- Title Page
- Table of Contents
- Preface
- Setting Up Devices and Using the GUI Clients
- Working with the Cisco Prime Network Vision Client
- Viewing and Managing NE Properties
- Device Configurations and Software Images
- Working with Prime Network Vision Maps
- Working with Links
- Labeling NEs Using Business Tags
- Working with the Prime Network Events
- Tracking Faults Using Prime Network Events
- Working with Tickets in Cisco Prime Network Vision
- Working with Reports
- Using Cisco PathTracer to Diagnose Problems
- Monitoring Carrier Ethernet Services
- Monitoring Carrier Grade NAT Properties
- Monitoring DWDM Properties
- Monitoring Ethernet Operations, Administration,and Maintenance Tool Properties
- Monitoring Y.1731 IPSLA Configuration
- IPv6 and IPv6 VPN over MPLS
- Monitoring MPLS Services
- Viewing IP and MPLS Multicast Configurations
- Monitoring MToP Services
- Viewing and Managing SBCs
- Monitoring AAA Configurations
- Monitoring IP Pools
- Monitoring BNG Configurations
- Monitoring Mobile Technologies
- Monitoring Data Center Configurations
- Icon and Button Reference
- Glossary
- Index
- User Roles Required to Work with MPLS Networks
- Working with MPLS-TP Tunnels
- Viewing VPNs
- Managing VPNs
- Working with VPN Overlays
- Monitoring MPLS Services
- Viewing VPN Properties
- Viewing Site Properties
- Viewing VRF Properties
- Viewing VRF Egress and Ingress Adjacents
- Viewing Routing Entities
- Viewing Label Switched Entity Properties
- Multicast Label Switching
- Viewing MP-BGP Information
- Viewing 6rd Tunnel Properties
- Viewing BFD Session Properties
- Viewing Cross-VRF Routing Entries
- Viewing Pseudowire End-to-End Emulation Tunnels
- Viewing MPLS TE Tunnel Information
- Configuring VRF
- Configuring IP Interface
- Configuring MPLS-TP
- Configuring MPLS-TE
- Configuring MPLS
- Configuring RSVP
- Configuring BGP
- Configuring VRRP
- Configuring Bundle Ethernet
Monitoring MPLS Services
The following topics describe how to view and manage aspects of Multiprotocol Label Switching (MPLS) services using Cisco Prime Network Vision (Prime Network Vision), including the MPLS service view, business configuration, and maps. The topics also describe the device inventory specific to MPLS VPNs, including routing entities, label switched entities (LSEs), BGP neighbors, Multiprotocol BGP (MP-BGP), VRF instances, pseudowires, and TE tunnels. Topics include:
•![]() User Roles Required to Work with MPLS Networks
User Roles Required to Work with MPLS Networks
User Roles Required to Work with MPLS Networks
This topic identifies the roles that are required to work with MPLS networks. Prime Network determines whether you are authorized to perform a task as follows:
•![]() For GUI-based tasks (tasks that do not affect elements), authorization is based on the default permission that is assigned to your user account.
For GUI-based tasks (tasks that do not affect elements), authorization is based on the default permission that is assigned to your user account.
•![]() For element-based tasks (tasks that do affect elements), authorization is based on the default permission that is assigned to your account. That is, whether the element is in one of your assigned scopes and whether you meet the minimum security level for that scope.
For element-based tasks (tasks that do affect elements), authorization is based on the default permission that is assigned to your account. That is, whether the element is in one of your assigned scopes and whether you meet the minimum security level for that scope.
For more information on user authorization, see the Cisco Prime Network 3.10 Administrator Guide.
The following tables identify the tasks that you can perform:
•![]() Table 19-1 identifies the tasks that you can perform if a selected element is not in one of your assigned scopes.
Table 19-1 identifies the tasks that you can perform if a selected element is not in one of your assigned scopes.
•![]() Table 19-2 identifies the tasks that you can perform if a selected element is in one of your assigned scopes.
Table 19-2 identifies the tasks that you can perform if a selected element is in one of your assigned scopes.
By default, users with the Administrator role have access to all managed elements. To change the Administrator user scope, see the topic on device scopes in the Cisco Prime Network 3.10 Administrator Guide.
Working with MPLS-TP Tunnels
MPLS-Transport Profile (MPLS-TP) is considered to be the next generation transport for those using SONET/SDH TDM technologies as they migrate to packet-switching technology. Although still under definition by the IETF, MPLS-TP provides:
•![]() Predetermined and long-lived connections.
Predetermined and long-lived connections.
•![]() Emphasis on manageability and deterministic behavior.
Emphasis on manageability and deterministic behavior.
•![]() Fast fault detection and recovery.
Fast fault detection and recovery.
•![]() Inband OAM.
Inband OAM.
MPLS-TP features include:
•![]() Manually provisioned MPLS-TP LSPs.
Manually provisioned MPLS-TP LSPs.
•![]() Reserved bandwidth for static MPLS-TP LSPs.
Reserved bandwidth for static MPLS-TP LSPs.
•![]() One-to-one path protection for MPLS-TP LSPs.
One-to-one path protection for MPLS-TP LSPs.
•![]() Working/Protected LSP switchover.
Working/Protected LSP switchover.
•![]() Continuity Check (CC), Proactive Continuity Verification (CV), and Remote Defect Indication (RDI) based on BFD.
Continuity Check (CC), Proactive Continuity Verification (CV), and Remote Defect Indication (RDI) based on BFD.
•![]() New fault OAM functions resulting from the MPLS-TP standardization effort.
New fault OAM functions resulting from the MPLS-TP standardization effort.
Prime Network automatically discovers network MPLS-TP tunnels from end to end, including LSPs, tunnel endpoints, and bandwidth. Network LSPs contain LSP endpoints and midpoints and are identified as working or protected.
Prime Network links the MPLS-TP tunnel components appropriately, provides a visual representation in Prime Network Vision maps, and displays the properties in logical inventory.
Prime Network employs warm start technology when rebooting. That is, when rebooting, Prime Network compares existing MPLS-TP tunnel information to topology changes that occur while Prime Network is down and updates MPLS-TP tunnel accordingly when Prime Network returns to operation.
The following options are available for working with MPLS-TP tunnels in Prime Network Vision:
•![]() Viewing MPLS-TP Tunnel Properties
Viewing MPLS-TP Tunnel Properties
•![]() Viewing LSPs Configured on an Ethernet Link
Viewing LSPs Configured on an Ethernet Link
•![]() Viewing LSP Endpoint Redundancy Service Properties
Viewing LSP Endpoint Redundancy Service Properties
•![]() Applying an MPLS-TP Tunnel Overlay
Applying an MPLS-TP Tunnel Overlay
•![]() Viewing MPLS-TP BFD session properties—See Viewing BFD Session Properties.
Viewing MPLS-TP BFD session properties—See Viewing BFD Session Properties.
Adding an MPLS-TP Tunnel
Prime Network Vision automatically discovers MPLS-TP tunnels, endpoints, and midpoints and enables you to add MPLP-TP tunnels to maps.
To add an MPLS-TP tunnel to a map:
Step 1 ![]() In Prime Network Vision, display the map to which you want to add the MPLS-TP tunnel.
In Prime Network Vision, display the map to which you want to add the MPLS-TP tunnel.
Step 2 ![]() Do either of the following:
Do either of the following:
•![]() From the File menu, choose Add to Map > MPLS-TP Tunnel.
From the File menu, choose Add to Map > MPLS-TP Tunnel.
•![]() In the main toolbar, click Add to Map, then choose Add to Map > MPLS-TP Tunnel.
In the main toolbar, click Add to Map, then choose Add to Map > MPLS-TP Tunnel.
The Add MPLS-TP Tunnel dialog box is displayed.
Step 3 ![]() Do either of the following:
Do either of the following:
•![]() Choose a search category, enter a search string, then click Go to narrow search results to a range of MPLS-TP tunnels or a specific MPLS-TP tunnel. Search categories include:
Choose a search category, enter a search string, then click Go to narrow search results to a range of MPLS-TP tunnels or a specific MPLS-TP tunnel. Search categories include:
–![]() Description
Description
–![]() Name
Name
–![]() System Name
System Name
•![]() Choose Show All to display all the MPLS-TP tunnels.
Choose Show All to display all the MPLS-TP tunnels.
Step 4 ![]() Select the MPLS-TP tunnel that you want to add to the map.
Select the MPLS-TP tunnel that you want to add to the map.
Step 5 ![]() Click OK.
Click OK.
The MPLS-TP tunnel is added to the map and to the navigation pane.
In Figure 19-1:
•![]() The devices are on the left side of the map, and the MPLS-TP tunnel is displayed in a thumbnail on the right.
The devices are on the left side of the map, and the MPLS-TP tunnel is displayed in a thumbnail on the right.
•![]() The devices are connected to each other and to the MPLS-TP tunnel via tunnels.
The devices are connected to each other and to the MPLS-TP tunnel via tunnels.
•![]() Physical links connect the devices to the Working and Protected LSPs.
Physical links connect the devices to the Working and Protected LSPs.
•![]() A redundancy service badge is displayed next to the Protected LSP in the navigation and map panes.
A redundancy service badge is displayed next to the Protected LSP in the navigation and map panes.
•![]() In the thumbnail:
In the thumbnail:
–![]() The tunnel endpoints are connected to each other via a tunnel.
The tunnel endpoints are connected to each other via a tunnel.
–![]() A physical link connects the Working and Protected LSPs.
A physical link connects the Working and Protected LSPs.
–![]() Business links connect the Working and Protected LSPs to each endpoint.
Business links connect the Working and Protected LSPs to each endpoint.
Figure 19-1 MPLS-TP Tunnel in Prime Network Vision Map
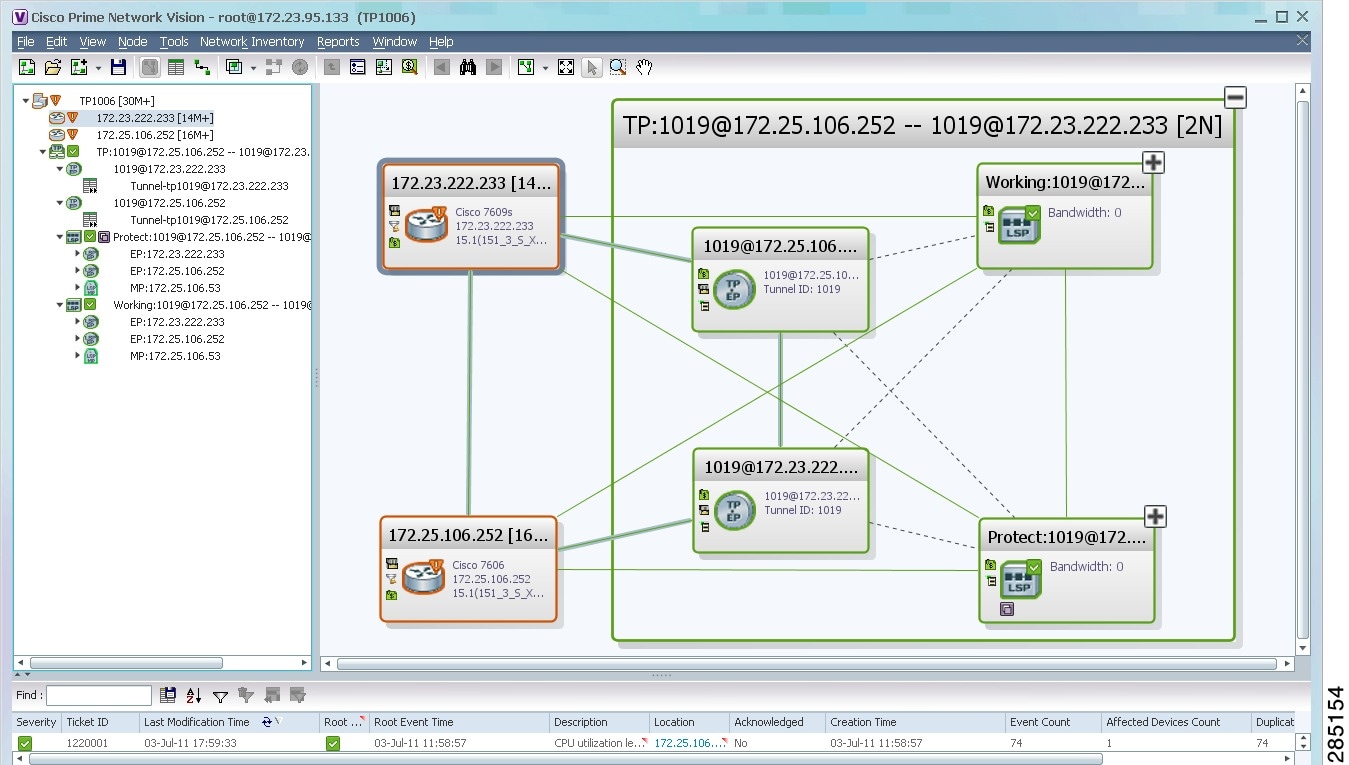
If an LSP is in lockout state, it is displayed with the lock badge ( ).
).
By expanding all aggregations in the MPLS-TP tunnel (see Figure 19-2), you can see components and links in the MPLS-TP tunnel, including:
•![]() MPLS-TP tunnel endpoints
MPLS-TP tunnel endpoints
•![]() LSP endpoints
LSP endpoints
•![]() LSP midpoints
LSP midpoints
Figure 19-2 MPLS-TP Tunnel Expanded
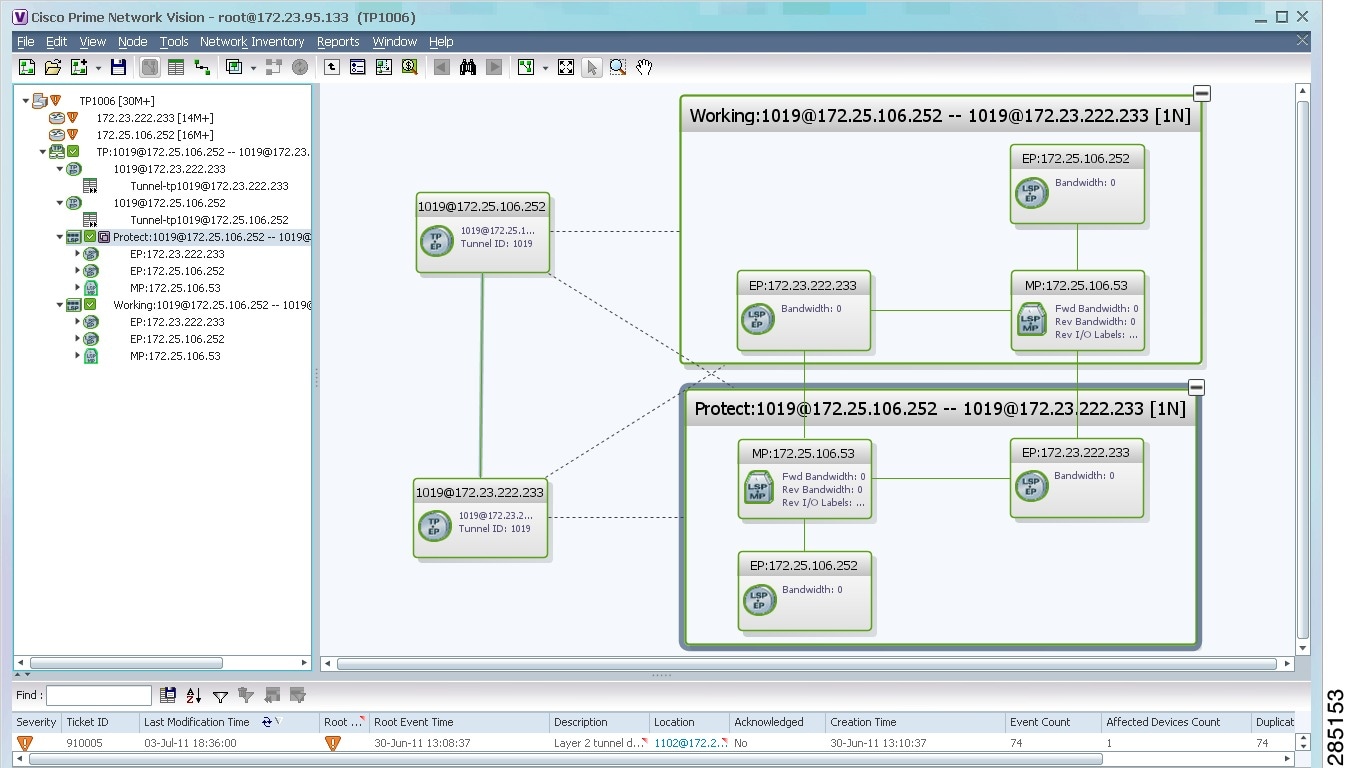
If an LSP is configured for redundancy service, a redundancy service badge is applied to the secondary (backup) LSP in the navigation and map panes in the navigation and map panes.
For more information about LSP redundancy service, see Viewing LSP Endpoint Redundancy Service Properties.
Viewing MPLS-TP Tunnel Properties
Prime Network Vision discovers and displays MPLS-TP attributes in the MPLS-TP branch in logical inventory as described in this topic.
Additional information about MPLS-TP tunnel properties are available in the following branches:
•![]() Routing Entities—See Viewing Routing Entities.
Routing Entities—See Viewing Routing Entities.
•![]() LSEs—See Viewing Label Switched Entity Properties.
LSEs—See Viewing Label Switched Entity Properties.
•![]() Pseudowires— See Viewing Pseudowire End-to-End Emulation Tunnels.
Pseudowires— See Viewing Pseudowire End-to-End Emulation Tunnels.
To view MPLS-TP tunnel properties:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > MPLS-TP > MPLS-TP Global.
In the logical inventory window, choose Logical Inventory > MPLS-TP > MPLS-TP Global.
The routing information is displayed as shown in Figure 19-3.
Figure 19-3 MPLS-TP Tunnel Properties in Logical Inventory
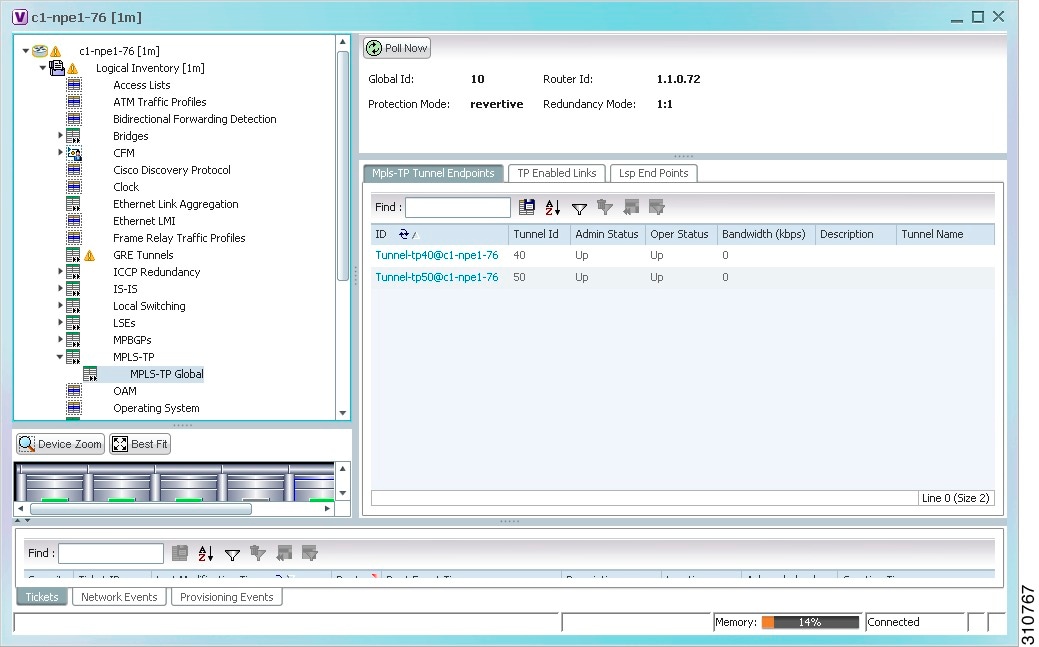
Table 19-3 describes the information that is available for MPLS-TP tunnels. The information that is displayed depends on the configuration.
Step 3 ![]() To view additional MPLS-TP tunnel endpoint properties, double-click the required entry in the MPLS-TP Tunnel Endpoints table.
To view additional MPLS-TP tunnel endpoint properties, double-click the required entry in the MPLS-TP Tunnel Endpoints table.
The MPLS-TP Tunnel Properties window is displayed as shown in Figure 19-4.
Figure 19-4 MPLS-TP Tunnel Properties Window
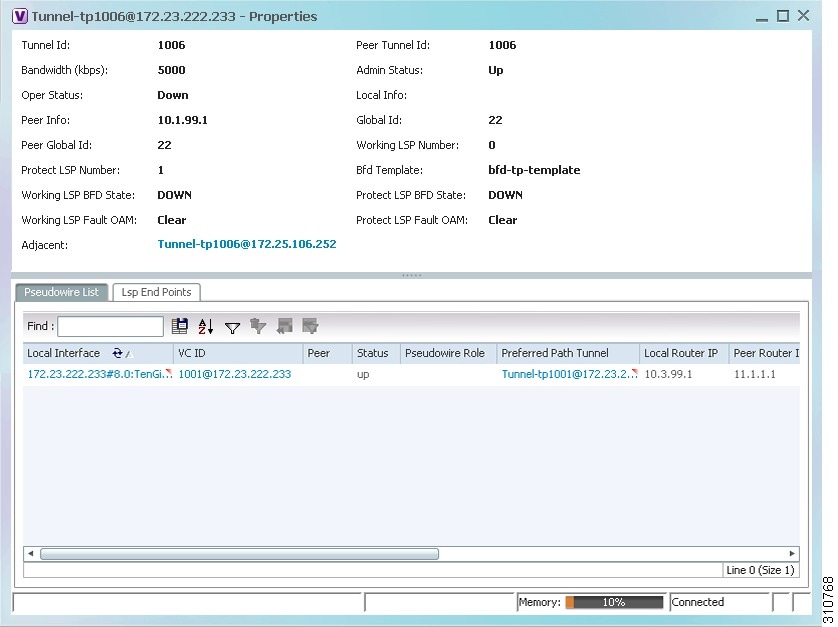
Table 19-4 describes the information available in the top portion of the MPLS-TP Tunnel Properties window. For information about the tabs that are displayed, see Table 19-3.
Viewing LSPs Configured on an Ethernet Link
A single Ethernet link can support a number of LSPs. Prime Network Vision enables you to view all LSPs on a single Ethernet link and to identify the source and destination labels.
To view LSPs configured on an Ethernet link:
Step 1 ![]() In the map view, right-click the required link and choose Properties.
In the map view, right-click the required link and choose Properties.
Step 2 ![]() In the link properties window, choose the required Ethernet link.
In the link properties window, choose the required Ethernet link.
The link properties window refreshes and displays the Labels button as shown in Figure 19-5.
Figure 19-5 Link Properties Window with All Labels Button
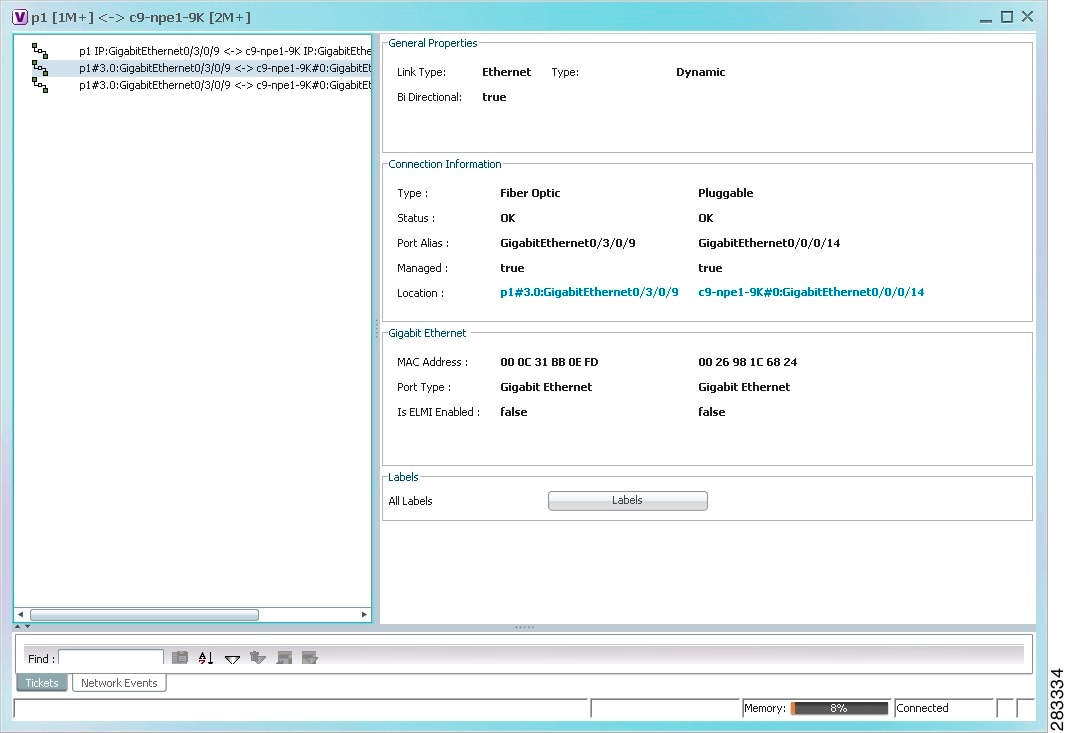
Step 3 ![]() Click Labels.
Click Labels.
The All Labels window is displayed as shown in Figure 19-6 with the LSP sources and destinations.
Figure 19-6 All Labels Table
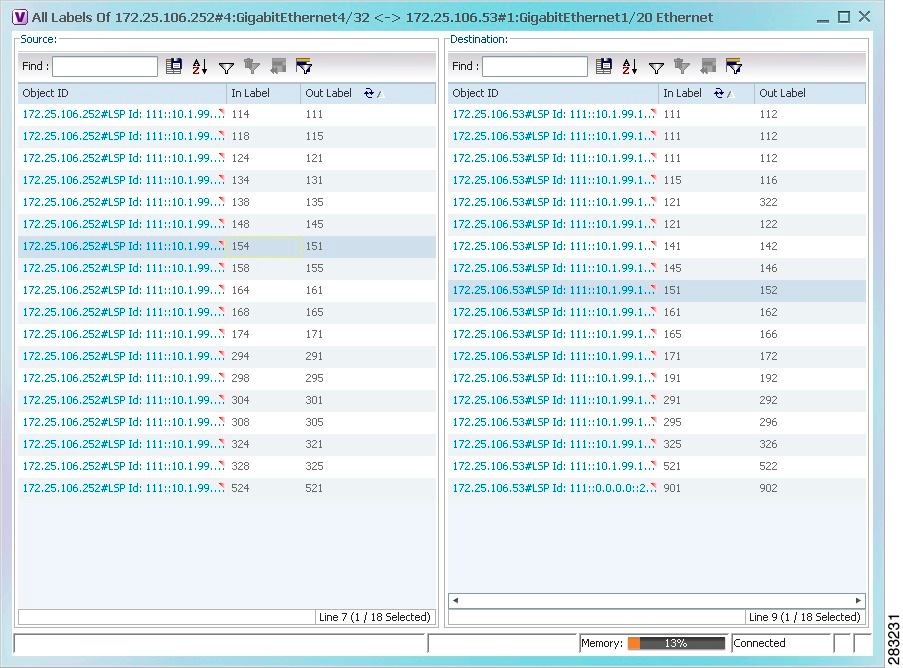
Step 4 ![]() To identify a specific path, click an outgoing label in the Source table. The corresponding in label is selected in the Destination table.
To identify a specific path, click an outgoing label in the Source table. The corresponding in label is selected in the Destination table.
Viewing LSP Endpoint Redundancy Service Properties
If an LSP endpoint in an MPLS-TP tunnel is configured for redundancy service, a redundancy service badge is applied to the secondary (backup) LSP endpoint in the navigation and map panes in Prime Network Vision. Additional redundancy service details are provided in the LSP endpoint properties window and the inventory window for the element on which the MPLS-TP tunnel is configured.
To view LSP endpoint redundancy service properties:
Step 1 ![]() To determine if an LSP endpoint on an MPLS-TP tunnel is configured for redundancy service, expand the required MPLS-TP tunnel in the navigation or map pane.
To determine if an LSP endpoint on an MPLS-TP tunnel is configured for redundancy service, expand the required MPLS-TP tunnel in the navigation or map pane.
If the LSP endpoint is configured for redundancy service, the redundancy service badge is displayed in the navigation and map panes as shown in Figure 19-7.
Figure 19-7 LSP Endpoint with Redundancy Service Badge
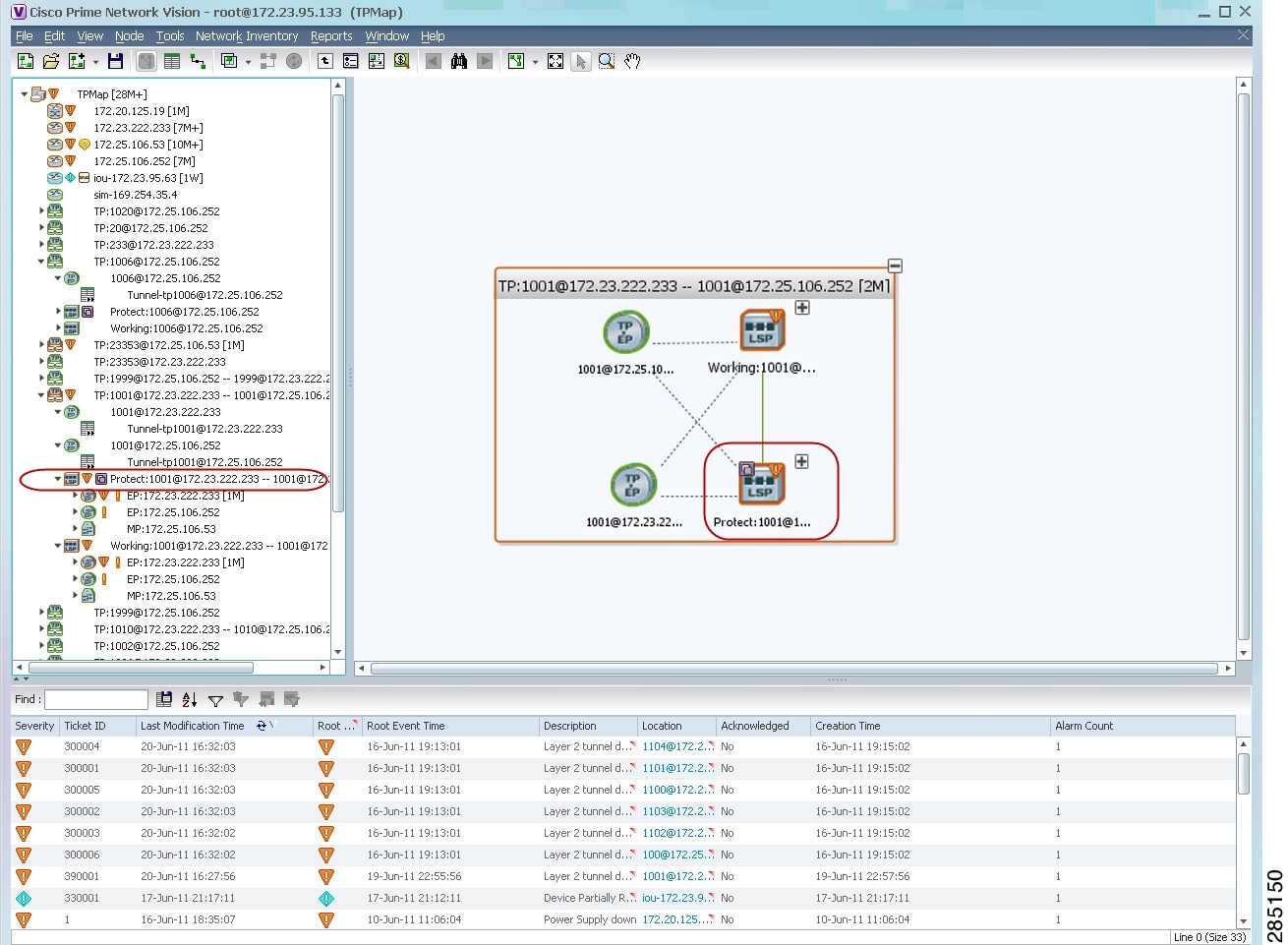
Step 2 ![]() To view properties for the LSP endpoint, navigate to and right-click the required endpoint in the map or navigation pane, and choose Properties.
To view properties for the LSP endpoint, navigate to and right-click the required endpoint in the map or navigation pane, and choose Properties.
The LSP endpoint properties window is displayed as shown in Figure 19-8.
Figure 19-8 LSP Endpoint Properties Window
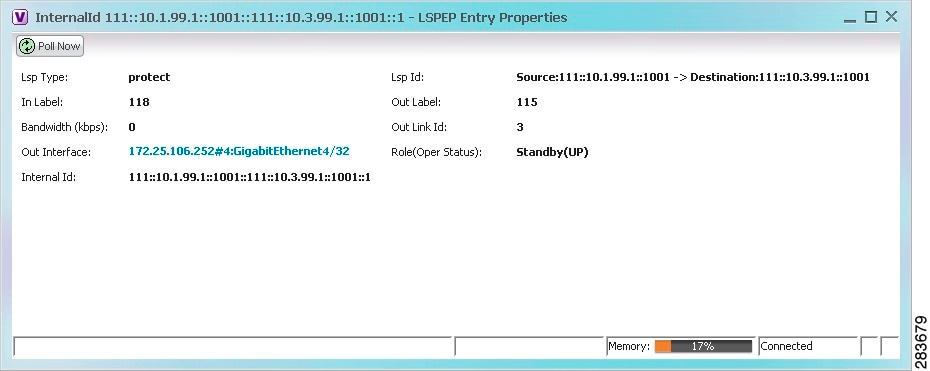
Table 19-5 describes the information displayed in the LSP Endpoint Properties window.
Step 3 ![]() To view LSP endpoint redundancy status in inventory, double-click the element on which the MPLS-TP tunnel is configured.
To view LSP endpoint redundancy status in inventory, double-click the element on which the MPLS-TP tunnel is configured.
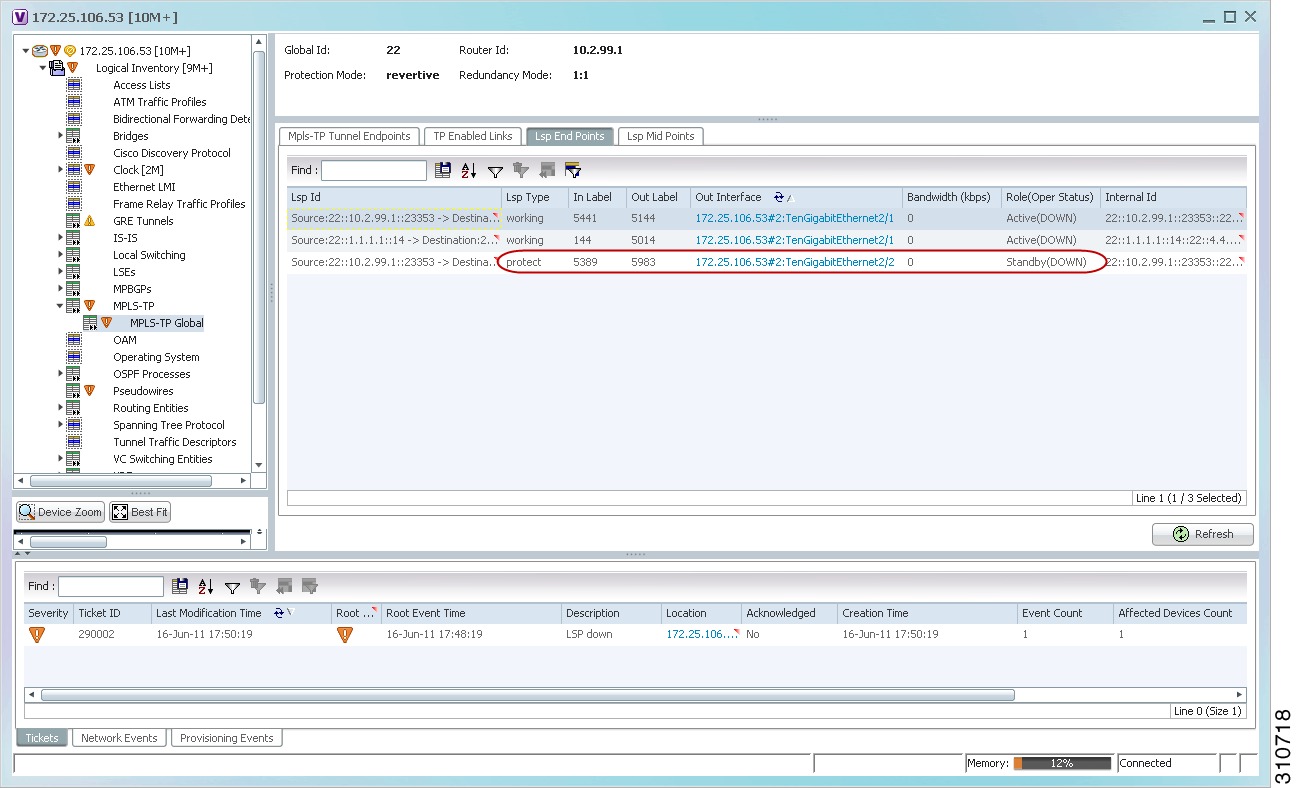
Step 4 ![]() Choose Logical Inventory > MPLS-TP > MPLS-TP Global > LSP End Points.
Choose Logical Inventory > MPLS-TP > MPLS-TP Global > LSP End Points.
Step 5 ![]() The LSP End Points tab contains the following information related to LSP redundancy service (see Figure 19-9):
The LSP End Points tab contains the following information related to LSP redundancy service (see Figure 19-9):
•![]() Whether the LSP endpoint is Working or Protected.
Whether the LSP endpoint is Working or Protected.
•![]() The LSP endpoint role, either Active or Standby.
The LSP endpoint role, either Active or Standby.
•![]() The operational status of the LSP endpoint, either Up or Down.
The operational status of the LSP endpoint, either Up or Down.
Figure 19-9 LSP End Points Tab in Logical Inventory
Applying an MPLS-TP Tunnel Overlay
You can select and display an overlay of a specific MPLS-TP tunnel on top of the devices displayed in a map view. The overlay is a snapshot of the network that visualizes the flows between the sites and tunnel peers. When an MPLS-TP tunnel is selected in the map, the following elements are highlighted in the map:
•![]() Elements on which TP endpoints and LSPs are configured.
Elements on which TP endpoints and LSPs are configured.
•![]() Links that carry TP traffic.
Links that carry TP traffic.
All elements and links that are not part of the MPLS-TP tunnel are dimmed.
To apply an MPLS-TP tunnel overlay:
Step 1 ![]() In Prime Network Vision, display the network map on which you want to apply an overlay.
In Prime Network Vision, display the network map on which you want to apply an overlay.
Step 2 ![]() From the main toolbar, click Choose Overlay Type and choose MPLS-TP tunnel.
From the main toolbar, click Choose Overlay Type and choose MPLS-TP tunnel.
The Select MPLS-TP tunnel Overlay dialog box is displayed.
Step 3 ![]() Do one of the following:
Do one of the following:
•![]() Choose a search category, enter a search string, then click Go to narrow the search results to a range of MPLS-TP tunnels or a specific MPLS-TP tunnel. Search categories include:
Choose a search category, enter a search string, then click Go to narrow the search results to a range of MPLS-TP tunnels or a specific MPLS-TP tunnel. Search categories include:
–![]() Description
Description
–![]() Name
Name
–![]() System Name
System Name
The search condition is "contains." Search strings are case-insensitive. For example, if you choose the Name category and enter "net," Prime Network Vision displays MPLS-TP tunnels that have "net" in their names whether net appears at the beginning of the name, the middle, or at the end: for example, Ethernet.
•![]() Choose Show All to display all MPLS-TP tunnels.
Choose Show All to display all MPLS-TP tunnels.
Step 4 ![]() Select the MPLS-TP tunnel overlay you want to apply to the map.
Select the MPLS-TP tunnel overlay you want to apply to the map.
The elements and links used by the selected MPLS-TP tunnel are highlighted in the network map, and the MPLS-TP tunnel name is displayed in the window title bar as shown in Figure 19-10.
Figure 19-10 MPLS-TP Tunnel Overlay
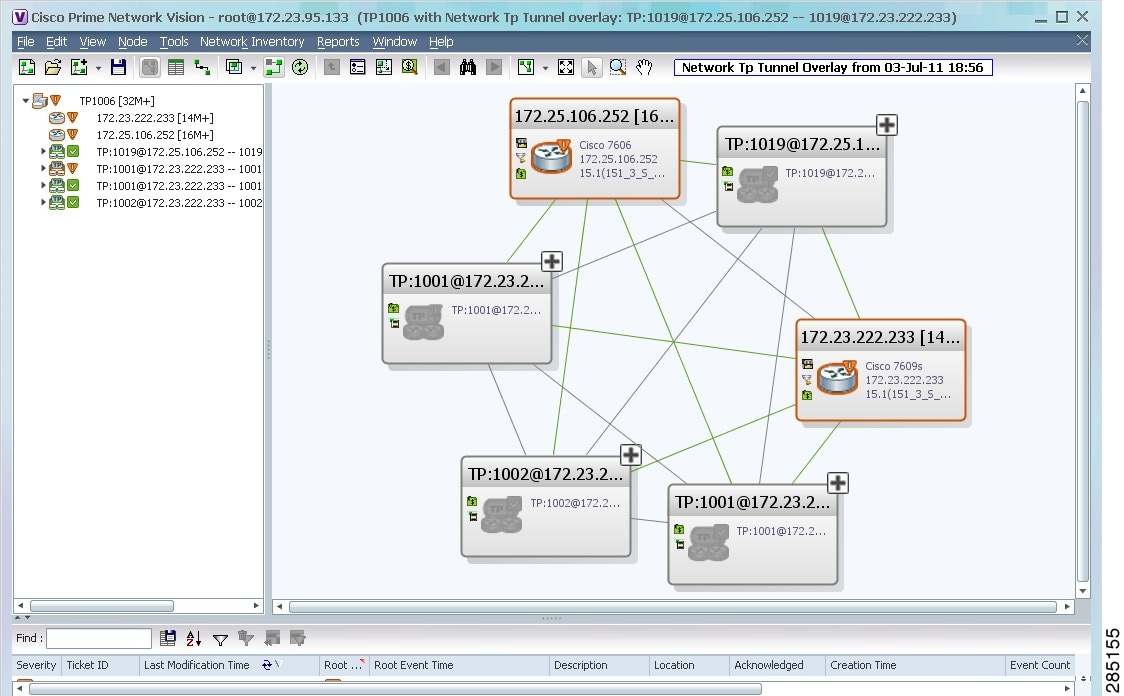

Note ![]() An overlay is a snapshot taken at a specific point in time and does not reflect changes that occur in the service. As a result, the information in an overlay can become stale. To update the overlay, click Refresh Overlay in the main toolbar.
An overlay is a snapshot taken at a specific point in time and does not reflect changes that occur in the service. As a result, the information in an overlay can become stale. To update the overlay, click Refresh Overlay in the main toolbar.
Viewing VPNs
Figure 19-11 shows a VPN displayed in the Prime Network Vision map view. In this example, the VPN is selected in the navigation pane, so the VPN details, such as virtual routers and IP interfaces, are not shown in the map view.
Figure 19-11 VPN in Prime Network Vision Map View
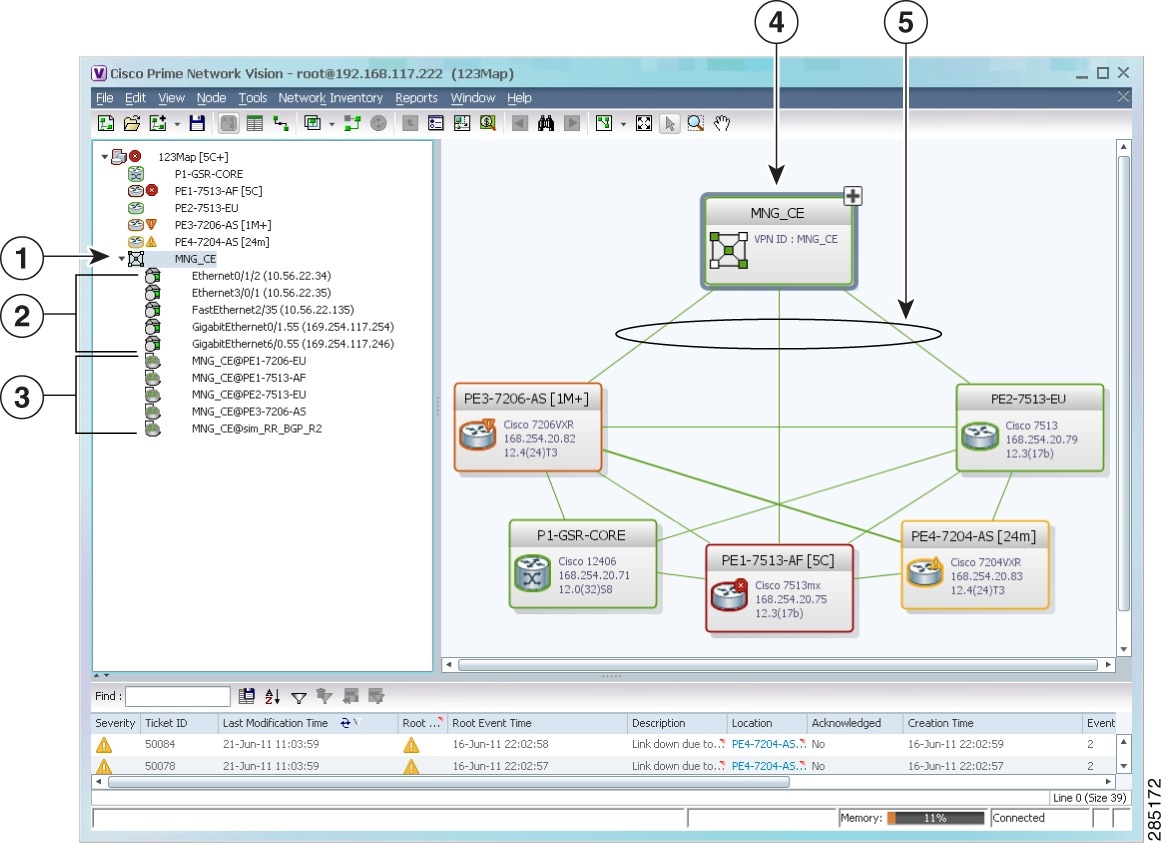
|
|
VPN in the navigation tree |
|
VPN in the map view |
|
|
Sites |
|
VPN links |
|
|
Virtual routers |
||
Figure 19-12 shows a VPN with details, including virtual routers and sites, in the Prime Network Vision map view.
Figure 19-12 VPN in Prime Network Vision Map View with VRFs and Sites
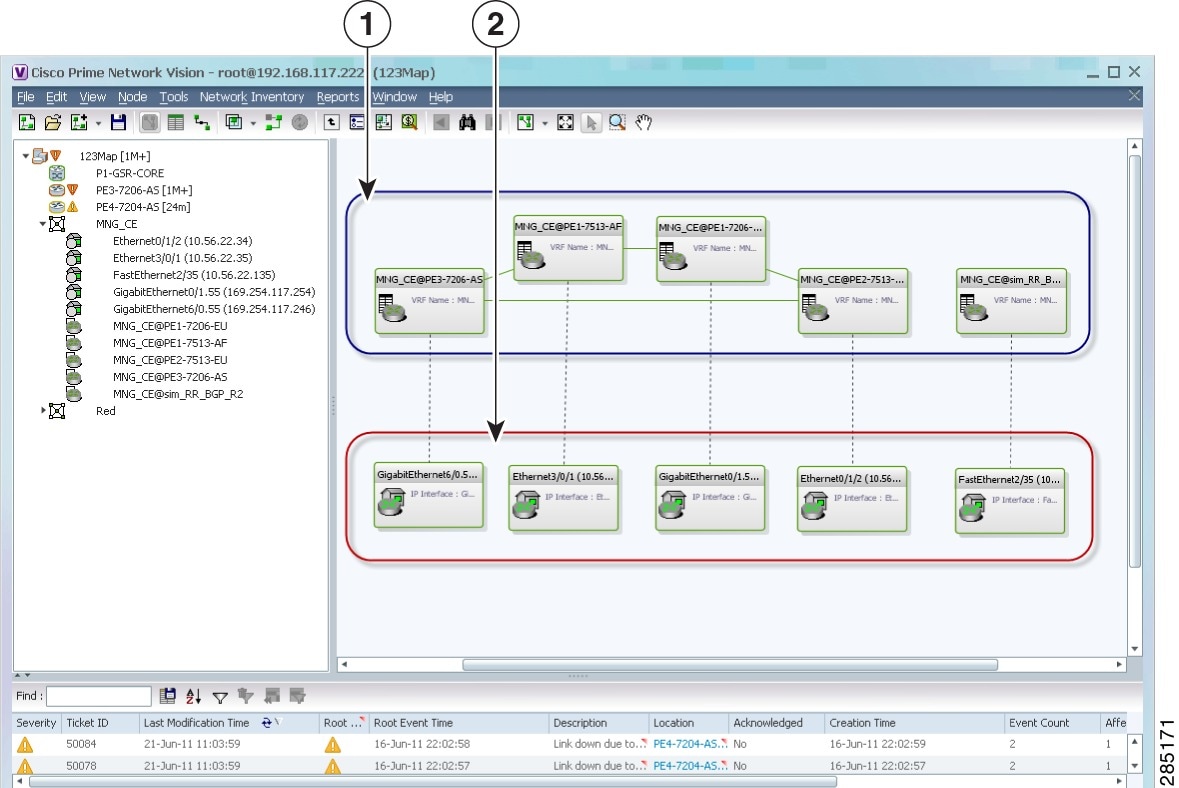
|
|
Virtual routers |
|
|
Sites |
The Prime Network Vision navigation pane displays the VPN business elements in a tree-and-branch representation. Each business element is represented by an icon in a color that reflects the highest alarm severity. The icon might also have a management state badge or alarm. For more information about icon severity colors and badges, see Prime Network Vision Status Indicators.
Table 19-6 shows the VPN icons in the Prime Network Vision map view.
|
|
|
|---|---|

|
Root (map name) or aggregation |
|
VPN |

|
Virtual router |

|
Site |
The highest level of the navigation pane displays the root or map name. The branches display the VPN and aggregated business elements as well as their names. The Layer 3 VPN sub-branch displays the virtual routers and sites contained in the VPN along with the names of the business elements. In addition, CE devices can be displayed in the Layer 2 and Layer 3 VPN sub-branches. If you select an aggregated business element in the navigation pane, the map view displays the business elements contained within the aggregated business element.
The Prime Network Vision map view displays the VPN business elements and aggregated business elements loaded in the map view, along with the names of the business elements. In addition, the map view displays the VPN topology (between the virtual routers in the VPNs) and the topology and associations between other business elements. After you select the root in the navigation pane, the map view displays all the VPNs.
Prime Network Vision presents tickets related to the map in the ticket area, which allows you to view and manage the VPN tickets.
Viewing Additional VPN Properties
Prime Network Vision allows you to select any element in the navigation pane or map view and view additional underlying properties. To view additional properties for an object, either double-click it or right-click it and choose Properties. Table 19-7 shows the additional properties available for VPN entities.
Managing VPNs
The following topics describe:
•![]() Moving a Virtual Router Between VPNs
Moving a Virtual Router Between VPNs
Creating a VPN
You can change business configurations by manually creating VPNs. The VPNs that are manually created do not contain virtual routers and sites.
To create a VPN:
Step 1 ![]() In the Prime Network Vision navigation pane, select the map root.
In the Prime Network Vision navigation pane, select the map root.
Step 2 ![]() From the File menu, choose Add to Map > VPN > New.
From the File menu, choose Add to Map > VPN > New.
Step 3 ![]() In the Create VPN dialog box, enter the following:
In the Create VPN dialog box, enter the following:
•![]() Name—A unique name for the new VPN.
Name—A unique name for the new VPN.

Note ![]() VPN business element names are case sensitive.
VPN business element names are case sensitive.
•![]() Icon—To use a custom icon for the VPN, click the button next to the Icon field and navigate to the icon file.
Icon—To use a custom icon for the VPN, click the button next to the Icon field and navigate to the icon file.

Note ![]() If a path is not specified to an icon, the default VPN icon is used (for more information about icons, see Table 19-6).
If a path is not specified to an icon, the default VPN icon is used (for more information about icons, see Table 19-6).
•![]() Description—(Optional) An additional VPN description.
Description—(Optional) An additional VPN description.
Step 4 ![]() Click OK.
Click OK.
The new VPN is added to the VPN list in the Add VPN dialog box.
For more information about loading the newly created VPN in the service view map, see Adding a VPN to a Map.
Adding a VPN to a Map
You can add a VPN to a map view if the VPN was previously created by a user or discovered by Prime Network Vision and are not currently displayed in the map.

Note ![]() Adding a VPN affects other users if they are working with the same map.
Adding a VPN affects other users if they are working with the same map.
To add an existing VPN to a map:
Step 1 ![]() In Prime Network Vision, display the map to which you want to add the VPN.
In Prime Network Vision, display the map to which you want to add the VPN.
Step 2 ![]() Do either of the following:
Do either of the following:
•![]() From the File menu, choose Add to Map > VPN > Existing.
From the File menu, choose Add to Map > VPN > Existing.
•![]() In the main toolbar, click Add to Map, then choose Add to Map > VPN > Existing.
In the main toolbar, click Add to Map, then choose Add to Map > VPN > Existing.
The Add VPN dialog box is displayed.
Step 3 ![]() Do either of the following:
Do either of the following:
•![]() Choose a search category, enter a search string, then click Go to narrow search results to a range of VPNs or a specific VPN. Search categories include:
Choose a search category, enter a search string, then click Go to narrow search results to a range of VPNs or a specific VPN. Search categories include:
–![]() Description
Description
–![]() Name
Name
The search condition is "contains." Search strings are case-insensitive. For example, if you choose the Name category and enter "net," Prime Network Vision displays VPNs that have "net" in their names whether at the beginning of the name, the middle, or the end.
•![]() Choose Show All to display all the VPNs.
Choose Show All to display all the VPNs.
Step 4 ![]() Select the VPN that you want to add to the map.
Select the VPN that you want to add to the map.

Tip ![]() Press Shift or Ctrl to choose multiple adjoining or nonadjoining VPNs.
Press Shift or Ctrl to choose multiple adjoining or nonadjoining VPNs.
Step 5 ![]() Click OK.
Click OK.
The VPN is displayed in the navigation pane and the selected map or subnetwork in the Prime Network Vision window content pane. In addition, any tickets are displayed in the ticket area.
Removing a VPN from a Map
You can remove one or more VPNs from the current active map. This change does not affect other maps. Removing a VPN from a map does not remove it from the Prime Network Vision database. The VPN will appear in the Add VPN dialog box, so you can add it back to the map at any time.
When removing VPNs from maps, keep the following in mind:
•![]() Removing a VPN affects other users if they are working with the same map view.
Removing a VPN affects other users if they are working with the same map view.
•![]() This option does not change the business configuration or database.
This option does not change the business configuration or database.
•![]() You cannot remove virtual routers or sites from the map without removing the VPN.
You cannot remove virtual routers or sites from the map without removing the VPN.
To remove a VPN, in the Prime Network Vision pane or map view, right-click the VPN and choose Remove from Map.
The VPN is removed from the map view along with all VPN elements, such as connected CE devices. Remote VPNs (extranets) are not removed.

Note ![]() If the routing information changes after an overlay is applied, the changes do not appear in the current overlay. Click Refresh Overlay to update the routing information.
If the routing information changes after an overlay is applied, the changes do not appear in the current overlay. Click Refresh Overlay to update the routing information.
Moving a Virtual Router Between VPNs
You can move a virtual router (including its sites) from one VPN to another after you create a VPN and add it to the service view map.

Note ![]() Moving a virtual router moves all of its sites as well.
Moving a virtual router moves all of its sites as well.
To move a virtual router:
Step 1 ![]() In the Prime Network Vision navigation pane or map, right-click the virtual router and choose Edit > Move selected.
In the Prime Network Vision navigation pane or map, right-click the virtual router and choose Edit > Move selected.
Step 2 ![]() Right-click the required VPN in the navigation pane or map to where you want to move the virtual router and choose Edit > Move here.
Right-click the required VPN in the navigation pane or map to where you want to move the virtual router and choose Edit > Move here.

The virtual router and its sites are displayed under the selected VPN in the navigation pane and in the map.
Working with VPN Overlays
The following topics describe:
•![]() Managing a VPN Overlay Display in the Map View
Managing a VPN Overlay Display in the Map View
•![]() Displaying VPN Callouts in a VPN Overlay
Displaying VPN Callouts in a VPN Overlay
Applying VPN Overlays
You can select and display an overlay of a specific VPN on top of the devices displayed in a map view. The overlay is a snapshot of the network that visualizes the flows between the sites and tunnel peers. When one network VPN is selected in the network map, the PE routers, MPLS routers, and physical links that carry the LSP used by the VPN are highlighted in the network map. All the devices and links that are not part of the VPN are dimmed.
The VPN service overlay allows you to isolate the parts of a network that are being used by a particular service. This information can then be used for troubleshooting. For example, the overlay can highlight configuration or design problems when bottlenecks occur and all the site interlinks use the same link.
To apply a VPN overlay:
Step 1 ![]() In Prime Network Vision, display the network map on which you want to apply an overlay.
In Prime Network Vision, display the network map on which you want to apply an overlay.
Step 2 ![]() From the main toolbar, click Choose Overlay Type and choose VPN.
From the main toolbar, click Choose Overlay Type and choose VPN.
The Select VPN Overlay dialog box is displayed.
Step 3 ![]() Do one of the following:
Do one of the following:
•![]() Choose a search category, enter a search string, then click Go to narrow the search results to a range of VPNs or a specific VPN. Search categories include:
Choose a search category, enter a search string, then click Go to narrow the search results to a range of VPNs or a specific VPN. Search categories include:
–![]() Description
Description
–![]() Name
Name
The search condition is "contains." Search strings are case-insensitive. For example, if you choose the Name category and enter "net," Prime Network Vision displays VPNs that have "net" in their names whether net appears at the beginning of the name, the middle, or at the end: for example, Ethernet.
•![]() Choose Show All to display all the VPNs.
Choose Show All to display all the VPNs.
Step 4 ![]() Select the VPN overlay that you want to apply to the map.
Select the VPN overlay that you want to apply to the map.
The PE routers, MPLS routers, and physical links used by the selected VPN are highlighted in the network map. The VPN name is displayed in the title of the window.

Note ![]() An overlay is a snapshot taken at a specific point in time and does not reflect changes that occur in the service. As a result, the information in an overlay can become stale. To update the overlay, click Refresh Overlay in the main toolbar.
An overlay is a snapshot taken at a specific point in time and does not reflect changes that occur in the service. As a result, the information in an overlay can become stale. To update the overlay, click Refresh Overlay in the main toolbar.
Managing a VPN Overlay Display in the Map View
After a VPN overlay is applied to a map, you can manage its display by using the overlay tools in the main toolbar:
•![]() To display the overlay, click Show Overlay on the main toolbar.
To display the overlay, click Show Overlay on the main toolbar.
•![]() To hide an active overlay, click Hide Overlay on the main toolbar.
To hide an active overlay, click Hide Overlay on the main toolbar.

Note ![]() The Show Overlay button is a toggle. When clicked, the overlay is displayed. When clicked again, the overlay is hidden.
The Show Overlay button is a toggle. When clicked, the overlay is displayed. When clicked again, the overlay is hidden.
•![]() To remove the VPN overlay, choose Show Overlay Type > None.
To remove the VPN overlay, choose Show Overlay Type > None.
Displaying VPN Callouts in a VPN Overlay
You can display or hide the callouts for VPN links displayed in a VPN overlay to show the details of the sites that are interlinked through the selected links. The callouts (see Figure 19-13) enable you to view the VPN traffic links for a specific link (either bidirectional or unidirectional).

Note ![]() The link must be displayed in the VPN overlay and not dimmed for you to display the link callouts.
The link must be displayed in the VPN overlay and not dimmed for you to display the link callouts.
Figure 19-13 Callouts Window
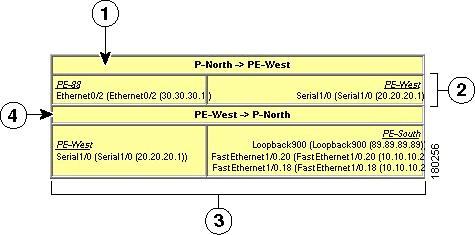
To display or hide the callouts:
Step 1 ![]() In the Prime Network Vision window, display the map view with the VPN overlay.
In the Prime Network Vision window, display the map view with the VPN overlay.
Step 2 ![]() Right-click the required link in the map view and choose Show Callouts.
Right-click the required link in the map view and choose Show Callouts.
Step 3 ![]() To hide the callouts, right-click the link in the map view that is displaying the callouts and choose Hide Callouts.
To hide the callouts, right-click the link in the map view that is displaying the callouts and choose Hide Callouts.
Monitoring MPLS Services
The following topics provide details for viewing MPLS services and technologies:
•![]() Viewing VRF Egress and Ingress Adjacents
Viewing VRF Egress and Ingress Adjacents
•![]() Viewing Label Switched Entity Properties
Viewing Label Switched Entity Properties
•![]() Viewing BFD Session Properties
Viewing BFD Session Properties
•![]() Viewing Cross-VRF Routing Entries
Viewing Cross-VRF Routing Entries
•![]() Viewing Pseudowire End-to-End Emulation Tunnels
Viewing Pseudowire End-to-End Emulation Tunnels
•![]() Viewing MPLS TE Tunnel Information
Viewing MPLS TE Tunnel Information
Viewing VPN Properties
To view the properties of a VPN:
Step 1 ![]() In the Prime Network Vision navigation pane or map view, do either of the following:
In the Prime Network Vision navigation pane or map view, do either of the following:
•![]() If the VPN icon is of the largest size, click the Properties button.
If the VPN icon is of the largest size, click the Properties button.
•![]() Right-click the VPN and choose Properties.
Right-click the VPN and choose Properties.
The VPN Properties window displays the following information:
•![]() Name—Name of the VPN.
Name—Name of the VPN.
•![]() ID—Unique identifier assigned to the VPN.
ID—Unique identifier assigned to the VPN.
Step 2 ![]() Click Close to close the VPN Properties dialog box.
Click Close to close the VPN Properties dialog box.
Viewing Site Properties
Prime Network Vision enables you to view site properties, including the interfaces that are configured on the PE device. The displayed properties reflect the configuration that Prime Network Vision automatically discovered for the device.
To view site properties, in the Prime Network Vision navigation pane or map view, right-click the required site and choose Properties.
Table 19-8 describes the information that is displayed in the Router IP Interface Properties window:
|
|
|
|---|---|
Name |
Name of the site, such as FastEthernet4/1.252. |
State |
Interface state, either Up or Down. |
IP Address |
IP address of the interface. |
Mask |
Network mask. |
Interface Description |
Description applied to the interface. |
Associated Entity |
Element and interface associated with the site, hyperlinked to its entry in physical inventory. |
|
|
|
Subnet |
IP address and subnet mask. Note |
Type |
Address type, such as Primary, Secondary, or IPv6 Unicast. |
Viewing VRF Properties
Prime Network Vision enables you to view VRF properties, including the VRF route distinguisher, import and export route targets, and any provisioned sites and VRF routes.
To view VRF properties, do either of the following in map view:
•![]() Double-click the element configured for VRFs.
Double-click the element configured for VRFs.
•![]() Expand the required VPN and double-click the virtual router.
Expand the required VPN and double-click the virtual router.
The VRF properties window is displayed as shown in Figure 19-14.
Figure 19-14 VRF Properties
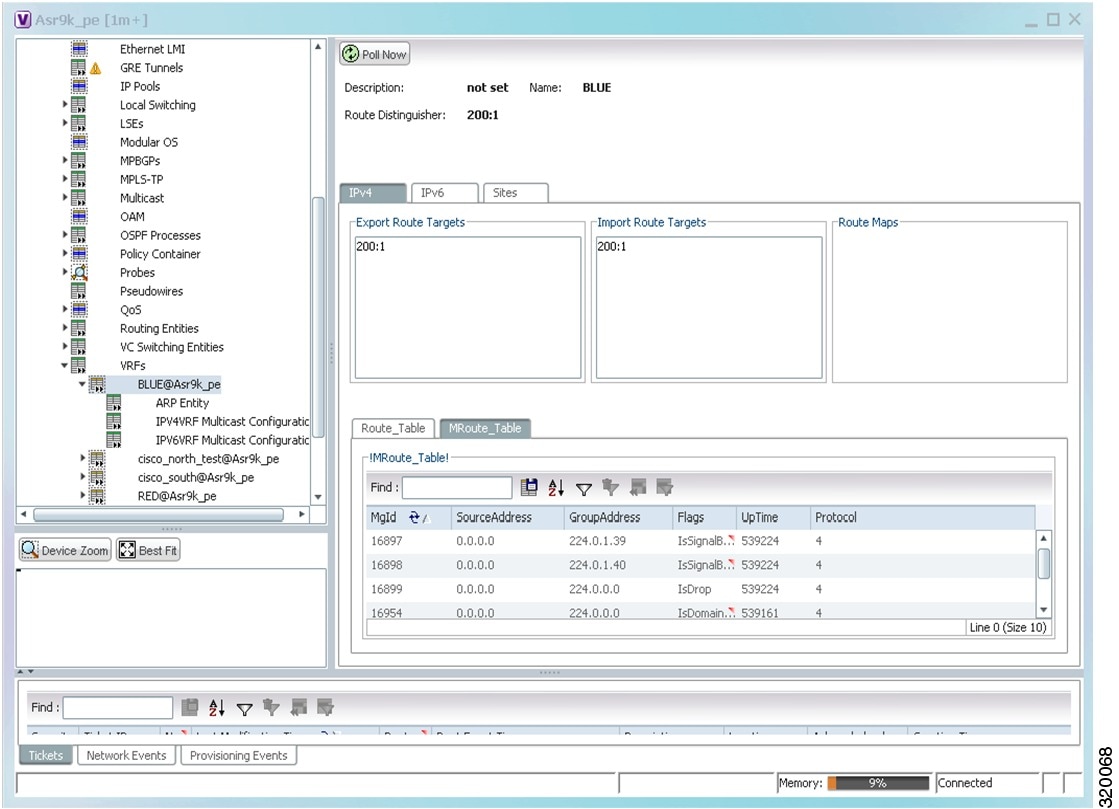
The VRF Properties window contains the VRF routing table for the device. The table is a collection of routes that are available or reachable to all the destinations or networks in the VRF. The forwarding table also contains MPLS encapsulation information.
Table 19-9 describes the information displayed in the VRF Properties window.

Note ![]() The VRF Properties window only displays properties and attributes that are provisioned in the VRF. You might not see all the fields and tabs described in Table 19-9.
The VRF Properties window only displays properties and attributes that are provisioned in the VRF. You might not see all the fields and tabs described in Table 19-9.
|
|
|
|---|---|
Route Distinguisher |
|
Name |
VRF name. |
Description |
Description of the VRF. |
|
|
|
Export Route Targets |
IPv4 export route targets contained by the VRF. |
Import Route Targets |
IPv4 import route targets contained by the VRF. |
Route Maps |
Route maps for the VRF. |
|
|
|
Export Route Targets |
IPv6 export route targets contained by the VRF. |
Import Route Targets |
IPv6 import route targets contained by the VRF. |
Route Maps |
Route maps for the VRF. |
|
|
|
Destination |
Destination of the specific network. |
Prefix Length |
Length of the network prefix in bits. |
Next Hop |
Next routing hop. |
Outgoing Interface |
Name of the outgoing interface; displayed if the Routing Protocol type is local. |
Type |
Route type: Direct (local), Indirect, or Static. |
Routing Protocol |
Routing protocol used to communicate with the other sites and VRFs: BGP or local. |
BGP Next Hop |
Border Gateway Protocol (BGP) next hop. This is the PE address from which to continue to get to a specific address. This field is empty when the routing entry goes to the CE. |
Bottom In Label |
Innermost label that is expected when MPLS traffic is received. |
Bottom Out Label |
Innermost label sent with MPLS traffic. |
Outer Label |
Outermost or top label in the stack used for MPLS traffic. |
|
|
|
Source Address |
The source IP address from where the multicast information is sent. |
Group Address |
The group IP address of the multicast. |
Flags |
The flag information pertaining to the multicast. |
Up Time |
The amount of time the interface has been active. |
Protocol |
The protocol information, which can be 4 or 6. |
|
|
|
Name |
Site name. |
IP Address |
IP address of the interface. |
Mask |
Subnet mask. |
State |
State of the subinterface: Up or Down. |
Associated Entity |
Element and interface associated with the site, hyperlinked to its entry in physical inventory. |
Description |
Interface description. |
Input Access List |
Access list applied to the inbound traffic. |
Output Access List |
Access list applied to the outbound traffic. |
Rate Limits |
If a rate limit is configured on an IP interface, the limit is shown as an IP interface property. This option is checked when a rate limit is defined on the IP interface, meaning the access list is a rate limit access list. IP interface traffic is measured and includes the average rate, normal burst size, excess burst size, conform action, and exceed action. Note Note |
IP Sec Map Name |
IP Security (IPsec) map name. |
Site Name |
Name of the business element to which the interface is attached. |
Viewing VRF Multicast Configuration details
To view global multicast configuration details for a VRF:
Step 1 ![]() Right-click on the required device and select Inventory.
Right-click on the required device and select Inventory.
Step 2 ![]() In the Inventory window, choose Logical Inventory > VRFs > vrf (where vrf is the required VRF) > IPV4VRF Multicast Configuration or IPV6VRF Multicast Configuration. The route policies configured on the device are displayed in the content pane.
In the Inventory window, choose Logical Inventory > VRFs > vrf (where vrf is the required VRF) > IPV4VRF Multicast Configuration or IPV6VRF Multicast Configuration. The route policies configured on the device are displayed in the content pane.
Table 19-10 describes the information that is displayed in the Router IP Interface Properties window:
Viewing VRF Egress and Ingress Adjacents
Prime Network Vision enables you to view the exporting and importing neighbors by displaying the VRF egress and ingress adjacents. In addition, you can view the connectivity between the VRFs for the route targets and view their properties. For example, if VRF A retrieved route target import X, you can view all VRFs that export X as a route target whether it is in the same or another VPN.
To display the VRF egress and ingress adjacents, you can use either an element configured for VRFs or a virtual router:
•![]() To use an element configured for VRFs:
To use an element configured for VRFs:
a. ![]() Double-click the element configured for VRFs.
Double-click the element configured for VRFs.
b. ![]() In the inventory window, choose Logical Inventory > VRFs > vrf where vrf is the required VRF.
In the inventory window, choose Logical Inventory > VRFs > vrf where vrf is the required VRF.
c. ![]() Right-click the required VRF and choose Show VRF Egress Adjacents or Show VRF Ingress Adjacents.
Right-click the required VRF and choose Show VRF Egress Adjacents or Show VRF Ingress Adjacents.
•![]() To use a virtual router, right-click the required VRF in the navigation pane, and choose Show VRF Egress Adjacents or Show VRF Ingress Adjacents.
To use a virtual router, right-click the required VRF in the navigation pane, and choose Show VRF Egress Adjacents or Show VRF Ingress Adjacents.
Table 19-11 describes the information displayed in the Adjacents window.
Viewing Routing Entities
To view routing entities:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity.
In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity.
The routing information is displayed as shown in Figure 19-15.
Figure 19-15 Routing Entity Table
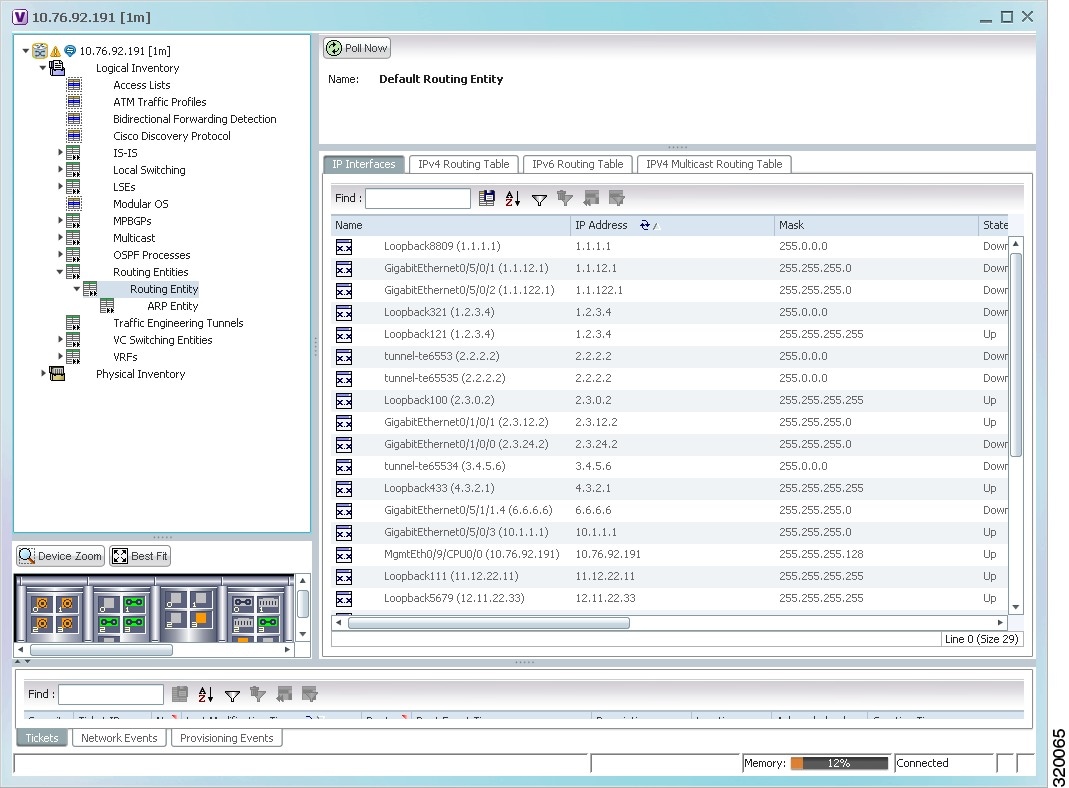
Table 19-12 describes the information that is displayed in the Routing Entity table.
|
|
|
|---|---|
Name |
Name of the routing entity. |
|
|
|
Name |
Site name. |
IP Address |
IP address of the interface. |
Mask |
Network mask. |
State |
State of the subinterface: Up or Down. |
Associated Entity |
Interface associated with the routing entity, hyperlinked to its location in physical inventory. |
Description |
Description of the interface. |
Input Access List |
If an input access list is assigned to an IP interface, the list is shown as an IP interface property, and a hyperlink highlights the related access list in the Access List table. When an access list is assigned to the inbound traffic on an IP interface, the actions assigned to the packet are performed. |
VRRP Group |
If a VRRP group is configured on an IP interface, the information is shown as an IP interface property. This option is checked when a rate limit is defined on the IP interface. Note |
Output Access List |
If an output access list is assigned to an IP interface, the list is shown as an IP interface property, and a hyperlink highlights the related access list in the Access List table. When an access list is assigned to the outbound traffic on an IP interface, the actions assigned to the packet are performed. |
Rate Limits |
If a rate limit is configured on an IP interface, the limit is shown as an IP interface property. This option is checked when a rate limit is defined on the IP interface, meaning the access list is a rate limit access list. IP interface traffic is measured and includes the average rate, normal burst size, excess burst size, conform action, and exceed action. Note Note |
IP Sec Map Name |
IP Security (IPsec) crypto map name. |
Site Name |
Name of the business element to which the interface is attached. |
|
|
|
Destination |
Destination of the specific network. |
Outgoing If Name |
Name of the outgoing interface; displayed if the Routing Protocol type is local. |
Type |
Routing type: Direct, Indirect, Static, Other, Invalid, or Unknown. |
Next Hop |
IP address from which to continue to get to a specific address. This field is empty when the routing entry goes to a PE router. |
Prefix Length |
Length of the network prefix in bits. |
Route Protocol Type |
Routing protocol used to communicate with other routers. |
IPv4 and IPv6 Multicast Routing Tabs |
|
Source Address |
The source IP address from where the multicast information is sent. |
Group Address |
The group IP address of the multicast. |
Flags |
The flag information pertaining to the multicast. |
Up Time |
The amount of time the interface has been active. |
Protocol |
The protocol information, which can be 4 or 6. |
Viewing the ARP Table
To view the ARP table:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity > ARP.
In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity > ARP.
Table 19-13 describes the information that is displayed in the ARP table.
Viewing the NDP Table
Neighbor Discovery Protocol (NDP) is used with IPv6 to discover other nodes, determine the link layer addresses of other nodes, find available routers, and maintain reachability information about the paths to other active neighbor nodes.
NDP functionality includes:
•![]() Router discovery
Router discovery
•![]() Autoconfiguration of addresses (stateless address autoconfiguration [SLAAC])
Autoconfiguration of addresses (stateless address autoconfiguration [SLAAC])
•![]() IPv6 address resolution (replaces Address Resolution Protocol [ARP])
IPv6 address resolution (replaces Address Resolution Protocol [ARP])
•![]() Neighbor reachability (neighbor unreachability detection [NUD])
Neighbor reachability (neighbor unreachability detection [NUD])
•![]() Duplicate address detection (DAD)
Duplicate address detection (DAD)
•![]() Redirection
Redirection
To view the NDP table:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity > ARP Entity.
In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity > ARP Entity.
Step 3 ![]() Click the NDP Table tab.
Click the NDP Table tab.
Figure 19-16 shows an example of the NDP Table tab.
Figure 19-16 NDP Table in Logical Inventory
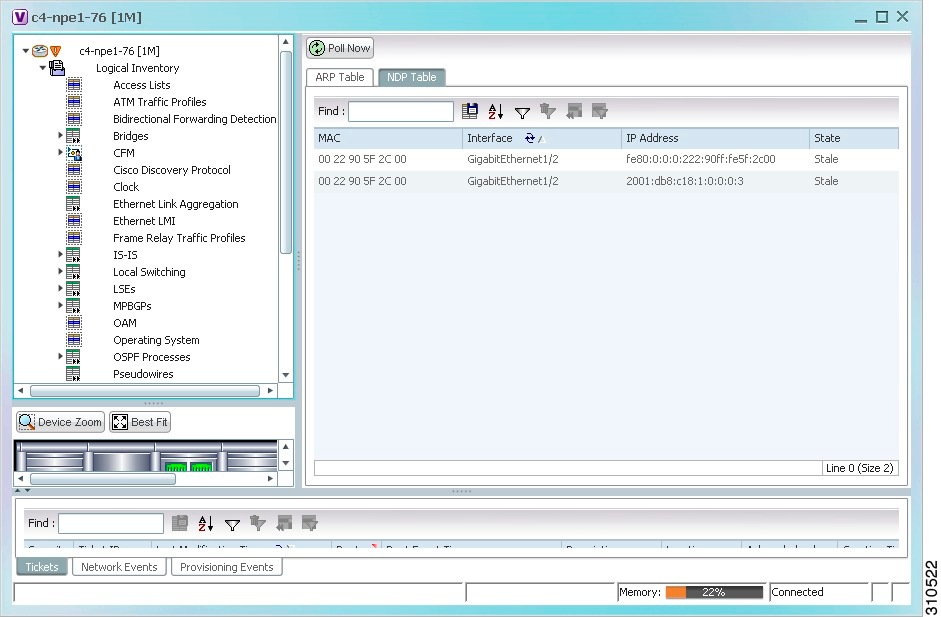
Table 19-14 describes the information displayed for NDP.
Viewing Rate Limit Information
To view rate limit information:
Step 1 ![]() Right-click the required element in Prime Network Vision and choose Inventory.
Right-click the required element in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity.
In the logical inventory window, choose Logical Inventory > Routing Entities > Routing Entity.
Step 3 ![]() In the IP Interfaces tab, double-click the required interface to view the IP interface properties. If a rate limit is configured on the IP interface, the Rate Limits tab is displayed.
In the IP Interfaces tab, double-click the required interface to view the IP interface properties. If a rate limit is configured on the IP interface, the Rate Limits tab is displayed.

Note ![]() Rate limit information is relevant only for Cisco IOS devices.
Rate limit information is relevant only for Cisco IOS devices.
Table 19-15 describes the information that is displayed in the Rate Limits tab of the IP Interface Properties dialog box.
Viewing VRRP Information
Virtual Router Redundancy Protocol (VRRP) is a non-proprietary redundancy protocol that is designed to increase the availability of the static default gateway servicing hosts on the same subnet. This increased reliability is achieved by advertising a virtual router (a representation of master and backup routers acting as a group) as a default gateway to the hosts instead of one physical router. Two or more physical routers are then configured to stand for the virtual router, with only one doing the actual routing at any given time. If the current physical router that is routing the data on behalf of the virtual router fails, another physical router automatically replaces it. The physical router that forwards data on behalf of the virtual router is called the master router; physical routers standing by to take over for the master router if needed are called backup routers.
To view VRRP information:
Step 1 ![]() Double-click the required element in Prime Network Vision.
Double-click the required element in Prime Network Vision.
Step 2 ![]() In logical inventory, choose Logical Inventory > Routing Entities > Routing Entity.
In logical inventory, choose Logical Inventory > Routing Entities > Routing Entity.
Step 3 ![]() In the IP Interfaces tab, double-click the required interface to view the IP interface properties. If VRRP is configured on the IP interface, the VRRP Groups tab is displayed.
In the IP Interfaces tab, double-click the required interface to view the IP interface properties. If VRRP is configured on the IP interface, the VRRP Groups tab is displayed.
Figure 19-17 VRRP Properties in IP Interface Properties Window
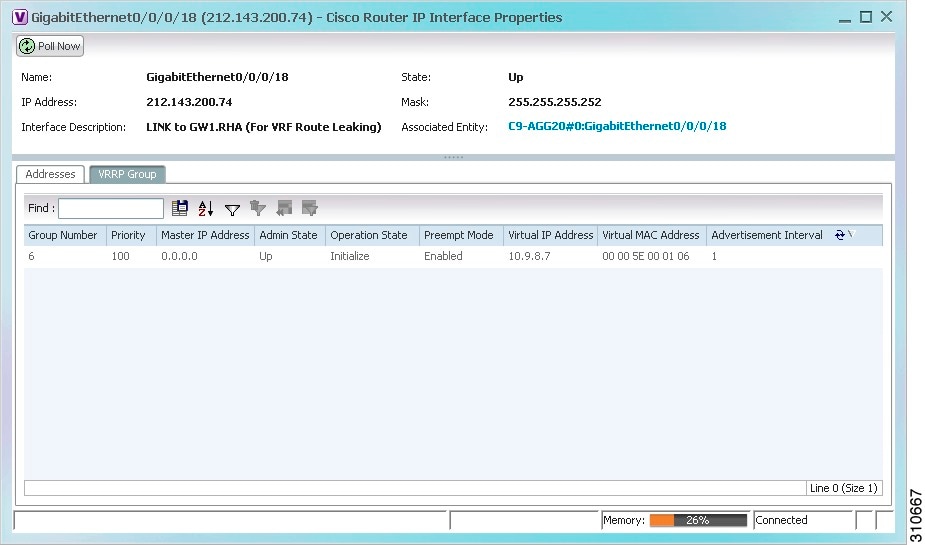
Table 19-16 describes the information in the VRRP Groups tab.
Viewing Label Switched Entity Properties
Logical inventory can display any or all of the following tabs for label switched entities, depending on the configuration:
•![]() Label Switching Table—Describes the MPLS label switching entries used for traversing MPLS core networks.
Label Switching Table—Describes the MPLS label switching entries used for traversing MPLS core networks.
•![]() LDP Neighbors—Details all MPLS interface peers that use the Label Distribution Protocol (LDP). LDP enables neighboring provider (P) or PE routers acting as label switch routers (LSRs) in an MPLS-aware network to exchange label prefix binding information, which is required to forwarding traffic. The LSRs discover potential peers in the network with which they can establish LDP sessions in order to negotiate and exchange the labels (addresses) to be used for forwarding packets.
LDP Neighbors—Details all MPLS interface peers that use the Label Distribution Protocol (LDP). LDP enables neighboring provider (P) or PE routers acting as label switch routers (LSRs) in an MPLS-aware network to exchange label prefix binding information, which is required to forwarding traffic. The LSRs discover potential peers in the network with which they can establish LDP sessions in order to negotiate and exchange the labels (addresses) to be used for forwarding packets.
Two LDP peer discovery types are supported:
–![]() Basic discovery—Used to discover directly connected LDP LSRs. An LSR sends hello messages to the all-routers-on-this-subnet multicast address, on interfaces for which LDP has been configured.
Basic discovery—Used to discover directly connected LDP LSRs. An LSR sends hello messages to the all-routers-on-this-subnet multicast address, on interfaces for which LDP has been configured.
–![]() Extended discovery—Used between indirectly connected LDP LSRs. An LSR sends targeted hello messages to specific IP addresses. Targeted sessions are configured because the routers are not physically connected, and broadcasting would not reach the peers. The IP addresses of both peers are required for extended discovery.
Extended discovery—Used between indirectly connected LDP LSRs. An LSR sends targeted hello messages to specific IP addresses. Targeted sessions are configured because the routers are not physically connected, and broadcasting would not reach the peers. The IP addresses of both peers are required for extended discovery.
If two LSRs are connected with two separate interfaces, two LDP discoveries are performed.
•![]() MPLS Interfaces—Contains information on MPLS interfaces and whether traffic engineering tunnels are configured on an interface.
MPLS Interfaces—Contains information on MPLS interfaces and whether traffic engineering tunnels are configured on an interface.
•![]() MPLS Label Range—Identifies whether MPLS uses static or dynamic routing, and the label range.
MPLS Label Range—Identifies whether MPLS uses static or dynamic routing, and the label range.
•![]() Traffic Engineering LSPs—Describes the MPLS traffic engineering Label Switched Paths (LSPs) provisioned on the switch entity. MPLS traffic engineering LSP, an extension to MPLS TE, provides flexibility when configuring LSP attributes for MPLS TE tunnels.
Traffic Engineering LSPs—Describes the MPLS traffic engineering Label Switched Paths (LSPs) provisioned on the switch entity. MPLS traffic engineering LSP, an extension to MPLS TE, provides flexibility when configuring LSP attributes for MPLS TE tunnels.
•![]() VRF Table—Describes MPLS paths that terminate locally at a VRF.
VRF Table—Describes MPLS paths that terminate locally at a VRF.
To view information for label switched entities:
Step 1 ![]() Double-click the required device in Prime Network Vision.
Double-click the required device in Prime Network Vision.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > LSEs > Label Switching.
In the logical inventory window, choose Logical Inventory > LSEs > Label Switching.
Table 19-17 describes the information that is displayed for label switched entities.
Step 3 ![]() Double-click an entry in any of the tables to view additional properties for that entry.
Double-click an entry in any of the tables to view additional properties for that entry.
Multicast Label Switching
Multicast Label Distribution protocol (mLDP) provides extensions to the Label Distribution Protocol (LDP) for the setup of point-to-multipoint (P2MP) and multipoint-to-multipoint (MP2MP) Label Switched Paths (LSPs) in MultiProtocol Label Switching (MPLS) networks. A P2MP LSP allows traffic from a single root (or ingress) node to be delivered to a number of leaf (or egress) nodes.
A MP2MP LSP allows traffic from multiple ingress nodes to be delivered to multiple egress nodes. Only a single copy of the packet will be sent on any link traversed by a multipoint LSP. Container is the holder of MPLS MLDP databases and neighbors instances for Multicast.
Viewing MLDP Database Information
To view the MLDP database information:
Step 1 ![]() Double-click the required device in Prime Network Vision.
Double-click the required device in Prime Network Vision.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > LSEs > Label Switching > Multicast Label Switching > Databases. The database information is displayed in the MLDP Databases content pane.
In the logical inventory window, choose Logical Inventory > LSEs > Label Switching > Multicast Label Switching > Databases. The database information is displayed in the MLDP Databases content pane.
Step 3 ![]() Select a database from the content pane, right-click and choose the Properties option. The MLDP Database Properties dialog box is displayed. You can click on the tabs to view more details.
Select a database from the content pane, right-click and choose the Properties option. The MLDP Database Properties dialog box is displayed. You can click on the tabs to view more details.
Table 19-19 describes the information that is displayed for MLDP Database Properties dialog box.
Viewing the MLDP Neighbors Information
To view information of MLDP neighbors:
Step 1 ![]() Double-click the required device in Prime Network Vision.
Double-click the required device in Prime Network Vision.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > LSEs > Label Switching > Multicast Label Switching > MLDP Neighbors. The MLDP peer information is displayed in the MLDP Peers content pane.
In the logical inventory window, choose Logical Inventory > LSEs > Label Switching > Multicast Label Switching > MLDP Neighbors. The MLDP peer information is displayed in the MLDP Peers content pane.
Step 3 ![]() Select a peer id from the content pane, right-click and choose the Properties option. The Peer ID Properties dialog box is displayed.
Select a peer id from the content pane, right-click and choose the Properties option. The Peer ID Properties dialog box is displayed.
Table 19-20 describes the information that is displayed for Peer ID Properties dialog box.
Viewing MP-BGP Information
The MP-BGP branch displays information about a router's BGP neighbors and cross-connect VRFs.

Note ![]() If there are multiple MP-BGP links between two devices, Prime Network displays each link in the content pane map view.
If there are multiple MP-BGP links between two devices, Prime Network displays each link in the content pane map view.
To view MP-BGP information:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > MPBGPs > MPBGP.
In the logical inventory window, choose Logical Inventory > MPBGPs > MPBGP.
Table 19-21 describes the information that is displayed for MP-BGP.
Viewing 6rd Tunnel Properties
IPv6 rapid deployment (6rd) is a mechanism that allows stateless tunneling of IPv6 over IPv4. From Prime Network Vision 3.8, 6rd is supported on the following devices:
•![]() Cisco 7600 series devices
Cisco 7600 series devices
•![]() Cisco ASR 1000 series devices
Cisco ASR 1000 series devices
To view 6rd tunnel properties:
Step 1 ![]() In Prime Network Vision, double-click the required device.
In Prime Network Vision, double-click the required device.
Step 2 ![]() In the inventory window, choose Logical Inventory > 6rd Tunnels.
In the inventory window, choose Logical Inventory > 6rd Tunnels.
The 6rd tunnel properties are displayed as shown in Figure 19-18.
Figure 19-18 6rd Tunnel Properties in Logical Inventory
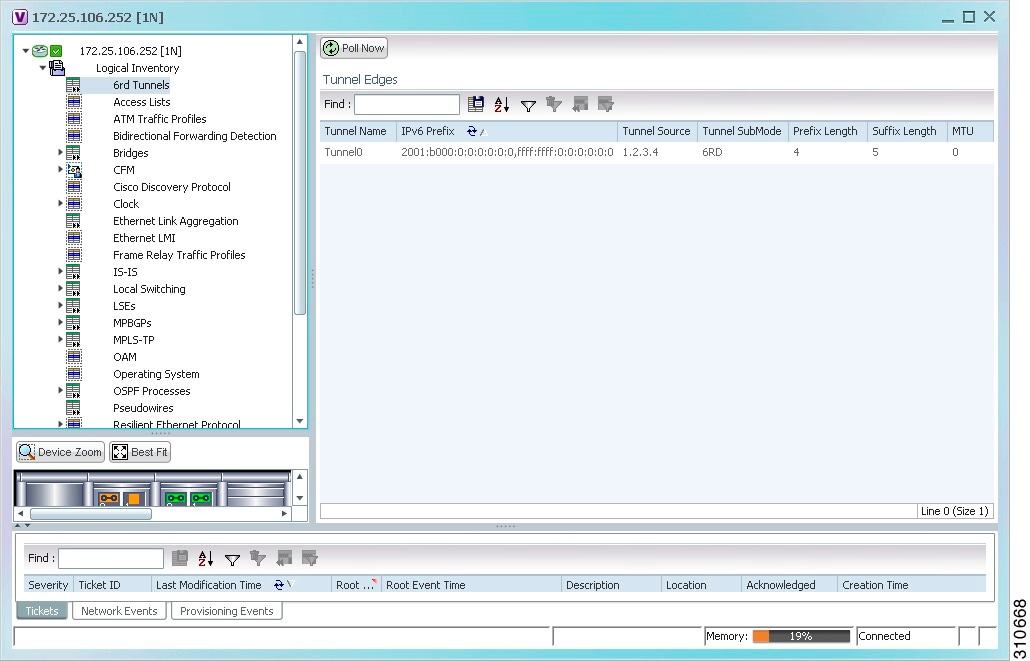
Table 19-22 describes the information displayed for 6rd tunnels.
Viewing BFD Session Properties
Bidirectional Forwarding Detection (BFD) is used to detect communication failures between two elements, or endpoints, that are connected by a link, such as a virtual circuit, tunnel, or LSP. BFD establishes sessions between the two endpoints over the link. If more than one link exists, BFD establishes a session for each link.
Prime Network Vision supports BFD with the following protocols: BGP, IPv4 (static), IPv6 (static), IS-IS, LAG (Ether channel), MPLS TE, MPLS-TP, and OSPF.
To view BFD session properties that are configured on an element:
Step 1 ![]() In Prime Network Vision, double-click the required device.
In Prime Network Vision, double-click the required device.
Step 2 ![]() In the inventory window, choose Logical Inventory > Bidirectional Forwarding Detection.
In the inventory window, choose Logical Inventory > Bidirectional Forwarding Detection.
The properties for BFD sessions are displayed as shown in Figure 19-19.
Figure 19-19 BFD Session Properties
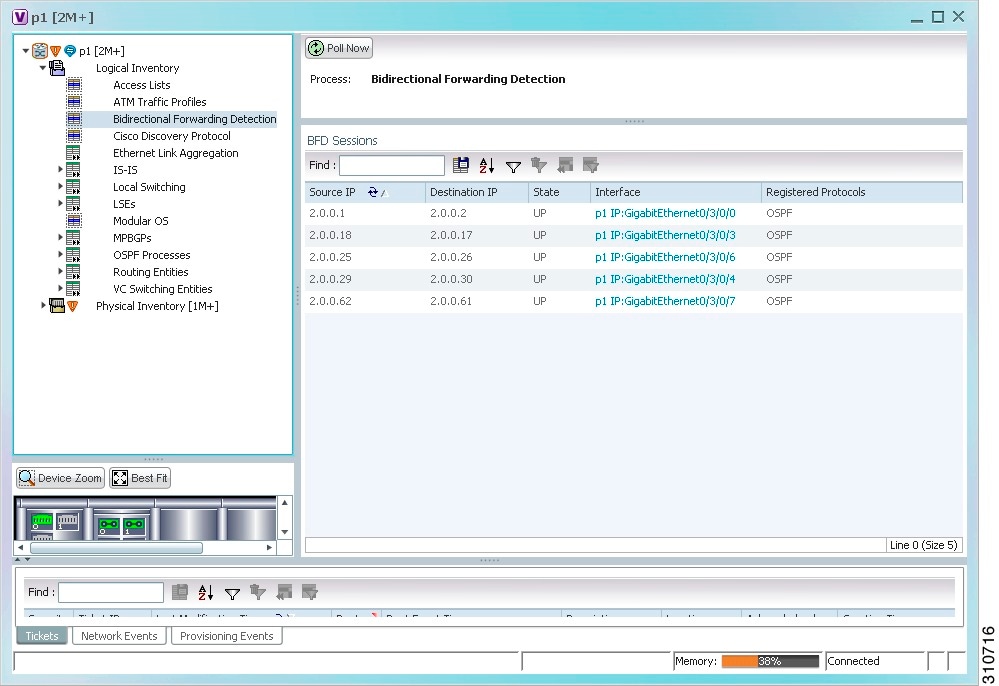
Table 19-23 describes the information displayed for BFD sessions.
For MPLS-TP BFD sessions, the information in Table 19-24 is displayed.
Step 3 ![]() To view additional properties, double-click the required entry in the Sessions table.
To view additional properties, double-click the required entry in the Sessions table.
Table 19-25 describes the information that is displayed in the Session Properties window.
Viewing Cross-VRF Routing Entries
Cross-VRF routing entries display routing information learned from the BGP neighbors (BGP knowledge base).
To view properties for cross-VRF routing entries:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > MPBGPs > MPBGP.
In the logical inventory window, choose Logical Inventory > MPBGPs > MPBGP.
Step 3 ![]() Click the Cross VRFs tab.
Click the Cross VRFs tab.
Step 4 ![]() Double-click the required entry in the list of cross-VRFs.
Double-click the required entry in the list of cross-VRFs.
The Cross VRF Properties window is displayed, containing the information described in Table 19-26.
Viewing Pseudowire End-to-End Emulation Tunnels
The Pseudowires branch in logical inventory displays a list of the Layer 2 tunnel edge properties (per edge), including tunnel status and VC labels.
To view pseudowire properties:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Pseudowires.
In the logical inventory window, choose Logical Inventory > Pseudowires.
The Tunnel Edges table is displayed and contains the information described in Table 19-27.
Viewing MPLS TE Tunnel Information
Prime Network Vision automatically discovers MPLS TE tunnels and enables you to view MPLS TE tunnel information in inventory.
To view MPLS TE tunnel information:
Step 1 ![]() Right-click the required device in Prime Network Vision and choose Inventory.
Right-click the required device in Prime Network Vision and choose Inventory.
Step 2 ![]() In the logical inventory window, choose Logical Inventory > Traffic Engineering Tunnels.
In the logical inventory window, choose Logical Inventory > Traffic Engineering Tunnels.
Table 19-28 describes the information that is displayed in the Tunnel Edges table.
The Traffic Engineering LSPs tab in the LSEs branch in logical inventory displays TE tunnel LSP information.
For details about the information displayed for TE tunnel LSPs, see Traffic Engineering LSPs.
Configuring VRF
VRF commands configures routes that are available or reachable to all the destinations or networks in the VRF.
Unless otherwise noted, all of the following commands are launched by right-clicking the VRF node and choosing Commands > Configuration.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|---|---|
Modify VRF Delete VRF |
Configures VRF properties, including the VRF route distinguisher, import and export route targets, and any provisioned sites and VRF routes. |
Configuring IP Interface
Unless otherwise noted, all of the following commands are launched by right-clicking the Routing Entities and choosing Commands > Configuration.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|---|---|
Create Interface Modify Interface Delete Interface Configure Secondary IP Address Delete Secondary IP Address |
Configure IP interface as part of the routing entity. |
Configuring MPLS-TP
Use these commands to configures MPLS transport profile (MPLS-TP) on the router.
Unless otherwise noted, all of the following commands are launched by right-clicking the appropriate node and selecting MPLS-TP Global > Commands > Configuration.
The table below lists the MPLS-TP configuration commands and the MPLS-TP supported network elements.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
Keep the following in mind:
•![]() LSP Path Lockout can be accessed at both the tunnel level and endpoint level. If you run the command at the tunnel level, you must indicate whether the Lsp is protected or working.
LSP Path Lockout can be accessed at both the tunnel level and endpoint level. If you run the command at the tunnel level, you must indicate whether the Lsp is protected or working.
•![]() To run the Global Configuration, BFD Configuration, and Link Configuration commands on the Cisco Carrier Packet Transport (CPT) System, right-click the device in the Prime Network Vision List or Map View, and click Logical Inventory > CPT Context Container.
To run the Global Configuration, BFD Configuration, and Link Configuration commands on the Cisco Carrier Packet Transport (CPT) System, right-click the device in the Prime Network Vision List or Map View, and click Logical Inventory > CPT Context Container.
Locking/Unlocking MPLS-TP Tunnels in Bulk
An MPLS-TP network has one or multiple LSPs running between endpoint devices. If you want to shutdown one of the interfaces in the network, the MPLS-TP packet must be diverted through an alternative LSP. This can be achieved by locking the interface.
The MPLS-TP bulk lockout/unlock option in Prime Network allows you to lock or unlock multiple MPLS-TP tunnels on different VNEs at the same time.
Before attempting to lock or unlock a tunnel, ensure that MPLS-TP tunnels have been configured for the link. Also, ensure that you have the appropriate rights (Configurator and above) to lock or unlock a tunnel.
Locking MPLS-TP Tunnels
To lock MPLS-TP tunnels in bulk:
Step 1 ![]() In the map view, right-click the required link and choose Properties.
In the map view, right-click the required link and choose Properties.
Step 2 ![]() In the link properties window, right-click on the required physical link and choose the Show MPLS-TP tunnels option. The MPLS-TP tunnels' commands dialog box is displayed, which lists all the tunnels in the selected link.
In the link properties window, right-click on the required physical link and choose the Show MPLS-TP tunnels option. The MPLS-TP tunnels' commands dialog box is displayed, which lists all the tunnels in the selected link.
Step 3 ![]() In the MPLS-TP tunnels' commands dialog box, choose the tunnels that you want to lock and select the Lock Out option in the Commands field.
In the MPLS-TP tunnels' commands dialog box, choose the tunnels that you want to lock and select the Lock Out option in the Commands field.
Step 4 ![]() Click Execute Now. You are prompted to confirm the lockout operation.
Click Execute Now. You are prompted to confirm the lockout operation.
Step 5 ![]() Click Yes to confirm. A message is displayed confirming that the selected tunnels have been locked. The status of the tunnel is automatically updated as Lockout(UP) after this operation.
Click Yes to confirm. A message is displayed confirming that the selected tunnels have been locked. The status of the tunnel is automatically updated as Lockout(UP) after this operation.
Unlocking MPLS-TP Tunnels
To unlock MPLS-TP tunnels in bulk:
Step 1 ![]() In the map view, right-click the required link and choose Properties.
In the map view, right-click the required link and choose Properties.
Step 2 ![]() In the link properties window, right-click on the required physical link and choose the Show MPLS-TP tunnels option. The MPLS-TP tunnels' commands dialog box is displayed, which lists all the tunnels in the selected link.
In the link properties window, right-click on the required physical link and choose the Show MPLS-TP tunnels option. The MPLS-TP tunnels' commands dialog box is displayed, which lists all the tunnels in the selected link.
Step 3 ![]() In the MPLS-TP tunnels' commands dialog box, select the locked tunnels that you want to unlock and select the Unlock option in the Commands field.
In the MPLS-TP tunnels' commands dialog box, select the locked tunnels that you want to unlock and select the Unlock option in the Commands field.
Step 4 ![]() Click Execute Now. You are prompted to confirm the unlock operation.
Click Execute Now. You are prompted to confirm the unlock operation.
Step 5 ![]() Click Yes to confirm. A message is displayed confirming that the selected tunnels have been unlocked. The status of the tunnels is automatically updated as Active(UP) after this operation.
Click Yes to confirm. A message is displayed confirming that the selected tunnels have been unlocked. The status of the tunnels is automatically updated as Active(UP) after this operation.

Note ![]() If you attempt to unlock a tunnel that is not locked, a message is displayed indicating that there are no valid tunnels to perform the unlock operation.
If you attempt to unlock a tunnel that is not locked, a message is displayed indicating that there are no valid tunnels to perform the unlock operation.
Configuring MPLS-TE
Use these commands to configures MPLS-TE on the router. The table below lists the MPLS-TE configuration commands and the MPLS-TE supported network elements.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
Configure MPLS-TE Global |
LSEs > right-click Label Switching > Commands > Configuration > |
Configures MPLS at the device level or an interface level. Contains information on MPLS interfaces and whether traffic engineering tunnels are configured. |
• • • |
Configure MPLS-TE Interface |
Routing Entities > Routing Entity> IP Interfaces tab, right-click the required interface > Commands > Configuration > |
Cisco ASR 9000 Series Routers |
|
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
Configuring MPLS
Multiprotocol label switching (MPLS) is a high-performance packet forwarding technology that integrates the performance and traffic management capabilities of data link layer (Layer 2) switching with the scalability, flexibility, and performance of network layer (Layer 3) routing. Use these commands to enable MPLS protocol on Cisco routers
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
Configure MPLS Discovery |
LSEs > right-click Label Switching > Commands > Configuration > |
Configure MPLS LDP discovery parameters to discover core MPLS networks. This also includes specifying the discovery method. |
• • • |
Configure MPLS Label Range |
Configures MPLS static and dynamic label range. |
||
Enable MPLS on Interface |
LSEs > Label Switching > right-click on a selected ID in the MPLS Interface tab Commands > Configuration > |
Enables/disables MPLS protocol on an interface. Contains information on MPLS interfaces and whether traffic engineering tunnels are configured on an interface. |
|
Disable MPLS on Interface |
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
Configuring RSVP
Use RSVP commands to establish a reserved-bandwidth path between hosts or the end systems to predetermine and ensure Quality of Service (QoS) for their data transmission.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
Configure RSVP |
LSEs > right-click Label Switching > Commands > Configuration > |
Configure RSVP on a device or an interface. |
• • • |
Delete RSVP |
Cisco ASR 9000 Series Routers |
||
Enable RSVP On Interface Disable RSVP On Interface |
Routing Entities > Routing Entity> IP Interfaces tab, right-click the required interface > Commands > Configuration |
• • • |
|
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
Configuring BGP
Multiprotocol BGP is an enhanced BGP that carries routing information for multiple network layer protocols and IP multicast routes. BGP commands configure the routing protocol to communicate with the other sites and VRFs.

Note ![]() BGP neighbors should be configured as part of BGP routing. At least one neighbor and at least one address family must be configured to enable BGP routing.
BGP neighbors should be configured as part of BGP routing. At least one neighbor and at least one address family must be configured to enable BGP routing.
The table below lists the commands that will be used to configure BGP Routing Protocol on Cisco Routers.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
Create BGP Router Modify BGP Router Delete BGP Router |
MPBGPs > right-click MPBGP > Commands > Configuration > |
Configures BGP routing and establish a BGP routing process with AS number and Router ID |
• • • • |
Create BGP Address Family Modify BGP Address Family Delete BGP Address Family |
Enter various address family configuration modes that uses IPv4, IPv6, L2VPN, VPNV4 or VPNV6 address prefixes. |
||
Create BGP Neighbor |
Places the router in neighbor configuration mode for BGP routing and configures the neighbor IP address as a BGP peer. |
||
Modify BGP Neighbor Delete BGP Neighbor |
MPBGP > MPBGP > right-click on the BGP neighbour in the content pane > Commands > Configuration > |
||
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
Configuring VRRP
The Virtual Router Redundancy Protocol (VRRP) feature allows for transparent failover at the first-hop IP router, enabling a group of routers to form a single virtual router. VRRP Command will be used to configure VRRP protocol on Cisco router.
These commands configures transparent failover at the first-hop IP router, enabling a group of routers to form a single virtual router.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
Create VRRP Group Delete VRRP Interface |
Routing Entities > Routing Entity> IP Interfaces tab, right-click the required interface > Commands > Configuration |
Configure a group of routers to form a single virtual router. Example is using VRRP group as default router on the client. The LAN clients can be configured with the virtual router as their default gateway thus avoiding single point of failure, which was the case in dynamic discovery protocol. |
Cisco ASR 9000 Series Routers |
Modify VRRP Group Delete VRRP Show VRRP |
Routing Entities > Routing Entity> IP Interfaces tab, double-click on the VRRP configured interface > select VRRP Group tab > right-click on required group. |
||
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
Configuring Bundle Ethernet
Configure a bundle of one or more ports to form a single link using bundle ethernet commands.
To run the these commands, the software on the network element must support the technology. Before executing any commands, you can preview them and view the results. For details on the software versions Prime Network supports for the listed supported network elements, see Cisco Prime Network 3.10 Supported Cisco VNEs.
You might be prompted to enter your device access credentials while executing a command. Once you have entered them, these credentials will be used for every subsequent execution of a command in the same GUI client session. If you want to change the credentials, click Edit Credentials. The Edit Credentials button will not be available for SNMP commands or if the command is scheduled for a later time.
|
|
|
|
|
|---|---|---|---|
|
|
|||
Configure Bundle Ethernet |
Physical Inventory > Chassis > Slot > Ethernet Port > Commands > Configuration > |
Configuring an Ethernet link bundle involves creating a bundle and adding member interfaces to that bundle. |
• • • |
1 Modify commands can be used to delete specific attributes, whereas the delete commands deletes the complete configuration. |
 Feedback
Feedback