- Auto Anchor SSID between Wireless LAN Controllers acting as MC
- Enabling Central Web Authentication on ISE
- Configuring Auto Anchor and Mobility Groups on Wireless Services
- Configuring Wireless Multicast on Wireless LAN Controllers
- Converged Access Consolidated Quick Reference Templates for Wireless LAN
- Converged Access Controller AP Join Issue Troubleshoot with Traces
- Converged Access Controllers MAC Address Entry for Network Mobility Service Protocol
- Configuration Example: Converged Access Management through Prime Infrastructure with SNMP v2 and v3
- Converged Access Path Maximum Transmission Unit Discovery
- Third-Party Certificate Installation on Converged Access Wireless LAN Controllers
- Configuration Example: Converged Access for WLC EAP-FAST with Internal RADIUS Server
- Converged Access and WLC Local EAP Authentication Configuration Example
- Configuration Example: Custom Web Authentication with Local Authentication
- Dynamic VLAN Assignment with Converged Access and ACS 5.2 Configuration Example
- Configuration Example: External RADIUS Server EAP Authentication
- External Web Authentication on Converged Access
- Installing Wireless Services
- Local Web Authentication with External RADIUS Authentication
- Local Web Authentication on Converged Access
- PEAP Authentication with Microsoft NPS Configuration
- QoS on Converged Access Controllers and Lightweight Access Points
- Configuration Example: TACACS Administrator Access to Converged Access Wireless LAN Controllers
- Configuration Example: Unified Access WLC Guest Anchor with Converged Access
- VideoStream Troubleshooting
- Custom Web Authentication Locally Hosted on WLC or an External Server
- Wireless Converged Access Chromecast Configuration Example
- Web Passthrough Configuration Example
- Configuration Examples: WPA2-PSK and Open Authentication
Converged Access and WLC Local EAP Authentication Configuration Example
This document describes how to configure the Cisco Catalyst 3850 Series Switch for Local Extensible Authentication Protocol (EAP) to authenticate the wireless network users. The authentication method used in this document is PEAP-MSChapv2, which is one of the most-common method available in the supplicants.
- Prerequisites
- WLC Local EAP Authentication
- Configuring Local EAP authentication
- Verifying the Local EAP Authentication Configuration
- Troubleshooting the Local EAP Authentication configuring issues
- Debugs for dot1x and EAP
Prerequisites
We recommend that you have basic and functional knowledge on the following topics:
-
WLC and Lightweight Access Points (LAPs).
-
Authentication, Authorization, and Accounting (AAA) server.
-
Wireless networks and wireless security issues.
 Note | The information in this document is written by assuming, wireless access points have already joined the Cisco Catalyst 3850 Series Switch and supplicant is properly configured for the authentication methods that are used. |
Supported Platforms and Releases
The information in this document is based on the following:
-
Code used for GUI Cisco Catalyst 3850 Series Switch is 03.02.02.SE.150-1.EX2 (This is valid on June 25, 2013).
-
Access Point (AP) used is AP1142N.
-
Supplicant used is Microsoft (MS) Windows 7 Enterprise with a wireless card TP-Link n600 Dual Band USB Adapter and Cisco Anyconnect Version 3.1.
 Note | The information in this document is created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. |
WLC Local EAP Authentication
Local EAP is an authentication method that allows user and wireless client authentication locally on the controller. When you enable local EAP, the controller serves as the authentication server and the local user database, hence it removes dependence on an external authentication server. Local EAP retrieves user credentials from the local user database.
To view the methods that local EAP supports for authentication between the controller and wireless client, enter the following command:
Device(config-eap-profile)# method ? fast EAP-FAST method allowed gtc EAP-GTC method allowed leap EAP-LEAP method allowed md5 EAP-MD5 method allowed mschapv2 EAP-MSCHAPV2 method allowed peap EAP-PEAP method allowed tls EAP-TLS method allowed
Configuring Local EAP authentication
Network Diagram of LAP and WLC
The following figure represents the network diagram of LAP and WLC connected to a wireless client.
Configuring Local EAP Authentication
Perform the following tasks in order to configure local EAP authentication:
-
Create a test user, by entering following command:
user-name test privilege 15 password 0 cisco type network-user description pass=cisco
-
To enable the authentication, authorization, and accounting (AAA) access control model, enter the following command:
aaa new-model
-
Define the authentication and authorization for AAA as shown in the following figure:
Figure 2. Flow of authentication and authorization for AAA 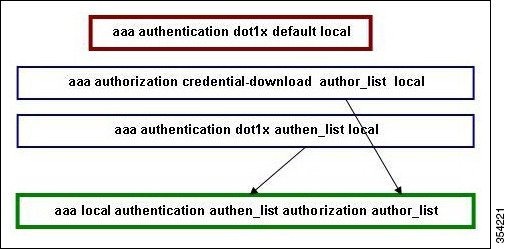
-
To terminate EAP sessions locally, enter the following command;
aaa authentication dot1x default local
-
To prepare a method list for the credential download, enter the following command;
aaa authorization credential-download author_list local

Note
In this example, the local is configured in the method list author_list. This method list is one of the parameters for the aaa local authentication authen_list authorization author_list CLI command.
-
Enter the following CLI command in order to define an authentication method list, which is used by the local EAP for verification of the credentials when the EAP requests local EAP with the EAP_VERIFY_PASSWORD_EVENT event:
aaa authentication dot1x authen_list local

Note
This method list name is the parameter for the aaa local authentication authen_list authorization author_list CLI command.
-
Specify where the local EAP must be downloaded or verify the credentials:
aaa local authentication authen_list authorization author_list

Note
Define the authen_list and author_list before downloading local EAP; refer to steps a and b for more information on how to prepare and define the method list.
-
-
Begin the dot1x process by entering following command:
dot1x system-auth-control
-
To define the supported authentication methods, create the EAP profile (For example, PEAP-MSchapv2).
eap profile PEAPProfile method peap method mschapv2
-
Use the EAP profile to configure the Service Set Identifier (SSID).
wlan TiagoNGWC 1 TiagoNGWC client vlan VLAN0080 ip dhcp server 192.168.80.14 local-auth PEAPProfile
-
Set up the DHCP pool and the Switch Virtual Interface (SVI) for the client VLAN. In the following example set up is completed on Converged Access with use of VLAN80:
ip dhcp excluded-address 192.168.80.1 192.168.80.99 ! ip dhcp pool VLAN80 network 192.168.80.0 255.255.255.0 default-router 192.168.80.14 interface Vlan80 ip address 192.168.80.14 255.255.255.0
Verifying the Local EAP Authentication Configuration
Perform the following task in order to verify your configuration:
Device# show wlan name TiagoNGWC
WLAN Profile Name : TiagoNGWC
================================================
Identifier : 1
Network Name (SSID) : TiagoNGWC
Status : Enabled
Broadcast SSID : Enabled
Maximum number of Associated Clients : 0
AAA Policy Override : Disabled
Network Admission Control
NAC-State : Disabled
Number of Active Clients : 1
Exclusionlist Timeout : 60
Session Timeout : 1800 seconds
CHD per WLAN : Enabled
Webauth DHCP exclusion : Disabled
Interface : VLAN0080
Interface Status : Up
Multicast Interface : Unconfigured
WLAN IPv4 ACL : unconfigured
WLAN IPv6 ACL : unconfigured
DHCP Server : 192.168.80.14
DHCP Address Assignment Required : Disabled
DHCP Option 82 : Disabled
DHCP Option 82 Format : ap-mac
DHCP Option 82 Ascii Mode : Disabled
DHCP Option 82 Rid Mode : Disabled
QoS Service Policy - Input
Policy Name : unknown
Policy State : None
QoS Service Policy - Output
Policy Name : unknown
Policy State : None
QoS Client Service Policy
Input Policy Name : unknown
Output Policy Name : unknown
WMM : Allowed
Channel Scan Defer Priority:
Priority (default) : 4
Priority (default) : 5
Priority (default) : 6
Scan Defer Time (msecs) : 100
Media Stream Multicast-direct : Disabled
CCX - AironetIe Support : Enabled
CCX - Gratuitous ProbeResponse (GPR) : Disabled
CCX - Diagnostics Channel Capability : Disabled
Dot11-Phone Mode (7920) : Invalid
Wired Protocol : None
Peer-to-Peer Blocking Action : Disabled
Radio Policy : All
DTIM period for 802.11a radio : 1
DTIM period for 802.11b radio : 1
Local EAP Authentication : PEAPProfile
Mac Filter Authorization list name : Disabled
Accounting list name : Disabled
802.1x authentication list name : Disabled
Security
802.11 Authentication : Open System
Static WEP Keys : Disabled
802.1X : Disabled
Wi-Fi Protected Access (WPA/WPA2) : Enabled
WPA (SSN IE) : Disabled
WPA2 (RSN IE) : Enabled
TKIP Cipher : Disabled
AES Cipher : Enabled
Auth Key Management
802.1x : Enabled
PSK : Disabled
CCKM : Disabled
CKIP : Disabled
IP Security : Disabled
IP Security Passthru : Disabled
L2TP : Disabled
Web Based Authentication : Disabled
Conditional Web Redirect : Disabled
Splash-Page Web Redirect : Disabled
Auto Anchor : Disabled
Sticky Anchoring : Enabled
Cranite Passthru : Disabled
Fortress Passthru : Disabled
PPTP : Disabled
Infrastructure MFP protection : Enabled
Client MFP : Optional
Webauth On-mac-filter Failure : Disabled
Webauth Authentication List Name : Disabled
Webauth Parameter Map : Disabled
Tkip MIC Countermeasure Hold-down Timer : 60
Call Snooping : Disabled
Passive Client : Disabled
Non Cisco WGB : Disabled
Band Select : Disabled
Load Balancing : Disabled
IP Source Guard : Disabled
Device# show wireless client mac-address 6470.0227.0a89 detail Client MAC Address : 6470.0227.0a89 Client Username : tiago AP MAC Address : 64d8.146f.e5a0 AP Name: APd48c.b52f.4a1e Client State : Associated Wireless LAN Id : 1 Wireless LAN Name: TiagoNGWC BSSID : 64d8.146f.e5a0 Connected For : 323 secs Protocol : 802.11n - 2.4 GHz Channel : 6 IPv4 Address : 192.168.80.100 IPv6 Address : Unknown Association Id : 1 Authentication Algorithm : Open System ... Policy Manager State : RUN Policy Manager Rule Created : Yes NPU Fast Fast Notified : Yes Last Policy Manager State : RUN Client Entry Create Time : 153207 seconds Policy Type : WPA2 Authentication Key Management : 802.1x Encryption Cipher : CCMP (AES) Management Frame Protection : No EAP Type : PEAP Interface : VLAN0080 VLAN : 80 Quarantine VLAN : 0 Access VLAN : 80 ...
Troubleshooting the Local EAP Authentication configuring issues
This section provides troubleshooting information on Local EAP Authentication configuring issues.
Enable Traces for Wireless Client Issues
-
To trace the wireless client issues enter the following command:
set trace group-wireless-client level debug debug client mac <MAC>
-
To filter on a specific MAC address, enter:
set trace group-wireless-client filter mac <MAC>
-
To view unfiltered output, enter:
show trace messages group-wireless-client
-
To view filtered output, enter:
show trace sys-filtered-traces
-
To view the settings, enter:
show trace all-buffer settings
-
Enable debug ip device tracking, suppose if you come across issues while retrieving IP addresses.
 Note | Depending on issues encountered, you may need to view other traces. |
Debugs for dot1x and EAP
Following are the debug commands used for dot1x and EAP configurations.
Debug command outputs are as follows;
Device# *Sep 19 07:00:21.423: 6470.0227.0A89 Association received from mobile on AP 64D8.146F.E5A0 1 wcm: cct Msg Sent at 1379573926 se *Sep 19 07:00:21.423: 6470.0227.0A89 qos upstream policy is unknown and downstreampolicy is unknown 1 wcm: Sent at 1379573926 se *Sep 19 07:00:21.423: 6470.0227.0A89 apChanged 0 wlanChanged 0 mscb ipAddr 192.168.80.100, apf RadiusOverride 0x0, numIPv6Addr=0 1 wcm: = 0^M *Sep 19 07:00:21.423: 6470.0227.0A89 Applying WLAN policy on MSCB. 1 wcm: ipAddr 192.168.80.100, apf RadiusOverride 0x0, numIPv6Addr=0 *Sep 19 07:00:21.424: 6470.0227.0A89 Applying WLAN ACL policies to client 1 wcm: 192.168.80.100, apf RadiusOverride 0x0, numIPv6Addr=0 *Sep 19 07:00:21.424: 6470.0227.0A89 No Interface ACL used for Wireless client in WCM(NGWC) 1 wcm: pf RadiusOverride 0x0, numIPv6Addr=0 *Sep 19 07:00:21.424: 6470.0227.0A89 Applying site-specific IPv6 override for station 6470.0227.0A89 - vapId 1, site 'default-group', interface 'VLAN0080' 1 wcm: *Sep 19 07:00:21.424: 6470.0227.0A89 Applying local bridging Interface Policy for station 6470.0227.0A89 - vlan 80, interface 'VLAN0080' 1 wcm: erface 'VLAN0080' *Sep 19 07:00:21.424: 6470.0227.0A89 STA - rates (8): 1 wcm: 130 132 139 12 18 150 24 36 48 72 96 108 0 0 0 0 *Sep 19 07:00:21.424: 6470.0227.0A89 STA - rates (12): 1 wcm: 130 132 139 12 18 150 24 36 48 72 96 108 0 0 0 0 *Sep 19 07:00:21.424: 6470.0227.0A89 new capwap_wtp_iif_id d7844000000004,sm capwap_wtp_iif_id d7844000000004 1 wcm: an 80, interface 'VLAN0080' *Sep 19 07:00:21.424: 6470.0227.0A89 In >= L2AUTH_COMPLETE for station 6470.0227.0A89 1 wcm: _iif_id d7844000000004 *Sep 19 07:00:21.424: 6470.0227.0A89 192.168.80.100 RUN (20) Change state to START (0) last state RUN (20) 1 wcm: *Sep 19 07:00:21.424: 6470.0227.0A89 WCDB_CHANGE: 1 wcm: Client 1 m_vlan 80 Radio iif id 0xdf0f4000000005 bssid iif id 0xcd248000000015, bssid 64D8.146F.E5A0 *Sep 19 07:00:21.424: 6470.0227.0A89 WCDB_AUTH: 1 wcm: Adding opt82 len 0 *Sep 19 07:00:21.425: 6470.0227.0A89 WCDB_LLM: 1 wcm: NoRun Prev Mob 1, Curr Mob 1 llmReq 5, return True *Sep 19 07:00:21.425: 6470.0227.0A89 auth state 0 mob state 1 setWme 0 wme 1 roam_sent 0 1 wcm: rn True *Sep 19 07:00:21.425: 6470.0227.0A89 WCDB_CHANGE: 1 wcm: auth=ASSOCIATION(0) vlan 80 radio 0 client_id 0xde51c000000021 mobility=Local(1) src_int 0xd7844000000004 dst_int 0x0 ackflag 2 reassoc_client 0 llm_notif 1 ip 192.168.80.100 ip_learn_type ARP *Sep 19 07:00:21.425: 6470.0227.0A89 192.168.80.100 START (0) Initializing policy 1 wcm: 0 client_id 0xde51c000000021 mobility=Local(1) src_int 0xd7844000000004 dst_int 0x0 ackflag 2 reassoc_client 0 llm_notif 1 ip 192.168.80.100 ip_learn_type ARP *Sep 19 07:00:21.425: PEM recv processing msg Del SCB(4) 1 wcm: T (0) Initializing policy *Sep 19 07:00:21.425: 6470.0227.0A89 192.168.80.100 START (0) Change state to AUTHCHECK (2) last state RUN (20) 1 wcm: bility=Local(1) src_int 0xd7844000000004 dst_int 0x0 ackflag 2 reassoc_client 0 llm_notif 1 ip 192.168.80.100 ip_learn_type ARP *Sep 19 07:00:21.425: 6470.0227.0A89 192.168.80.100 AUTHCHECK (2) Change state to 8021X_REQD (3) last state RUN (20) 1 wcm: y=Local(1) src_int 0xd7844000000004 dst_int 0x0 ackflag 2 reassoc_client 0 llm_notif 1 ip 192.168.80.100 ip_learn_type ARP *Sep 19 07:00:21.425: 6470.0227.0A89 192.168.80.100 8021X_REQD (3) DHCP required on AP 64D8.146F.E5A0 vapId 1 apVapId 1for this client 1 wcm: 0xd7844000000004 dst_int 0x0 ackflag 2 reassoc_client 0 llm_notif 1 ip 192.168.80.100 ip_learn_type ARP *Sep 19 07:00:21.425: 6470.0227.0A89 Not Using WMM Compliance code qosCap 00 1 wcm: uired on AP 64D8.146F.E5A0 vapId 1 apVapId 1for this client *Sep 19 07:00:21.425: 6470.0227.0A89 192.168.80.100 8021X_REQD (3) Plumbed mobile LWAPP rule on AP 64D8.146F.E5A0 vapId 1 apVapId 1 1 wcm: nt *Sep 19 07:00:21.425: 6470.0227.0A89 apfPemAddUser2 (apf_policy.c: 1 wcm:161) Changing state for mobile 6470.0227.0A89 on AP 64D8.146F.E5A0 from Associated to Associated *Sep 19 07:00:21.426: 6470.0227.0A89 Stopping deletion of Mobile Station: 1 wcm: (callerId: 48) *Sep 19 07:00:21.426: 6470.0227.0A89 Ms Timeout = 0, Session Timeout = 1800 1 wcm: llerId: 48) *Sep 19 07:00:21.426: 6470.0227.0A89 Sending Assoc Response to station on BSSID 64D8.146F.E5A0 (status 0) ApVapId 1 Slot 0 1 wcm: .146F.E5A0 from Associated to Associated *Sep 19 07:00:21.426: 6470.0227.0A89 apfProcessAssocReq (apf_80211.c: 1 wcm: 5260) Changing state for mobile 6470.0227.0A89 on AP 64D8.146F.E5A0 from Associated to Associated *Sep 19 07:00:21.426: 6470.0227.0A89 192.168.80.100 8021X_REQD (3) Handling pemDelScb Event skipping delete 1 wcm: 7.0A89 on AP 64D8.146F.E5A0 from Associated to Associated *Sep 19 07:00:21.435: dot1x-sm:[6470.0227.0a89, Ca0] Posting RESTART on Client 0x60000009 *Sep 19 07:00:21.435: dot1x_auth Ca0: during state auth_authenticated, got event 13(restart) *Sep 19 07:00:21.435: @@@ dot1x_auth Ca0: auth_authenticated -> auth_restart *Sep 19 07:00:21.435: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting authenticated state *Sep 19 07:00:21.435: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009: entering restart *Sep 19 07:00:21.435: dot1x-ev:[6470.0227.0a89, Ca0] Override cfg - MAC 6470.0227.0a89 - profile PEAPProfile *Sep 19 07:00:21.435: dot1x-ev:[6470.0227.0a89, Ca0] Override cfg - SuppTimeout 30s, ReAuthMax 2, MaxReq 2, TxPeriod 30s *Sep 19 07:00:21.435: dot1x-ev:[6470.0227.0a89, Ca0] Sending create new context event to EAP for 0x60000009 (6470.0227.0a89) *Sep 19 07:00:21.435: EAP-EVENT: Received context create from LL (Dot1x-Authenticator) (0x60000009) *Sep 19 07:00:21.436: EAP-AUTH-EVENT: Received AAA ID 0x0000001F from LL *Sep 19 07:00:21.436: EAP-AUTH-AAA-EVENT: Assigning AAA ID 0x0000001F *Sep 19 07:00:21.436: EAP-AUTH-EVENT: Received Session ID "c0a82104523aa0a30000001f" from LL *Sep 19 07:00:21.436: EAP-AUTH-EVENT: Setting authentication mode: Passthrough *Sep 19 07:00:21.436: EAP-EVENT: Using EAP profile "PEAPProfile" (handle 0x26000052) *Sep 19 07:00:21.436: eap_authen : initial state eap_auth_initialize has enter *Sep 19 07:00:21.436: EAP-EVENT: Allocated new EAP context (handle = 0x26000052) *Sep 19 07:00:21.436: dot1x-sm:[6470.0227.0a89, Ca0] Posting !EAP_RESTART on Client 0x60000009 *Sep 19 07:00:21.436: dot1x_auth Ca0: during state auth_restart, got event 6(no_eapRestart) *Sep 19 07:00:21.436: @@@ dot1x_auth Ca0: auth_restart -> auth_connecting *Sep 19 07:00:21.436: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:enter connecting state *Sep 19 07:00:21.436: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009: restart connecting *Sep 19 07:00:21.436: EAP-EVENT: Received EAP event 'EAP_AUTHENTICATOR_START' on handle 0x26000052 *Sep 19 07:00:21.436: eap_authen : during state eap_auth_initialize, got event 25(eapStartTmo) *Sep 19 07:00:21.436: @@@ eap_authen : eap_auth_initialize -> eap_auth_select_action *Sep 19 07:00:21.436: eap_authen : during state eap_auth_select_action, got event 20(eapDecisionPropose) *Sep 19 07:00:21.436: @@@ eap_authen : eap_auth_select_action -> eap_auth_propose_method *Sep 19 07:00:21.436: eap_authen : idle during state eap_auth_propose_method *Sep 19 07:00:21.436: @@@ eap_authen : eap_auth_propose_method -> eap_auth_method_request *Sep 19 07:00:21.436: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:21.436: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:21.436: EAP-AUTH-EVENT: Current method = Identity *Sep 19 07:00:21.436: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_ID_REQUEST' on handle 0x26000052 *Sep 19 07:00:21.436: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:21.437: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:21.437: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xA Length:0x0047 Type:IDENTITY *Sep 19 07:00:21.437: Payload: 006E6574776F726B69643D546961676F ... *Sep 19 07:00:21.437: EAP-EVENT: Started 'Authenticator ReqId Retransmit' timer (30s) for EAP sesion handle 0x26000052 *Sep 19 07:00:21.437: EAP-EVENT: Started EAP tick timer *Sep 19 07:00:21.437: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_TX_PACKET' on handle 0x26000052 *Sep 19 07:00:21.437: dot1x-sm:[6470.0227.0a89, Ca0] Posting RX_REQ on Client 0x60000009 *Sep 19 07:00:21.437: dot1x_auth Ca0: during state auth_connecting, got event 10(eapReq_no_reAuthMax) *Sep 19 07:00:21.437: @@@ dot1x_auth Ca0: auth_connecting -> auth_authenticating *Sep 19 07:00:21.437: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009: authenticating state entered *Sep 19 07:00:21.437: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:connecting authenticating action *Sep 19 07:00:21.437: dot1x-sm:[6470.0227.0a89, Ca0] Posting AUTH_START for 0x60000009 *Sep 19 07:00:21.437: dot1x_auth_bend Ca0: during state auth_bend_idle, got event 4(eapReq_authStart) *Sep 19 07:00:21.437: @@@ dot1x_auth_bend Ca0: auth_bend_idle -> auth_bend_request *Sep 19 07:00:21.437: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering request state *Sep 19 07:00:21.437: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL packet *Sep 19 07:00:21.437: dot1x-packet:[6470.0227.0a89, Ca0] Platform changed src mac of EAPOL packet *Sep 19 07:00:21.438: dot1x-registry:registry:dot1x_ether_macaddr called *Sep 19 07:00:21.438: dot1x-packet:EAPOL pak Tx - Ver: 0x3 type: 0x0 *Sep 19 07:00:21.438: dot1x-packet: length: 0x0047 *Sep 19 07:00:21.438: dot1x-packet:EAP code: 0x1 id: 0xA length: 0x0047 *Sep 19 07:00:21.438: dot1x-packet: type: 0x1 *Sep 19 07:00:21.438: dot1x-packet:[6470.0227.0a89, Ca0] EAPOL packet sent to client 0x60000009 *Sep 19 07:00:21.438: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:idle request action *Sep 19 07:00:22.149: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:22.149: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.149: dot1x-packet: length: 0x000A *Sep 19 07:00:22.149: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 1, LEN= 10 *Sep 19 07:00:22.149: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89, daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.000a *Sep 19 07:00:22.149: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.150: dot1x-packet: length: 0x000A *Sep 19 07:00:22.150: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:22.150: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:22.150: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:22.150: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:22.150: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:22.150: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:22.150: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.150: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xA Length:0x000A Type:IDENTITY *Sep 19 07:00:22.150: Payload: 746961676F *Sep 19 07:00:22.150: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:22.150: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:22.150: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:22.150: EAP-AUTH-EVENT: EAP Response type = Identity *Sep 19 07:00:22.150: EAP-EVENT: Stopping 'Authenticator ReqId Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:22.150: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:22.150: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:22.151: EAP-AUTH-EVENT: Received peer identity: tiago *Sep 19 07:00:22.151: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_IDENTITY' on handle 0x26000052 *Sep 19 07:00:22.151: eap_authen : during state eap_auth_method_response, got event 13(eapMethodEnd) *Sep 19 07:00:22.151: @@@ eap_authen : eap_auth_method_response -> eap_auth_select_action *Sep 19 07:00:22.151: eap_authen : during state eap_auth_select_action, got event 19(eapDecisionPass) *Sep 19 07:00:22.151: @@@ eap_authen : eap_auth_select_action -> eap_auth_passthru_init *Sep 19 07:00:22.151: eap_authen : during state eap_auth_passthru_init, got event 22(eapPthruIdentity) *Sep 19 07:00:22.151: @@@ eap_authen : eap_auth_passthru_init -> eap_auth_aaa_req *Sep 19 07:00:22.151: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_GET_PEER_MAC_ADDRESS' on handle 0x26000052 *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:22.151: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:22.151: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:22.151: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:22.151: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:22.152: EAP-EVENT: Received context create from LL (AAA_LOCAL_EAP) (0x00000019) *Sep 19 07:00:22.152: EAP-AUTH-EVENT: Setting authentication mode: Local *Sep 19 07:00:22.152: EAP-EVENT: Using EAP profile "PEAPProfile" (handle 0xCE000053) *Sep 19 07:00:22.152: eap_authen : initial state eap_auth_initialize has enter *Sep 19 07:00:22.152: eap_authen : during state eap_auth_initialize, got event 25(eapStartTmo) *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_initialize -> eap_auth_select_action *Sep 19 07:00:22.152: eap_authen : during state eap_auth_select_action, got event 20(eapDecisionPropose) *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_select_action -> eap_auth_propose_method *Sep 19 07:00:22.152: eap_authen : idle during state eap_auth_propose_method *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_propose_method -> eap_auth_method_request *Sep 19 07:00:22.152: eap_authen : during state eap_auth_method_request, got event 21(eapDecisionWait) *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_method_request -> eap_auth_idle *Sep 19 07:00:22.152: EAP-EVENT: Allocated new EAP context (handle = 0xCE000053) *Sep 19 07:00:22.152: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.152: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xA Length:0x000A Type:IDENTITY *Sep 19 07:00:22.152: Payload: 746961676F *Sep 19 07:00:22.152: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:22.152: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:22.152: EAP-AUTH-EVENT: EAP Response type = Identity *Sep 19 07:00:22.152: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:22.152: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:22.152: EAP-AUTH-EVENT: Received peer identity: tiago *Sep 19 07:00:22.153: eap_authen : during state eap_auth_method_response got event 13(eapMethodEnd) *Sep 19 07:00:22.153: @@@ eap_authen : eap_auth_method_response -> eap_auth_select_action *Sep 19 07:00:22.153: EAP-AUTH-EVENT: Using authentication mode: Local *Sep 19 07:00:22.153: EAP-EVENT: Local methods by EAP type: [025 026] *Sep 19 07:00:22.153: eap_authen : during state eap_auth_select_action, got event 20(eapDecisionPropose) *Sep 19 07:00:22.153: @@@ eap_authen : eap_auth_select_action -> eap_auth_propose_method *Sep 19 07:00:22.153: eap_authen : idle during state eap_auth_propose_method *Sep 19 07:00:22.153: @@@ eap_authen : eap_auth_propose_method -> eap_auth_method_request *Sep 19 07:00:22.153: EAP-AUTH-EVENT: Maximum EAP packet size: 1456 *Sep 19 07:00:22.153: EAP-EVENT: Sending method (PEAP) event 'New Context' on handle 0xCE000053 *Sep 19 07:00:22.153: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:22.153: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:22.153: eap_authen : during state eap_auth_method_request, got event 15(eapMethodWaitReply) *Sep 19 07:00:22.153: @@@ eap_authen : eap_auth_method_request -> eap_auth_idle *Sep 19 07:00:22.154: EAP-EVENT: Received Method (PEAP) event 'EAP_METHOD_REPLY' on handle 0xCE000053 *Sep 19 07:00:22.154: eap_authen : during state eap_auth_idle, got event 4(eapMethodReply) *Sep 19 07:00:22.154: @@@ eap_authen : eap_auth_idle -> eap_auth_method_response *Sep 19 07:00:22.154: EAP-AUTH-EVENT: Handling asynchronous method response for context 0xCE000053 *Sep 19 07:00:22.154: EAP-AUTH-EVENT: EAP method state: Continue *Sep 19 07:00:22.154: EAP-AUTH-EVENT: EAP method decision: Unknown *Sep 19 07:00:22.154: eap_authen : during state eap_auth_method_response, got event 14(eapMethodContinue) *Sep 19 07:00:22.154: @@@ eap_authen : eap_auth_method_response -> eap_auth_method_request *Sep 19 07:00:22.154: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:22.154: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:22.154: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.154: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:22.154: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:22.154: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xB Length:0x0006 Type:PEAP *Sep 19 07:00:22.154: Payload: 21 *Sep 19 07:00:22.154: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_TX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.154: EAP-EVENT: eap_aaa_reply *Sep 19 07:00:22.154: EAP-AUTH-AAA-EVENT: Reply received session_label BB000020 *Sep 19 07:00:22.154: EAP-AUTH-AAA-EVENT: Response contains EAP Message, code: 1 *Sep 19 07:00:22.155: EAP-EVENT: Received AAA event 'EAP_AAA_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.155: EAP-AUTH-RX-AAA-PAK: Code:REQUEST ID:0xB Length:0x0006 Type:PEAP *Sep 19 07:00:22.155: Payload: 21 *Sep 19 07:00:22.155: eap_authen : during state eap_auth_aaa_idle, got event 5(eapAAARxPacket) *Sep 19 07:00:22.155: @@@ eap_authen : eap_auth_aaa_idle -> eap_auth_aaa_resp *Sep 19 07:00:22.155: eap_authen : idle during state eap_auth_aaa_resp *Sep 19 07:00:22.155: @@@ eap_authen : eap_auth_aaa_resp -> eap_auth_tx_packet2 *Sep 19 07:00:22.155: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.155: eap_authen : idle during state eap_auth_tx_packet2 *Sep 19 07:00:22.155: @@@ eap_authen : eap_auth_tx_packet2 -> eap_auth_idle2 *Sep 19 07:00:22.155: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xB Length:0x0006 Type:PEAP *Sep 19 07:00:22.155: Payload: 21 *Sep 19 07:00:22.155: EAP-EVENT: Started 'Authenticator Retransmit' timer (30s) for EAP sesion handle 0x26000052 *Sep 19 07:00:22.155: EAP-EVENT: Started EAP tick timer *Sep 19 07:00:22.155: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_TX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.155: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAP_REQ for 0x60000009 *Sep 19 07:00:22.155: dot1x_auth_bend Ca0: during state auth_bend_response, got event 7(eapReq) *Sep 19 07:00:22.155: @@@ dot1x_auth_bend Ca0: auth_bend_response -> auth_bend_request *Sep 19 07:00:22.155: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting response state *Sep 19 07:00:22.155: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering request state *Sep 19 07:00:22.155: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL packet *Sep 19 07:00:22.155: dot1x-packet:[6470.0227.0a89, Ca0] Platform changed src mac of EAPOL packet *Sep 19 07:00:22.155: dot1x-registry:registry:dot1x_ether_macaddr called *Sep 19 07:00:22.155: dot1x-packet:EAPOL pak Tx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.155: dot1x-packet: length: 0x0006 *Sep 19 07:00:22.155: dot1x-packet:EAP code: 0x1 id: 0xB length: 0x0006 *Sep 19 07:00:22.155: dot1x-packet: type: 0x19 *Sep 19 07:00:22.156: dot1x-packet:[6470.0227.0a89, Ca0] EAPOL packet sent to client 0x60000009 *Sep 19 07:00:22.156: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response request action *Sep 19 07:00:22.395: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:22.395: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.395: dot1x-packet: length: 0x0098 *Sep 19 07:00:22.395: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 25, LEN= 152 *Sep 19 07:00:22.396: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89 , daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.0098 *Sep 19 07:00:22.396: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.396: dot1x-packet: length: 0x0098 *Sep 19 07:00:22.396: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:22.396: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:22.396: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:22.396: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:22.396: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:22.396: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:22.396: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.396: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xB Length:0x0098 Type:PEAP *Sep 19 07:00:22.396: Payload: 810000008E1603010089010000850301 ... *Sep 19 07:00:22.396: eap_authen : during state eap_auth_idle2, got event 1(eapRxPacket) *Sep 19 07:00:22.396: @@@ eap_authen : eap_auth_idle2 -> eap_auth_received2 *Sep 19 07:00:22.396: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:22.396: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.396: EAP-EVENT: Stopping 'Authenticator Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:22.396: eap_authen : during state eap_auth_received2, got event 10(eapMethodData) *Sep 19 07:00:22.397: @@@ eap_authen : eap_auth_received2->eap_auth_aaa_req *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:22.397: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:22.397: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:22.397: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:22.397: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:22.397: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.398: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xB Length:0x0098 Type:PEAP *Sep 19 07:00:22.398: Payload: 810000008E1603010089010000850301 ... *Sep 19 07:00:22.398: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:22.398: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:22.398: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:22.398: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.398: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:22.398: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:22.398: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:22.398: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:22.398: eap_authen : during state eap_auth_method_response, got event 15(eapMethodWaitReply) *Sep 19 07:00:22.398: @@@ eap_authen : eap_auth_method_response -> eap_auth_idle *Sep 19 07:00:22.399: EAP-EVENT: Received Method (PEAP) event 'EAP_METHOD_REPLY' on handle 0xCE000053 *Sep 19 07:00:22.399: eap_authen : during state eap_auth_idle, got event 4(eapMethodReply) *Sep 19 07:00:22.399: @@@ eap_authen : eap_auth_idle -> eap_auth_method_response *Sep 19 07:00:22.399: EAP-AUTH-EVENT: Handling asynchronous method response for context 0xCE000053 *Sep 19 07:00:22.399: EAP-AUTH-EVENT: EAP method state: Continue *Sep 19 07:00:22.399: EAP-AUTH-EVENT: EAP method decision: Unknown *Sep 19 07:00:22.399: eap_authen : during state eap_auth_method_response, got event 14(eapMethodContinue) *Sep 19 07:00:22.399: @@@ eap_authen : eap_auth_method_response -> eap_auth_method_request *Sep 19 07:00:22.399: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:22.399: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:22.399: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.399: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:22.399: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:22.399: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xC Length:0x02B1 Type:PEAP *Sep 19 07:00:22.399: Payload: 81000002A7160301004A020000460301 ... *Sep 19 07:00:22.399: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_TX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.399: EAP-EVENT: eap_aaa_reply *Sep 19 07:00:22.400: EAP-AUTH-AAA-EVENT: Reply received session_label BB000020 *Sep 19 07:00:22.400: EAP-AUTH-AAA-EVENT: Response contains EAP Message, code: 1 *Sep 19 07:00:22.400: EAP-EVENT: Received AAA event 'EAP_AAA_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.400: EAP-AUTH-RX-AAA-PAK: Code:REQUEST ID:0xC Length:0x02B1 Type:PEAP *Sep 19 07:00:22.400: Payload: 81000002A7160301004A020000460301 ... *Sep 19 07:00:22.400: eap_authen : during state eap_auth_aaa_idle, got event 5(eapAAARxPacket) *Sep 19 07:00:22.400: @@@ eap_authen : eap_auth_aaa_idle -> eap_auth_aaa_resp *Sep 19 07:00:22.400: eap_authen : idle during state eap_auth_aaa_resp *Sep 19 07:00:22.400: @@@ eap_authen : eap_auth_aaa_resp -> eap_auth_tx_packet2 *Sep 19 07:00:22.400: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.400: eap_authen : idle during state eap_auth_tx_packet2 *Sep 19 07:00:22.400: @@@ eap_authen : eap_auth_tx_packet2 -> eap_auth_idle2 *Sep 19 07:00:22.400: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xC Length:0x02B1 Type:PEAP *Sep 19 07:00:22.400: Payload: 81000002A7160301004A020000460301 ... *Sep 19 07:00:22.400: EAP-EVENT: Started 'Authenticator Retransmit' timer (30s) for EAP sesion handle 0x26000052 *Sep 19 07:00:22.400: EAP-EVENT: Started EAP tick timer *Sep 19 07:00:22.400: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_TX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.400: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAP_REQ for 0x60000009 *Sep 19 07:00:22.400: dot1x_auth_bend Ca0: during state auth_bend_response, got event 7(eapReq) *Sep 19 07:00:22.400: @@@ dot1x_auth_bend Ca0: auth_bend_response -> auth_bend_request *Sep 19 07:00:22.400: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting response state *Sep 19 07:00:22.400: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering request state *Sep 19 07:00:22.400: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL packet *Sep 19 07:00:22.401: dot1x-packet:[6470.0227.0a89, Ca0] Platform changed src mac of EAPOL packet *Sep 19 07:00:22.401: dot1x-registry:registry:dot1x_ether_macaddr called *Sep 19 07:00:22.401: dot1x-packet:EAPOL pak Tx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.401: dot1x-packet: length: 0x02B1 *Sep 19 07:00:22.401: dot1x-packet:EAP code: 0x1 id: 0xC length: 0x02B1 *Sep 19 07:00:22.401: dot1x-packet: type: 0x19 *Sep 19 07:00:22.401: dot1x-packet:[6470.0227.0a89, Ca0] EAPOL packet sent to client 0x60000009 *Sep 19 07:00:22.401: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response request action *Sep 19 07:00:22.646: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:22.646: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.646: dot1x-packet: length: 0x00C8 *Sep 19 07:00:22.646: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 25, LEN= 200 *Sep 19 07:00:22.646: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89 , daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.00c8 *Sep 19 07:00:22.646: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.646: dot1x-packet: length: 0x00C8 *Sep 19 07:00:22.647: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:22.647: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:22.647: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:22.647: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:22.647: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:22.647: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:22.647: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.647: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xC Length:0x00C8 Type:PEAP *Sep 19 07:00:22.647: Payload: 81000000BE1603010086100000820080 ... *Sep 19 07:00:22.647: eap_authen : during state eap_auth_idle2, got event 1(eapRxPacket) *Sep 19 07:00:22.647: @@@ eap_authen : eap_auth_idle2 -> eap_auth_received2 *Sep 19 07:00:22.647: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:22.647: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.647: EAP-EVENT: Stopping 'Authenticator Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:22.647: eap_authen : during state eap_auth_received2, got event 10(eapMethodData) *Sep 19 07:00:22.647: @@@ eap_authen : eap_auth_received2 -> eap_auth_aaa_req *Sep 19 07:00:22.647: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:22.647: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:22.647: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:22.647: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:22.648: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:22.648: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:22.648: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:22.648: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:22.648: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:22.648: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:22.648: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:22.648: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.648: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xC Length:0x00C8 Type:PEAP *Sep 19 07:00:22.648: Payload: 81000000BE1603010086100000820080 ... *Sep 19 07:00:22.648: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:22.648: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:22.648: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:22.648: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.649: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:22.649: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:22.649: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:22.649: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:22.649: eap_authen : during state eap_auth_method_response, got event 15(eapMethodWaitReply) *Sep 19 07:00:22.649: @@@ eap_authen : eap_auth_method_response -> eap_auth_idle *Sep 19 07:00:22.675: EAP-EVENT: Received Method (PEAP) event 'EAP_METHOD_REPLY' on handle 0xCE000053 *Sep 19 07:00:22.675: eap_authen : during state eap_auth_idle, got event 4(eapMethodReply) *Sep 19 07:00:22.675: @@@ eap_authen : eap_auth_idle -> eap_auth_method_response *Sep 19 07:00:22.675: EAP-AUTH-EVENT: Handling asynchronous method response for context 0xCE000053 *Sep 19 07:00:22.675: EAP-AUTH-EVENT: EAP method state: Continue *Sep 19 07:00:22.675: EAP-AUTH-EVENT: EAP method decision: Unknown *Sep 19 07:00:22.675: eap_authen : during state eap_auth_method_response, got event 14(eapMethodContinue) *Sep 19 07:00:22.675: @@@ eap_authen : eap_auth_method_response -> eap_auth_method_request *Sep 19 07:00:22.675: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:22.675: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:22.675: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.675: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:22.675: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:22.675: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xD Length:0x003D Type:PEAP *Sep 19 07:00:22.676: Payload: 81000000331403010001011603010028 ... *Sep 19 07:00:22.676: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_TX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.676: EAP-EVENT: eap_aaa_reply *Sep 19 07:00:22.676: EAP-AUTH-AAA-EVENT: Reply received session_label BB000020 *Sep 19 07:00:22.676: EAP-AUTH-AAA-EVENT: Response contains EAP Message, code: 1 *Sep 19 07:00:22.676: EAP-EVENT: Received AAA event 'EAP_AAA_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.676: EAP-AUTH-RX-AAA-PAK: Code:REQUEST ID:0xD Length:0x003D Type:PEAP *Sep 19 07:00:22.676: Payload: 81000000331403010001011603010028 ... *Sep 19 07:00:22.676: eap_authen : during state eap_auth_aaa_idle, got event 5(eapAAARxPacket) *Sep 19 07:00:22.676: @@@ eap_authen : eap_auth_aaa_idle -> eap_auth_aaa_resp *Sep 19 07:00:22.676: eap_authen : idle during state eap_auth_aaa_resp *Sep 19 07:00:22.676: @@@ eap_authen : eap_auth_aaa_resp -> eap_auth_tx_packet2 *Sep 19 07:00:22.676: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:22.676: eap_authen : idle during state eap_auth_tx_packet2 *Sep 19 07:00:22.676: @@@ eap_authen : eap_auth_tx_packet2 -> eap_auth_idle2 *Sep 19 07:00:22.676: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xD Length:0x003D Type:PEAP *Sep 19 07:00:22.676: Payload: 81000000331403010001011603010028 ... *Sep 19 07:00:22.676: EAP-EVENT: Started 'Authenticator Retransmit' timer (30s) for EAP sesion handle 0x26000052 *Sep 19 07:00:22.676: EAP-EVENT: Started EAP tick timer *Sep 19 07:00:22.676: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_TX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.677: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAP_REQ for 0x60000009 *Sep 19 07:00:22.677: dot1x_auth_bend Ca0: during state auth_bend_response, got event 7(eapReq) *Sep 19 07:00:22.677: @@@ dot1x_auth_bend Ca0: auth_bend_response -> auth_bend_request *Sep 19 07:00:22.677: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting response state *Sep 19 07:00:22.677: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering request state *Sep 19 07:00:22.677: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL packet *Sep 19 07:00:22.677: dot1x-packet:[6470.0227.0a89, Ca0] Platform changed src mac of EAPOL packet *Sep 19 07:00:22.677: dot1x-registry:registry:dot1x_ether_macaddr called *Sep 19 07:00:22.677: dot1x-packet:EAPOL pak Tx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.677: dot1x-packet: length: 0x003D *Sep 19 07:00:22.677: dot1x-packet:EAP code: 0x1 id: 0xD length: 0x003D *Sep 19 07:00:22.677: dot1x-packet: type: 0x19 *Sep 19 07:00:22.677: dot1x-packet:[6470.0227.0a89, Ca0] EAPOL packet sent to client 0x60000009 *Sep 19 07:00:22.677: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response request action *Sep 19 07:00:22.902: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:22.903: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.903: dot1x-packet: length: 0x0006 *Sep 19 07:00:22.903: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 25, LEN= 6 *Sep 19 07:00:22.903: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89 , daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.0006 *Sep 19 07:00:22.903: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:22.903: dot1x-packet: length: 0x0006 *Sep 19 07:00:22.903: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:22.903: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:22.903: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:22.903: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:22.903: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:22.903: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:22.904: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:22.904: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xD Length:0x0006 Type:PEAP *Sep 19 07:00:22.904: Payload: 01 *Sep 19 07:00:22.904: eap_authen : during state eap_auth_idle2,got event 1(eapRxPacket) *Sep 19 07:00:22.904: @@@ eap_authen : eap_auth_idle2 -> eap_auth_received2 *Sep 19 07:00:22.904: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:22.904: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.904: EAP-EVENT: Stopping 'Authenticator Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:22.904: eap_authen : during state eap_auth_received2, got event 10(eapMethodData) *Sep 19 07:00:22.904: @@@ eap_authen : eap_auth_received2 -> eap_auth_aaa_req *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:22.904: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:22.904: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:22.905: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:22.905: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:22.905: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:22.905: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:22.905: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xD Length:0x0006 Type:PEAP *Sep 19 07:00:22.905: Payload: 01 *Sep 19 07:00:22.905: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:22.905: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:22.905: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:22.905: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:22.905: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:22.905: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:22.905: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:22.905: EAP-EVENT: Received context create from LL (PEAP) (0x69000006) *Sep 19 07:00:22.905: EAP-AUTH-EVENT: Setting authentication mode: Local *Sep 19 07:00:22.905: EAP-EVENT: Using EAP profile "PEAP Inner Method EAP Profile" (handle 0x99000054) *Sep 19 07:00:22.905: eap_authen : initial state eap_auth_initialize has enter *Sep 19 07:00:22.905: EAP-EVENT: Allocated new EAP context (handle = 0x99000054) *Sep 19 07:00:22.906: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:22.906: eap_authen : during state eap_auth_method_response, got event 15(eapMethodWaitReply) *Sep 19 07:00:22.906: @@@ eap_authen : eap_auth_method_response -> eap_auth_idle *Sep 19 07:00:22.906: EAP-EVENT: Received EAP event 'EAP_AUTHENTICATOR_START' on handle 0x99000054 *Sep 19 07:00:22.906: eap_authen : during state eap_auth_initialize, got event 25(eapStartTmo) *Sep 19 07:00:22.906: @@@ eap_authen : eap_auth_initialize -> eap_auth_select_action *Sep 19 07:00:22.906: eap_authen : during state eap_auth_select_action, got event 20(eapDecisionPropose) *Sep 19 07:00:22.906: @@@ eap_authen : eap_auth_select_action -> eap_auth_propose_method *Sep 19 07:00:22.906: eap_authen : idle during state eap_auth_propose_method *Sep 19 07:00:22.906: @@@ eap_authen : eap_auth_propose_method -> eap_auth_method_request *Sep 19 07:00:22.908: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response request action *Sep 19 07:00:23.148: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:23.148: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:23.148: dot1x-packet: length: 0x0048 *Sep 19 07:00:23.148: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 25, LEN= 72 *Sep 19 07:00:23.148: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89 , daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.0048 *Sep 19 07:00:23.148: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:23.148: dot1x-packet: length: 0x0048 *Sep 19 07:00:23.148: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:23.148: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:23.148: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:23.148: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:23.148: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:23.148: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:23.149: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:23.149: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xE Length:0x0048 Type:PEAP *Sep 19 07:00:23.149: Payload: 011703010018E5BC67F95BDE2D2BF45C ... *Sep 19 07:00:23.149: eap_authen : during state eap_auth_idle2, got event 1(eapRxPacket) *Sep 19 07:00:23.149: @@@ eap_authen : eap_auth_idle2 -> eap_auth_received2 *Sep 19 07:00:23.149: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:23.149: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:23.149: EAP-EVENT: Stopping 'Authenticator Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:23.149: eap_authen : during state eap_auth_received2, got event 10(eapMethodData) *Sep 19 07:00:23.149: @@@ eap_authen : eap_auth_received2 -> eap_auth_aaa_req *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:23.149: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:23.149: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:23.150: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:23.150: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:23.150: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:23.150: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:23.150: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xE Length:0x0048 Type:PEAP *Sep 19 07:00:23.150: Payload: 011703010018E5BC67F95BDE2D2BF45C ... *Sep 19 07:00:23.150: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:23.150: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:23.150: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:23.150: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:23.150: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:23.150: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:23.150: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:23.150: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:23.150: eap_authen : during state eap_auth_method_response, got event 15(eapMethodWaitReply) *Sep 19 07:00:23.150: @@@ eap_authen : eap_auth_method_response -> eap_auth_idle *Sep 19 07:00:23.151: EAP-EVENT: Received LL (PEAP) event 'EAP_RX_PACKET' on handle 0x99000054 *Sep 19 07:00:23.151: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0xE Length:0x000A Type:IDENTITY *Sep 19 07:00:23.151: Payload: 746961676F *Sep 19 07:00:23.151: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:23.151: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:23.151: EAP-AUTH-EVENT: EAP Response received by context 0x99000054 *Sep 19 07:00:23.151: EAP-AUTH-EVENT: EAP Response type = Identity *Sep 19 07:00:23.151: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:23.151: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:23.151: EAP-AUTH-EVENT: Received peer identity: tiago *Sep 19 07:00:23.151: eap_authen : during state eap_auth_method_response, got event 13(eapMethodEnd) *Sep 19 07:00:23.151: @@@ eap_authen : eap_auth_method_response -> eap_auth_select_action *Sep 19 07:00:23.151: EAP-AUTH-EVENT: Using authentication mode: Local *Sep 19 07:00:23.151: EAP-EVENT: Sending LL (PEAP) event 'EAP_GET_CREDENTIAL_PROFILE_FROM_USERNAME' on handle 0x99000054 *Sep 19 07:00:23.151: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_GET_CREDENTIAL_PROFILE_FROM_USERNAME' on handle 0xCE000053 *Sep 19 07:00:23.151: EAP-AUTH-EVENT: Waiting for asynchronous reply from LL (AAA_LOCAL_EAP) *Sep 19 07:00:23.151: EAP-AUTH-EVENT: Waiting for asynchronous reply from LL (PEAP) *Sep 19 07:00:23.152: EAP-EVENT: Local methods by EAP type: [006 026] *Sep 19 07:00:23.152: eap_authen : during state eap_auth_select_action, got event 21(eapDecisionWait) *Sep 19 07:00:23.152: @@@ eap_authen : eap_auth_select_action -> eap_auth_idle *Sep 19 07:00:23.152: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_LL_REPLY' on handle 0xCE000053 *Sep 19 07:00:23.152: EAP-AUTH-EVENT: Relaying LL response for context 0xCE000053 *Sep 19 07:00:23.152: EAP-AUTH-EVENT: Using credential profile name: tiago (0xCE000053) *Sep 19 07:00:23.152: EAP-EVENT: Sending method (PEAP) event 'LL Response' on handle 0xCE000053 *Sep 19 07:00:23.152: EAP-EVENT: Received LL (PEAP) event 'EAP_LL_REPLY' on handle 0x99000054 *Sep 19 07:00:23.152: eap_authen : during state eap_auth_idle, got event 2(eapLLReply) *Sep 19 07:00:23.152: @@@ eap_authen : eap_auth_idle -> eap_auth_select_action *Sep 19 07:00:23.152: EAP-AUTH-EVENT: Using credential profile name: tiago (0x99000054) *Sep 19 07:00:23.152: eap_authen : during state eap_auth_select_action, got event 20(eapDecisionPropose) *Sep 19 07:00:23.152: @@@ eap_authen : eap_auth_select_action -> eap_auth_propose_method *Sep 19 07:00:23.152: eap_authen : idle during state eap_auth_propose_method *Sep 19 07:00:23.152: @@@ eap_authen : eap_auth_propose_method -> eap_auth_method_request *Sep 19 07:00:23.152: EAP-AUTH-EVENT: Maximum EAP packet size: 1464 *Sep 19 07:00:23.152: EAP-EVENT: Sending method (GTC) event 'New Context' on handle 0x99000054 *Sep 19 07:00:23.153: EAP-EVENT: Sending method (GTC) event 'Receive Packet' on handle 0x99000054 *Sep 19 07:00:23.153: EAP-AUTH-EVENT: Method (GTC) state: Continue *Sep 19 07:00:23.153: EAP-AUTH-EVENT: Method (GTC) decision: Unknown *Sep 19 07:00:23.153: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:23.153: EAP-AUTH-EVENT: Current method = 6 *Sep 19 07:00:23.153: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:23.153: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xF Length:0x0005 Type:GTC *Sep 19 07:00:23.153: EAP-EVENT: Sending LL (PEAP) event 'EAP_TX_PACKET' on handle 0x99000054 *Sep 19 07:00:23.153: EAP-EVENT: Received Method (PEAP) event 'EAP_METHOD_REPLY' on handle 0xCE000053 *Sep 19 07:00:23.153: eap_authen : during state eap_auth_idle, got event 4(eapMethodReply) *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_idle -> eap_auth_method_response *Sep 19 07:00:23.153: EAP-AUTH-EVENT: Handling asynchronous method response for context 0xCE000053 *Sep 19 07:00:23.153: EAP-AUTH-EVENT: EAP method state: Continue *Sep 19 07:00:23.153: EAP-AUTH-EVENT: EAP method decision: Unknown *Sep 19 07:00:23.153: eap_authen : during state eap_auth_method_response, got event 14(eapMethodContinue) *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_method_response -> eap_auth_method_request *Sep 19 07:00:23.153: eap_authen : idle during state eap_auth_method_request *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_method_request -> eap_auth_tx_packet *Sep 19 07:00:23.153: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:23.153: eap_authen : idle during state eap_auth_tx_packet *Sep 19 07:00:23.153: @@@ eap_authen : eap_auth_tx_packet -> eap_auth_idle *Sep 19 07:00:23.153: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xF Length:0x002B Type:PEAP *Sep 19 07:00:23.153: Payload: 011703010020377AEA34B95C78A82976 ... *Sep 19 07:00:23.153: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_TX_PACKET' on handle 0xCE000053 *Sep 19 07:00:23.154: EAP-EVENT: eap_aaa_reply *Sep 19 07:00:23.154: EAP-AUTH-AAA-EVENT: Reply received session_label BB000020 *Sep 19 07:00:23.154: EAP-AUTH-AAA-EVENT: Response contains EAP Message, code: 1 *Sep 19 07:00:23.154: EAP-EVENT: Received AAA event 'EAP_AAA_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:23.154: EAP-AUTH-RX-AAA-PAK: Code:REQUEST ID:0xF Length:0x002B Type:PEAP *Sep 19 07:00:23.154: Payload: 011703010020377AEA34B95C78A82976 ... *Sep 19 07:00:23.154: eap_authen : during state eap_auth_aaa_idle, got event 5(eapAAARxPacket) *Sep 19 07:00:23.154: @@@ eap_authen : eap_auth_aaa_idle -> eap_auth_aaa_resp *Sep 19 07:00:23.154: eap_authen : idle during state eap_auth_aaa_resp *Sep 19 07:00:23.154: @@@ eap_authen : eap_auth_aaa_resp -> eap_auth_tx_packet2 *Sep 19 07:00:23.154: EAP-AUTH-EVENT: Current method = 25 *Sep 19 07:00:23.154: eap_authen : idle during state eap_auth_tx_packet2 *Sep 19 07:00:23.154: @@@ eap_authen : eap_auth_tx_packet2 -> eap_auth_idle2 *Sep 19 07:00:23.154: EAP-AUTH-TX-PAK: Code:REQUEST ID:0xF Length:0x002B Type:PEAP *Sep 19 07:00:23.154: Payload: 011703010020377AEA34B95C78A82976 ... *Sep 19 07:00:23.154: EAP-EVENT: Started 'Authenticator Retransmit' timer (30s) for EAP sesion handle 0x26000052 *Sep 19 07:00:23.154: EAP-EVENT: Started EAP tick timer *Sep 19 07:00:23.154: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_TX_PACKET' on handle 0x26000052 *Sep 19 07:00:23.154: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAP_REQ for 0x60000009 *Sep 19 07:00:23.154: dot1x_auth_bend Ca0: during state auth_bend_response, got event 7(eapReq) *Sep 19 07:00:23.154: @@@ dot1x_auth_bend Ca0: auth_bend_response -> auth_bend_request *Sep 19 07:00:23.154: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting response state *Sep 19 07:00:23.871: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response request action *Sep 19 07:00:24.114: dot1x-packet:[6470.0227.0a89, Ca0] Queuing an EAPOL pkt on Authenticator Q *Sep 19 07:00:24.114: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:24.114: dot1x-packet: length: 0x0048 *Sep 19 07:00:24.114: dot1x-ev:[Ca0] Dequeued pkt: Int Ca0 CODE= 2,TYPE= 25, LEN= 72 *Sep 19 07:00:24.114: dot1x-ev:[Ca0] Received pkt saddr =6470.0227.0a89 , daddr = 64d8.146f.e5a0, pae-ether-type = 888e.0300.0048 *Sep 19 07:00:24.115: dot1x-packet:EAPOL pak rx - Ver: 0x3 type: 0x0 *Sep 19 07:00:24.115: dot1x-packet: length: 0x0048 *Sep 19 07:00:24.115: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAPOL_EAP for 0x60000009 *Sep 19 07:00:24.115: dot1x_auth_bend Ca0: during state auth_bend_request, got event 6(eapolEap) *Sep 19 07:00:24.115: @@@ dot1x_auth_bend Ca0: auth_bend_request -> auth_bend_response *Sep 19 07:00:24.115: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering response state *Sep 19 07:00:24.115: dot1x-ev:[6470.0227.0a89, Ca0] Response sent to the server from 0x60000009 *Sep 19 07:00:24.115: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:request response action *Sep 19 07:00:24.115: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_RX_PACKET' on handle 0x26000052 *Sep 19 07:00:24.115: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0x12 Length:0x0048 Type:PEAP *Sep 19 07:00:24.115: Payload: 0117030100186DEF131BC85E44CBDD50 ... *Sep 19 07:00:24.115: eap_authen : during state eap_auth_idle2, got event 1(eapRxPacket) *Sep 19 07:00:24.115: @@@ eap_authen : eap_auth_idle2 -> eap_auth_received2 *Sep 19 07:00:24.115: EAP-AUTH-EVENT: EAP Response received by context 0x26000052 *Sep 19 07:00:24.115: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:24.115: EAP-EVENT: Stopping 'Authenticator Retransmit' timer for EAP sesion handle 0x26000052 *Sep 19 07:00:24.115: eap_authen : during state eap_auth_received2, got event 10(eapMethodData) *Sep 19 07:00:24.115: @@@ eap_authen : eap_auth_received2 -> eap_auth_aaa_req *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Adding Audit-Session-ID "c0a82104523aa0a30000001f" to RADIUS Req *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Added Audit-Session-ID *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Adding IDB "0x38167B5C" to RADIUS Req *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Added IDB *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Adding EAP profile name "PEAPProfile" to RADIUS Req *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Added EAP profile name to request *Sep 19 07:00:24.116: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_CUSTOMIZE_AAA_REQUEST' on handle 0x26000052 *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: eap_auth_aaa_authen_request_shim aaa_service 19, eap aaa_list handle 0, mlist handle 0 *Sep 19 07:00:24.116: EAP-AUTH-AAA-EVENT: Request sent successfully *Sep 19 07:00:24.116: eap_authen : during state eap_auth_aaa_req, got event 24(eapAAAReqOk) *Sep 19 07:00:24.116: @@@ eap_authen : eap_auth_aaa_req -> eap_auth_aaa_idle *Sep 19 07:00:24.116: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_RX_PACKET' on handle 0xCE000053 *Sep 19 07:00:24.116: EAP-AUTH-RX-PAK: Code:RESPONSE ID:0x12 Length:0x0048 Type:PEAP *Sep 19 07:00:24.117: Payload: 0117030100186DEF131BC85E44CBDD50 ... *Sep 19 07:00:24.117: eap_authen : during state eap_auth_idle, got event 1(eapRxPacket) *Sep 19 07:00:24.117: @@@ eap_authen : eap_auth_idle -> eap_auth_received *Sep 19 07:00:24.117: EAP-AUTH-EVENT: EAP Response received by context 0xCE000053 *Sep 19 07:00:24.117: EAP-AUTH-EVENT: EAP Response type = Method (25) *Sep 19 07:00:24.117: eap_authen : during state eap_auth_received, got event 10(eapMethodData) *Sep 19 07:00:24.117: @@@ eap_authen : eap_auth_received -> eap_auth_method_response *Sep 19 07:00:24.117: EAP-EVENT: Sending method (PEAP) event 'Receive Packet' on handle 0xCE000053 *Sep 19 07:00:24.117: EAP-AUTH-EVENT: Waiting for asynchronous reply from method (PEAP) *Sep 19 07:00:24.117: eap_authen : during state eap_auth_method_response, got event 15(eapMethodWaitReply) *Sep 19 07:00:24.117: @@@ eap_authen : eap_auth_method_response -> eap_auth_idle *Sep 19 07:00:24.118: EAP-EVENT: Received Method (PEAP) event 'EAP_METHOD_REPLY' on handle 0xCE000053 *Sep 19 07:00:24.118: eap_authen : during state eap_auth_idle, got event 4(eapMethodReply) *Sep 19 07:00:24.118: @@@ eap_authen : eap_auth_idle -> eap_auth_method_response *Sep 19 07:00:24.118: EAP-AUTH-EVENT: Handling asynchronous method response for context 0xCE000053 *Sep 19 07:00:24.118: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_KEY_AVAILABLE' on handle 0xCE000053 *Sep 19 07:00:24.118: EAP-AUTH-EVENT: EAP method state: Done *Sep 19 07:00:24.118: EAP-AUTH-EVENT: EAP method decision: Unconditional Success *Sep 19 07:00:24.118: eap_authen : during state eap_auth_method_response, got event 13(eapMethodEnd) *Sep 19 07:00:24.118: @@@ eap_authen : eap_auth_method_response -> eap_auth_select_action *Sep 19 07:00:24.118: eap_authen : during state eap_auth_select_action, got event 18(eapDecisionSuccess) *Sep 19 07:00:24.118: @@@ eap_authen : eap_auth_select_action -> eap_auth_success *Sep 19 07:00:24.118: EAP-EVENT: Received get canned status from lower layer (0xCE000053) *Sep 19 07:00:24.118: EAP-AUTH-TX-PAK: Code:SUCCESS ID:0x12 Length:0x0004 *Sep 19 07:00:24.118: EAP-EVENT: Sending method (PEAP) event 'Free Context' on handle 0xCE000053 *Sep 19 07:00:24.119: EAP-EVENT: Sending LL (AAA_LOCAL_EAP) event 'EAP_SUCCESS' on handle 0xCE000053 *Sep 19 07:00:24.119: EAP-EVENT: Received free context (0xCE000053) from LL (AAA_LOCAL_EAP) *Sep 19 07:00:24.119: EAP-EVENT: eap_aaa_reply *Sep 19 07:00:24.119: EAP-AUTH-AAA-EVENT: Reply received session_label BB000020 *Sep 19 07:00:24.119: EAP-AUTH-AAA-EVENT: Response contains EAP Message, code: 3 *Sep 19 07:00:24.119: EAP-AUTH-AAA-EVENT: Response contains MS MPPE Send Key, length:139 *Sep 19 07:00:24.119: EAP-AUTH-AAA-EVENT: Response contains MS MPPE Recv Key, length:97 *Sep 19 07:00:24.119: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_KEY_AVAILABLE' on handle 0x26000052 *Sep 19 07:00:24.119: EAP-AUTH-AAA-EVENT: Authorization not required for this context *Sep 19 07:00:24.119: EAP-EVENT: Received LL (AAA_LOCAL_EAP) event 'EAP_DELETE' on handle 0xCE000053 *Sep 19 07:00:24.119: EAP-AUTH-AAA-ERROR: Failed to delete aaa coord transaction for 0xCE000053 *Sep 19 07:00:24.119: EAP-AUTH-EVENT: Freed EAP auth context *Sep 19 07:00:24.119: EAP-EVENT: Freed EAP context *Sep 19 07:00:24.120: EAP-EVENT: Received AAA event 'EAP_AAA_SUCCESS' on handle 0x26000052 *Sep 19 07:00:24.120: eap_authen : during state eap_auth_aaa_idle, got event 7(eapAAASuccess) *Sep 19 07:00:24.120: @@@ eap_authen : eap_auth_aaa_idle -> eap_auth_success *Sep 19 07:00:24.120: EAP-AUTH-TX-PAK: Code:SUCCESS ID:0x12 Length:0x0004 *Sep 19 07:00:24.120: EAP-AUTH-EVENT: SUCCESS for EAP method ID: 25, name: PEAP, on handle 0x26000052 *Sep 19 07:00:24.120: EAP-EVENT: Sending LL (Dot1x-Authenticator) event 'EAP_SUCCESS' on handle 0x26000052 *Sep 19 07:00:24.120: dot1x-packet:[6470.0227.0a89, Ca0] Received an EAP Success *Sep 19 07:00:24.120: dot1x-sm:[6470.0227.0a89, Ca0] Posting EAP_SUCCESS for 0x60000009 *Sep 19 07:00:24.120: dot1x_auth_bend Ca0: during state auth_bend_response, got event 11(eapSuccess) *Sep 19 07:00:24.120: @@@ dot1x_auth_bend Ca0: auth_bend_response -> auth_bend_success *Sep 19 07:00:24.120: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting response state *Sep 19 07:00:24.120: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering success state *Sep 19 07:00:24.120: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:response success action *Sep 19 07:00:24.120: dot1x_auth_bend Ca0: idle during state auth_bend_success *Sep 19 07:00:24.121: @@@ dot1x_auth_bend Ca0: auth_bend_success -> auth_bend_idle *Sep 19 07:00:24.121: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering idle state *Sep 19 07:00:24.121: dot1x-sm:[6470.0227.0a89, Ca0] Posting AUTH_SUCCESS on Client 0x60000009 *Sep 19 07:00:24.121: dot1x_auth Ca0: during state auth_authenticating, got event 12(authSuccess_portValid) *Sep 19 07:00:24.121: @@@ dot1x_auth Ca0: auth_authenticating -> auth_authc_result *Sep 19 07:00:24.121: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:exiting authenticating state *Sep 19 07:00:24.121: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering authc result state *Sep 19 07:00:24.121: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL success immediately *Sep 19 07:00:24.121: dot1x-ev:[6470.0227.0a89, Ca0] Sending EAPOL packet *Sep 19 07:00:24.121: dot1x-packet:[6470.0227.0a89, Ca0] Platform changed src mac of EAPOL packet *Sep 19 07:00:24.121: dot1x-registry:registry:dot1x_ether_macaddr called *Sep 19 07:00:24.121: dot1x-packet:EAPOL pak Tx - Ver: 0x3 type: 0x0 *Sep 19 07:00:24.121: dot1x-packet: length: 0x0004 *Sep 19 07:00:24.121: dot1x-packet:EAP code: 0x3 id: 0x12 length: 0x0004 *Sep 19 07:00:24.121: dot1x-packet:[6470.0227.0a89, Ca0] EAPOL packet sent to client 0x60000009 *Sep 19 07:00:24.122: dot1x-ev:[6470.0227.0a89, Ca0] Received Authz Success for the client 0x60000009 (6470.0227.0a89) *Sep 19 07:00:24.122: dot1x-sm:[6470.0227.0a89, Ca0] Posting AUTHZ_SUCCESS on Client 0x60000009 *Sep 19 07:00:24.122: dot1x_auth Ca0: during state auth_authc_result, got event 23(authzSuccess) *Sep 19 07:00:24.122: @@@ dot1x_auth Ca0: auth_authc_result -> auth_authenticated *Sep 19 07:00:24.122: dot1x-sm:[6470.0227.0a89, Ca0] 0x60000009:entering authenticated state *Sep 19 07:00:24.122: dot1x-ev:[6470.0227.0a89, Ca0] EAPOL success packet was sent earlier. *Sep 19 07:00:24.122: EAP-EVENT: Received free context (0x26000052) from LL (Dot1x-Authenticator) *Sep 19 07:00:24.122: EAP-EVENT: Received LL (Dot1x-Authenticator) event 'EAP_DELETE' on handle 0x26000052 *Sep 19 07:00:24.123: EAP-AUTH-AAA-ERROR: Failed to delete aaa coord transaction for 0x26000052 *Sep 19 07:00:24.123: EAP-AUTH-EVENT: Freed EAP auth context *Sep 19 07:00:24.123: EAP-EVENT: Freed EAP context *Sep 19 07:00:24.122: 6470.0227.0A89 client incoming attribute size are 304 1 wcm: pemDelScb Event skipping delete *Sep 19 07:00:24.636: 6470.0227.0A89 192.168.80.100 8021X_REQD (3) Change state to L2AUTHCOMPLETE (4) last state RUN (20) 1 wcm: ^K4D8.146F.E5A *Sep 19 07:00:24.636: 6470.0227.0A89 WCDB_CHANGE: 1 wcm: Client 1 m_vlan 80 Radio iif id 0xdf0f4000000005 bssid iif id 0xcd248000000015, bssid 64D8.146F.E5A0 *Sep 19 07:00:24.636: 6470.0227.0A89 WCDB_AUTH: 1 wcm: Adding opt82 len 0 *Sep 19 07:00:24.636: 6470.0227.0A89 WCDB_CHANGE: 1 wcm: Suppressing SPI (L2 Auth for reassoc) pemstate 4 state L2_AUTH(1) vlan 80 client_id 0xde51c000000021 mob 1 ackflag 2 dropd 0 *Sep 19 07:00:24.636: 6470.0227.0A89 192.168.80.100 L2AUTHCOMPLETE (4) pemAdvanceState2: 1 wcm: MOBILITY-COMPLETE with state 4. *Sep 19 07:00:24.636: 6470.0227.0A89 Send request to EPM 1 wcm: UTHCOMPLETE (4) pemAdvanceState2: MOBILITY-COMPLETE with state 4. *Sep 19 07:00:24.649: 6470.0227.0A89 Received _EPM_SPI_STATUS_SUCCESS for request sent for client 1 wcm: for client *Sep 19 07:00:24.649: 6470.0227.0A89 Post-auth policy ACK recvd from EPM, unset flag on MSCB 1 wcm: ient *Sep 19 07:00:24.907: EAP-EVENT: Stopped EAP tick timer
 Feedback
Feedback