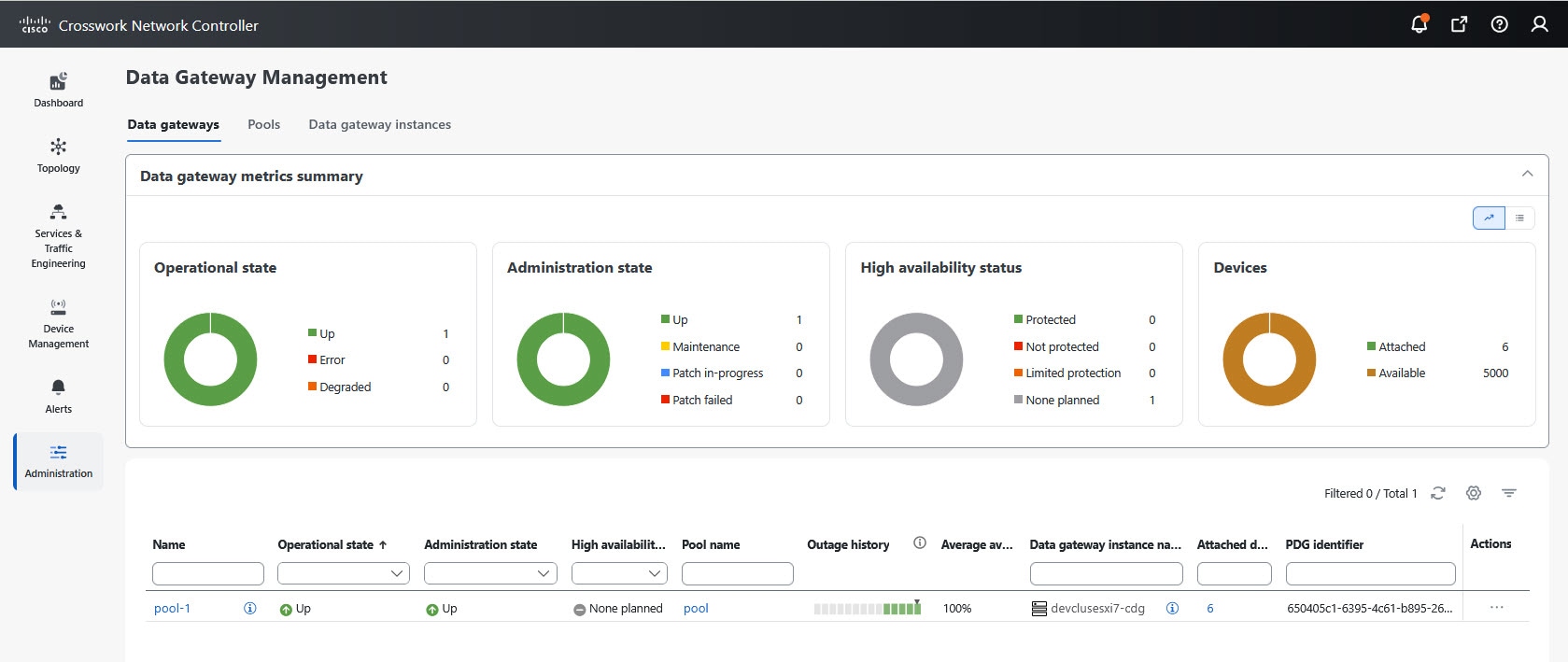
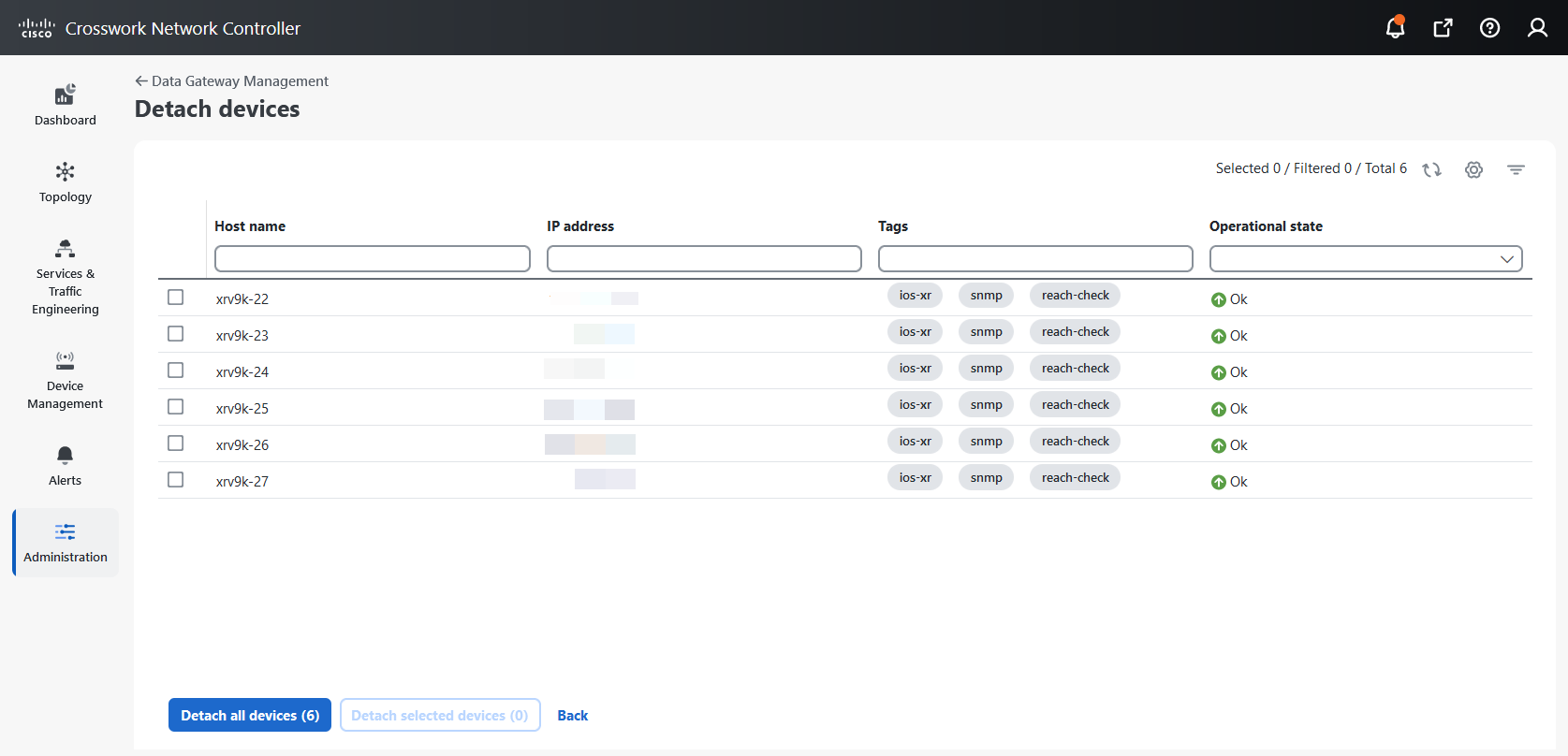
 next to the attached device count to view the list of devices attached to the selected Data Gateway."
next to the attached device count to view the list of devices attached to the selected Data Gateway."




 Feedback
Feedback