-
NAT rules apply to through the device traffic only, they do not apply to traffic initiated by the device, such as a RADIUS
authentication.
-
For interfaces
that are members of a bridge group, you write NAT rules for the member
interfaces. You cannot write NAT rules for the Bridge Virtual Interface (BVI)
itself.
-
You cannot write NAT rules for a Virtual Tunnel Interface (VTI), which are
used in site-to-site VPN. Writing rules for the VTI's source interface will
not apply NAT to the VPN tunnel. To write NAT rules that will apply to VPN
traffic tunneled on a VTI, you must use "any" as the interface; you cannot
explicitly specify interface names.
-
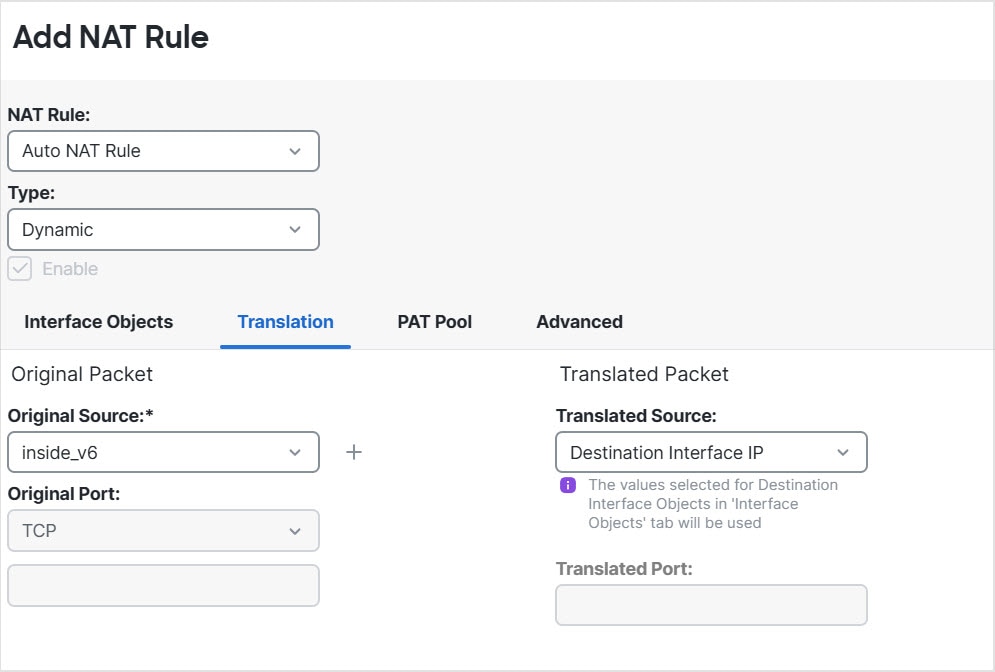
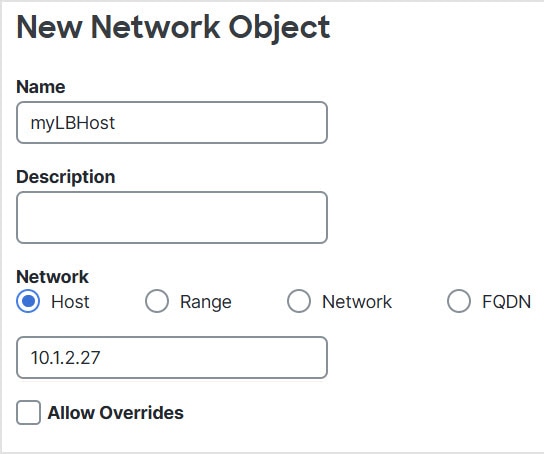
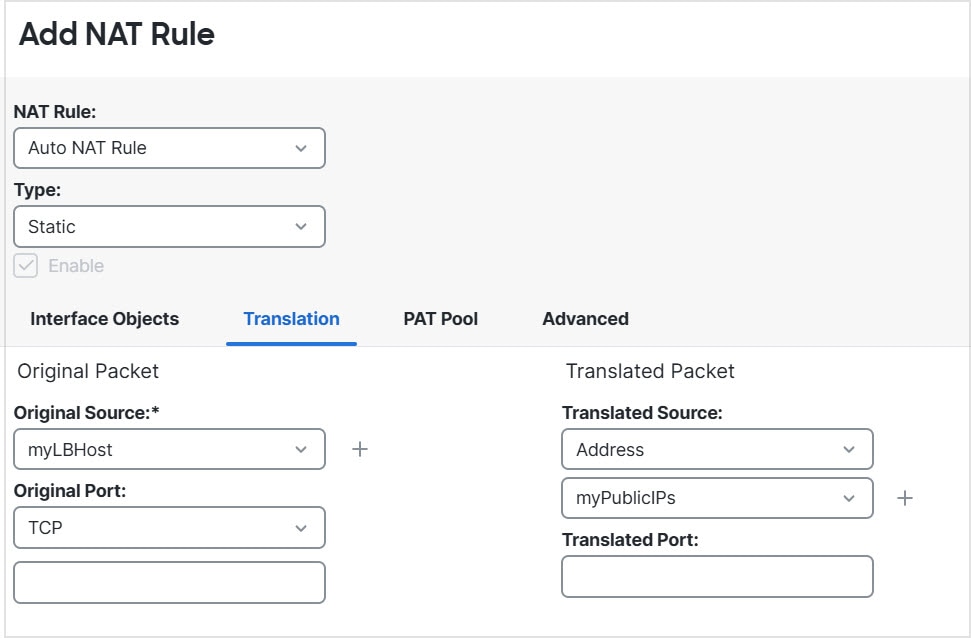
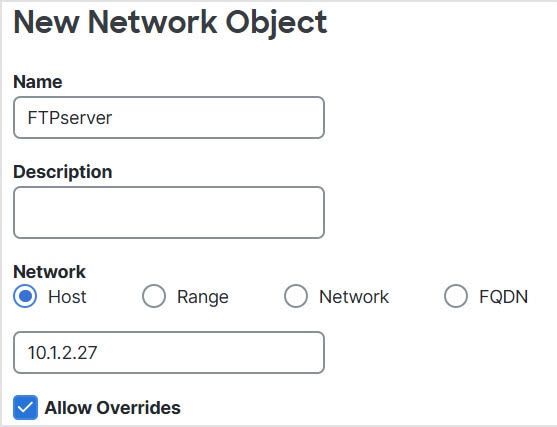
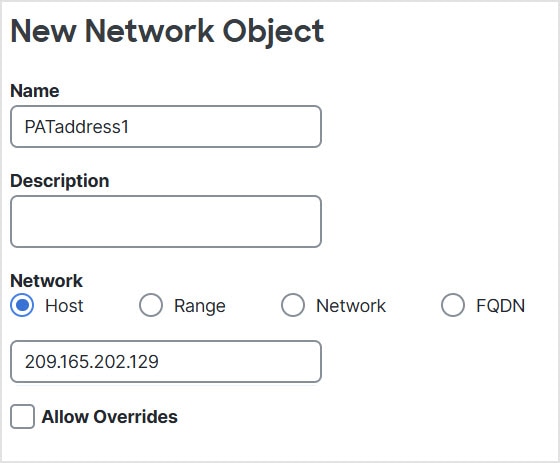
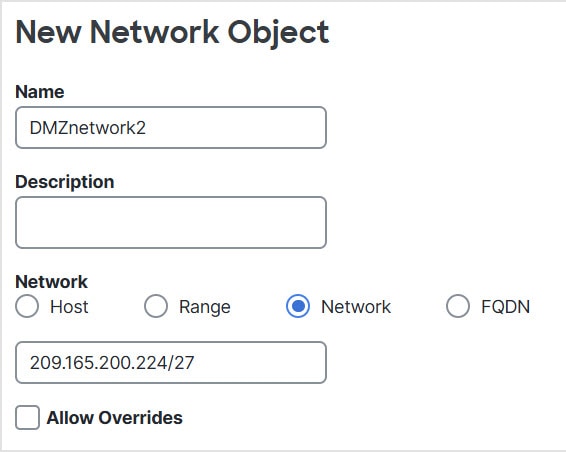
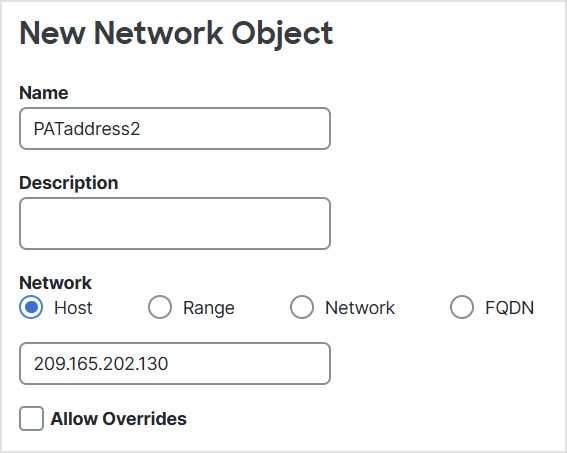
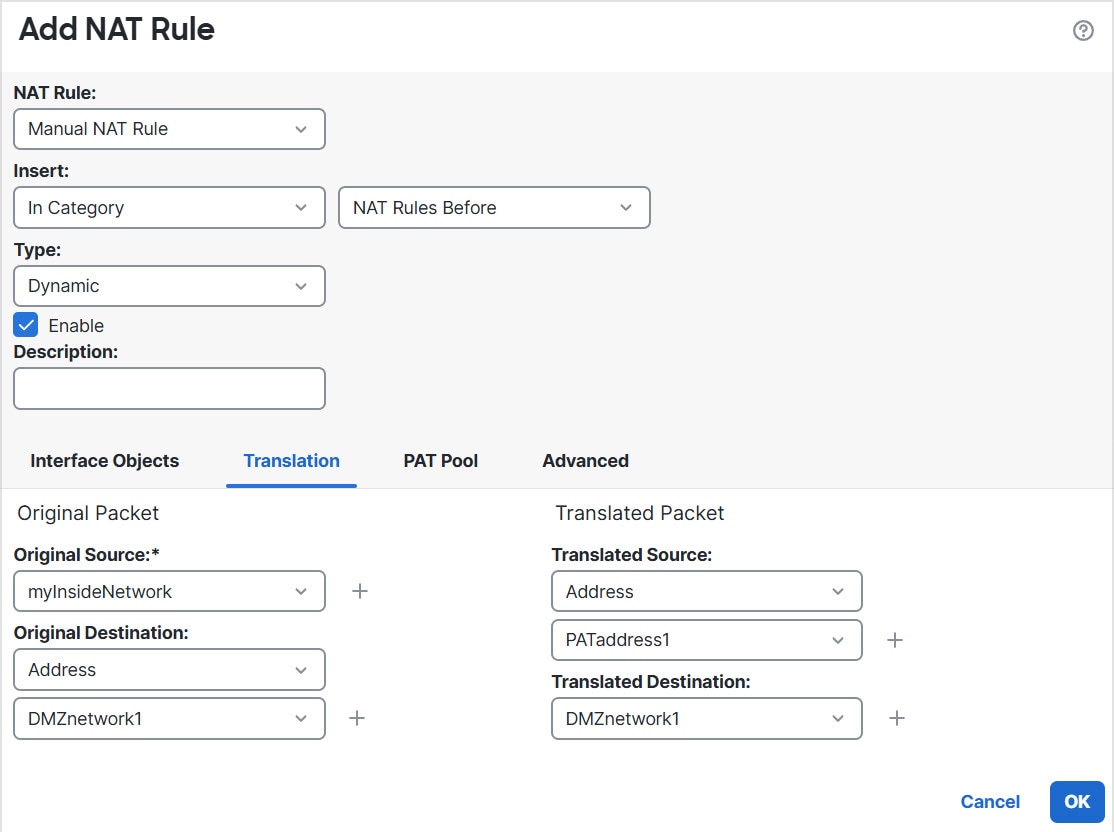
(Auto NAT only.) You can only define a single NAT rule for a given object; if you want to configure multiple NAT rules for an object,
you need to create multiple objects with different names that specify the same IP address.
-
If a VPN is
defined on an interface, inbound ESP traffic on the interface is not subject to
the NAT rules. The system allows the ESP traffic for established VPN tunnels
only, dropping traffic not associated with an existing tunnel. This restriction
applies to ESP and UDP ports 500 and 4500.
-
If you define a site-to-site VPN on a device that is behind a device that is applying dynamic PAT, so that UDP ports 500 and
4500 are not the ones actually used, you must initiate the connection from the device that is behind the PAT device. The responder
cannot initiate the security association (SA) because it does not know the correct port numbers.
-
If you change the NAT configuration, and you do not want to wait for existing translations to time out before the new NAT
configuration is used, you can clear the translation table using the clear xlate command in the device CLI. However, clearing the translation table disconnects all current connections that use translations.
If you create a new NAT rule that should apply to an existing connection
(such as a VPN tunnel), you need to use clear conn
to end the connection. Then, the attempt to re-establish the connection
should hit the NAT rule and the connection should be NAT'ed correctly.

Note
|
If you remove a dynamic NAT or PAT rule, and then add a new rule with
mapped addresses that overlap the addresses in the removed rule, then
the new rule will not be used until all connections associated with the
removed rule time out or are cleared using the clear
xlate or clear conn
commands. This safeguard ensures that the same address is not assigned
to multiple hosts.
|
-
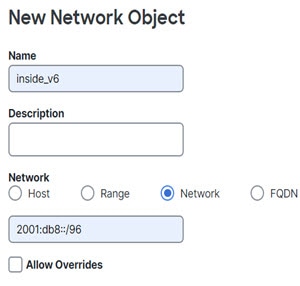
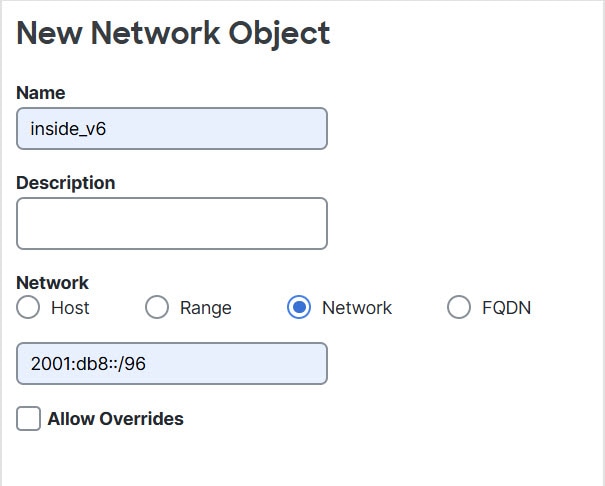
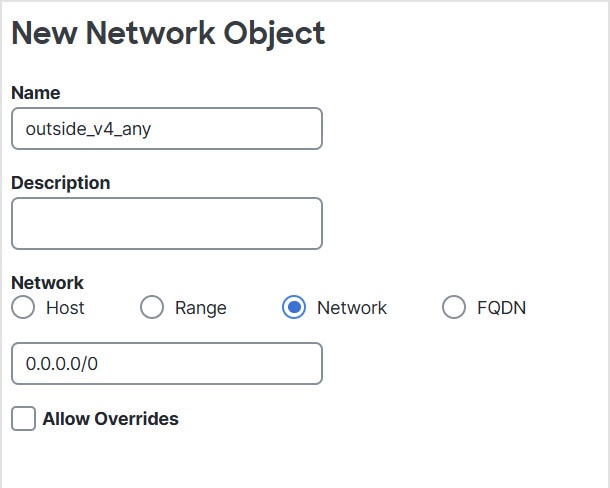
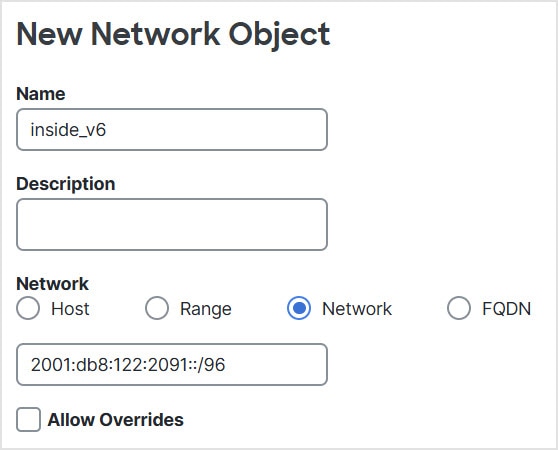
You cannot use an object group with both IPv4 and IPv6
addresses; the object group must include only one type of address.
-
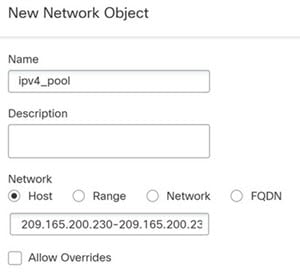
A network object used in NAT cannot include more than 131,838 IP addresses,
either explicitly or implied in a range of addresses or a subnet. Break up
the address space into smaller ranges and write separate rules for the
smaller objects.
-
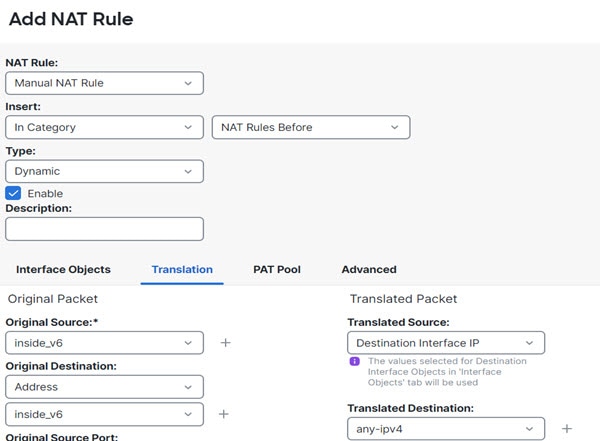
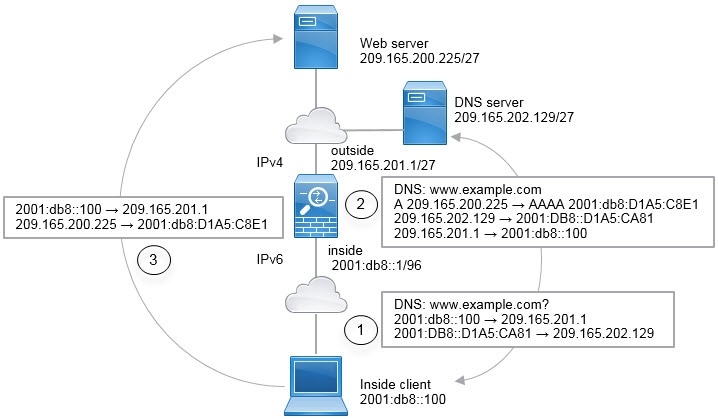
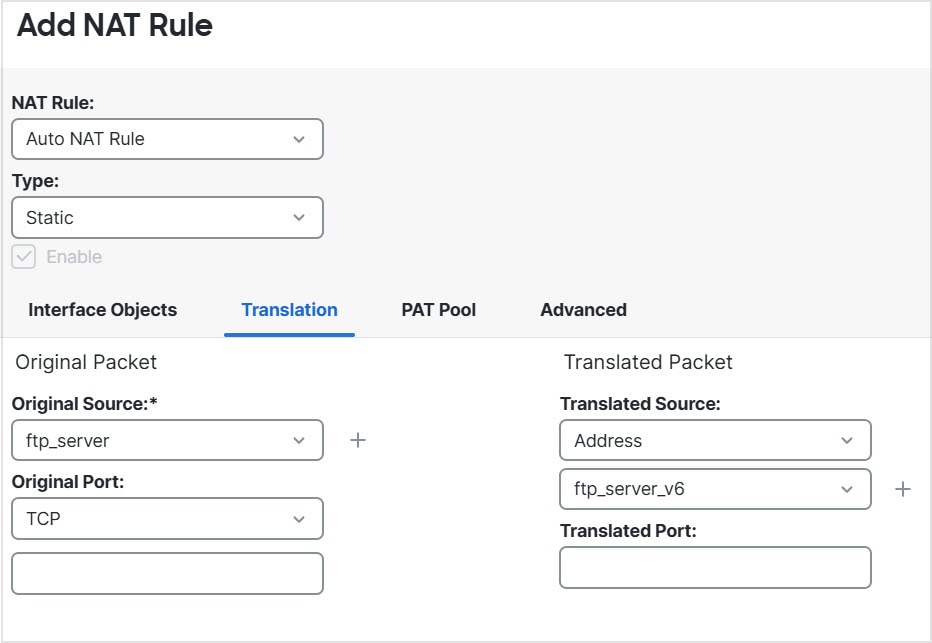
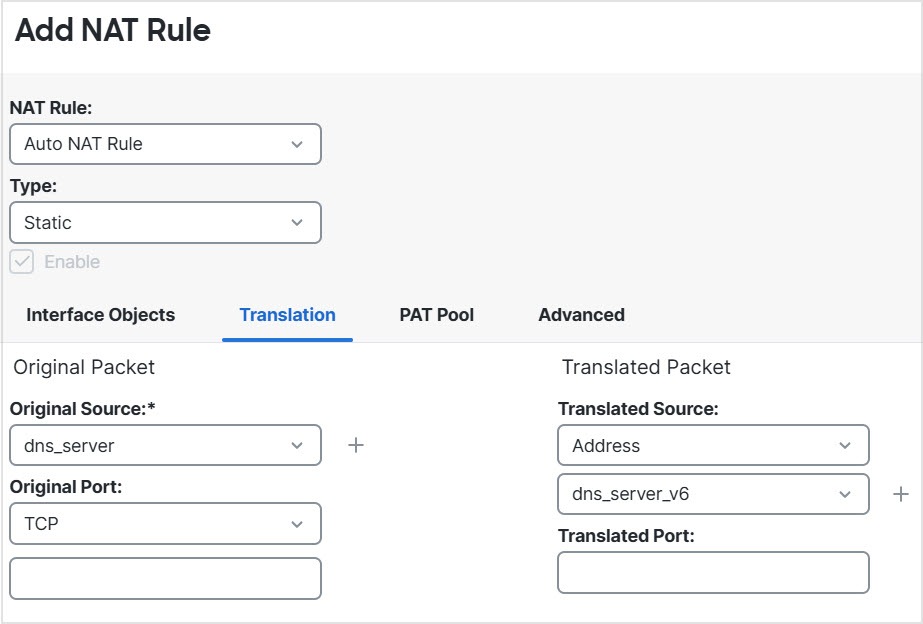
(Manual
NAT only.) When using any as the source address in a NAT rule, the definition of “any” traffic (IPv4 vs. IPv6) depends on the rule. Before the Firewall Threat Defense device performs NAT on a packet, the packet must be IPv6-to-IPv6 or IPv4-to-IPv4; with this prerequisite, the Firewall Threat Defense device can determine the value of any in a NAT rule. For example, if you configure a rule from “any” to an IPv6 server, and that server was mapped from an IPv4
address, then any means “any IPv6 traffic.” If you configure a rule from “any” to “any,” and you map the source to the interface IPv4 address,
then any means “any IPv4 traffic” because the mapped interface address implies that the destination is also IPv4.
-
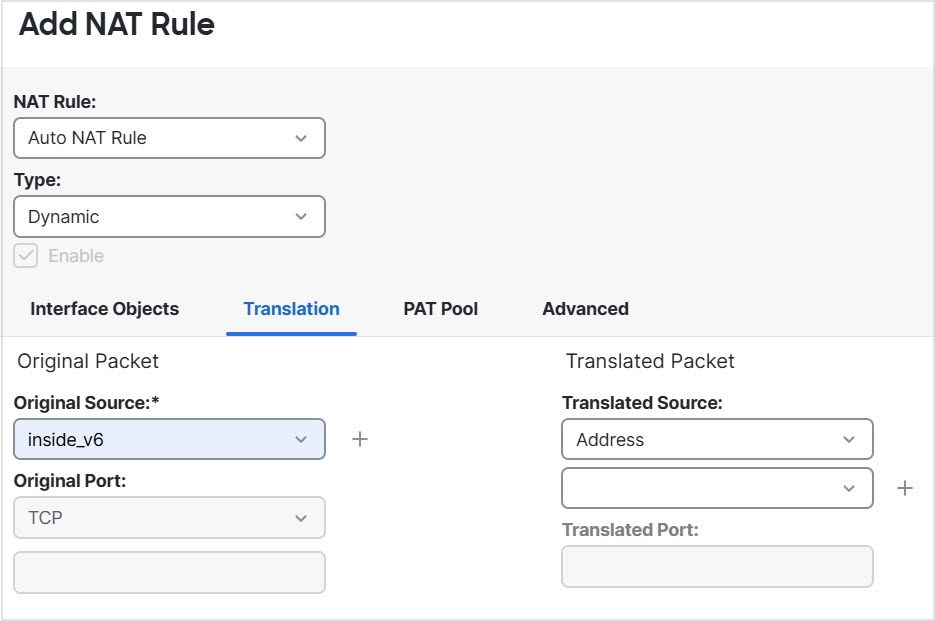
You can use the same mapped object or group in multiple NAT
rules.
-
The mapped IP address pool cannot include:
-
The mapped interface IP address. If you specify “any” interface
for the rule, then all interface IP addresses are disallowed. For interface PAT
(routed mode only), specify the interface name instead of the interface
address.
-
The
failover interface IP address.
-
(Transparent mode.) The management IP address.
-
(Dynamic NAT.) The standby interface IP address when VPN is
enabled.
-
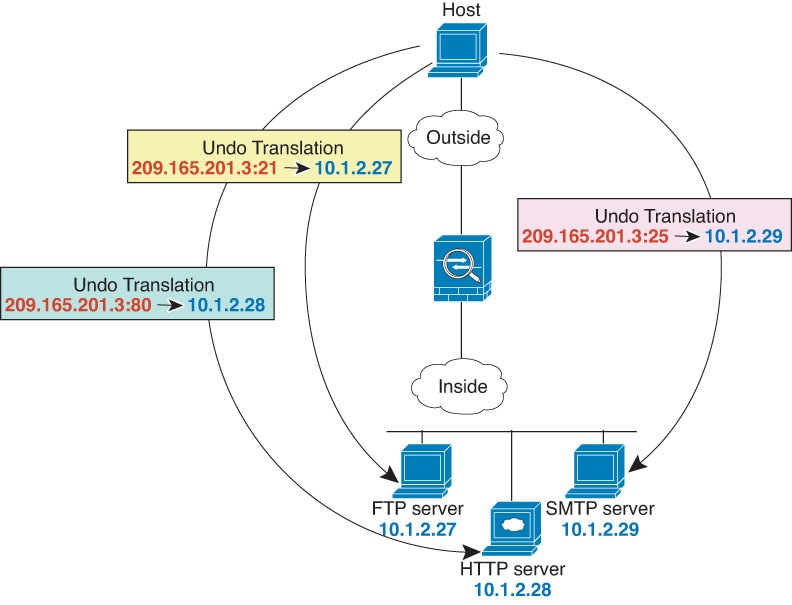
Avoid using overlapping addresses in static and dynamic NAT
policies. For example, with overlapping addresses, a PPTP connection can fail
to get established if the secondary connection for PPTP hits the static instead
of dynamic xlate.
-
You cannot use overlapping addresses in the source address of a NAT rule and a remote access VPN address pool.
-
If you specify a destination interface in a rule, then that interface is used as the egress interface rather than looking
up the route in the routing table. However, for identity NAT, you have the option to use a route lookup instead.
-
If you use PAT on Sun RPC traffic, which is used to connect to NFS servers, be aware that
the NFS server might reject connections if the PAT'ed port is above 1024.
The default configuration of NFS servers is to reject connections from ports
higher than 1024. The error is typically "Permission Denied." Mapping ports above 1024 happens
if you do not select the option to include the reserved ports (1-1023)
in the port range of a PAT pool. You can avoid this problem by
changing the NFS server configuration to allow all port numbers.
-
NAT applies to through traffic only. Traffic generated by the system is not subject to NAT.
-
Do not name a network object or group pat-pool, using any combination of
upper- or lower-case letters.
-
The unidirectional option is mainly useful for testing purposes and might not
work with all protocols. For example, SIP requires protocol inspection to
translate SIP headers using NAT, but this will not occur if you make the
translation unidirectional.
-
You cannot use NAT on the internal payload of Protocol Independent Multicast
(PIM) registers.
-
(Manual
NAT) When writing NAT rules for a dual ISP interface setup (primary and
backup interfaces using service level agreements in the routing
configuration), do not specify destination criteria in the rule. Ensure the
rule for the primary interface comes before the rule for the backup
interface. This allows the device to choose the correct NAT destination
interface based on the current routing state when the primary ISP is
unavailable. If you specify destination objects, the NAT rule will always
select the primary interface for the otherwise duplicate rules.
-
If you get the ASP drop reason nat-no-xlate-to-pat-pool for traffic that
should not match the NAT rules defined for the interface, configure identity
NAT rules for the affected traffic so the traffic can pass untranslated.
-
If you configure NAT for GRE tunnel endpoints, you must disable keepalives on the endpoints or the tunnel cannot be established.
The endpoints send keepalives to the original addresses.
-
DHCP and BOOTP share ports UDP/67-68. Because BOOTP is obsolete, writing NAT rules for the bootps port can cause port allocation
problems when also running DHCP. Consider using DHCP relay instead for transmitting DHCP requests between network segments.
-
(Secure Firewall 200) If you use PAT with SIP sessions, and you send thousands of SIP connections through the device, reduce the SIP invite timeout
to the minimum of 1 minute. This can avoid problems with free memory consumption by xlates related to the SIP sessions. Configure the timeout on the Timeout page in the Platform Settings policy.
-
In rare cases, return traffic (server to client) with an existing translation (xlate) might be logged as a new flow in Connection
Events. This can occur when the client has already terminated the connection and the server sends another packet that reaches
the device during the brief interval between connection closure and xlate removal, often due to application behavior or TCP
stack cleanup. Because the device removes the xlate only after deleting the connection, a server packet can arrive while the
xlate still exists. If no valid connection entry is found, the device logs a separate connection event based on the matched
Access Control Policy rule.






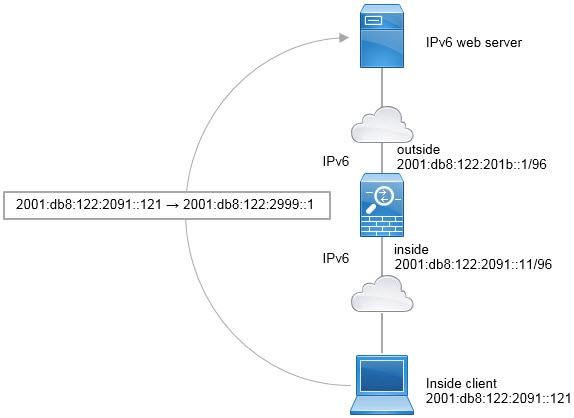
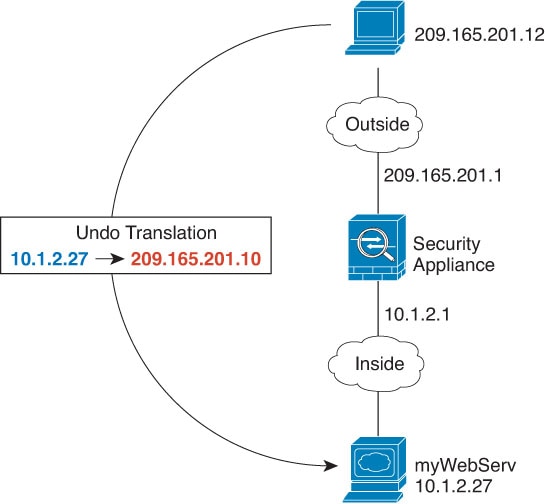
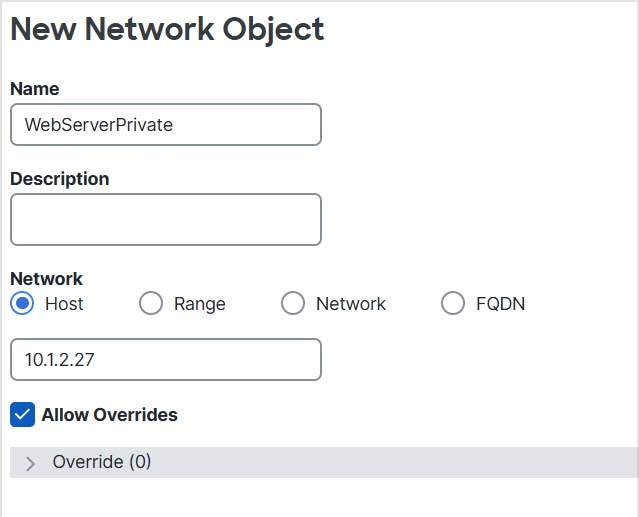
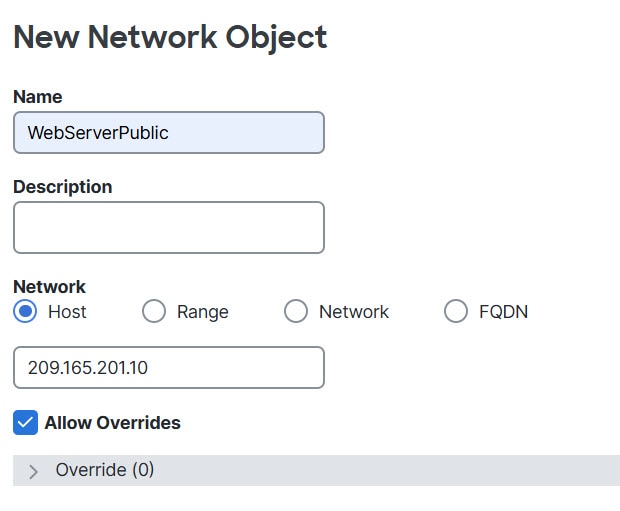
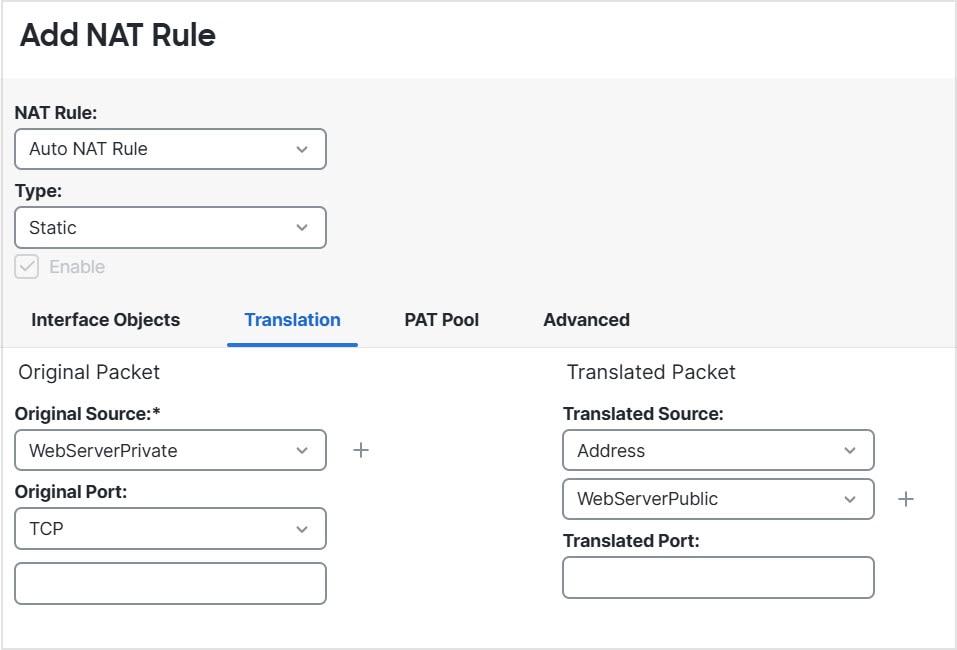
 Feedback
Feedback