Manage Objects
An object is a container of information that you can use in one or more security policies. Objects make it easy to maintain policy consistency. You can create a single object, use it different policies, modify the object, and that change is propagated to every policy that uses the object. Without objects, you would need to modify all the policies, individually, that require the same change.
When you onboard a device, Security Cloud Control recognizes all the objects used by that device, saves them, and lists them on the Objects page. From the Objects page, you can edit existing objects and create new ones to use in your security policies.
Security Cloud Control calls an object used on multiple devices a shared object and identifies them in the Objects page with this badge  .
.
Sometimes a shared object develops some "issue" and is no longer perfectly shared across multiple policies or devices:
-
Duplicate objects are two or more objects on the same device with different names but the same values. These objects usually serve similar purposes and are used by different policies. Duplicate objects are identified by this issue icon:
-
Inconsistent objects are objects on two or more devices with the same name but different values. Sometimes users create objects in different configurations with same name and content but over time the values of these objects diverge which creates the inconsistency. Inconsistent objects are identified by this issue icon:

-
Unused objects are objects that exist in a device configuration but are not referenced by another object, an access-list, or a NAT rule. Unused objects are identified by this issue icon:

You can also create objects for immediate use in rules or policies. You can create an object that is unassociated with any rule or policy. When you use that unassociated object in a rule or policy, Security Cloud Control creates a copy of it and uses the copy.
You can view the objects managed by Security Cloud Control by navigating to the Objects menu or by viewing them in the details of a network policy.
Security Cloud Control allows you to manage network and service objects across supported devices from one location. With Security Cloud Control, you can manage objects in these ways:
-
Search for and filter all your objects based on a variety of criteria.
-
Find duplicate, unused, and inconsistent objects on your devices and consolidate, delete, or resolve those object issues.
-
Find unassociated objects and delete them if they are unused.
-
Discover shared objects that are common across devices.
-
Evaluate the impact of changes to an object on a set of policies and devices before committing the change.
-
Compare a set of objects and their relationships with different policies and devices.
-
Capture objects in use by a device after it has been on-boarded to Security Cloud Control.
If you have issues with creating, editing, or reading objects from an onboarded device, see Troubleshoot Security Cloud Control for more information.
Object Types
The following table describes the objects that you can create for your devices and manage using Security Cloud Control.
|
Object |
Description |
|---|---|
|
Address pool objects can be configured to match against an individual IPv4 or IPv6 address or an IP address range. |
|
|
AnyConnect Client Profile objects are file objects and represent files used in configurations, typically for remote access VPN policies. They can contain an AnyConnect Client Profile and AnyConnect Client Image files. |
|
|
Network groups and network objects (collectively referred to as network objects) define the addresses of hosts or networks. |
|
|
Service objects, service groups, and port groups are reusable components that contain protocols or ports considered part of the TCP/IP protocol suite. |
|
|
A time range object defines a specific time consisting of a start time, an end time, and optional recurring entries. You use these objects in network policies to provide time-based access to certain features or assets. |
|
|
Trustpoints let you manage and track digital certificates in ASA. |
|
Object |
Description |
|---|---|
|
An application filter object defines the applications used in an IP connection, or a filter that defines applications by type, category, tag, risk, or business relevance. You can use these objects in policies to control traffic instead of using port specifications. |
|
|
AnyConnect Client Profile objects are file objects and represent files used in configurations, typically for remote access VPN policies. They can contain an AnyConnect Client Profile and AnyConnect Client Image files. |
|
|
Digital certificates provide digital identification for authentication. Certificates are used for SSL (Secure Socket Layer), TLS (Transport Layer Security), and DTLS (Datagram TLS) connections, such as HTTPS and LDAPS. |
|
|
DNS servers are needed to resolve fully-qualified domain names (FQDN), such as www.example.com, to IP addresses. You can configure different DNS group objects for management and data interfaces. |
|
|
A geolocation object defines countries and continents that host the device that is the source or destination of traffic. You can use these objects in policies to control traffic instead of using IP addresses. |
|
|
An IKEv1 policy object contain the parameters required for IKEv1 policies when defining VPN connections. |
|
|
IKEv2 Policy |
An IKEv2 policy objects contain the parameters required for IKEv2 policies when defining VPN connections. |
|
IKEv1 IPSEC Proposal |
IPsec Proposal objects configure the IPsec proposal used during IKE Phase 1 negotiations. The IPsec proposal defines the combination of security protocols and algorithms that secure traffic in an IPsec tunnel. |
|
IKEv2 IPSEC Proposal |
IPsec Proposal objects configure the IPsec proposal used during IKE Phase 2 negotiations. The IPsec proposal defines the combination of security protocols and algorithms that secure traffic in an IPsec tunnel. |
|
Network groups and network objects (collectively referred to as network objects) define the addresses of hosts or networks. |
|
|
A security zone is a grouping of interfaces. Zones divide the network into segments to help you manage and classify traffic. |
|
|
Service objects, service groups, and port groups are reusable components that contain protocols or ports considered part of the TCP/IP protocol suite. |
|
|
A SGT dynamic object identifies source or destination addresses based on an SGT assigned by ISE and can then be matched against incoming traffic. |
|
|
A syslog server object identifies a server that can receive connection-oriented or diagnostic system log (syslog) messages. |
|
|
Use URL objects and groups (collectively referred to as URL objects) to define the URL or IP addresses of web requests. You can use these objects to implement manual URL filtering in access control policies or blocking in Security Intelligence policies. |
|
Object |
Description |
|---|---|
|
Network groups and network objects (collectively referred to as network objects) define the addresses of hosts or networks. |
|
|
Service objects, service groups, and port groups are reusable components that contain protocols or ports considered part of the TCP/IP protocol suite. |
Shared Objects

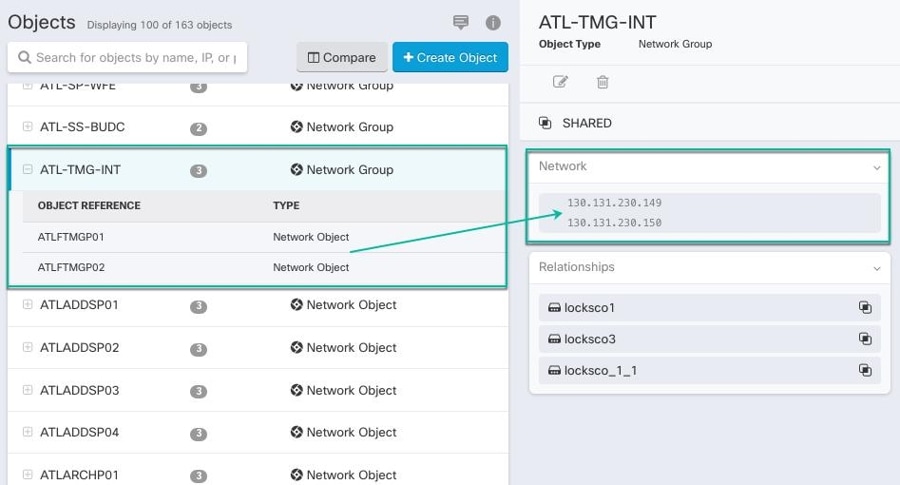
When looking at a shared object, Security Cloud Control shows you the contents of the object in the object table. Shared objects have exactly the same contents. Security Cloud Control shows you a combined or "flattened" view of the elements of the object in the details pane. Notice that in the details pane, the network elements are flattened into a simple list and not directly associated with a named object.
Object Overrides
An object override allows you to override the value of a shared network object on specific devices. Security Cloud Control uses the corresponding value for the devices that you specify when configuring the override. Although the objects are on two or more devices with the same name but different values, Security Cloud Control doesn't identify them as Inconsistent objects only because these values are added as overrides.
You can create an object whose definition works for most devices, and then use overrides to specify modifications to the object for the few devices that need different definitions. You can also create an object that needs to be overridden for all devices, but its use allows you to create a single policy for all devices. Object overrides allow you to create a smaller set of shared policies for use across devices without giving up the ability to alter policies when needed for individual devices.
For example, consider a scenario where you have a printer server in each of your offices, and you have created a printer server
object print-server. You have a rule in your ACL to deny printer servers from accessing the internet. The printer server object has a default
value that you want to change from one office to another. You can do this by using object overrides and maintain rule and
"printer-server" object consistent across all locations, although their values may be different.
 Note |
Security Cloud Control allows you to override objects associated with the rules in a ruleset. When you add a new object to a rule, you can override it only after you attach a device to the ruleset and save the changes. See Configure Rulesets for an FTD for more information. |
 Note |
If there are inconsistent objects, you can combine them into a single shared object with overrides. For more information, see Resolve Inconsistent Object Issues. |
Unassociated Objects
You can create objects for immediate use in rules or policies. You can also create an object that is unassociated with any rule or policy. When you use that unassociated object in a rule or policy, Security Cloud Control creates a copy of it and uses the copy. The original unassociated object remains among the list of available objects until it is either deleted by a nightly maintenance job, or you delete it.
Unassociated objects remain in Security Cloud Control as a copy to ensure that not all configurations are lost if the rule or policy associated with the object is deleted accidentally.
In the left pane, click Objects >  and check the Unassociated checkbox.
and check the Unassociated checkbox.
Compare Objects
Procedure
|
Step 1 |
In the left pane, click Objects and choose an option. |
|
Step 2 |
Filter the objects on the page to find the objects you want to compare. |
|
Step 3 |
Click the Compare button |
|
Step 4 |
Select up to three objects to compare. |
|
Step 5 |
View the objects, side-by-side, at the bottom of the screen.
|
|
Step 6 |
(Optional) The Relationships box shows how an object is used. It may be associated with a device or a policy. If the object is associated with a device, you can click the device name and then click View Configuration to see the configuration of the device. Security Cloud Control shows you the device's configuration file and highlights the entry for that object. |
Filters
You can use many different filters on the Security Devices and Objects pages to find the devices and objects you are looking for.
To filter, click  in the left-hand pane of the Security Devices, Policies, and Objects tabs:
in the left-hand pane of the Security Devices, Policies, and Objects tabs:
The Security Devices filter allows you to filter by device type, hardware and software versions, snort version, configuration status, connection states, conflict detection, and secure device connectors, and labels. You can apply filters to find devices within a selected device type tab. You can use filters to find devices within the selected device type tab.
 Note |
When the FTD tab is opened, the filter pane provides filters to show FDM-managed devices based on the management application through which the devices are accessed from Security Cloud Control.
|
The object filter allows you to filter by device, issue type, shared objects, unassociated objects, and object type. You can include system objects in your results or not. You can also use the search field to search for objects in the filter results that contain a certain name, IP address, or port number.
The object type filter allows you to filter objects by type, such as network object, network group, URL object, URL group, service object, and service group. The shared objects filter allows filtering objects having default values or override values.
When filtering devices and objects, you can combine your search terms to create several potential search strategies to find relevant results.
In the following example, filters are applied to search for objects that are "Issues (Unused OR Inconsistent) AND Shared Objects (with Default Values OR Additional Values) AND Unassociated Objects."
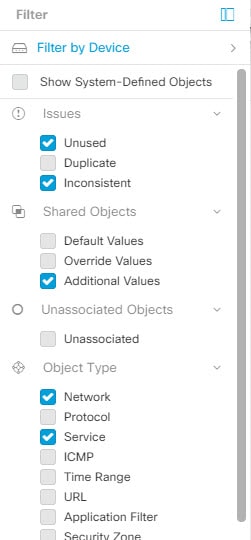
Object Filters
To filter, click  in the left-hand pane of the Objects tab:
in the left-hand pane of the Objects tab:
-
Filter by Device: Lets you pick a specific device so that you can see objects found on the selected device.
-
Issues: Lets you pick unused, duplicate, and inconsistent objects to view.
-
Ignored Issues: Lets you view all the objects whose inconsistencies you had ignored.
-
Shared Objects: Lets you view all the objects that Security Cloud Control has found to be shared on more than one device. You can choose to see shared objects with only default values or override values, or both.
-
Unassociated Objects: Lets you view all the objects that are not associated with any rule or policy.
-
Object Type: Lets you select an object type to see only those type of objects that you have selected, such as network objects, network groups, URL objects, URL groups, service objects, and service groups.
Sub filters – Within each main filter, there are sub-filters you can apply to further narrow down your selection. These sub-filters are based on Object Type – Network, Service, Protocol, etc.
The selected filters in this filter bar would return objects that match the following criteria:
* Objects that are on one of two devices. (Click Filter by Device to specify the devices.) AND are
* Inconsistent objects AND are
* Network objects OR Service objects AND
* Have the word "group" in their object naming convention
Because Show System Objects is checked, the result would include both system objects and user-defined objects.
Show System-Defined Objects Filter
Some devices come with predefined objects for common services. These system objects are convenient because they are already made for you and you can use them in your rules and policies. There can be many system objects in the objects table. System objects cannot be edited or deleted.
Show System-Defined Objects is off by default. To display system objects in the object table, check Show System-Defined Objects in the filter bar. To hide system objects in the object table, leave Show System Objects unchecked in the filter bar.
If you hide system objects, they will not be included in your search and filtering results. If you show system objects, they will be included in your object search and filtering results.
Configure Object Filters
You can filter on as few or as many criteria as you want. The more categories you filter by, the fewer results you should expect.
Procedure
|
Step 1 |
In the left pane, click Objects and choose an option. |
|
Step 2 |
In the left pane, click Objects. |
|
Step 3 |
Open the filter panel by clicking the filter icon |
|
Step 4 |
If you want to restrict your results to those found on particular devices:
|
|
Step 5 |
Check Show System Objects to include system objects in your search results. Uncheck Show System Objects to exclude system objects from your search results. |
|
Step 6 |
Check the object Issues you want to filter by. If you check more than one issue, objects in any of the categories you check are included in your filter results. |
|
Step 7 |
Check Ignored issues if you want to see the object that had issues but was ignored by the administrator. |
|
Step 8 |
Check the required filter in Shared Objects if you are filtering for objects shared between two or more devices.
|
|
Step 9 |
Check Unassociated if you are filtering for objects that are not part of any rule or policy. |
|
Step 10 |
Check the Object Types you want to filter by. |
|
Step 11 |
You can also add an object name, IP address, or port number to the Objects search field to find objects with your search criteria among the filtered results. |
When to Exclude a Device from Filter Criteria
When adding a device to filtering criteria, the results show you the objects on a device but not the relationships of those objects to other devices. For example, assume ObjectA is shared between ASA1 and ASA2. If you were to filter objects to find shared objects on ASA1, you would find ObjectA but the Relationships pane would only show you that the object is on ASA1.
To see all the devices to which an object is related, don't specify a device in your search criteria. Filter by the other criteria and add search criteria if you choose to. Select an object that Security Cloud Control identifies and then look in the Relationships pane. You will see all the devices and policies the object is related to.
Unignore Objects
One way to resolve unused, duplicate, or inconsistent objects is to ignore them. You may decide that though an object is unused, a duplicate, or inconsistent, there are valid reasons for that state and you choose to leave the object issue unresolved. At some point in the future, you may want to resolve those ignored objects. As Security Cloud Control does not display ignored objects when you search for object issues, you will need to filter the object list for ignored objects and then act on the results.
Procedure
|
Step 1 |
In the left pane, click Objects and choose an option. |
|
Step 2 |
In the Object table, select the object you want to unignore. You can unignore one object at a time. |
|
Step 3 |
Click Unignore in the details pane. |
|
Step 4 |
Confirm your request. Now, when you filter your objects by issue, you should find the object that was previously ignored. |
Deleting Objects
You can delete a single object or mulitple objects.
Delete a Single Object
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, choose Objects and choose an option. |
|
Step 2 |
In the left pane, click Objects. |
|
Step 3 |
Locate the object you want to delete by using object filters and the search field, and select it. |
|
Step 4 |
Review the Relationships pane. If the object is used in a policy or in an object group, you cannot delete the object until you remove it from that policy or group. |
|
Step 5 |
In the Actions pane, click the Remove icon |
|
Step 6 |
Confirm that you want to delete the object by clicking OK. |
|
Step 7 |
Review and deploy the changes you made, or wait and deploy multiple changes at once. |
Delete a Group of Unused Objects
As you onboard devices and start resolving object issues, you find many unused objects. You can delete up to 50 unused objects at a time.
Procedure
|
Step 1 |
Use the Issues filter to find unused objects. You can also use the Device filter to find objects that are not associated with a device by selecting No Device. Once you have filtered the object list, the object checkboxes appear. |
|
Step 2 |
Check the Select all checkbox in the object table header to select all the objects found by the filter that appear in the object table; or, check individual checkboxes for individual objects you want to delete. |
|
Step 3 |
In the Actions pane, click the Remove icon |
|
Step 4 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Network Objects
A network object can contain a host name, a network IP address, a range of IP addresses, a fully qualified domain name (FQDN), or a subnetwork expressed in CIDR notation. Network groups are collections of network objects and other individual addresses or subnetworks that you add to the group. Network objects and network groups are used in access rules, network policies, and NAT rules.
Note that not all platforms support network objects, such as Cisco Meraki and Multicloud Defense; when you share dynamic objects, Security Cloud Control automatically translates the appropriate information from the originating platform or device into a set of usable information that Security Cloud Control can use.
|
Device type |
IPv4 / IPv6 |
Single Address |
Range of addresses |
Fully Qualified Domain Name |
Subnet using CIDR Notation |
|---|---|---|---|---|---|
|
ASA |
IPv4 and IPv6 |
Yes |
Yes |
Yes |
Yes |
|
FTD |
IPv4 and IPv6 |
Yes |
Yes |
Yes |
Yes |
|
Multicloud Defense |
IPv4 and IPv6 |
Yes |
Yes |
Yes |
Yes |
|
Device type |
IP Value |
Network Object |
Network Groups |
|---|---|---|---|
|
ASA |
Yes |
Yes |
Yes |
|
FTD |
No |
Yes |
Yes |
|
Multicloud Defense |
Yes |
Yes |
Yes |
Reusing Network Objects Across Products
If you have a Security Cloud Control tenant with a Cloud-Delivered Firewall Management Center and one or more on-premises management centers onboarded to your tenant:
-
When you create a Secure Firewall Threat Defense, FDM-managed Firewall Threat Defense, ASA, or Meraki network object or group, a copy of the object is also added to the objects list on the Objects page used when configuring Cloud-Delivered Firewall Management Center, and vice versa.
-
When you create a Secure Firewall Threat Defense, FDM-managed Firewall Threat Defense, or ASA network object or group, an entry is created in the Devices with Pending Changes page for each On-Premises Firewall Management Center for which Discover & Manage Network Objects is enabled. From this list, you can choose and deploy the object to the on-premises management center on which you want to use the object and discard the ones that you do not want. Navigate , select the on-premises management center, and click Objects to see your objects in the On-Premises Firewall Management Center user interface and assign them to policies.
Changes you make to network objects or groups on either page apply to the object or group instance on both pages. Deleting an object from one page also deletes the corresponding copy of the object from the other page.
Exceptions:
-
If a network object of the same name already exists for Cloud-Delivered Firewall Management Center, the new Secure Firewall Threat Defense, FDM-managed Firewall Threat Defense, ASA, or Meraki network object will not be replicated on the Objects page of Security Cloud Control.
-
Network objects and groups in onboarded Firewall Threat Defense devices that are managed by on-premises Secure Firewall Management Center are not replicated and cannot be used in Cloud-Delivered Firewall Management Center.
Note that for on-premises Secure Firewall Management Center instances that have been migrated to Cloud-Delivered Firewall Management Center, network objects and groups are replicated to the Security Cloud Control objects page if they are used in policies that were deployed to FTD devices.
-
Sharing Network Objects between Security Cloud Control and Cloud-Delivered Firewall Management Center is automatically enabled on new tenants but must be requested for existing tenants. If your network objects are not being shared with Cloud-Delivered Firewall Management Center, contact TAC to have the features enabled on your tenant.
-
Sharing network objects between Security Cloud Control and On-Premises Management Center is not automatically enabled on Security Cloud Control for new on-premises management centers onboarded to Security Cloud Control. If your network objects are not being shared with On-Premises Management Center, ensure the Discover & Manage Network Objects toggle button is enabled for the on-premises management center in Settings or contact TAC to have the features enabled on your tenant.
Viewing Network Objects
Network objects you create using Security Cloud Control and those Security Cloud Control recognizes in an onboarded device's configuration are displayed on the Objects page. They are labeled with their object type. This allows you to filter by object type to quickly find the object you are looking for.
When you select a network object on the Objects page, you see the object's values in the Details pane. The Relationships pane shows you if the object is used in a policy and on what device the object is stored.
When you click on a network group, you see the contents of that group. The network group is a conglomerate of all the values given to it by the network objects.
Create or Edit ASA Network Objects and Network Groups
An ASA network object can contain a hostname, an IP address, or a subnet address expressed in CIDR notation. Network groups are conglomerates of network objects, network groups, and IP addresses that are used in access rules, network policies, and NAT rules. You can create, read, update, and delete network objects and network groups using Security Cloud Control.
|
Device type |
IPv4 / IPv6 |
Single Address |
Range of addresses |
Partially Qualified Domain Name (PQDN) |
Subnet using CIDR Notation |
|---|---|---|---|---|---|
|
ASA |
IPv4 / IPv6 |
Yes |
Yes |
Yes |
Yes |
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Create an ASA Network Object
A network object can contain a host name, a network IP address, a range of IP addresses, a fully qualified domain name (FQDN), or a subnetwork expressed in CIDR notation. Network objects are used in access rules, network policies, and NAT rules. You can create, update, and delete network objects and network groups using Security Cloud Control.
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click the blue plus button |
||
|
Step 3 |
Click . |
||
|
Step 4 |
Enter an object name. |
||
|
Step 5 |
Select Create a network object. |
||
|
Step 6 |
(optional) Enter an object description. |
||
|
Step 7 |
In the Value section, add the IP address information in one of these ways:
|
||
|
Step 8 |
Click Add.
|
Create an ASA Network Group
A network group can contain IP address values, network objects, and network groups. When you are creating a new network group, you can search for existing objects by their name, IP addresses, IP address range, or FQDN and add them to the network group. If the object isn't present, you can instantly create that object in the same interface and add it to the network group. Network groups can contain both IPv4 and IPv6 addresses.
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click the blue plus button |
||
|
Step 3 |
Click . |
||
|
Step 4 |
Enter an Object Name. |
||
|
Step 5 |
Select Create a network group. |
||
|
Step 6 |
(optional) Enter an object description. |
||
|
Step 7 |
In the Values field, enter a value or object name. When you start typing, Security Cloud Control provides object names or values that match your entry. |
||
|
Step 8 |
You can choose one of the existing objects shown or create a new one based on the name or value that you have entered. |
||
|
Step 9 |
If Security Cloud Control finds a match, to choose an existing object, click Add to add the network object or network group to the new network group. |
||
|
Step 10 |
If you have entered a value or object that is not present, you can perform one of the following:
It is possible to create a new object even though the value is already present. You can make changes to those objects and save them.
|
||
|
Step 11 |
After adding the required objects, click Add to create a new network group. |
||
|
Step 12 |
Edit an ASA Network Object
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
||
|
Step 3 |
Select the network object and click the edit icon |
||
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created in the procedures above.
|
||
|
Step 5 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
||
|
Step 6 |
Click Confirm to finalize the change to the object and any devices affected by it. |
Edit an ASA Network Group
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Locate the network group you want to edit by using object filters and search field. |
||
|
Step 3 |
Select the network group and click the edit icon |
||
|
Step 4 |
If you want to change the objects or network groups that are already added to the network group, perform the following steps:
|
||
|
Step 5 |
If you want to add new network objects or network groups to this network group, you have to perform the following steps:
It is possible to create a new object even though the value is already present. You can make changes to those objects and save them. |
||
|
Step 6 |
Click Save. Security Cloud Control displays the policies that will be affected by the change. |
||
|
Step 7 |
Click Confirm to finalize the change to the object and any devices affected by it. |
||
|
Step 8 |
Add Additional Values to a Shared Network Group in Security Cloud Control
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the shared network group that you want to edit by using object filters and search field. |
|
Step 3 |
Click the edit icon
|
|
Step 4 |
In the Additional Values field, enter a value or name. When you start typing, Security Cloud Control provides object names or values that match your entry. |
|
Step 5 |
You can choose one of the existing objects shown or create a new one based on the name or value that you have entered. |
|
Step 6 |
If Security Cloud Control finds a match, to choose an existing object, click Add to add the network object or network group to the new network group. |
|
Step 7 |
If you have entered a value or object that is not present, you can perform one of the following:
It is possible to create a new object even though the value is already present. You can make changes to those objects and save them. |
|
Step 8 |
In the Devices column, click the cell associated with the newly added object and click Add Devices. |
|
Step 9 |
Select the devices that you want and click OK. |
|
Step 10 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
|
Step 11 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 12 |
Edit Additional Values in a Shared Network Group in Security Cloud Control
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object having the override you want to edit by using object filters and search field. |
|
Step 3 |
Click the edit icon |
|
Step 4 |
Modify the override value:
|
|
Step 5 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
|
Step 6 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 7 |
Deleting Network Objects and Groups in Security Cloud Control
If Cloud-Delivered Firewall Management Center is deployed on your tenant:
Deleting a network object or group from the Manage > Objects page deletes the replicated network object or group from the Manage > Objects page on the Cloud-Delivered Firewall Management Center and vice-versa.
Create or Edit a Firepower Network Object or Network Groups
A Firepower network object can contain a hostname, an IP address, or a subnet address expressed in CIDR notation. Network groups are conglomerates of network objects and network groups that are used in access rules, network policies, and NAT rules. You can create, read, update, and delete network objects and network groups using Security Cloud Control.
Firepower network objects and groups can be used by ASA, Firewall Threat Defense, FDM-managed, and Meraki devices. See Reusing Network Objects Across Products.
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
|
Device type |
IPv4 / IPv6 |
Single Address |
Range of addresses |
Partially Qualified Domain Name (PQDN) |
Subnet using CIDR Notation |
|---|---|---|---|---|---|
| Firepower | IPv4 / IPv6 | Yes | Yes | Yes | Yes |
Create a Firepower Network Object
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click the blue plus button |
||
|
Step 3 |
Click . |
||
|
Step 4 |
Enter an Object Name. |
||
|
Step 5 |
Select Create a network object. |
||
|
Step 6 |
In the Value section:
|
||
|
Step 7 |
Click Add. Attention: The newly created network objects aren't associated with any FDM-managed device as they aren't part of any rule or policy. To see these objects, select the Unassociated objects category in object filters. For more information, see Object Filters. Once you use the unassociated objects in a device's rule or policy, such objects are associated with that device. |
Create a Firepower Network Group
A network group can contain network objects and network groups. When you create a new network group, you can search for existing objects by their name, IP addresses, IP address range, or FQDN and add them to the network group. If the object isn't present, you can instantly create that object in the same interface and add it to the network group.
 Note |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the Cloud-Delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click the blue plus button |
|
Step 3 |
Click . |
|
Step 4 |
Enter an Object Name. |
|
Step 5 |
Select Create a network group. |
|
Step 6 |
In the Values field, enter a value or name. When you start typing, Security Cloud Control provides object names or values that match your entry. |
|
Step 7 |
You can choose one of the existing objects shown or create a new one based on the name or value that you have entered. |
|
Step 8 |
If Security Cloud Control finds a match, to choose an existing object, click Add to add the network object or network group to the new network group. |
|
Step 9 |
If you have entered a value or object that is not present, you can perform one of the following:
It is possible to create a new object even though the value is already present. You can make changes to those objects and save them. Note: You can click the edit icon to modify the details. Clicking the delete button doesn't delete the object itself; instead, it removes it from the network group. |
|
Step 10 |
After adding the required objects, click Save to create a new network group. |
|
Step 11 |
Edit a Firepower Network Object
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
||
|
Step 3 |
Select the network object and click the edit icon |
||
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created them in "Create a Firepower Network Group".
|
||
|
Step 5 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
||
|
Step 6 |
Click Confirm to finalize the change to the object and any devices affected by it. |
Edit a Firepower Network Group
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the network group you want to edit by using object filters and search field. |
|
Step 3 |
Select the network group and click the edit icon |
|
Step 4 |
Change the object name and description if needed. |
|
Step 5 |
If you want to change the objects or network groups that are already added to the network group, perform the following steps:
|
|
Step 6 |
If you want to add new network objects or network groups to this network group, you have to perform the following steps:
It's is possible to create a new object even though the value is already present. You can make changes to those objects and save them. |
|
Step 7 |
Click Save. Security Cloud Control displays the policies that will be affected by the change. |
|
Step 8 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 9 |
Add an Object Override
 Caution |
If Cloud-Delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding Cloud-Delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Locate the object to which you want to add an override, using object filters and search field. |
||
|
Step 3 |
Select the network object and click the edit icon |
||
|
Step 4 |
Enter the value in the Override Values dialog box and click + Add Value.
|
||
|
Step 5 |
Once you see that the value is added, click the cell in the Devices column in Override Values. |
||
|
Step 6 |
Click Add Devices, and choose the device to which you want the override to be added. The device you select must contain the object to which you are adding the override. |
||
|
Step 7 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
||
|
Step 8 |
Click Confirm to finalize the addition of the override to the object and any devices affected by it.
|
||
|
Step 9 |
See Object Overrides to know more about object overrides and Edit Object Overrides to edit an existing override. |
Edit Object Overrides
You can modify the value of an existing override as long as the object is present on the device.
Procedure
|
Step 1 |
Navigate to Manage > Objects. |
|
Step 2 |
Locate the object having override you want to edit by using object filters and search field. |
|
Step 3 |
Select the object having override and click the edit icon |
|
Step 4 |
Modify the override value:
|
|
Step 5 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
|
Step 6 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 7 |
Add Additional Values to a Shared Network Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the shared network group you want to edit by using object filters and search field. |
|
Step 3 |
Click the edit icon
|
|
Step 4 |
In the Additional Values field, enter a value or name. When you start typing, Security Cloud Control provides object names or values that match your entry. |
|
Step 5 |
You can choose one of the existing objects shown or create a new one based on the name or value that you have entered. |
|
Step 6 |
If Security Cloud Control finds a match, to choose an existing object, click Add to add the network object or network group to the new network group. |
|
Step 7 |
If you have entered a value or object that is not present, you can perform one of the following:
It is possible to create a new object even though the value is already present. You can make changes to those objects and save them. |
|
Step 8 |
In the Devices column, click the cell associated with the newly added object and click Add Devices. |
|
Step 9 |
Select the devices that you want and click OK. |
|
Step 10 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
|
Step 11 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 12 |
Edit Additional Values in a Shared Network Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object having the override you want to edit by using object filters and search field. |
|
Step 3 |
Click the edit icon |
|
Step 4 |
Modify the override value:
|
|
Step 5 |
Click Save. Security Cloud Control displays the devices that will be affected by the change. |
|
Step 6 |
Click Confirm to finalize the change to the object and any devices affected by it. |
|
Step 7 |
Deleting Network Objects and Groups in Security Cloud Control
If Cloud-Delivered Firewall Management Center is deployed on your tenant:
Deleting a network object or group from the Manage > Objects page deletes the replicated network object or group from the Manage > Objects page on the Cloud-Delivered Firewall Management Center and vice-versa.
Discover and Manage On-Prem Firewall Management Center Network Objects
Procedure
|
Step 1 |
In the left pane, choose to view the Services page. |
||||
|
Step 2 |
If you already have onboarded an on-premises management center to Security Cloud Control, select it. If you want to onboard a new on-premises management center, see Onboard an On-Prem Firewall Management Center. |
||||
|
Step 3 |
Choose Settings from the Actions pane on the right. Note that you do not get to see the Actions pane when you select more than one on-premises management center.
|
||||
|
Step 4 |
Enable the Discover & Manage Network Objects toggle button. If you want your changes to be automatically synchronized with on-premises management center and not staged for review, turn the Enable automatic sync of network objects toggle on.
For every new on-premises management center onboarded to Security Cloud Control, this toggle button needs to be enabled manually. Once you enable this option, Security Cloud Control starts to discover objects from your on-premises management center, which you can share, manage, and use to set consistent object definitions across other platforms managed by Security Cloud Control. In Security Cloud Control, when you add overrides to objects that are discovered from an on-premises management center and push the changes back to the on-premises management center, these objects start accepting overrides in the on-premises management center even if they were not accepting overrides before—the Allow Overrides checkbox in View Network Object window is checked automatically when an override is added from Security Cloud Control.
|
URL Objects
URL objects and URL groups are used by Firepower devices. Use URL objects and groups (collectively referred to as URL objects) to define the URL or IP addresses of web requests. You can use these objects to implement manual URL filtering in access control policies or blocking in Security Intelligence policies. A URL object defines a single URL or IP address, whereas a URL group defines more than one URL or IP address.
Before You Begin
When creating URL objects, keep the following points in mind:
-
If you do not include a path (that is, there is no / character in the URL), the match is based on the server's hostname only. The hostname is considered a match if it comes after the :// separator, or after any dot in the hostname. For example, ign.com matches ign.com and www.ign.com, but it does not match verisign.com.
-
If you include one or more / character, the entire URL string is used for a substring match, including the server name, path, and any query parameters. However, we recommend that you do not use manual URL filtering to block or allow individual web pages or parts of sites, as servers can be reorganized and pages moved to new paths. Substring matching can also lead to unexpected matches, where the string you include in the URL object also matches paths on unintended servers or strings within query parameters.
-
The system disregards the encryption protocol (HTTP vs HTTPS). In other words, if you block a website, both HTTP and HTTPS traffic to that website is blocked, unless you use an application condition to target a specific protocol. When creating a URL object, you do not need to specify the protocol when creating an object. For example, use example.com rather than http://example.com.
-
If you plan to use a URL object to match HTTPS traffic in an access control rule, create the object using the subject common name in the public key certificate used to encrypt the traffic. Also, the system disregards subdomains within the subject common name, so do not include subdomain information. For example, use example.com rather than www.example.com.
However, please understand that the subject common name in the certificate might be completely unrelated to a web site's domain name. For example, the subject common name in the certificate for youtube.com is *.google.com (this of course might change at any time). You will get more consistent results if you use the SSL Decryption policy to decrypt HTTPS traffic so that URL filtering rules work on decrypted traffic.

Note
URL objects will not match HTTPS traffic if the browser resumes a TLS session because the certificate information is no longer available. So even if you carefully configure the URL object, you might get inconsistent results for HTTPS connections.
Create or Edit an FDM-Managed URL Object
URL objects are reusable components that specify a URL or IP address.
To create a URL object, follow these steps:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name and description. |
|
Step 4 |
Select Create a URL object. |
|
Step 5 |
Enter the specific URL or IP address for your object. |
|
Step 6 |
Click Add. |
Create a Firepower URL Group
A URL group can be made up of one or more URL objects representing one or more URLs or IP addresses. The Firepower Device Manager and Firepower Management Center also refer to these objects as "URL Objects."
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name and description. |
|
Step 4 |
Select Create a URL group. |
|
Step 5 |
Add an existing object by clicking Add Object, selecting an object, and clicking Select. Repeat this step to add more objects. |
|
Step 6 |
Click Add when you are done adding URL objects to the URL group. |
Edit a Firepower URL Object or URL Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Filter the objects to find the object you want to edit and then select the object in the object table. |
|
Step 3 |
In the details pane, click |
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 5 |
Click Save. |
|
Step 6 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
Application Filter Objects
Application filter objects are used by Firepower devices. An application filter object defines the applications used in an IP connection, or a filter that defines applications by type, category, tag, risk, or business relevance. You can use these objects in policies to control traffic instead of using port specifications.
Although you can specify individual applications, application filters simplify policy creation and administration. For example, you could create an access control rule that identifies and blocks all high risk, low business relevance applications. If a user attempts to use one of those applications, the session is blocked.
You can select applications and application filters directly in a policy without using application filter objects. However, an object is convenient if you want to create several policies for the same group of applications or filters. The system includes several pre-defined application filters, which you cannot edit or delete.
 Note |
Cisco frequently updates and adds additional application detectors via system and vulnerability database (VDB) updates. Thus, a rule blocking high risk applications can automatically apply to new applications without you having to update the rule manually. |
 Note |
When an FDM-managed device is onboarded to Security Cloud Control, it converts the application filters to application filter objects without altering the rule defined in Access Rule or SSL Decryption. Because of a configuration change, the device's configuration status is changed to 'Not Synced' and requires configuration deployment from Security Cloud Control. In general, FDM does not convert the application filters to application filter objects until you manually save the filters. |
Create and Edit a Firepower Application Filter Object
An application filter object allows you to target hand-picked applications or a group of applications identified by the filters. This application filter objects can be used in policies.
Create a Firepower Application Filter Object
To create an application filter object, follow this procedure:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click . |
||
|
Step 3 |
Enter an object name for the object and optionally, a description. |
||
|
Step 4 |
Click Add Filter and select the applications and filters to add to the object. The initial list shows applications in a continually scrolling list. Click Advanced Filter to see the filter options and to get an easier view for selecting applications. Click Add when you have made your selections. You can repeat the process to add additional applications or filters.
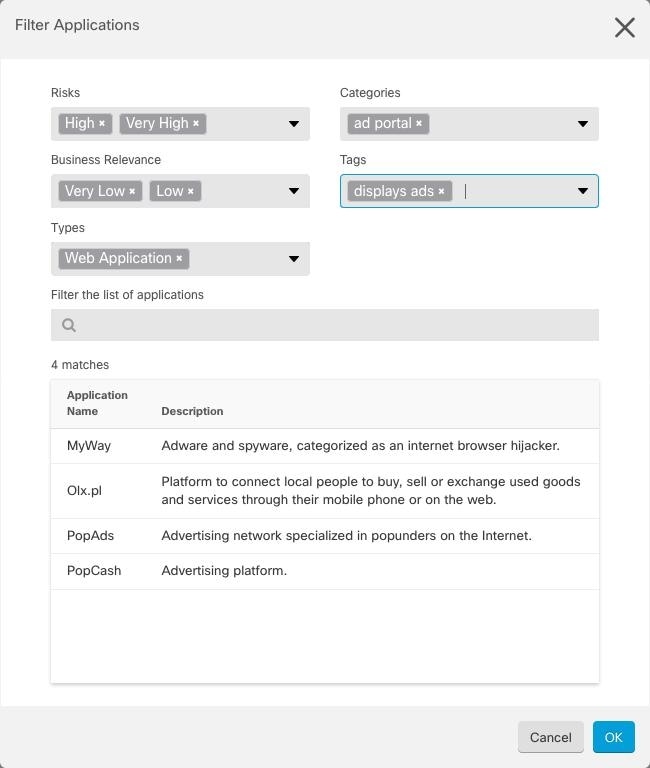
Risks: The likelihood that the application is used for purposes that might be against your organization's security policy, from very low to very high. Business Relevance: The likelihood that the application is used within the context of your organization's business operations, as opposed to recreationally, from very low to very high. Types: The type of application.
Categories: A general classification for the application that describes its most essential function. Tags: Additional information about the application, similar to category. For encrypted traffic, the system can identify and filter traffic using only the applications tagged SSL Protocol. Applications without this tag can only be detected in unencrypted or decrypted traffic. Also, the system assigns the decrypted traffic tag to applications that the system can detect in decrypted traffic only, not encrypted or unencrypted. Applications List (bottom of the display): This list updates as you select filters from the options above the list, so you can see the applications that currently match the filter. Use this list to verify that your filter is targeting the desired applications when you intend to add filter criteria to the rule. To add a specific application or applications to your object, select them from the filtered list. Once you select the applications, the filter will no longer apply. If you want the filter itself to be the object, do not select an application from the list. Then the object will represent every application identified by the filter. |
||
|
Step 5 |
Click OK to save your changes. |
Edit a Firepower Application Filter Object
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object you want to edit. |
|
Step 4 |
Click the edit icon |
|
Step 5 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 6 |
Click Save. |
|
Step 7 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
Geolocation Objects
A geolocation object defines countries and continents that host the device that is the source or destination of traffic. You can use these objects in policies to control traffic instead of using IP addresses. For example, using geographical location, you could easily restrict access to a particular country without needing to know all of the potential IP addresses used there.
You can typically select geographical locations directly in a policy without using geolocation objects. However, an object is convenient if you want to create several policies for the same group of countries and continents.
Update Geolocation Database
To ensure that you are using up-to-date geographical location data to filter your traffic, Cisco strongly recommends that you regularly update the geolocation database (GeoDB). At this time, this is not a task that you can perform using Security Cloud Control. See the following sections of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager for the version your device is running to learn more about the GeoDB and how to update it.
-
Updating System Databases and Feeds
-
Updating System Databases
Create and Edit a Firepower Geolocation Filter Object
You can create a geolocation object by itself on the object page or when creating a security policy. This procedure creates a geolocation object from the object page.
To create a geolocation object, follow these steps:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name for the object and optionally, a description. |
|
Step 4 |
In the filter bar, start typing the name of a country or a region and you are presented with a list of possible matches. |
|
Step 5 |
Check the country, countries, or regions that you want to add to the object. |
|
Step 6 |
Click Add. |
Edit a Geolocation Object
Procedure
|
Step 1 |
In the left pane, choose Manage > Objects. |
|
Step 2 |
Use the filter panes and search field to locate your object. |
|
Step 3 |
In the Actions pane, click Edit. |
|
Step 4 |
You can change the name of the object and add or remove countries and regions to your object. |
|
Step 5 |
Click Save. |
|
Step 6 |
You will be notified if any devices are impacted. Click Confirm. |
|
Step 7 |
If a device or policy was impacted, open the Security Devices page and Preview and Deploy the changes to the device. |
DNS Group Objects
Domain Name System (DNS) groups define a list of DNS servers and some associated attributes. DNS servers are needed to resolve fully-qualified domain names (FQDN), such as www.example.com, to IP addresses. You can configure different DNS group objects for management and data interfaces.
Create a DNS Group Object
Use the following procedure to create a new DNS group object in Security Cloud Control:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click . |
||
|
Step 3 |
Enter an Object Name. |
||
|
Step 4 |
(Optional) Add a description. |
||
|
Step 5 |
Enter the IP address of a DNS server. You can add up to six DNS servers; click the Add DNS Server. If you want to remove a server address, click the delete icon.
|
||
|
Step 6 |
Enter the Domain Search Name. This domain is added to hostnames that are not fully qualified; for example, serverA instead of serverA.example.com. |
||
|
Step 7 |
Enter the number of Retries. The number of times, from 0 to 10, to retry the list of DNS servers when the system does not receive a response. The default is 2. This setting applies to DNS groups used on the data interfaces only. |
||
|
Step 8 |
Enter the Timeout value. The number of seconds, from 1 to 30, to wait before trying the next DNS server. The default is 2 seconds. Each time the system retries the list of servers, this timeout doubles. This setting applies to DNS groups used on the data interfaces only. |
||
|
Step 9 |
Click Add. |
Edit a DNS Group Object
You can edit a DNS group object that was created in Security Cloud Control or in Firewall Device Manager. Use the following procedure to edit an existing DNS group object:
Procedure
|
Step 1 |
In the Security Cloud Control navigation bar on the left, click Manage > Objects. |
|
Step 2 |
Locate the DNS Group Object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object and click the edit icon |
|
Step 4 |
Edit any of the following entries:
|
|
Step 5 |
Click Save. |
|
Step 6 |
Delete a DNS Group Object
Use the following procedure to delete a DNS Group Object from Security Cloud Control:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the DNS Group Object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object and click the Remove icon |
|
Step 4 |
Confirm you want to delete the DNS group object and click Ok. |
|
Step 5 |
Add a DNS Group Object as an FDM-Managed DNS Server
You can add a DNS group object as the preferred DNS Group for either the Data Interface or the Management Interface.
Certificate Objects
Digital certificates provide digital identification for authentication. Certificates are used for SSL (Secure Socket Layer), TLS (Transport Layer Security), and DTLS (Datagram TLS) connections, such as HTTPS and LDAPS.
See the About Certificates and Configuring Certificates following sections of the Resuable Objects chapter of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager for the version your device is running.
About Certificates
Digital certificates provide digital identification for authentication. A digital certificate includes information that identifies a device or user, such as the name, serial number, company, department, or IP address. A digital certificate also includes a copy of the public key for the user or device. Certificates are used for SSL (Secure Socket Layer), TLS (Transport Layer Security), and DTLS (Datagram TLS) connections, such as HTTPS and LDAPS.
You can create the following types of certificate:
-
Internal certificates—Internal identity certificates are certificates for specific systems or hosts. You can generate these yourself using the OpenSSL toolkit or get them from a certificate authority (CA). You can also generate a self-signed certificate.
The system comes with the following pre-defined internal certificates, which you can use as is or replace: DefaultInternalCertificate and DefaultWebServerCertificate
-
Internal Certificate Authority (CA) certificates—Internal CA certificates are certificates that the system can use to sign other certificates. These certificates differ from internal identity certificates with respect to the basic constraints extension and the CA flag, which are enabled for CA certificates but disabled for identity certificates. You can generate these yourself using the OpenSSL toolkit or get them from a certificate authority. You can also generate a self-signed internal CA certificate. If you configure self-signed internal CA certificates, the CA runs on the device itself.
The system comes with the following pre-defined internal CA certificate, which you can use as is or replace: NGFW-Default-InternalCA
-
Trusted Certificate Authority (CA) certificates—A trusted CA certificate is used to sign other certificates. It is self-signed and called a root certificate. A certificate that is issued by another CA certificate is called a subordinate certificate.
Certificate Authorities (CAs) are trusted authorities that "sign" certificates to verify their authenticity, thereby guaranteeing the identity of the device or user. CAs issue digital certificates in the context of a PKI, which uses public-key or private-key encryption to ensure security. A CA can be a trusted third party, such as VeriSign, or a private (in-house) CA that you establish within your organization. CAs are responsible for managing certificate requests and issuing digital certificates.
The system includes many trusted CA certificates from third-party certificate authorities. These are used by SSL decryption policies for Decrypt Re-Sign actions.
For more information, see the Certificate Types Used by Feature section of the Reusable Objects chapter of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager for the version your device is running.
Certificate Types Used by Feature
You need to create the right type of certificate for each feature. The following features require certificates.
Identity Policies (Captive Portal)—Internal Certificate
(Optional.) Captive portal is used in identity policies. Users must accept this certificate when authenticating to the device for purposes of identifying themselves and receiving the IP address associated with their usernames. If you do not supply a certificate, the device uses an automatically generated certificate.
SSL Decryption Policy—Internal, Internal CA, and Trusted CA Certificates.
(Required.) The SSL decryption policy uses certificates for the these purposes:
-
Internal certificates are used for known key decryption rules.
-
Internal CA certificates are used for decrypt re-sign rules when creating the session between the client and FDM-managed device.
-
Trusted CA certificates
-
They are used indirectly for decrypt re-sign rules when creating the session between the FDM-managed device and server. Unlike the other certificates, you do not directly configure these certificates in the SSL decryption policy; they simply need to be uploaded to the system. The system includes a large number of trusted CA certificates, so you might not need to upload any additional certificates.
-
When creating an Active Directory Realm object and configuring the directory server to use encryption.
-
Configuring Certificates
Certificates used in identity policies or SSL decryption policies must be an X509 certificate in PEM or DER format. You can use OpenSSL to generate certificates if needed, obtain them from a trusted Certificate Authority, or create self-signed certificates.
Use these procedures to configure certificate objects:
-
To view or edit a certificate, click either the edit icon or the view icon for the certificate.
-
To delete an unreferenced certificate, click the trash can icon (delete icon) for the certificate. See Deleting Objects.
Uploading Internal and Internal CA Certificates
Internal identity certificates are certificates for specific systems or hosts. You can generate these yourself using the OpenSSL toolkit or get them from a Certificate Authority. You can also generate a self-signed certificate.
Internal Certificate Authority (CA) certificates (Internal CA certificates) are certificates that the system can use to sign other certificates. These certificates differ from internal identity certificates with respect to the basic constraints extension and the CA flag, which are enabled for CA certificates but disabled for identity certificates. You can generate these yourself using the OpenSSL toolkit or get them from a Certificate Authority. You can also generate a self-signed internal CA certificate. If you configure self-signed internal CA certificates, the CA runs on the device itself.
For information on the features that use these certificates, see Certificate Type Used by Feature.
Procedure
This procedure creates an internal or internal CA certificate by uploading a certificate file or pasting existing certificate text into a text box. If you want to generate a self-signed certificate, see Generating Self-Signed Internal and Internal CA Certificates.
To create an internal or internal CA certificate object, or when adding a new certificate object to a policy, follow this procedure:
Procedure
|
Step 1 |
Do one of the following:
|
|
Step 2 |
Enter a Name for the certificate. The name is used in the configuration as an object name only, it does not become part of the certificate itself. |
|
Step 3 |
In step 1, select Internal Certificate or Internal CA. |
|
Step 4 |
In step 2, select Upload to upload the certificate file. |
|
Step 5 |
In step 3, in the Server Certificate area, paste the certificate contents in the text box or upload the certificate file as explained in the wizard. If you paste the certificate into the text box, the certificate must include the BEGIN CERTIFICATE and END CERTIFICATE lines. For example: |
-----BEGIN CERTIFICATE-----
MIICMTCCAZoCCQDdUV3NGK/cUjANBgkqhkiG9w0BAQsFADBdMQswCQYDVQQGEwJV
UzETMBEGA1UECAwKU29tZS1TdGF0ZTEhMB8GA1UECgwYSW50ZXJuZXQgV2lkZ2l0
(...5 lines removed...)
shGJDReRYJQqilhHZrYTWZAYTrD7NQPHutK+ZiJng67cPgnNDuXEn55UwMOQoHBp
HMUwmhiGZlzJM8BpX2Js2yQ3ms30pr8rO+gPCPMCAwEAATANBgkqhkiG9w0BAQsF
AAOBgQCB02CebA6YjJCGr2CJZrQSeUwSveRBpmOuoqm98o2Z+5gJM5CkqgfxwCUn
RV7LRfQGFYd76V/5uor4Wx2ZCjqy6+zuQEm4ZxWNSZpA9UBixFXJCs9MBO4qkG5D
vlk3WYJfcgyJ10h4E4b0W2xiixBU+xoOTLRATnbKY36EWAG5cw==
-----END CERTIFICATE-----|
Step 6 |
In step 3, in the Certificate Key area, paste the key contents into the Certificate Key text box or upload the key file as explained in the wizard. If you paste the key into the text box, the key must include the BEGIN PRIVATE KEY or BEGIN RSA PRIVATE KEY and END PRIVATE KEY or END PRIVATE KEY lines.
|
||
|
Step 7 |
Click Add. |
Uploading Trusted CA Certificates
A trusted Certificate Authority (CA) certificate is used to sign other certificates. It is self-signed and called a root certificate. A certificate that is issued by another CA certificate is called a subordinate certificate.
For information on the features that use these certificates, see Certificate Type Used by Feature.
Obtain a trusted CA certificate from an external certificate authority, or create one using your own internal CA, for example, with OpenSSL tools. Then, use the following procedure to upload the certificate.
Procedure
Procedure
|
Step 1 |
Do one of the following:
|
|
Step 2 |
Enter a Name for the certificate. The name is used in the configuration as an object name only; it does not become part of the certificate itself. |
|
Step 3 |
In step 1, select External CA Certificate and click Continue. The wizard advances to step 3. |
|
Step 4 |
In step 3, in the Certificate Contents area, paste the certificate contents in the text box or upload the certificate file as explained in the wizard. The certificate must adhere to these guidelines:
|
|
Step 5 |
Click Add. |
Generating Self-Signed Internal and Internal CA Certificates
Internal identity certificates are certificates for specific systems or hosts. You can generate these yourself using the OpenSSL toolkit or get them from a Certificate Authority. You can also generate a self-signed certificate.
Internal Certificate Authority (CA) certificates (Internal CA certificates) are certificates that the system can use to sign other certificates. These certificates differ from internal identity certificates with respect to the basic constraints extension and the CA flag, which are enabled for CA certificates but disabled for identity certificates. You can generate these yourself using the OpenSSL toolkit or get them from a Certificate Authority. You can also generate a self-signed internal CA certificate. If you configure self-signed internal CA certificates, the CA runs on the device itself.
You can also create these certificates using OpenSSL, or obtain them from a trusted CA, and upload them. For more information, see Uploading Internal and Internal CA Certificates.
For information on the features that use these certificates, see Certificate Type Used by Feature.
 Note |
New self-signed certificates are generated with a 5-year validity term. Be sure to replace certificates before they expire. |
 Warning |
Upgrading devices that have self-signed certificates may experience issues; see New Certificate Detected for more information. |
Procedure
This procedure generates a self-signed certificate by entering the appropriate certificate field values in a wizard. If you want to create an internal or internal CA certificate by uploading a certificate file, see Uploading Internal and Internal CA Certificates.
To generate a self-signed certificate, follow this procedure:
Procedure
|
Step 1 |
Do one of the following:
|
|
Step 2 |
Enter a Name for the certificate. The name is used in the configuration as an object name only, it does not become part of the certificate itself. |
|
Step 3 |
In step 1, select Internal Certificate or Internal CA. |
|
Step 4 |
In step 2, select Self-Signed to create the self-signed certificate in this step. |
|
Step 5 |
Configure at least one of the following for the certificate subject and issuer information.
|
|
Step 6 |
Click Add. |
Trustpoint Objects
Security Cloud Control allows you to add digital certificates as trustpoint objects and then install them on one or multiple managed ASA devices. A single trustpoint object is a container that holds an identity pair (identity certificate and issuer's CA certificate), identity certificate only, or CA certificate only.
You can configure many trustpoints in an ASA device. The supported certificate formats are PKCS12, PEM, and DER.
Adding an Identity Certificate Object Using PKCS12
This procedure creates an internal certificate identity or internal identity certificate by uploading a certificate file or pasting existing certificate text into a text box. You can generate as many identity certificates as you want.
You can upload a file encoded in PKCS12 format. A PKCS12 is a single file that holds the CA server certificate, any intermediate certificates, and the private key in one encrypted file. A PKCS#12, or PFX, file holds a server certificate, intermediate certificates, and a private key in one encrypted file. Enter the Passphrase value for decryption.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an Object Name for the certificate. The name is used in the configuration as an object name only, it does not become part of the certificate itself. |
|
Step 4 |
In the Certificate Type step, select Identity Certificate. |
|
Step 5 |
In the Import Type step, select Upload to upload the certificate file. The Enrollment step is set to Terminal. |
|
Step 6 |
In the Certificate Contents step, enter the PKCS12 format details. A PKCS#12, or PFX, file holds a server certificate, intermediate certificates, and a private key in one encrypted file. Enter the Passphrase value for decryption. |
|
Step 7 |
Click Continue. |
|
Step 8 |
In the Advanced Options step, you can configure the following: In the Revocation tab, you can configure the following:
Click the Others tab:
|
|
Step 9 |
Click Add. |
Create a Self-Signed Identity Certificate Object
This procedure describes steps for generating a self-signed certificate for your ASA by entering the appropriate certificate field values in a wizard. You can generate as many self-signed certificates as you want.
To create a Self-Signed identity certificate object, perform these steps:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an Object Name for the certificate. The name is used in the configuration as an object name only; it does not become part of the certificate itself. |
|
Step 4 |
In the Identity Certificate step, select Identity Certificate. |
|
Step 5 |
In the Import Type step, select New to upload the certificate file and click Continue. |
|
Step 6 |
In the Enrollment step, select Self-Signed and click Continue. The Certificates Content step appears. Read Self-Signed and CSR Certificate Generation Based on Certificate Contents to understand the CN and SANS content in the Self-Signed certificate that is being generated. |
|
Step 7 |
In the Certificate Contents step, configure the following:
|
|
Step 8 |
In the Advanced Options step, you can configure the following: In the Revocation tab, you can configure the following:
Click the Others tab:
|
|
Step 9 |
Click Add. |
Add an Identity Certificate Object for Certificate Signing Request (CSR)
The Certification Authority (CA) server information and enrollment parameters are required to generate Certificate Signing Requests (CSRs) and obtain Identity Certificates from the specified CA. You need to select either Rivest-Shamir-Adleman (RSA) or Elliptic Curve Digital Signature Algorithm (ECDSA) key type to generate the request.
Create a trustpoint object by providing identification information and optionally uploading a CA certificate obtained from a CA.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click |
||
|
Step 3 |
Enter an Object Name for the certificate. The name is used in the configuration as an object name only; it does not become part of the certificate itself. |
||
|
Step 4 |
In the Identity Certificate step, select Identity Certificate. |
||
|
Step 5 |
In the Import Type step, select New to upload the certificate file and click Continue. |
||
|
Step 6 |
In the Enrollment step, select Manual. |
||
|
Step 7 |
(optional) You can paste or upload the CA certificate obtained from your CA. You can leave the field empty. |
||
|
Step 8 |
Click Continue. The Certificates Content step appears. Read Self-Signed and CSR Certificate Generation Based on Certificate Contents to understand the CN and SANS content in the Signed certificate that is being generated. |
||
|
Step 9 |
In the Certificate Contents step, configure the following:
|
||
|
Step 10 |
In the Advanced Options step, you can configure the following: In the Revocation tab, you can configure the following:
Click the Others tab:
|
||
|
Step 11 |
Click Add. This creates a trustpoint certificate object. |
Add a Trusted CA Certificate Object
Obtain a trusted CA certificate from an external certificate authority, or create one using your own internal CA, for example, with OpenSSL tools. You can upload a file encoded in one of the following supported formats:
-
Distinguished Encoding Rules (DER)
-
Privacy-enhanced Electronic Mail (PEM)
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an Object Name for the certificate. The name is used in the configuration as an object name only; it does not become part of the certificate itself. |
|
Step 4 |
In the Certificate Type step, select Trusted CA Certificate. |
|
Step 5 |
In the Certificate Contents step, paste the certificate contents in the text box or upload the CA certificate file as explained in the wizard. |
|
Step 6 |
Click Continue. The wizard advances to step 4. The certificate must follow these guidelines:
|
|
Step 7 |
In the Advanced Options step, you can configure the following: In the Revocation tab, you can configure the following:
Click the Others tab:
|
|
Step 8 |
Click Add. This creates a trustpoint certificate object. |
Self-Signed and CSR Certificate Generation Based on Certificate Contents
You need to have an idea of the CN and SANS content in the Self-Signed and CSR certificates. The content is based on the parameters you specify during their creation. You need to configure the parameters precisely for the AnyConnect clients to connect to the intended VPN headends of your organization.
This section provides different use cases with examples to give you an idea of the content of Self-Signed and CSR certificates based on the parameters specified.
Usecase 1: Different CN and FQDN values
Example:
-
Common Name (CN): mywebsite.com
-
FQDN: mysan.com
|
Common Name |
unstructuredName |
SANS |
|
|---|---|---|---|
|
Self-Signed |
mywebsite.com |
mysan.com |
mysan.com |
|
CSR |
mywebsite.com |
mysan.com |
- |
Usecase 2: FQDN field set to None
Example:
-
Common Name (CN): mywebsite.com
-
FQDN: None
|
Common Name |
SANS |
|
|---|---|---|
|
Self-Signed |
Host Name |
- |
|
CSR |
mywebsite.com |
- |
Usecase 3: No FQDN (Default FQDN)
Example:
-
Common Name (CN): mywebsite.com
|
Common Name |
unstructuredName |
SANS |
|
|---|---|---|---|
|
Self-Signed |
mywebsite.com |
Host Name |
- |
|
CSR |
mywebsite.com |
Host Name |
Host Name |
Usecase 4: IP Address is specified in FQDN
Example:
-
Common Name (CN): mywebsite.com
-
FQDN: 4.5.6.7
|
Common Name |
unstructuredName |
SANS |
|
|---|---|---|---|
|
Self-Signed |
mywebsite.com |
4.5.6.7 |
- |
|
CSR |
mywebsite.com |
4.5.6.7 |
4.5.6.7 |
Usecase 5: IP Address is Specified
Example:
-
IP Address: 4.5.6.7
-
Common Name (CN): mywebsite.com
-
FQDN: fqdn.com
|
Common Name |
unstructuredAddress |
unstructuredName |
SANS |
|
|---|---|---|---|---|
|
Self-Signed |
mywebsite.com |
4.5.6.7 |
fqdn.com |
- |
|
CSR |
mywebsite.com |
4.5.6.7 |
fqdn.com |
fqdn.com |
Usecase 6: Serial Number Check box is Selected
Example:
-
Serial Number: 9AQXMWOKDT9
|
serialNumber |
SANS |
|
|---|---|---|
|
Self-Signed |
9AQXMWOKDT9 |
- |
|
CSR |
9AQXMWOKDT9 |
fqdn.com |
Usecase 7: Email Address is Specified
Example:
-
EA: abc@xyz.com
|
unstructredName |
emailAddress |
SANS |
|
|---|---|---|---|
|
Self-Signed |
Host Name |
abc@xyz.com |
Host Name |
|
CSR |
Host Name |
abc@xyz.com |
- |
About IPsec Proposals
IPsec is one of the most secure methods for setting up a VPN. IPsec provides data encryption at the IP packet level, offering a robust security solution that is standards-based. With IPsec, data is transmitted over a public network through tunnels. A tunnel is a secure, logical communication path between two peers. Traffic that enters an IPsec tunnel is secured by a combination of security protocols and algorithms called a transform set. During the IPsec security association (SA) negotiation, peers search for a transform set that is the same at both peers.
There are separate IPsec proposal objects based on the IKE version, IKEv1, or IKEv2:
-
When you create an IKEv1 IPsec proposal, you select the mode in which IPsec operates, and define the required encryption and authentication types. You can select single options for the algorithms. If you want to support multiple combinations in a VPN, create and select multiple IKEv1 IPsec Proposal objects.
-
When you create an IKEv2 IPsec proposal, you can select all of the encryption and hash algorithms allowed in a VPN. The system orders the settings from the most secure to the least secure and negotiates with the peer until a match is found. This allows you to potentially send a single proposal to convey all the allowed combinations instead of the need to send each allowed combination individually as with IKEv1.
The Encapsulating Security Protocol (ESP) is used for both IKEv1 and IKEv2 IPsec proposals. It provides authentication, encryption, and antireplay services. ESP is IP protocol type 50.
 Note |
We recommend using both encryption and authentication on IPsec tunnels. |
Managing an IKEv1 IPsec Proposal Object
IPsec Proposal objects configure the IPsec proposal used during IKE Phase 2 negotiations. The IPsec proposal defines the combination of security protocols and algorithms that secure traffic in an IPsec tunnel. There are separate objects for IKEv1 and IKEv2. Currently, Security Cloud Control supports IKEv1 IPsec proposal objects.
The Encapsulating Security Protocol (ESP) is used for both IKEv1 and IKEv2 IPsec proposals. It provides authentication, encryption, and anti-replay services. ESP is IP protocol type 50.
 Note |
We recommend using both encryption and authentication on IPsec tunnels. |
Create or Edit an IKEv1 IPsec Proposal Object
There are several pre-defined IKEv1 IPsec proposals. You can also create new proposals to implement other combinations of security settings. You cannot edit or delete system-defined objects.
This procedure explains how you can create and edit objects directly through the Objects page. You can also create IKEv1 IPsec Proposals objects while editing the IKEv1 IPsec settings in a Site-to-Site VPN connection by clicking the Create New IKEv1 Proposal link shown in the object list.
Procedure
|
Step 1 |
From the left pane, click Manage > Objects. |
|
Step 2 |
Do one of these things:
|
|
Step 3 |
Enter an object name for the new object. |
|
Step 4 |
Select the Mode in which the IKEv1 IPsec Proposal object operates.
|
|
Step 5 |
Select the ESP Encryption (Encapsulating Security Protocol encryption) algorithm for this proposal. For an explanation of the options, see Deciding Which Encryption Algorithm to Use. |
|
Step 6 |
Select the ESP Hash or integrity algorithm to use for authentication. For an explanation of the options, see Deciding Which Hash Algorithms to Use. |
|
Step 7 |
Click Add. |
Managing an IKEv2 IPsec Proposal Object
IPsec Proposal objects configure the IPsec proposal used during IKE Phase 2 negotiations. The IPsec proposal defines the combination of security protocols and algorithms that secure traffic in an IPsec tunnel.
When you create an IKEv2 IPsec proposal, you can select all of the encryption and hash algorithms allowed in a VPN. The system orders the settings from the most secure to the least secure and negotiates with the peer until a match is found. This allows you to potentially send a single proposal to convey all the allowed combinations instead of the need to send each allowed combination individually as with IKEv1.
Create or Edit an IKEv2 IPsec Proposal Object
There are several pre-defined IKEv2 IPsec proposals. You can also create new proposals to implement other combinations of security settings. You cannot edit or delete system-defined objects.
The following procedure explains how you can create and edit objects directly through the Objects page. You can also create IKEv2 IPsec Proposals objects while editing the IKEv2 IPsec settings in a VPN connection by clicking the Create New IPsec Proposal link shown in the object list.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Do one of these things:
|
|
Step 3 |
Enter an object name for the new object. |
|
Step 4 |
Configure the IKE2 IPsec proposal objects:
|
|
Step 5 |
Click Add. |
About Global IKE Policies
Internet Key Exchange (IKE) is a key management protocol that is used to authenticate IPsec peers, negotiate and distribute IPsec encryption keys, and automatically establish IPsec security associations (SAs).
The IKE negotiation comprises two phases. Phase 1 negotiates a security association between two IKE peers, which enables the peers to communicate securely in Phase 2. During Phase 2 negotiation, IKE establishes SAs for other applications, such as IPsec. Both phases use proposals when they negotiate a connection. An IKE proposal is a set of algorithms that two peers use to secure the negotiation between them. IKE negotiation begins by each peer agreeing on a common (shared) IKE policy. This policy states which security parameters are used to protect subsequent IKE negotiations.
IKE policy objects define the IKE proposals for these negotiations. The objects that you enable are the ones used when the peers negotiate a VPN connection: you cannot specify different IKE policies per connection. The relative priority of each object determines which of these policies are tried first, with the lower number being a higher priority. The connection is not established if the negotiation fails to find a policy that both peers can support.
To define the global IKE policy, you select which objects to enable for each IKE version. If the pre-defined objects do not satisfy your requirements, create new policies to enforce your security policy.
Managing IKEv1 Policies
About IKEv1 Policy
Internet Key Exchange (IKE) version 1 policy objects contain the parameters required for IKEv1 policies when defining VPN connections. IKE is a key management protocol that facilitates the management of IPsec-based communications. It is used to authenticate IPsec peers, negotiate and distribute IPsec encryption keys, and automatically establish IPsec security associations (SAs).
There are several pre-defined IKEv1 policies. If any suit your needs, simply enable them by clicking the State toggle. You can also create new policies to implement other combinations of security settings. You cannot edit or delete system-defined objects.
Create or Edit an IKEv1 Policy
The following procedure explains how you can create and edit objects directly through the Objects page. You can also create an IKEv1 policy while editing the IKE settings in a Site-to-Site VPN connection by clicking the Create New IKEv1 Policy link shown in the object list.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Do one of these things:
|
|
Step 3 |
Enter an object name, up to 128 characters. |
|
Step 4 |
Configure the IKEv1 properties.
|
|
Step 5 |
Click Add. |
Managing IKEv2 Policies
About IKEv2 Policy
Internet Key Exchange (IKE) version 2 policy objects contain the parameters required for IKEv2 policies when defining VPN connections. IKE is a key management protocol that facilitates the management of IPsec-based communications. It is used to authenticate IPsec peers, negotiate and distribute IPsec encryption keys, and automatically establish IPsec security associations (SAs).
There are several pre-defined IKEv2 policies. If any suit your needs, simply enable them by clicking the State toggle. You can also create new policies to implement other combinations of security settings. You cannot edit or delete system-defined objects.
Create or Edit an IKEv2 Policy
The following procedure explains how you can create and edit objects directly through the Objects page. You can also create an IKEv2 policy while editing the IKE settings in a Site-to-Site VPN connection by clicking the Create New IKEv2 Policy link shown in the object list.
Procedure
|
Step 1 |
In the Security Cloud Control navigation bar on the left, click Manage > Objects. |
|
Step 2 |
Do one of these things:
|
|
Step 3 |
Enter an object name, up to 128 characters. |
|
Step 4 |
Configure the IKEv2 properties.
|
|
Step 5 |
Click Add. |
RA VPN Objects
Configure Identity Sources for FDM-Managed Device
Identity Sources, such as Microsoft AD realms and RADIUS Servers, are AAA servers and databases that define user accounts for the people in your organization. You can use this information in a variety of ways, such as providing the user identity associated with an IP address, or authenticating remote access VPN connections or access to Security Cloud Control.
Click Manage > Objects, then click  and choose to create your sources. You would then use these objects when you configure the services that require an identity source.
You can apply appropriate filters to search existing sources and manage them.
and choose to create your sources. You would then use these objects when you configure the services that require an identity source.
You can apply appropriate filters to search existing sources and manage them.
Active Directory Realms
Active Directory provides user account and authentication information. When you deploy a configuration that includes an AD realm to an FDM-managed device, Security Cloud Control fetches users and groups from the AD server.
You can use this source for the following purposes:
-
Remote Access VPN, as a primary identity source. You can use AD in conjunction with a RADIUS server.
-
Identity policy, for active authentication and as the user identity source used with passive authentication.
-
Identity rule, for active authentication for a user.
Security Cloud Control requests an updated list of user groups once every 24 hours. Because you can add a maximum of 50 users or groups to a rule, selecting groups usually makes more sense than selecting individual users. For example, you could create a rule allowing the Engineering group access to a development network, and create a subsequent rule that denies all other access to the network. Then, to make the rule apply to new engineers, you only need to add the engineer to the Engineering group in the directory server.
Active Directory Realms In Security Cloud Control
You configure the AD realm when you create an AD Identity object. The identity source objects wizard assists in determining how to connect to the AD server and where the AD server is located in the network.
 Note |
If you create an AD realm in Security Cloud Control, Security Cloud Control remembers the AD password when you create affiliate identity source objects and when you add those objects to an identity rule. |
Active Directory Realms In FDM
You can point to AD realm objects that were created in FDM from the Security Cloud Control objects wizard. Note that Security Cloud Control does not read the AD password for AD realm objects that are created in FDM. You must manually enter the correct AD password in Security Cloud Control.
To configure an AD realm in Firewall Device Managers, see the Configuring AD Identity Realms section of the Reusable Objects chapters of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager for the version your device is running.
Supported Directory Servers
You can use AD on Windows Server 2008 and 2012.
Note the following about your server configuration:
-
If you want to perform user control on user groups or on users within groups, you must configure user groups on the directory server. The system cannot perform user group control if the server organizes the users in a basic object hierarchy.
-
The directory server must use the field names listed in the following table in order for the system to retrieve user metadata from the servers for that field:
|
Metadata |
Active Directory Field |
|---|---|
| LDAP user name | samaccountname |
| First name | givename |
| Last Name | sn |
| email address |
userprincipalname (if mail has no value) |
| Department |
department distinguishedname (if department has no value) |
| Telephone number | telephonenumber |
Determining the Directory Base DN
When you configure directory properties, you need to specify the common base Distinguished Name (DN) for users and groups. The base is defined in your directory server and differs from network to network. You must enter the correct bases for identity policies to work. If the base is wrong, the system cannot determine user or group names, and thus identity-based policies will be inoperable.
 Note |
To get the correct bases, consult the administrator who is responsible for the directory servers. |
For an active directory, you can determine the correct bases by logging into the AD server as a domain administrator, and using the dsquery command at a command prompt as follows to determine the bases:
User search base
Enter the dsquery user command with known username (partial or complete) to determine the base distinguished name. For example, the following command uses the partial name "John*" to return information for all users that start with "John."
C:\Users\Administrator>dsquery user -name "John*"
"CN=John Doe,CN=Users,DC=csc-lab,DC=example,DC=com"
The base DN would be "DC=csc-lab,DC=example,DC=com."
Group search base
Enter the dsquery group command with a known group name to determine the base DN. For example, the following command uses the group name Employees to return the distinguished name:
C:\>dsquery group -name "Employees"
"CN=Employees,CN=Users,DC=csc-lab,DC=example,DC=com"
The group base DN would be "DC=csc-lab,DC=example,DC=com."
You can also use the ADSI Edit program to browse the AD structure (). In ADSI Edit, right click any object, such as an organizational unit (OU), group, or user, and choose Properties to view the distinguished name. You can then copy the string of DC values as the base.
To verify that you have the correct base:
Procedure
|
Step 1 |
Click the Test Connection button in the directory properties to verify connectivity. Resolve any problems, and save the directory properties. |
|
Step 2 |
Commit changes to the device. |
|
Step 3 |
Create an access rule, select the Users tab, and try to add known user and group names from the directory. You should see auto-complete suggestions as you type for matching users and groups in the realm that contains the directory. If these suggestions appear in a drop-down list, then the system was able to query the directory successfully. If you see no suggestions, and you are certain the string you typed should appear in a user or group name, you need to correct the corresponding search base. |
What to do next
See Create and Edit a Firepower Threat Defense Active Directory Realm Object for more information.
RADIUS Servers and Groups
You can use RADIUS servers to authenticate and authorize administration users.
When you configure a feature to use RADIUS servers, you select a RADIUS group instead of individual servers. A RADIUS group is a collection of RADIUS servers that are copies of each other. If a group has more than one server, they form a chain of backup servers to provide redundancy in case one server becomes unavailable. But even if you have only one server, you must create a one-member group to configure RADIUS support for a feature.
You can use this source for the following purposes:
-
Remote Access VPN, as an identity source for authentication, and for authorization and accounting. You can use AD in conjunction with a RADIUS server.
-
Identity policy, as a passive identity source to collect user identity from remote access VPN logins.
See Create and Edit a Firepower Threat Defense RADIUS Server Object or Group for more information.
Create or Edit an Active Directory Realm Object
About Active Directory Realm Objects
When you create or edit an identity source object such as an AD realm object, Security Cloud Control sends the configuration request to the FDM-managed devices through the SDC. The FDM-managed device then communicates with the configured AD realm.
Note that Security Cloud Control does not read the Directory Password for AD realms that are configured through the Firewall Device Manager console. If you use an AD realm object that was originally created in Firewall Device Manager, you must manually enter the Directory Password.
Create an FTD Active Directory Realm Object
Use the following procedure to create an object:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click |
||
|
Step 3 |
Enter an Object Name for the object. |
||
|
Step 4 |
Select the Device Type is as FTD. |
||
|
Step 5 |
In the first part of the wizard, select Active Directory Realm as the Identity Source Type. Click Continue. |
||
|
Step 6 |
Configure the basic realm properties.
|
||
|
Step 7 |
Configure the directory server properties.
|
||
|
Step 8 |
(Optional) Use the Test button to validate the configuration. |
||
|
Step 9 |
(Optional) Click Add another configuration to add multiple AD servers to the AD realm. The AD servers need to be duplicates of each other and support the same AD domain. Therefore, the basic realm properties such as Directory name, Directory Password, and Base Distinguished Name must be the same across all AD servers associated with that AD realm. |
||
|
Step 10 |
Click Add. |
||
|
Step 11 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Edit an FTD Active Directory Realm Object
Note that you cannot change the Identity Source Type when editing an Identity source object. You must create a new object with the correct type.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object you want to edit. |
|
Step 4 |
Click the edit icon |
|
Step 5 |
Edit the values in the dialog box in the same fashion that you created in the procedures above. Expand the configuration bar listed below to edit or test the hostname/IP address or encryption information. |
|
Step 6 |
Click Save. |
|
Step 7 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
|
Step 8 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Create or Edit a RADIUS Server Object or Group
About RADIUS Server Objects or Groups
When you create or edit an identity source object such as a RADIUS server object or a group of RADIUS server objects, Security Cloud Control sends the configuration request to the FDM-managed devices through the SDC. The FDM-managed device then communicates with the configured AD realm.
Create a RADIUS Server Object
RADIUS servers provide AAA (authentication, authorization, and accounting) services.
Use the following procedure to create an object:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an Object name for the object. |
|
Step 4 |
For the Device Type, select FTD. |
|
Step 5 |
For the Identity Source type, select RADIUS Server. Click Continue. |
|
Step 6 |
Edit the Identity Source configuration with the following properties:
|
|
Step 7 |
If you have Cisco Identity Services Engine (ISE) already configured for your network and are using the server for remote access VPN Change of Authorization configuration, click the RA VPN Only link and configure the following:
|
|
Step 8 |
Click Add. |
|
Step 9 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Create a RADIUS Server Group
A RADIUS server group contains one or more RADIUS server objects. The servers within a group must be copies of each other. These servers form a chain of backup servers, so that if the first server is unavailable, the system can try the next server in the list.
Use the following procedure to create an object group:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click |
||
|
Step 3 |
Enter an Object name for the object. |
||
|
Step 4 |
Select the Device Type as FTD. |
||
|
Step 5 |
Select RADIUS Server Group as the Identity Source Type. Click Continue. |
||
|
Step 6 |
Edit the Identity Source configuration with the following properties:
|
||
|
Step 7 |
Select an AD realm that supported the RADIUS server from the drop-down menu. If you have not already created an AD realm, click Create from inside the drop-down menu. |
||
|
Step 8 |
Click the Add button
|
||
|
Step 9 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Edit a Radius Server Object or Group
Use the following procedure to edit a Radius server object or Radius server group:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object you want to edit. |
|
Step 4 |
Click the edit icon |
|
Step 5 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. To edit or test the hostname/IP address or encryption information, expand the configuration bar. |
|
Step 6 |
Click Save. |
|
Step 7 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
|
Step 8 |
Review and Deploy now the changes you made, or wait and deploy multiple changes at once. |
Security Zone Object
A security zone is a grouping of interfaces. Zones divide the network into segments to help you manage and classify traffic. You can define multiple zones, but a given interface can be in one zone only.
The Firepower system creates the following zones during initial configuration and they are displayed in Security Cloud Control's object page. You can edit zones to add or remove interfaces, or you can delete the zones if you no longer use them.
-
inside_zone-Includes the inside interface. This zone is intended to represent internal networks.
-
outside_zone-Includes the outside interface. This zone is intended to represent networks external to your control, such as the internet.
Typically, you would group interfaces by the role they play in your network. For example, you would place the interface that connects to the internet in the outside_zone security zone, and all of the interfaces for your internal networks in the inside_zone security zone. Then, you could apply access control rules to traffic coming from the outside zone and going to the inside zone.
Before creating zones, consider the access rules and other policies you want to apply to your networks. For example, you do not need to put all internal interfaces into the same zone. If you have 4 internal networks, and you want to treat one differently than the other three, you can create two zones rather than one. If you have an interface that should allow outside access to a public web server, you might want to use a separate zone for the interface.
Create or Edit a Firepower Security Zone Object
A security zone is a grouping of interfaces. Zones divide the network into segments to help you manage and classify traffic. You can define multiple zones, but a given interface can be in one zone only.
A security zone object is not associated with a device unless it is used in a rule for that device.
Create a Security Zone Object
To create a security zone object, follow these instructions:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click to create the object. |
|
Step 3 |
Give the object a name and, optionally, a description. |
|
Step 4 |
Select the interfaces to put in the security zone. |
|
Step 5 |
Click Add. |
Edit a Security Zone Object
After onboarding an FDM-managed device, you will find there are already at least two security zones, one is the inside_zone and the other is the outside_zone. These zones can be edited or deleted. To edit any security zone object, follow these instructions:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Find the object you want to edit:
|
||
|
Step 3 |
Select the object. |
||
|
Step 4 |
Click the Edit icon |
||
|
Step 5 |
After editing any of the attributes of the object. Click Save. |
||
|
Step 6 |
After clicking Save you receive a message explaining how these changes will affect other devices. Click Confirm to save the changes or Cancel. |
Service Objects
ASA Service Objects
ASA service objects, service groups, and port groups are reusable components that contain protocols or ports considered part of the IP protocol suite. In a service object you can specify a single protocol and assign it to a source port, destination port, or both source and destination ports. A service group contains many service objects and can include a mix of protocols.
A port group is a kind of ASA service object. Port groups contain port objects that pair a service type, such as TCP or UDP, and a port number or a range of port numbers. You can then use the objects in security policies for the purposes of defining traffic matching criteria. For example, you can use them in access control rules to allow traffic to a specific range of TCP ports.
See Create and Edit ASA Service Objects for more information.
Firepower Service Objects
FTD service objects, service groups, and port groups are reusable components that contain protocols or ports considered part of the IP protocol suite.
FTD service groups are collections of service objects. A service group may contain objects for one or more protocols. You can use the objects and groups in security policies for purposes of defining network traffic matching criteria, for example, to use access rules to allow traffic to specific TCP ports. The system includes several pre-defined objects for common services. You can use these objects in your policies; however, you cannot edit or delete system-defined objects.
Firepower Device Manager and Firepower Management Center refer to service objects as port objects and service groups and port groups.
See Create and Edit Firepower Threat Defense Service Objects for more information.
Protocol Objects
Protocol objects are a type of service object that contain less-commonly used or legacy protocols. Protocol objects are identified by a name and protocol number. Security Cloud Control recognizes these objects in ASA and Firepower (FDM-managed device) configurations and gives them their own filter of "Protocols" so you can find them easily.
See Create and Edit Firepower Threat Defense Service Objects for more information.
ICMP Objects
An Internet Control Message Protocol (ICMP) object is a service object specifically for ICMP and IPv6-ICMP messages. Security Cloud Control recognizes these objects in ASA and Firepower configurations when those devices are onboarded and Security Cloud Control gives them their own filter of "ICMP" so you can find the objects easily.
Using Security Cloud Control, you can rename or remove ICMP objects from an ASA configuration. You can use Security Cloud Control to create, update, and delete ICMP and ICMPv6 objects in a Firepower configuration.
 Note |
For the ICMPv6 protocol, AWS does not support choosing specific arguments. Only rules that allow all ICMPv6 messages are supported. See Create and Edit Firepower Threat Defense Service Objects for more information. |
Create and Edit ASA Service Objects
In a service object, you can specify a single protocol and assign it to a source port, destination port, or both source and destination ports.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name. |
|
Step 4 |
Select Create a service object |
|
Step 5 |
Click the Service Type button and select the protocol for which you want to make an object.
|
|
Step 6 |
Click Add. |
Examples
-
A service object that identifies incoming FTP traffic would be one with a TCP Service type and a destination port range of 21.
-
A service object that identifies outgoing DNS and DNS over TCP traffic would be one with a tcp-udb service type and a source port equal to 53.
Create an ASA Service Group
A service group can be made up of one or more service objects representing one or more protocols.
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name. |
|
Step 4 |
Select Create a service group. |
|
Step 5 |
Add an existing object by clicking Add Object, selecting an object, and clicking Select. Repeat this step to add more objects. |
|
Step 6 |
If needed, add an extra individual service type value to the service group
|
|
Step 7 |
To add more individual port values, click Add Another Value and repeat step 6. |
|
Step 8 |
Click Add when you are done adding service objects and service values to the service group. |
Edit an ASA Service Object or Service Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Filter the objects to find the object you want to edit and then select the object in the object table. |
|
Step 3 |
In the details pane, click edit |
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 5 |
Click Save. |
|
Step 6 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
Create and Edit Firepower Service Objects
To create a firepower service object, follow these steps:
Firewall Device Manager (FDM-managed) service objects are reusable components that specify a TCP/IP protocol and a port. The Firewall Device Manager, On-Premises Firewall Management Center and Cloud-Delivered Firewall Management Center refer to these objects as "Port Objects."
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name and description. |
|
Step 4 |
Select Create a service object. |
|
Step 5 |
Click the Service Type button and select the protocol for which you want to create an object. |
|
Step 6 |
Configure the protocol as follows:
|
|
Step 7 |
Click Add. |
|
Step 8 |
Review and deploy the changes you made now, or wait and deploy multiple changes at once. |
Create a Firepower Service Group
A service group can be made up of one or more service objects representing one or more protocols. The service objects need to be created before they can be added to the group. The Firepower Device Manager and Firepower Management Center refer to these objects as "Port Objects."
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click . |
|
Step 3 |
Enter an object name and description. |
|
Step 4 |
Select Create a service group. |
|
Step 5 |
Add an object to the group by clicking Add Object.
|
|
Step 6 |
Click Add when you are done adding service objects to the service group. |
|
Step 7 |
Review and deploy the changes you made now, or wait and deploy multiple changes at once. |
Edit a Firepower Service Object or Service Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Filter the objects to find the object you want to edit and then select the object in the object table. |
|
Step 3 |
In the Actions pane, click Edit
|
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 5 |
Click Save. |
|
Step 6 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
|
Step 7 |
Review and deploy the changes you made now, or wait and deploy multiple changes at once. |
Security Group Tag Group
Security Group Tags
About Security Group Tags
If you use Cisco Identity Services Engine (ISE) to define and use security group tag (SGT) for classifying traffic in a Cisco TrustSec network, you can write access control rules that use SGT as matching criteria. Thus, you can block or allow access based on security group membership rather than IP addresses.
In ISE, you can create a SGT and assign host or network IP addresses to each tag. If you assign an SGT to a user's account, the SGT is assigned to the user's traffic. After you configure FDM-managed device to connect to an ISE server and create the SGT, you can create SGT groups in Security Cloud Control and build access control rules around them. Note that you must configure ISE's SGT Exchange Protocol (SXP) mapping before you can associate an SGT to an FDM-managed device. See Security Group Tag Exchange Protocol in the Cisco Identity Services Engine Administrator Guide of the version you are currently running for more information.
When an FDM-managed device evaluates SGT as a traffic matching criteria for an access control rule, it uses the following priority:
-
The source SGT defined in the packet, if any. No destination matching is done using this technique. For the SGT to be in the packet, the switches and routers in the network must be configured to add them. See the ISE documentation for information on how to implement this method.
-
The SGT assigned to the user session, as downloaded from the ISE session directory. You need to enable the option to listen to session directory information for this kind of SGT matching, but this option is on by default when you first create the ISE identity source. The SGT can be matched to source or destination. Although not required, you would also normally set up a passive authentication identity rule, using the ISE identity source along with an AD realm, to collect user identity information.
-
The SGT-to-IP address mapping downloaded using SXP. If the IP address is within the range for an SGT, then the traffic matches the access control rule that uses the SGT. The SGT can be matched to source or destination.

Note
You cannot use the information retrieved from ISE directly in an access control rule. Instead, you need to create SGT groups, which refer to the downloaded SGT information. Your SGT groups can refer to more than one SGT, so you can apply policy based on a relevant collections of tags if that is appropriate.
Version Support
Security Cloud Control currently supports SGT and SGT groups on FDM-managed devices running Version 6.5 and later. an FDM-managed device allows you to configure and connect to an ISE server in Version 6.5 and later but not does not support SGT configuration in the UI until Version 6.7.
From the FDM-managed UI, this means that an FDM-managed device running Version 6.5 or later can download SXP mappings of SGTs but cannot be manually added to objects or access control rules. To make changes to the SGTs for devices running Version 6.5 or Version 6.6, you must use the ISE UI. If the device running Version 6.5 is onboarded to Security Cloud Control, however, you can see the current SGTs associated with the device and create SGT groups.
SGT in Security Cloud Control
Security Group Tags
SGTs are read-only in Security Cloud Control. You cannot create or edit an SGT in Security Cloud Control. To create an SGT, see the Cisco Identity Services Engine Administrator Guide of the version your are currently running.
SGT Groups
 Note |
An FDM-managed device refers to groups of SGTs as SGT dynamic objects. In Security Cloud Control, these lists of tags are currently called SGT groups. You can create an SGT group in Security Cloud Control without referring to the FDM-managed device or ISE UI. |
Use SGT groups to identify source or destination addresses based on an SGT assigned by ISE. You can then use the objects in access control rules for purposes of defining traffic matching criteria. You cannot use the information retrieved from ISE directly in an access control rule. Instead, you need to create SGT groups, which refer to the downloaded SGT information.
Your SGT groups can refer to more than one SGT, so you can apply policy based on relevant collections of tags if that is appropriate.
In order to create an SGT group in Security Cloud Control, you must have at least one SGT already configured and SGT mappings from an ISE server configured for the FDM-managed console of the device you want to use. Note that if more than one FDM-managed device is associated with the same ISE server, an SGT or SGT group can be applied to more than one device. If a device is not associated with an ISE server, you cannot include SGT objects in your access control rule, or apply an SGT group to that device configuration.
SGT Groups in Rules
SGT groups can be added to access control rules; they appear as source or destination network objects.
You can create an SGT group from the Objects page. See Create an SGT Group for more information.
Create an SGT Group
To create an SGT group that can be used for an access control rule, use the following procedure:
Before you begin
You must have the following configurations or environments configured prior to creating a security group tag (SGT) group:
-
FDM-managed device must be running at least Version 6.5.
-
You must configure the ISE identity source to subscribe to SXP mappings and enable deploy changes. To manage SXP mappings, see Configure Security Groups and SXP Publishing in ISE of the Firepower Device Manager Configuration Guide for the version you're using, Version 6.7 and later.
-
All SGTs must be created in ISE. To create an SGT, see the Cisco Identity Services Engine Configuration Guide of the version your are currently running.
Edit an SGT Group
To edit an SGT group, use the following procedure:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Locate the SGT group you want to edit by using object filters and search field. |
||
|
Step 3 |
Select the SGT group and click the edit icon |
||
|
Step 4 |
Modify the SGT group. Edit the name, description, or the SGTs associated with the group. |
||
|
Step 5 |
Click Save.
|
Add an SGT Group to an Access Control Rule
To add an SGT group to an access control rule, use the following procedure:
Procedure
|
Step 1 |
In the left pane, click Inventory. |
||
|
Step 2 |
In the left pane, click . |
||
|
Step 3 |
Click the Devices tab to locate the device or the Templates tab to locate the model device. |
||
|
Step 4 |
Click the FTD tab and select the device you want to add the SGT group to. |
||
|
Step 5 |
In theManagement pane, select Policy. |
||
|
Step 6 |
Click the blue plus button |
||
|
Step 7 |
Locate the SGT group(s) you want to edit by using object filters and search field. |
||
|
Step 8 |
Click Save. |
||
|
Step 9 |
Preview and Deploy Configuration Changes for All Devices.
|
Syslog Server Objects
FDM-managed devices have a limited capacity to store events. To maximize storage for events, you can configure an external server. A system log (syslog) server object identifies a server that can receive connection-oriented or diagnostic syslog messages. If you have a syslog server set up for log collection and analysis, you can use the Security Cloud Control to create objects to define them and use the objects in the related policies.
Create and Edit Syslog Server Objects
To create a new syslog server object, follow these steps:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click the Create Object button |
|
Step 3 |
Select Syslog Server under FDM-managed device object types |
|
Step 4 |
Configure the syslog server object properties:
|
|
Step 5 |
Click Add. |
|
Step 6 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Edit Syslog Server Objects
To edit an existing syslog server object, follow these steps:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the desired syslog server object and select it. You can filter |
|
Step 3 |
In the Actions pane, click Edit. |
|
Step 4 |
Make the desired edits and click Save. |
|
Step 5 |
Confirm the changes you made. |
|
Step 6 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Create a Syslog Server Object for Secure Logging Analytics (SaaS)
Create a syslog server object with the IP address, TCP port, or UDP port of the Secure Event Connector (SEC) you want to send events to. You would create one syslog object for every SEC that you have onboarded to your tenant but you would only send events from one rule to one syslog object representing one SEC.
Procedure
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click the Create Object button |
||
|
Step 3 |
Select Syslog Server under FDM-managed device object types. |
||
|
Step 4 |
Configure the syslog server object properties. To find these properties of the SEC, from the navigation pane on the left, choose . Then select the Secure Event Connector you want to configure the syslog object for and look in the Details pane on the right.
|
||
|
Step 5 |
Click Add. |
ASA Time Range Objects
What is a Time Range Object?
A time range object defines a specific time consisting of a start time, an end time, and optional recurring entries. You use these objects in network policies to provide time-based access to certain features or assets. For example, you could create an access rule that allows access to a particular server during working hours only. Creating a time range does not restrict access to the device. Note that the times configured for these objects are local to the device.
You can add an absolute or recurring time ranges to this object. Recurring ranges are considered to be periodic time ranges.
 Note |
If a time range has both absolute and periodic values specified, then the periodic values are evaluated only after the absolute start time is reached and they are not further evaluated after the absolute end time is reached. |
Create an ASA Time Range Object
Use the following procedure to create a time range object for an ASA device:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click . |
||
|
Step 3 |
Enter an object name. |
||
|
Step 4 |
Define a time range.
|
||
|
Step 5 |
Click Add to create the object. |
Edit an ASA Time Range Object
Use the following procedure to edit a time range object for an ASA device:
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Filter the objects to find the object you want to edit and then select the object in the object table. |
|
Step 3 |
In the details pane, click edit |
|
Step 4 |
Edit the values as needed and click Save. |
|
Step 5 |
If the object is currently used by any policies, Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
|
Step 6 |
If the object is used in a policy on a device, review and deploy now the changes you made, or wait and deploy multiple changes at once. |
 .
.
 .
.
 to create an object.
to create an object.
 in the
in the  arrow in
arrow in  arrow in
arrow in  appearing beside the object name or network group to modify them.
appearing beside the object name or network group to modify them.

 Feedback
Feedback