Access Control Lists for VXLAN Traffic on Cisco Nexus Switches
All scenarios that are mentioned in the previous table are explained with the following host details:
-
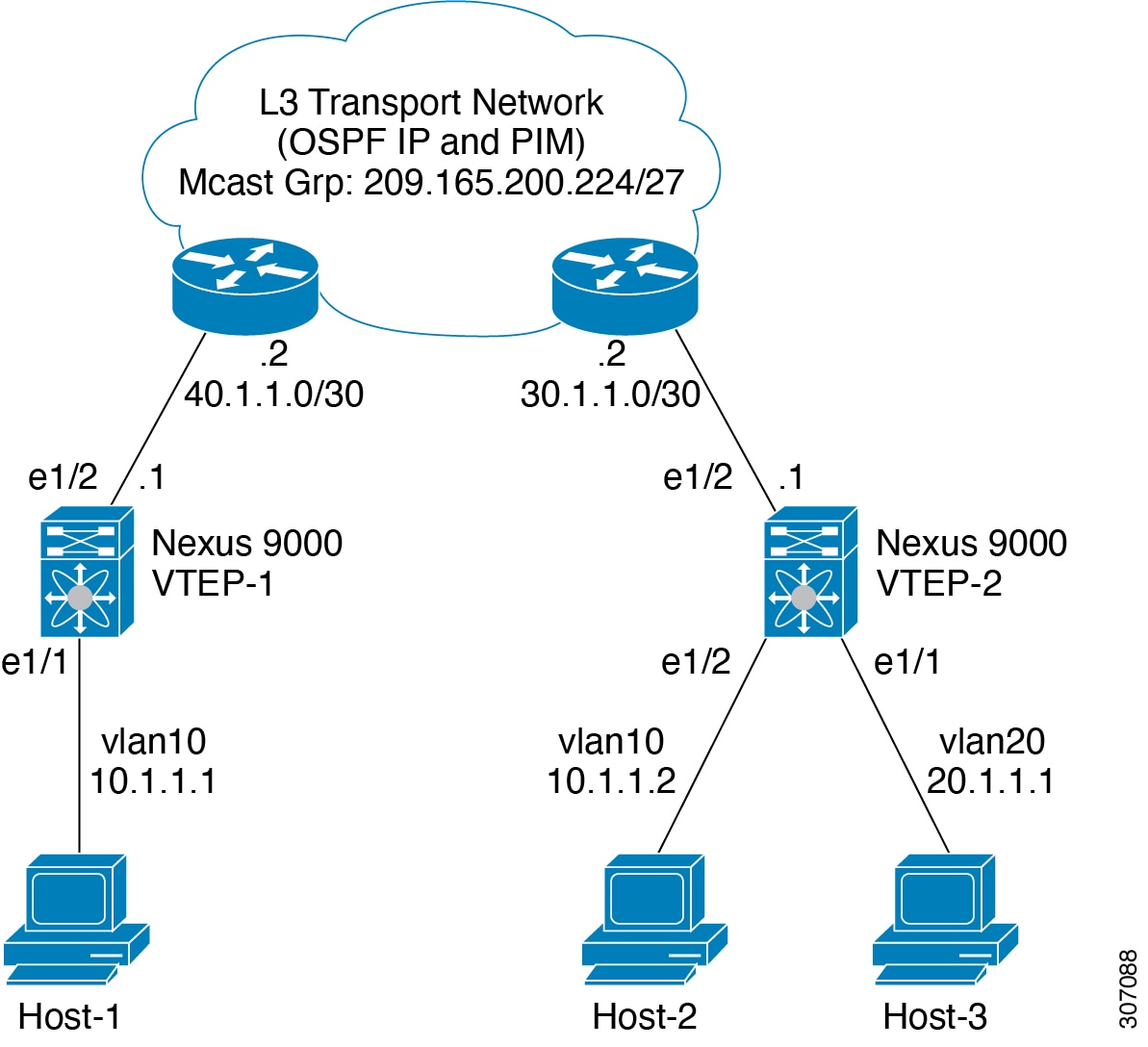
Host-1: 10.1.1.1/24 VLAN-10
-
Host-2: 10.1.1.2/24 VLAN-10
-
Host-3: 20.1.1.1/24 VLAN-20
-
Case 1: Layer 2 traffic/L2 VNI that flows between Host-1 and Host-2 on VLAN-10.
-
Case 2: Layer 3 traffic/L3 VNI that flows between Host-1 and Host-3 on VLAN-10 and VLAN-20.
| Scenario |
ACL Direction |
ACL Type |
VTEP Type |
Port Type |
Flow Direction |
Traffic Type |
Supported |
|---|---|---|---|---|---|---|---|
|
1 |
Ingress |
PACL |
Ingress VTEP |
L2 port |
Access to Network [GROUP:encap direction] |
Native L2 traffic [GROUP:inner] |
YES |
|
2 |
VACL |
Ingress VTEP |
VLAN |
Access to Network [GROUP:encap direction] |
Native L2 traffic [GROUP:inner] |
YES |
|
|
3 |
Ingress |
RACL |
Ingress VTEP |
Tenant L3 SVI |
Access to Network [GROUP:encap direction] |
Native L3 traffic [GROUP:inner] |
YES |
|
4 |
Egress |
RACL |
Ingress VTEP |
uplink L3/L3-PO/SVI |
Access to Network [GROUP:encap direction] |
VXLAN encap [GROUP:outer] |
NO |
|
5 |
Ingress |
RACL |
Egress VTEP |
Uplink L3/L3-PO/SVI |
Network to Access [GROUP:decap direction] |
VXLAN encap [GROUP:outer] |
NO |
|
6 |
Egress |
PACL |
Egress VTEP |
L2 port |
Network to Access [GROUP:decap direction] |
Native L2 traffic [GROUP:inner] |
NO |
|
7a |
VACL |
Egress VTEP |
VLAN |
Network to Access [GROUP:decap direction] |
Native L2 traffic [GROUP:inner] |
YES |
|
|
7b |
VACL |
Egress VTEP |
Destination VLAN |
Network to Access [GROUP:decap direction] |
Native L3 traffic [GROUP:inner] |
YES |
|
|
8 |
Egress |
RACL |
Egress VTEP |
Tenant L3 SVI |
Network to Access [GROUP:decap direction] |
Post-decap L3 traffic [GROUP:inner] |
YES |
ACL implementation for VXLAN is the same as regular IP traffic. The host traffic is not encapsulated in the ingress direction at the encapsulation switch. The implementation is a bit different for the VXLAN encapsulated traffic at the decapsulation switch as the ACL classification is based on the inner payload. The supported ACL scenarios for VXLAN are explained in the following topics and the unsupported cases are also covered for both encapsulation and decapsulation switches.
 Feedback
Feedback