Login Requirements for Security Cloud Control
The IdP account contains the user's credentials and the IdP authenticates the user based on those credentials. Mutlifactor authentication provides an added layer of identity security. The Security Cloud Control user record primarily contains the username, the Security Cloud Control tenant with which they are associated, and the user's role. When a user logs in, Security Cloud Control tries to map the IdP's user ID to an existing user record on a tenant in Security Cloud Control. The user is logged in to that tenant when Security Cloud Control finds a match.
Unless your enterprise has its own single sign-on identity provider, your identity provider is Security Cloud Sign On. Security Cloud Sign On uses Duo for multifactor authentication.
To log into Security Cloud Control, you must first create an account in Cisco Security Cloud Sign On, configure multifactor authentication (MFA) using Duo Security and have your tenant Super Admin create a Security Cloud Control record.
On October 14, 2019, Security Cloud Control converted all previously existing tenants to use Cisco Security Cloud Sign On as their identity provider and Duo for MFA.
 Note |
|
If your Security Cloud Control tenant existed before October 14, 2019, see Migrate to Cisco Security Cloud Sign On Identity Provider.
Initial Login to Your New Security Cloud Control Tenant
Before You Begin
 Install DUO Security. We recommend installing the Duo Security app on a mobile phone. Review Duo Guide to Two Factor Authentication: Enrollment Guide if you have questions about installing Duo.
Install DUO Security. We recommend installing the Duo Security app on a mobile phone. Review Duo Guide to Two Factor Authentication: Enrollment Guide if you have questions about installing Duo.
Time Synchronization. You are going to use your mobile device to generate a one-time password. It is important that your device clock is synchronized with real time as the OTP is time-based. Make sure your device clock is set automatically or manually set it to the correct time.
Security Cloud Control uses Cisco Security Cloud Sign On as its identity provider and Duo for multifactor authentication (MFA). If you do not have a Cisco Security Cloud Sign On account, when you create a new Security Cloud Control tenant, the provisioning flow involves various steps, including creating a Security Cloud Sign On account and configuring MFA using Duo. To create a new tenant, click here.
MFA provides an added layer of security in protecting your user identity. Two-factor authentication, a type of MFA, requires two components, or factors, to ensure the identity of the user logging in to Security Cloud Control. The first factor is a username and password, and the second is a one-time password (OTP), which is generated on demand.
 Important |
If your Security Cloud Control tenant existed before October 14, 2019, use Migrate to Cisco Security Cloud Sign On Identity Provider for login instructions instead of this article. |
Signing in to Security Cloud Control in Different Regions
These are the URLs you use to sign in to Security Cloud Control in different AWS regions:
|
Region |
Security Cloud Control URL |
|---|---|
|
Asia-Pacific and Japan (APJ) |
|
|
Australia (AUS) |
|
|
Europe, the Middle East, and Africa (EMEA) |
|
|
India (IN) |
|
|
United States (US) |
Troubleshooting Login Failures
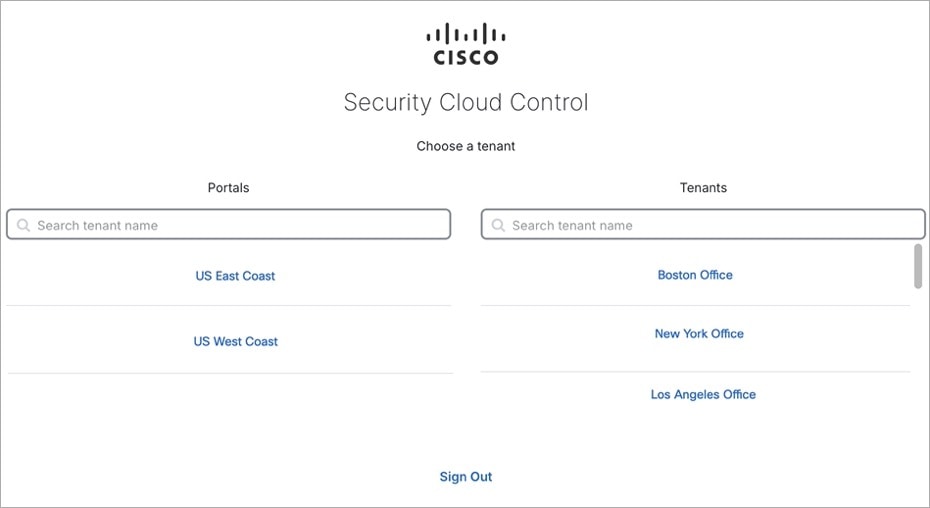
Login Fails Because You are Inadvertently Logging in to the Wrong Security Cloud Control Region
Make sure you are logging in to the appropriate Security Cloud Control region. After you log in to https://sign-on.security.cisco.com, you will be given a choice of what region to access.
 ), and perform device actions using the options in the right pane. You can also see
device information such as version, number of devices being managed by the management
center, device type, and the synchronization status of the device. Clicking on the
managed devices icon takes you to the
), and perform device actions using the options in the right pane. You can also see
device information such as version, number of devices being managed by the management
center, device type, and the synchronization status of the device. Clicking on the
managed devices icon takes you to the 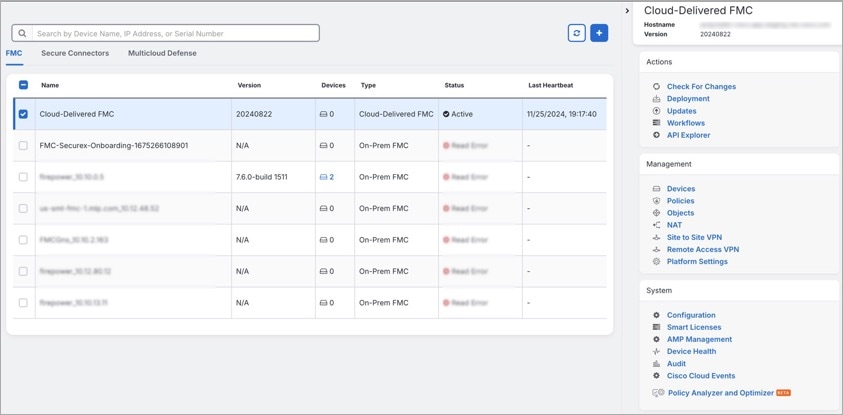
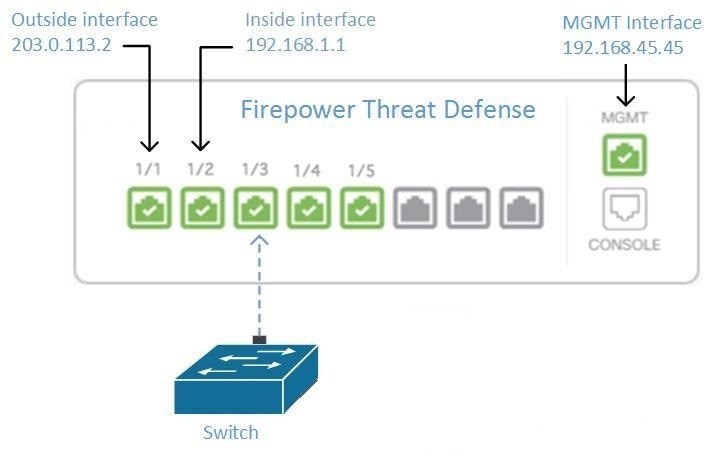
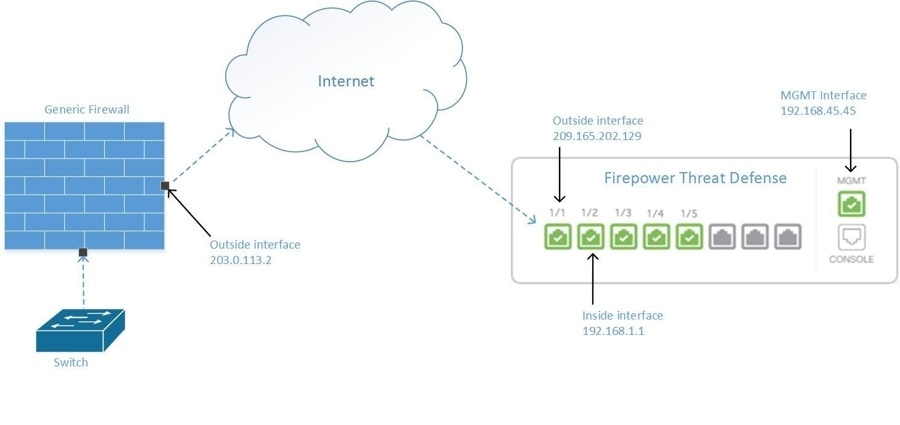
 .
.


 and check the Unassociated checkbox.
and check the Unassociated checkbox.
 .
.
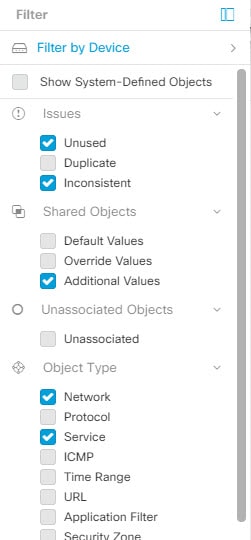

 .
.
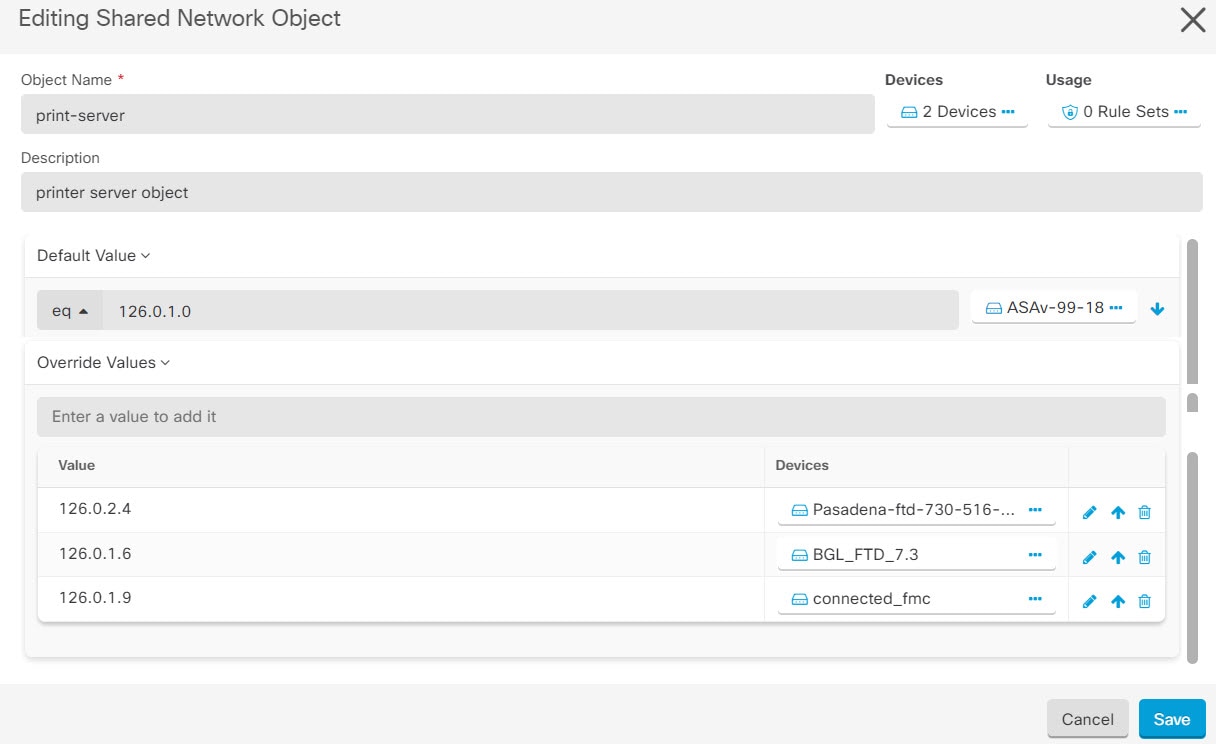
 to create an object.
to create an object.
 in the
in the  arrow in
arrow in  arrow in
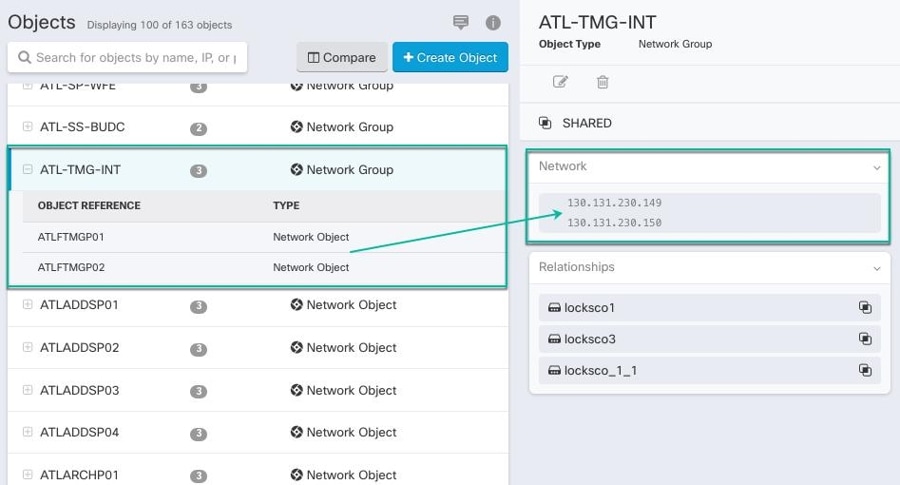
arrow in  appearing beside the object name or network group to modify them.
appearing beside the object name or network group to modify them.
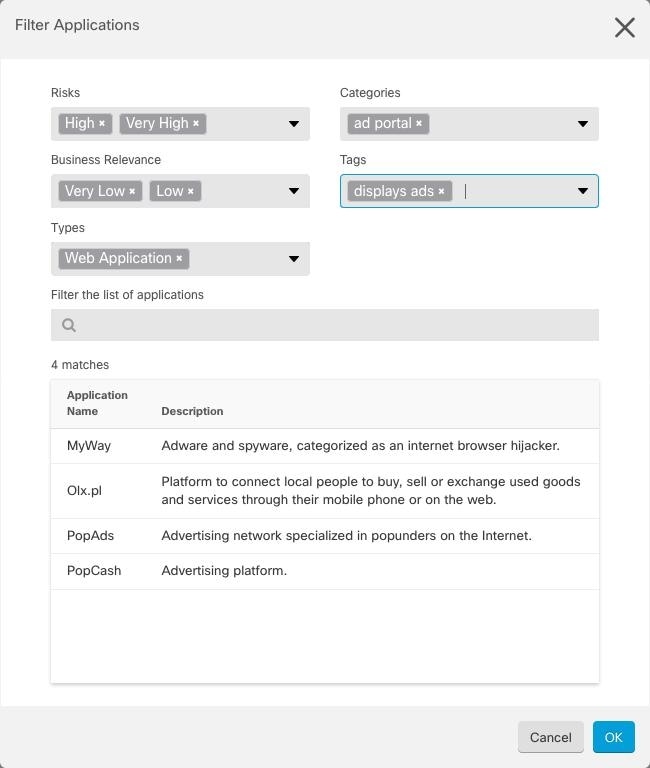


 .
.
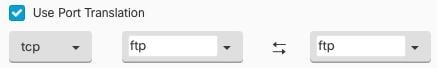
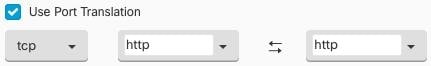
 Feedback
Feedback