About rule-based decryption policies
Rule-based decryption policies
Decryption policy you create using a wizard that steps you through the available options for inbound decryption, outbound decryption, or both. After you create the rule-based decryption policy, you can add more rules to it, reorder rules, or make other changes to suit your needs.
A rule-based decryption policy is the most flexible but also the most potentially complicated. You can convert a standard decryption policy to a rule-based policy at any time.
Which type of decryption policy is right for me?
This topic discusses standard decryption policies and rule-based decryption policies.
Standard decryption policies
We recommend the standard decryption policy type because it's easy to set up with a wizard-like appearance, enabling you to easily pick security zones, users and networks, and other objects to use in your policy. A standard decryption policy is particularly suited for anyone who is not proficient at understanding the ins and outs of decryption policies.
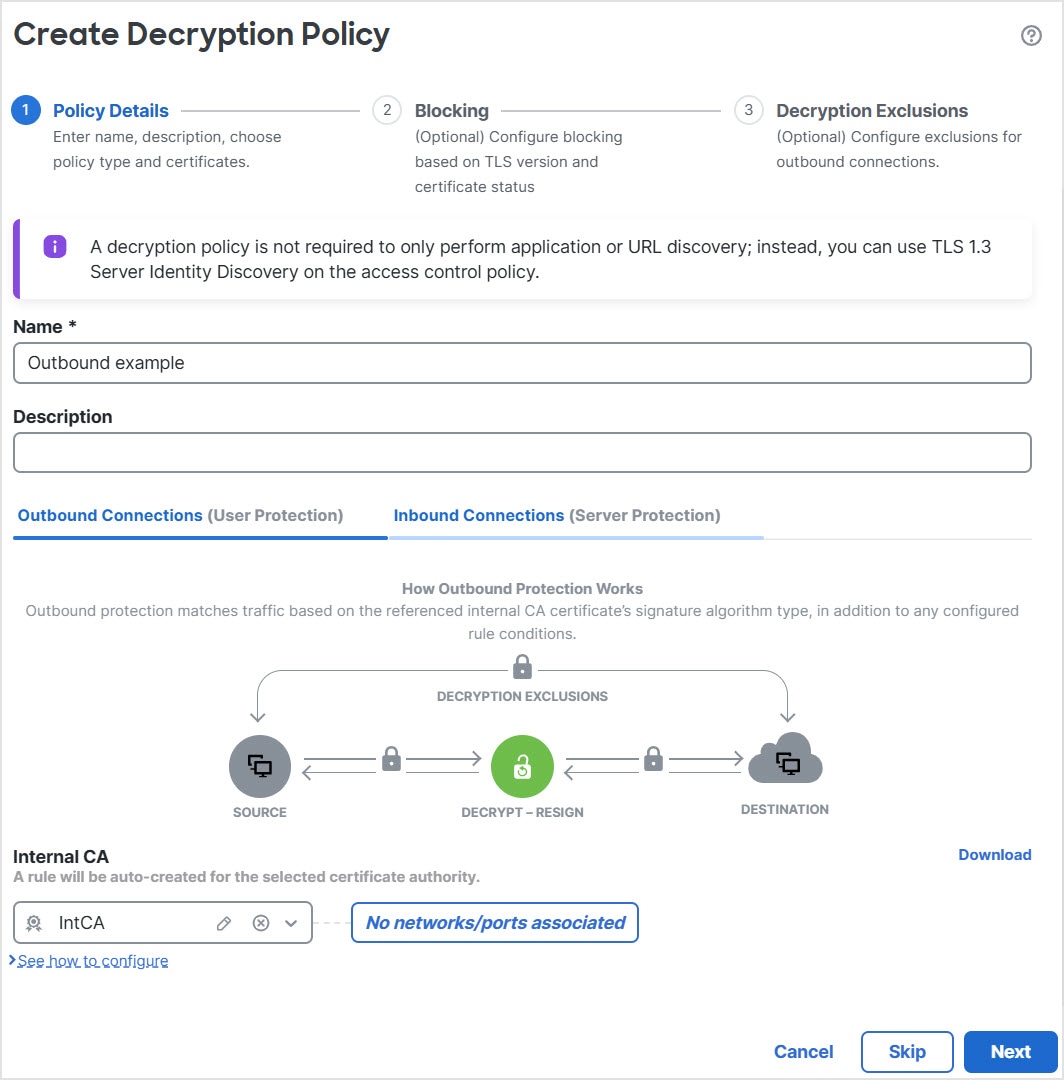
Following is an example of setting up a standard decryption policy.

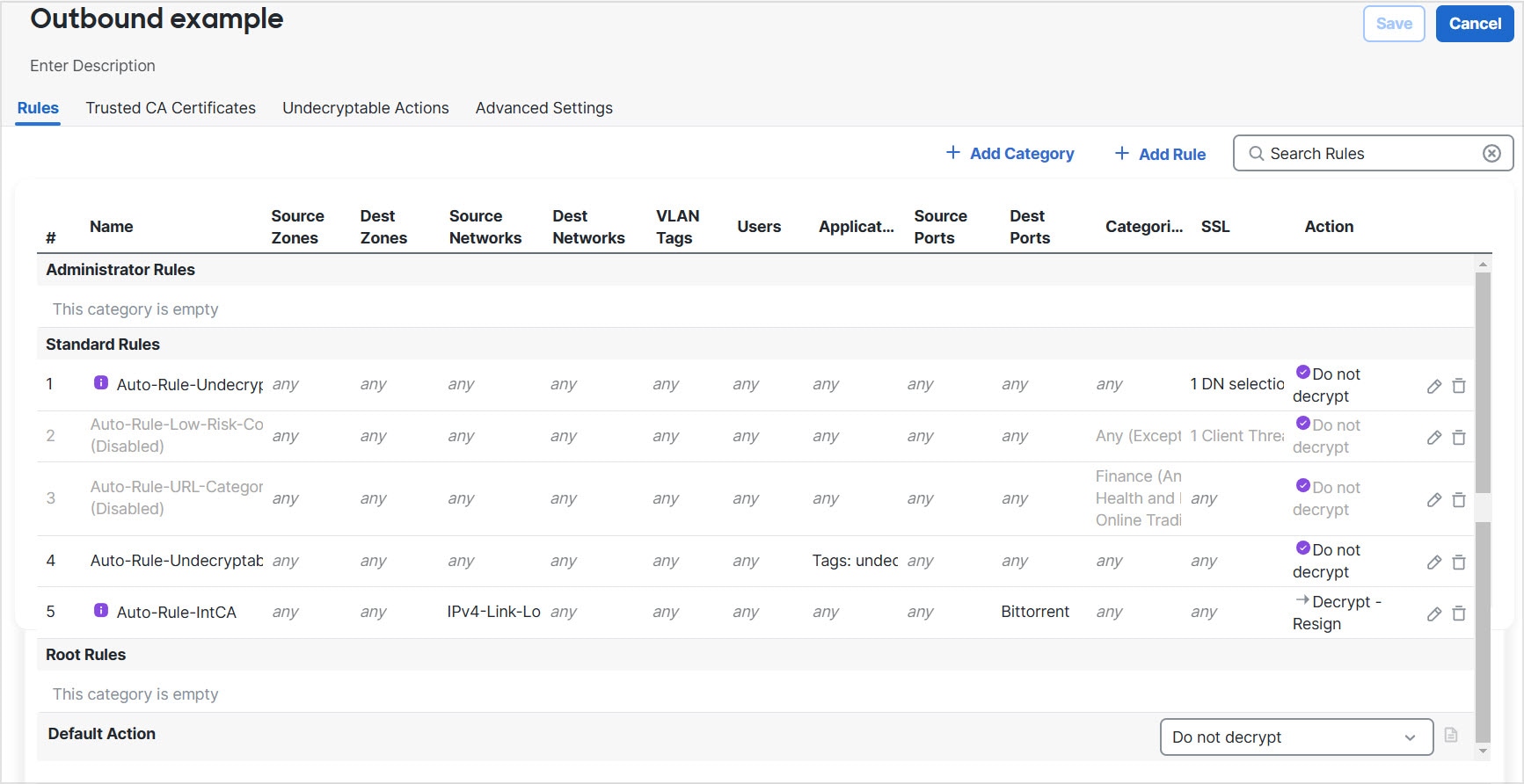
The preceding policy decrypts outbound traffic only. All traffic from the OutsideZone security zone on any IPv4 network is
decrypted using an internal CA named IntCA.
Note the following:
-
The preceding rule is a partial example; more options are available.
-
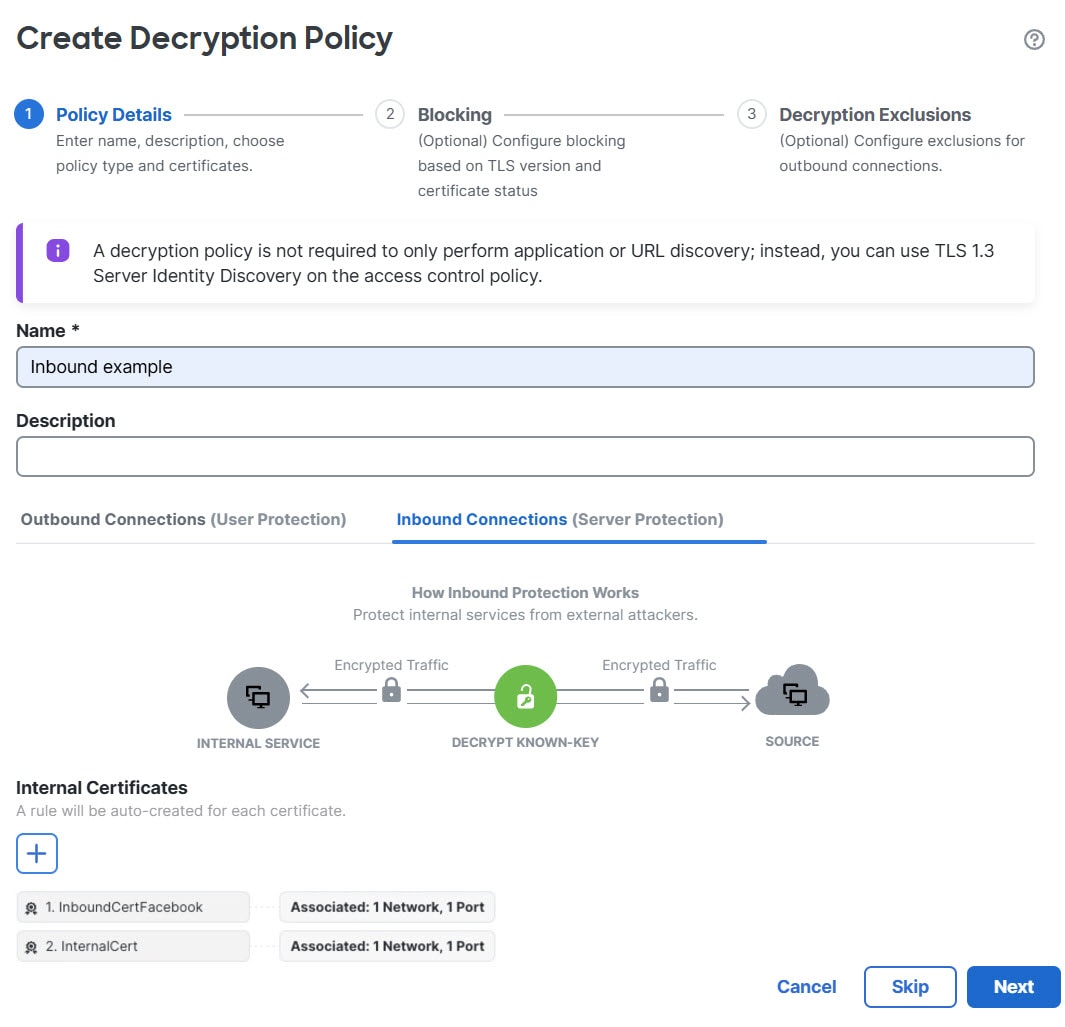
You can configure inbound criteria, outbound criteria, or both.
-
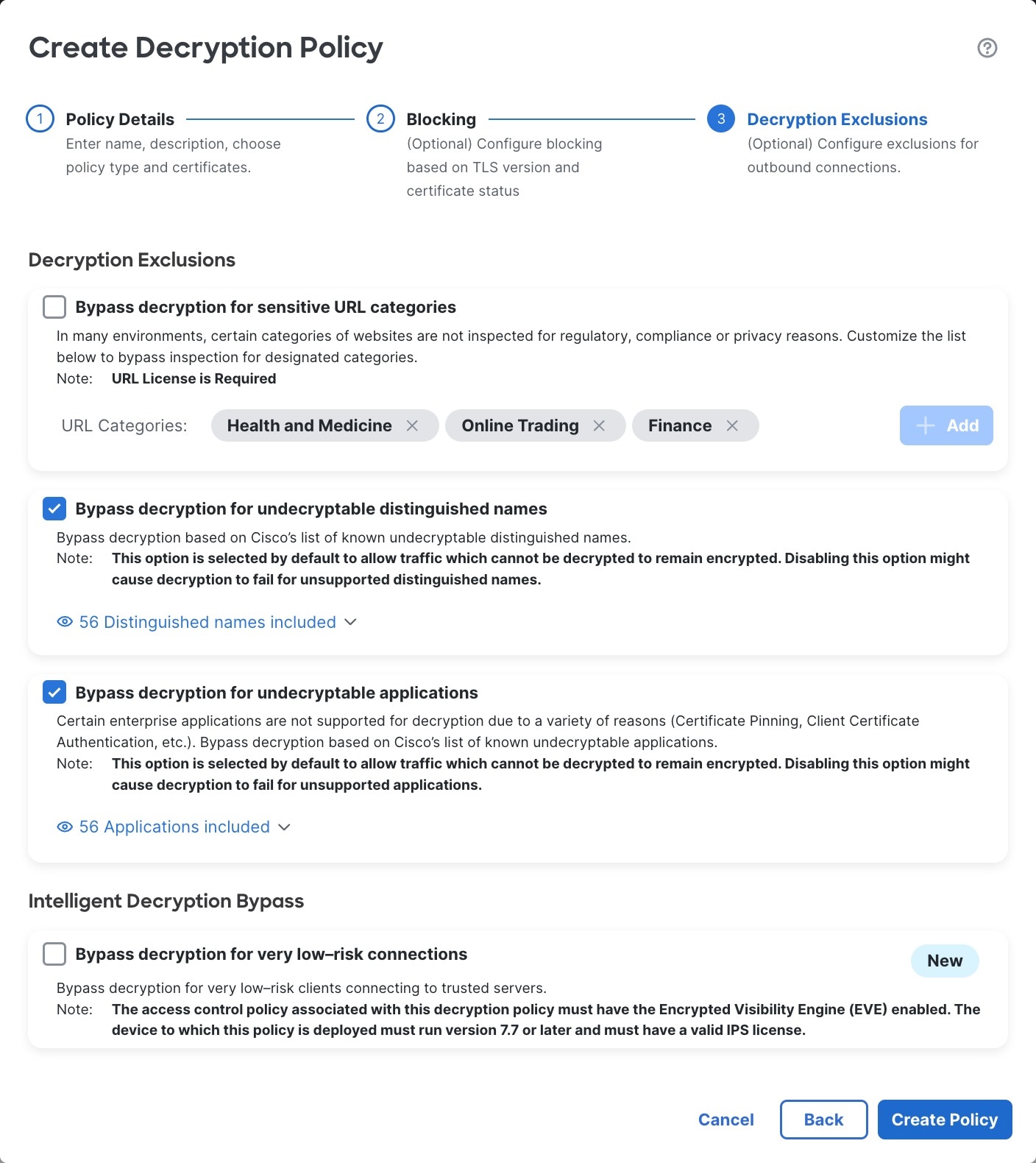
In addition to objects, you can also optionally configure outbound decryption exclusions, such as:
-
Undecryptable applications (such as ones that use certificate pinning).
-
URL categories such as medical, trading, and finance.
-
-
You can configure outbound block criteria for certificate status and TLS version.
-
A standard policy has advanced policy options that are similar to rule-based policies.
Rule-based decryption policies
Decryption policy you create using a wizard that steps you through the available options for inbound decryption, outbound decryption, or both. After you create the rule-based decryption policy, you can add more rules to it, reorder rules, or make other changes to suit your needs.
A rule-based decryption policy is the most flexible but also the most potentially complicated. You can convert a standard decryption policy to a rule-based policy at any time.



 Feedback
Feedback