Feature history for IGMP
This table provides release and platform support information for the features explained in this module.
These features are available in all the releases subsequent to the one they were introduced in, unless noted otherwise.
|
Release |
Feature name and description |
Supported platform |
|---|---|---|
|
Cisco IOS XE 17.18.1 |
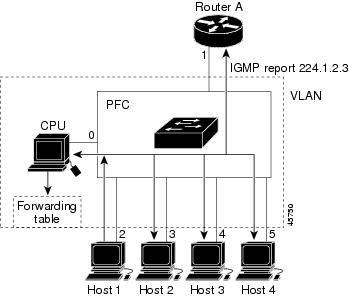
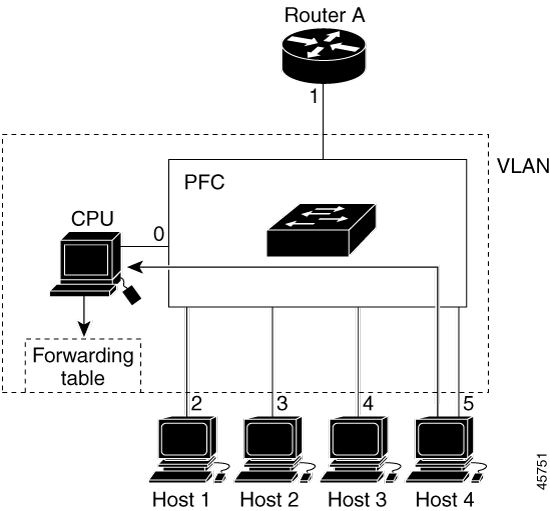
IGMP: IGMP is a communication protocol used between hosts on a LAN and network devices to monitor IP multicast group memberships. |
Cisco C9350 Series Smart Switches Cisco C9610 Series Smart Switches |


 Feedback
Feedback