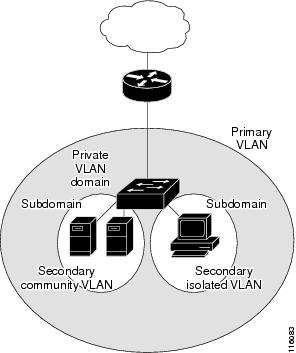
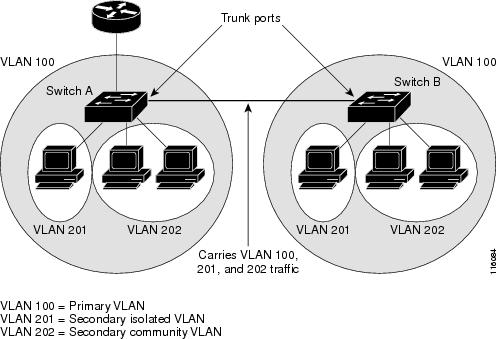
Restrictions for Private VLANs
 Note |
In some cases, the configuration is accepted with no error messages, but the commands have no effect. |
-
Do not configure fallback bridging on the device with private VLANs.
-
Do not configure a remote SPAN (RSPAN) VLAN as a primary or a secondary VLAN of a private-VLAN.
-
Do not configure private VLAN ports on interfaces configured for these other features:
-
Dynamic-access port VLAN membership
-
Dynamic Trunking Protocol (DTP)
-
IP Source Guard
-
IPv6 First Hop Security (FHS)
-
IPv6 Security Group (SG)
-
Multicast VLAN Registration (MVR)
-
Voice VLAN
-
Web Cache Communication Protocol (WCCP)
-
-
Port Aggregation Protocol (PAgP) and Link Aggregation Control Protocol (LACP) are supported only for Private VLAN promiscuous trunk ports and Private VLAN isolated trunk ports.
-
You can configure IEEE 802.1x port-based authentication on a private-VLAN port, but do not configure 802.1x with port security, voice VLAN, or per-user ACL on private-VLAN ports.
-
A private-VLAN host or promiscuous port cannot be a SPAN destination port. If you configure a SPAN destination port as a private-VLAN port, the port becomes inactive.
-
If you configure a static MAC address on a promiscuous port in the primary VLAN, you need not add the same static address to all associated secondary VLANs. Similarly, if you configure a static MAC address on a host port in a secondary VLAN, you need not add the same static MAC address to the associated primary VLAN. Also, when you delete a static MAC address from a private-VLAN port, you do not have to remove all instances of the configured MAC address from the private VLAN.

Note
Dynamic MAC addresses learned in the secondary VLAN of a private VLAN are replicated to the primary VLANs. All MAC entries are learnt on secondary VLANs, even if the traffic ingresses from primary VLAN. If a MAC address is dynamically learnt in the primary VLAN, it is not replicated in the associated secondary VLANs.
-
Configure Layer 3 VLAN interfaces (switch value interfaces) only for primary VLANs.
-
Private VLAN configured with MACsec or Virtual Private LAN Services (VPLS) or Cisco Software-Defined Access solution on the same VLAN does not work.
 Feedback
Feedback