User authentication systems
A user authentication system is a security feature that
-
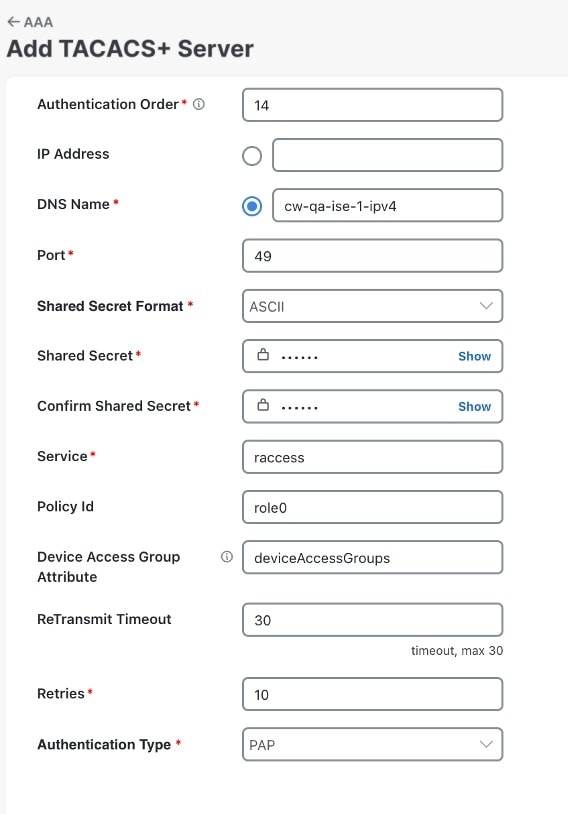
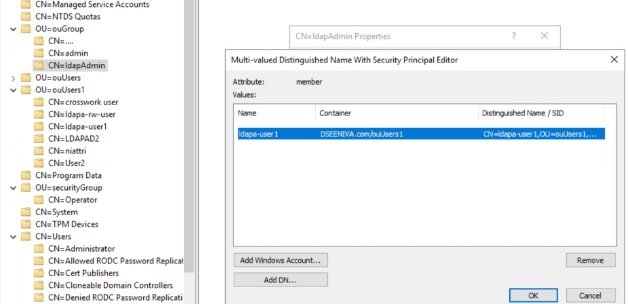
verifies user identities through external servers such as TACACS+, LDAP, or RADIUS,
-
centralizes account and role management across the organization, and
-
enables administrators to enforce consistent access policies for all users.
Best practice for external server changes
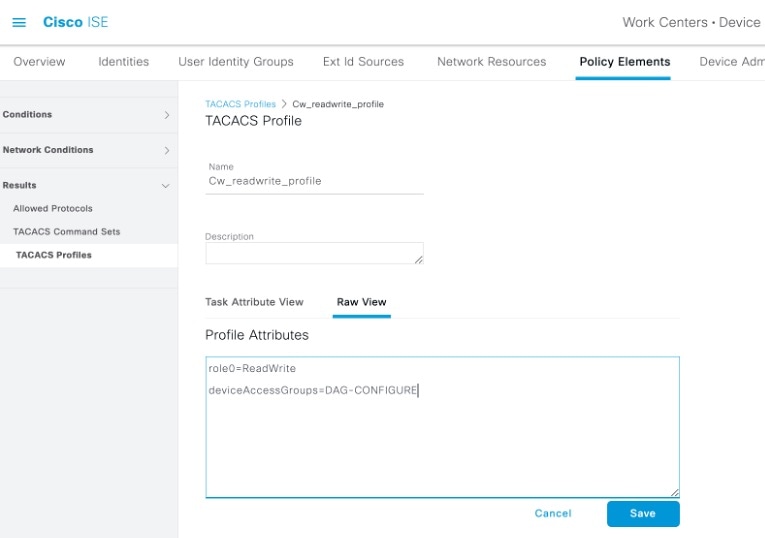
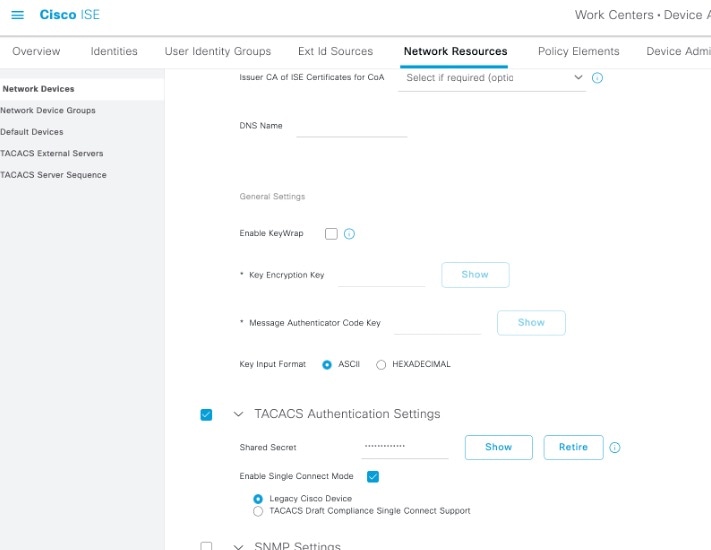
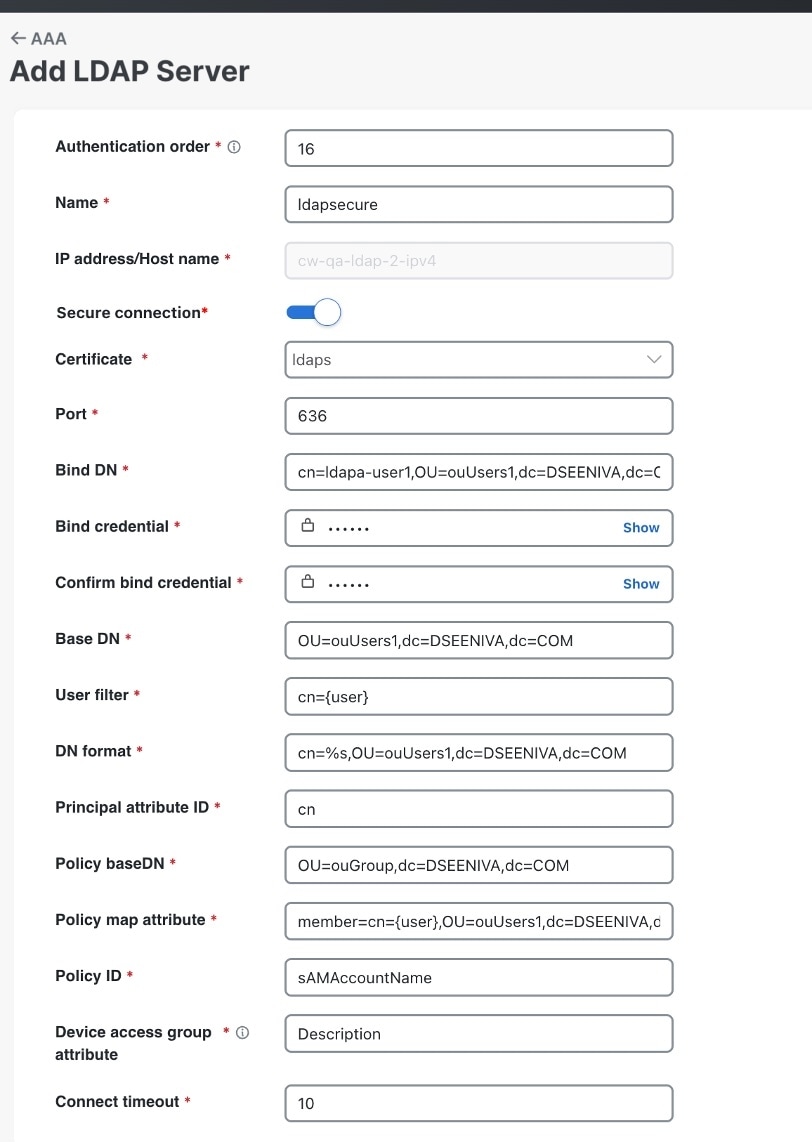
Crosswork Network Controller supports configuration of up to 5 external authentication servers. When making changes to authentication server settings, observe the following recommendations:
-
Perform all server additions, updates, or deletions in a single planned session to minimize user login disruptions.
-
Ensure you have appropriate permissions before attempting to configure or delete external authentication servers.
-
Wait a few minutes between consecutive changes to AAA server settings to avoid causing authentication errors or external login failures.
-
Give write permission for remote authentication server APIs only to users who are authorized to manage or delete external authentication servers.
-
After updating external server configuration in geo-redundant deployments, restart any standby appliance services as instructed by the documentation.
-
Remember that changes to external authentication servers immediately affect all new user logins.

 ) located at the top right corner of the window.
) located at the top right corner of the window.
 Feedback
Feedback