Brewing global connectivity and visibility for Nestlé
Nestlé depends on Cisco networking and assurance for connectivity, proactive troubleshooting, and full visibility across 1700 sites.
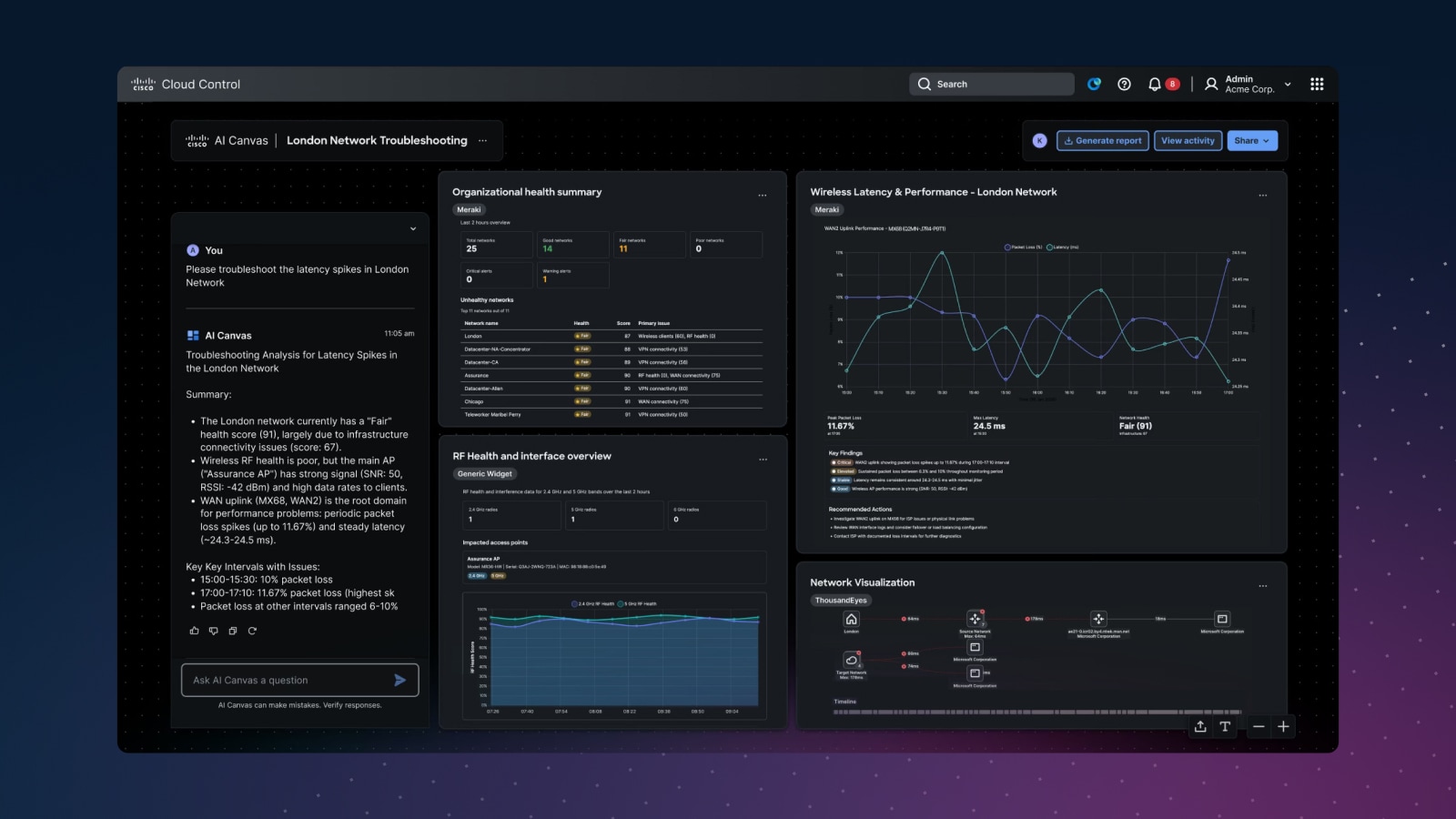




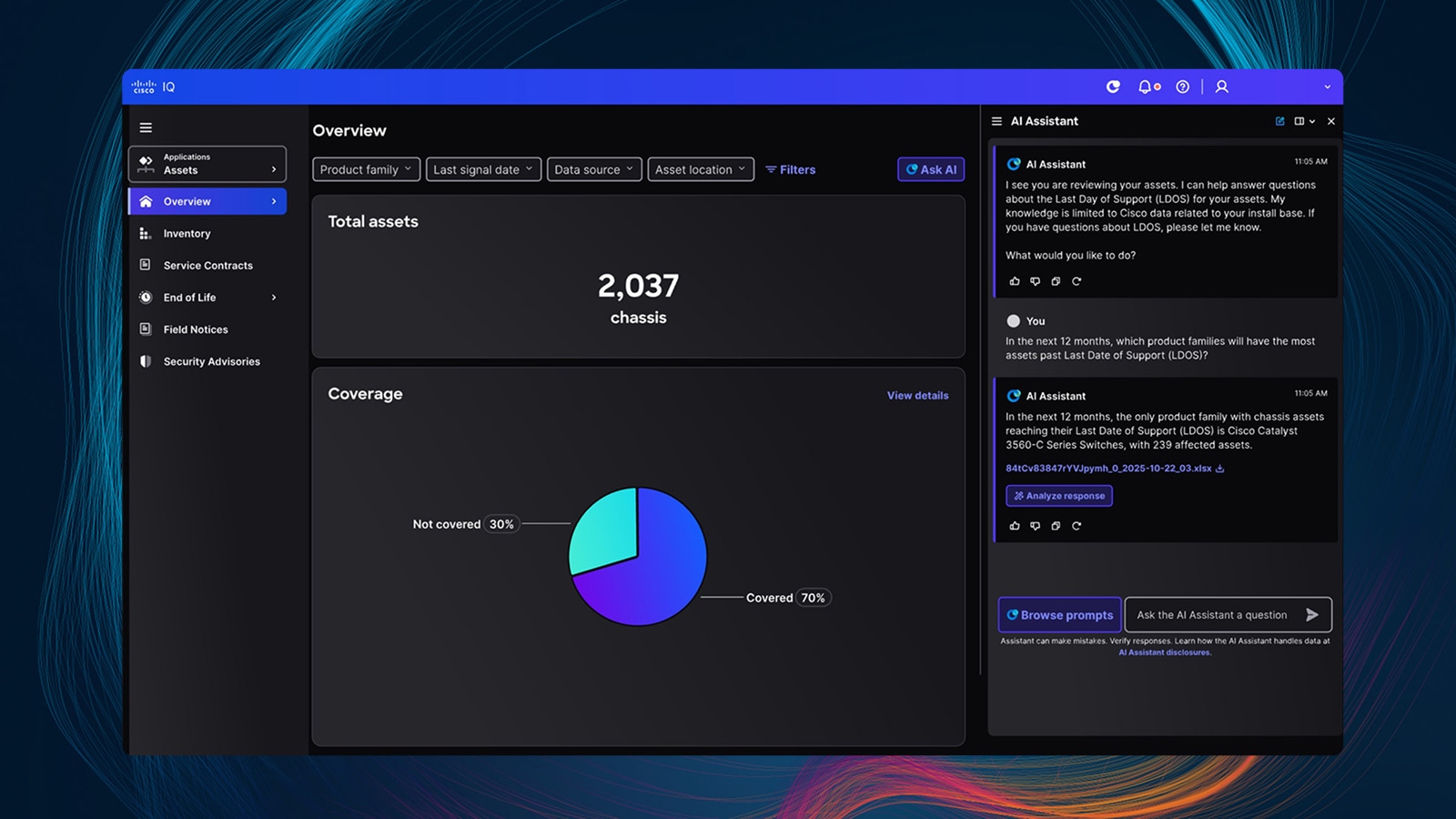
Move beyond visibility to autonomous operations with trusted, policy-bound agents that execute complex workflows at machine speed - while humans govern intent, policy, and risk.
AI-optimized networking that unifies scale, speed, and resilience—so AI workloads run faster, more efficiently, and at global scale.
Purpose-built programmable silicon powers networks with leading performance, efficiency, and scale – optimized for AI workloads across hyperscalers, service providers, enterprises, and data centers.
Deliver zero-trust segmentation and application protection with a highly-distributed security fabric and unified management across data center, cloud, campus, and IoT environments.
Security is embedded at every layer of the network, scaling to support any AI application while simplifying even the most sophisticated campus and enterprise environment.
Redefine edge computing with a full-stack platform that delivers data center performance, modularity, centralized management, and built-in security where you need it most.
Cisco IQ is the unified AI-powered experience that delivers real-time insights, assessments, troubleshooting, learning, automation, and agent-driven guidance to power Cisco support and professional services.
Modernize and transform your data centers to power traditional and AI workloads anywhere—with speed, scale, and flexibility.
Create agile, resilient workplaces that evolve with employee needs and deliver incredible customer experiences everywhere.
Keep your organization securely up and running in the face of any disruption—from cyberattacks to third-party outages and other technical failures.



Modernize and transform your data centers to power traditional and AI workloads anywhere—with speed, scale, and flexibility.

Create agile, resilient workplaces that evolve with employee needs and deliver incredible customer experiences everywhere.

Keep your organization securely up and running in the face of any disruption—from cyberattacks to outages and technical failures.

Nestlé depends on Cisco networking and assurance for connectivity, proactive troubleshooting, and full visibility across 1700 sites.

The McLaren Mastercard Formula 1 Team relies on Cisco networking and security for AI workloads processing race data, fueling 24 races worldwide.

Tripadvisor uses Cisco networking and collaboration to connect global offices—powering collaborative, sustainable work worldwide.