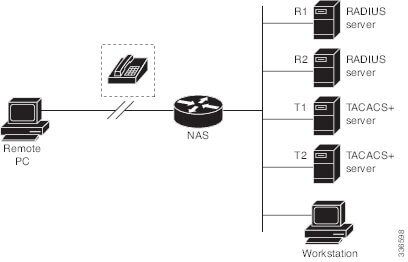
Use the aaa
authentication
login default command with the group
group-name method to specify a subset of RADIUS or TACACS+ servers to use as the login authentication method. To specify and define
the group name and the members of the group, use the aaa
group
server command. For example, use the aaa
group
server command to first define the members of group
loginrad :
Device> enable
Device# configure terminal
Device(config)# aaa group server radius loginrad
Device(config-sg-radius)# server 172.16.2.3
Device(config-sg-radius)# server 172.16.2 17
Device(config-sg-radius)# server 172.16.2.32
Device(config-sg-radius)# end
This command specifies RADIUS servers 172.16.2.3, 172.16.2.17, and 172.16.2.32 as members of the group loginrad .
To specify group
loginrad as the method of user authentication at login when no other method list has been defined, enter the following command:
Device(config)# aaa authentication login default group loginrad
Before you can use a group name as the login authentication method, you need to enable communication with the RADIUS or TACACS+
security server. For more information about establishing communication with a RADIUS server, refer to the chapter “Configuring
RADIUS.” For more information about establishing communication with a TACACS+ server, refer to the chapter “Configuring TACACS+.”


 Feedback
Feedback