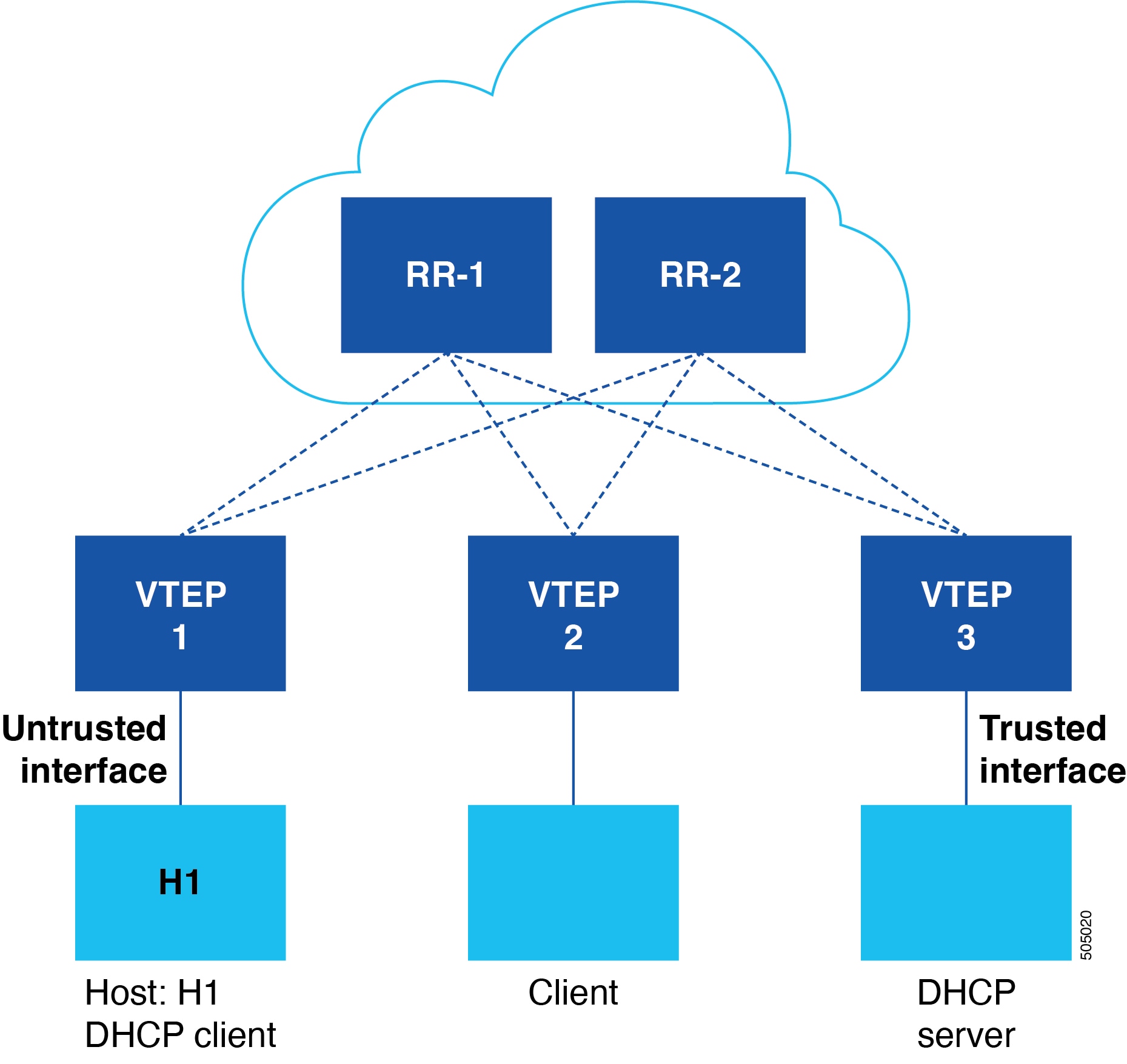
DHCP Snooping in VXLAN BGP EVPN
DHCP Snooping in VXLAN BGP EVPN is a process that
-
validates ARP/GARP packets sent from a host, preventing ARP spoofing and malicious ARP storms,
-
validates data-plane traffic from the host using IPSG, preventing malicious hosts from sending data traffic, and
-
replicates DHCP Snooping entries across the VXLAN fabric, enabling DAI and IPSG to function across the fabric even after a host move.
First Hop Security
First Hop Security (FHS) is an access security feature that
-
provides security to the network at the access point where the host connects to the first switch,
-
authorizes and authenticates hosts, and
-
protects the network by ensuring only authorized hosts are allowed network access.
The Dot1x, port-security, and DHCP Snooping are examples of access security features.
DHCP Snooping database
DHCP Snooping database (DB) is a database that
-
contains the MAC address of the host, the IP address assigned to the host by the DHCP server, VLAN, and other details like the lease time,
-
can contain local or remote snooping DB entries, and
-
can be configured using the ip source binding ip address vlan vlan-id interface interface interface command.

Note
Snooping entries added through this command are referred to as static entries, and they are distributed across all VTEPs.
Distributed DHCP Snooping database
Distributed DHCP Snooping DB is a database that
-
validates ARPs/GARPs sent from the host using DAI,

Note
The ARP/GARP will be dropped if there is no matching entry in the DB.
-
validates data-plane traffic from the host using IPSG, and
-
is replicated across the fabric.
 Feedback
Feedback