Migrate Between Management Center Models
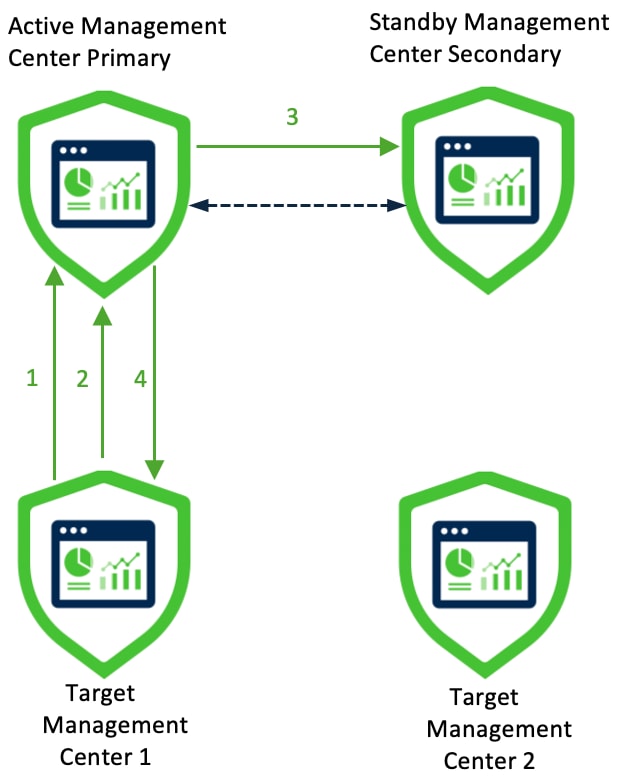
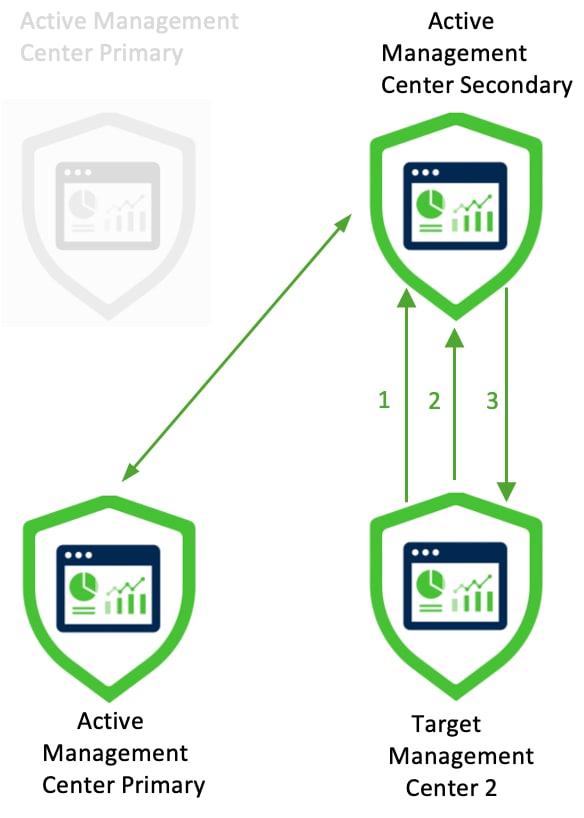
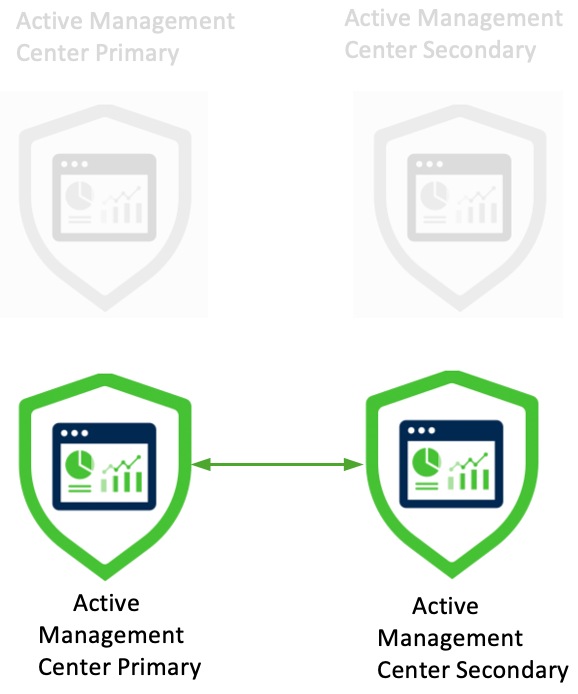
The Secure Management Center Migration wizard allows you to migrate from one Management Center model to another Management Center model. The wizard simplifies your migration experience. After the migration, configurations and events from the source Management Center are available in the target Management Center.
There are two ways of migrating a Management Center:
-
Connected mode: Connect to the source Management Center for migration. Use this method when the source and target Management Centers can connect to each other over HTTPS.
-
Migration bundle mode: Create a migration bundle in the source Management Center and upload it to the target Management Center. Use this method when the source and target Management Centers cannot connect to each other over HTTPS.
Benefits of Using the Secure Management Center Migration Wizard
-
Simplified migration: Migrates the Management Center models seamlessly using the intuitive wizard.
-
Unaffected source Management Center: Ensures that the source Management Center is unaffected, irrespective of whether the migration succeeds or fails.
-
Comprehensive readiness checks: Minimizes errors when migrating between models by providing detailed readiness checks.
-
Real-time monitoring: Tracks the progress of the migration using the user interface.
-
Extensive licensing support: Provides support for all licensing modes such as evaluation, connected, and Specific License Reservation (SLR).




 Feedback
Feedback