The following is a
sample configuration of basic policing for all the traffic received with a CoS
of 4. The first value following the
police command
limits the average traffic rate to 10, 000,000 bits per second (bps); the
second value represents the additional burst size (10 kilobytes). The policy is
assigned to Gigabit Ethernet port 1.
Router(config)# class-map video-class
Router(config-cmap)# match cos 4
Router(config-cmap)# exit
Router(config)# policy-map video-policy
Router(config-pmap)# class video-class
Router(config-pmap-c)# police 10000000 10000
Router(config-pmap-c-police)# exit
Router(config-pmap-c)# exit
Router(config-pmap)# exit
Router(config)# interface gigabitethernet0/1
Router(config-if)# service-policy input video-policy
Router(config-if)# exit
The following is a
sample configuration that shows the policing of traffic over cross-connect EVC:
Router(config)# interface GigabitEthernet0/3
Router(config-if)# service instance 22 ethernet
Router(config-if-svr)# encapsulation dot1q 22
Router(config-if-svr)# rewrite ingress tag pop 1 symmetric
Router(config-if-svr)# xconnect 1.1.1.1 100 encapsulation mpls
Router(config-if-svr)# service-policy input policy1
Router(config-if-svr)# exit
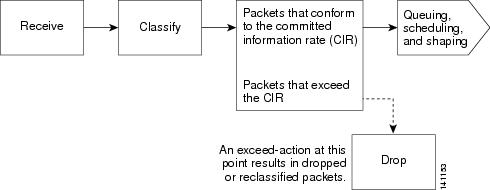
You can use the
conform-action
and
exceed-action
policy-map class configuration commands or the
conform-action
and
exceed-action
policy-map class police configuration commands to specify the action to be
taken when a packet conforms to or exceeds the specified traffic rate.
Conform actions
involve sending the corresponding packet without modifications, setting a new
CoS, DSCP, or IP precedence value, or setting up a QoS group value for
classification at the egress. Exceed actions involve dropping the packet,
sending the packet without modification, setting a new CoS, DSCP, or IP
precedence to a value, or setting a QoS group value for classification at the
egress.
You can configure
each marking action by using explicit values, table maps, or a combination of
both. Table maps list specific traffic attributes and map (or convert) them to
other attributes.
You can configure
multiple conform and exceed actions simultaneously for each service class.
After you create a
table map, configure a policy-map policer to use the table map.

Note
|
In
Cisco ASR 901
router, the
from –type
action in the table map must be
cos .
|
To configure multiple
actions in a class, you can enter multiple conform or exceed action entries in
the policy-map class police configuration mode, as in this example:
Router(config)# policy-map map1
Router(config-pmap)# class class1
Router(config-pmap-c)# police 100000 500000
Router(config-pmap-c-police)# conform-action set-cos-transmit 4
Router(config-pmap-c-police)# conform-action set-qos-transmit 4
Router(config-pmap-c-police)# exceed-action set-cos-transmit 2
Router(config-pmap-c-police)# exceed-action set-qos-transmit 2
Router(config-pmap-c-police)# exit
Router(config-pmap-c)# exit
Router(config-pmap)# exit

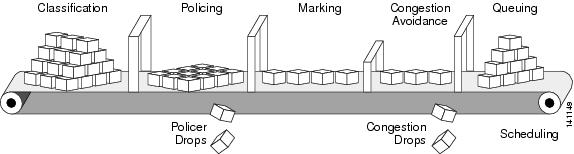
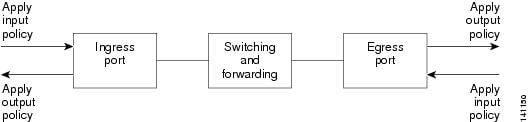
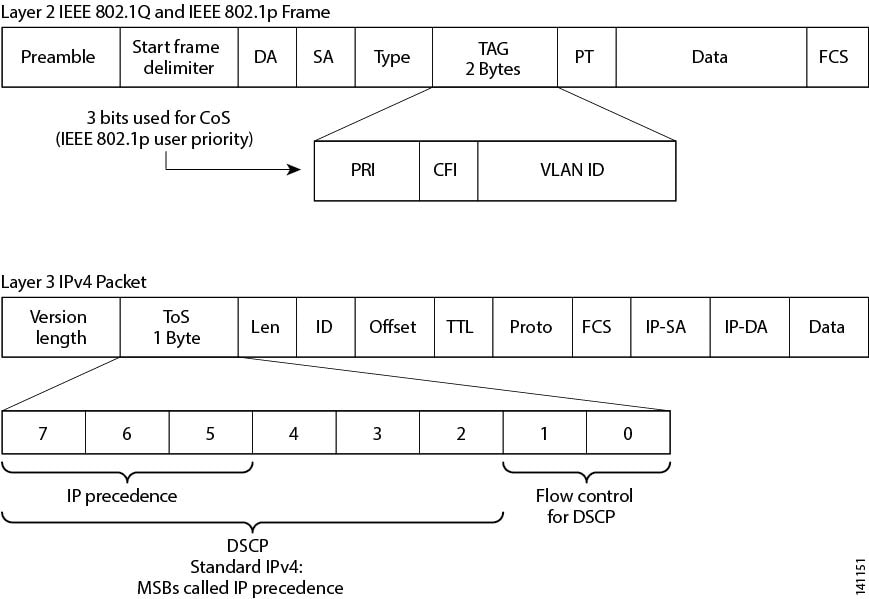
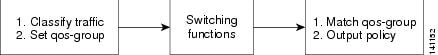

 Feedback
Feedback