- Preface
- Product Overview
- Basic Router Configuration
- Configuring Ethernet CFM and Y.1731 Performance Monitoring on Layer 3 Interfaces
- Configuring Power Management
- Configuring Security Features
- Configuring Secure Storage
- Configuring Backup Data Lines and Remote Management
- Configuring Ethernet Switches
- Configuring Voice Functionality
- Configuring the Serial Interface
- Configuring Wireless Devices
- Configuring PPP over Ethernet with NAT
- Configuring PPP over ATM with NAT
- Environmental and Power Management
- Configuring a LAN with DHCP and VLANs
- Configuring a VPN Using Easy VPN and an IPSec Tunnel
- Configuring Cisco Multimode G.SHDSL EFM/ATM
- Configuring VDSL2 Bonding and Single-Wire Pair
- Configuring Cisco IOx
- Deployment Scenarios
- Troubleshooting Cisco 800 Series Routers
- Cisco IOS Software Basic Skills
- Concepts
- ROM Monitor
- Index
Cisco 800 Series Integrated Services Routers Software Configuration Guide
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 24, 2014
Chapter: Configuring Backup Data Lines and Remote Management
- Configuring Backup Interfaces
- Configuring Cellular Dial-on-Demand Routing Backup
- Configuring Dial Backup and Remote Management Through the Console or Auxiliary Port
- Configuring Data Line Backup and Remote Management Through the ISDN S/T Port
- Configuring Gigabit Ethernet Failover Media
- Configuring Third-Party SFPs
Configuring Backup
Data Lines and Remote Management
The Cisco 819 series and Cisco 880 Series Integrated Services Routers (ISRs) support backup data connectivity with a backup data line that enables them to mitigate WAN downtime.
 Note | Voice backup is available on router models C881SRST and C888SRST. For information on configuring voice backup, see Configuring Voice Functionality |
Cisco 880 ISRs also support remote management functions as follows:
- Through the auxiliary port on Cisco 880 series ISRs
- Through the ISDN S/T port on the Cisco 880 series ISRs
Cisco 819 ISRs a support remote management functions through the auxiliary port on any Cisco 819 series ISRs.
 Note | On Cisco 819 sries and Cisco880 series ISRs, the console port and the auxiliary port are on the same physical RJ-45 port; therefore, the two ports cannot be activated simultaneously. You must use the CLI to enable the desired function. |
 Note | Cisco 892F ISRs have a Gigabit Ethernet (GE) port that supports copper connections or a small-form-factor pluggable (SFP) port that supports fiber connections and can be configured for failover redundancy when the network goes down. |
This chapter describes configuring backup data lines and remote management in the following sections:
- Configuring Backup Interfaces
- Configuring Cellular Dial-on-Demand Routing Backup
- Configuring Dial Backup and Remote Management Through the Console or Auxiliary Port
- Configuring Data Line Backup and Remote Management Through the ISDN S/T Port
- Configuring Gigabit Ethernet Failover Media
- Configuring Third-Party SFPs
Configuring Backup Interfaces
When the router receives an indication that the primary interface is down, the backup interface becomes enabled. After the primary connection has been restored for a specified period, the backup interface is disabled.
Even if the backup interface comes out of standby mode, the router does not enable the backup interface unless the router receives the traffic specified for that backup interface.
Table below shows the backup interfaces for Cisco 810, Cisco 880 and Cisco 890 series ISRs, along with their port designations. Basic configurations for these interfaces are given in the Configuring WAN Interfaces
|
Router Model Number |
ISDN |
3G |
V.92 |
|---|---|---|---|
|
881G, 886G, 887G, 887VG, 888G |
— |
Yes |
— |
|
886, 886VA, 887, 887V, 888, 888E |
Yes |
— |
— |
|
891 |
— |
— |
Yes |
|
892, 892F |
Yes |
— |
— |
|
819 |
|
Yes |
|
To configure your router with a backup interface, perform these steps, beginning in global configuration mode:
1.
interface
type
number
2.
backup
interface
interface-type
interface-number
3.
exit
DETAILED STEPS
Configuring Cellular Dial-on-Demand Routing Backup
To monitor the primary connection and initiate the backup connection over the cellular interface when needed, the router can use one of the following methods:
- Backup Interface—Backup interface that stays in standby mode until the primary interface line protocol is detected as down and then is brought up. See the Configuring Backup Interfaces.
- Dialer Watch—Backup feature that integrates dial backup with routing capabilities. See the Configuring DDR Backup Using Dialer Watch.
- Floating Static Route—Route through the backup interface has an administrative distance that is greater than the administrative distance of the primary connection route and therefore would not be in the routing table until the primary interface goes down. When the primary interaface goes down, the floating static route is used. See the Configuring DDR Backup Using Floating Static Route.
 Note | You cannot configure a backup interface for the cellular interface and any other asynchronous serial interface. |
- Configuring DDR Backup Using Dialer Watch
- Configuring DDR Backup Using Floating Static Route
- Cellular Wireless Modem as Backup with NAT and IPsec Configuration
Configuring DDR Backup Using Dialer Watch
To initiate dialer watch, you must configure the interface to perform dial-on-demand routing (DDR) and backup. Use traditional DDR configuration commands, such as dialer maps, for DDR capabilities. To enable dialer watch on the backup interface and create a dialer list, use the following commands in interface configuration mode.
or
dialer group dialer group number
1.
configure
terminal
2.
interface
type
number
3.
dialer
watch-group
group-number
4.
dialer
watch-list
group-number
ip
ip-address
address-mask
5.
dialer-list
dialer-group
protocol
protocol-name
{permit
|
deny
|
list
access-list-number |
access-group}
6.
ip
access-list
access-list-number
permit
ip
source
address
7.
interface
cellular
0
8.
Do one of the
following:
DETAILED STEPS
Configuring DDR Backup Using Floating Static Route
To configure a floating static default route on the secondary interface, use the following commands, beginning in the global configuration mode.
 Note | Make sure you have ip classless enabled on your router. |
1.
configure
terminal
2.
ip
route
network-number
network-mask
{ip
address
|
interface}
[administrative
distance] [name
name]
DETAILED STEPS
Cellular Wireless Modem as Backup with NAT and IPsec Configuration
The following example shows how to configure the 3G wireless modem as backup with NAT and IPsec on either GSM or CDMA networks.
 Note | The receive and transmit speeds cannot be configured. The actual throughput depends on the cellular network service. |
Current configuration : 3433 bytes ! version 12.4 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Router ! boot-start-marker boot-end-marker ! ! no aaa new-model ! ! ! ! crypto isakmp policy 1 encr 3des authentication pre-share crypto isakmp key gsm address 128.107.241.234 *** or cdma *** ! ! crypto ipsec transform-set gsm ah-sha-hmac esp-3des *** or cdma *** ! crypto map gsm1 10 ipsec-isakmp *** or cdma1 *** set peer 128.107.241.234 set transform-set gsm *** or cdma *** match address 103 ! ! ! no ip dhcp use vrf connected ip dhcp excluded-address 10.4.0.254 ! ip dhcp pool gsmpool *** or cdmapool *** network 10.4.0.0 255.255.0.0 dns-server 66.209.10.201 66.102.163.231 default-router 10.4.0.254 ! ! ip cef ! no ipv6 cef multilink bundle-name authenticated chat-script gsm "" "atdt*98*1#" TIMEOUT 30 "CONNECT" *** or cdma *** ! ! archive log config hidekeys ! ! controller DSL 0 mode atm line-term cpe line-mode 4-wire standard line-rate 4608 ! ! ! ! interface ATM0 no ip address ip virtual-reassembly load-interval 30 no atm ilmi-keepalive ! interface ATM0.1 point-to-point backup interface Cellular0 ip nat outside ip virtual-reassembly pvc 0/35 pppoe-client dial-pool-number 2 ! ! interface FastEthernet0 ! interface FastEthernet1 ! interface FastEthernet2 ! interface FastEthernet3 ! interface Cellular0 ip address negotiated ip nat outside ip virtual-reassembly encapsulation ppp no ip mroute-cache dialer in-band dialer idle-timeout 0 dialer string gsm *** or cdma *** dialer-group 1 async mode interactive no ppp lcp fast-start ppp chap hostname chunahayev@wwan.ccs ppp chap password 0 B7uhestacr ppp ipcp dns request crypto map gsm1 *** or cdma1 *** ! interface Vlan1 description used as default gateway address for DHCP clients ip address 10.4.0.254 255.255.0.0 ip nat inside ip virtual-reassembly ! interface Dialer2 ip address negotiated ip mtu 1492 ip nat outside ip virtual-reassembly encapsulation ppp load-interval 30 dialer pool 2 dialer-group 2 ppp authentication chap callin ppp chap hostname cisco@dsl.com ppp chap password 0 cisco ppp ipcp dns request crypto map gsm1 *** or cdma1 *** ! ip local policy route-map track-primary-if ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 Dialer2 track 234 ip route 0.0.0.0 0.0.0.0 Cellular0 254 no ip http server no ip http secure-server ! ! ip nat inside source route-map nat2cell interface Cellular0 overload ip nat inside source route-map nat2dsl interface Dialer2 overload ! ip sla 1 icmp-echo 209.131.36.158 source-interface Dialer2 timeout 1000 frequency 2 ip sla schedule 1 life forever start-time now access-list 1 permit any access-list 2 permit 10.4.0.0 0.0.255.255 access-list 3 permit any access-list 101 permit ip 10.4.0.0 0.0.255.255 any access-list 102 permit icmp any host 209.131.36.158 access-list 103 permit ip host 166.136.225.89 128.107.0.0 0.0.255.255 access-list 103 permit ip host 75.40.113.246 128.107.0.0 0.0.255.255 dialer-list 1 protocol ip list 1 dialer-list 2 protocol ip permit ! ! ! route-map track-primary-if permit 10 match ip address 102 set interface Dialer2 ! route-map nat2dsl permit 10 match ip address 101 match interface Dialer2 ! route-map nat2cell permit 10 match ip address 101 match interface Cellular0 ! ! control-plane ! ! line con 0 no modem enable line aux 0 line 3 exec-timeout 0 0 script dialer gsm *** or cdma *** login modem InOut no exec line vty 0 4 login ! scheduler max-task-time 5000 ! webvpn cef end
Configuring Dial Backup and Remote Management Through the Console or Auxiliary Port
When customer premises equipment, such as a Cisco 880 series ISR or Cisco 819 series ISR, is connected to an ISP, an IP address is dynamically assigned to the router, or the IP address may be assigned by the router peer through the centrally managed function. The dial backup feature can be added to provide a failover route in case the primary line fails. The Cisco 880 series ISRs can use the auxiliary port for dial backup and remote management.
Figure below shows the network configuration used for remote management access and for providing backup to the primary WAN line.
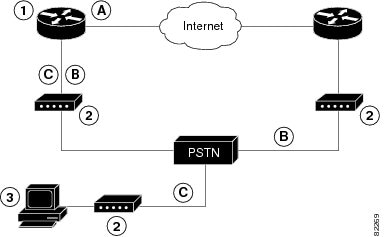
|
1 |
Cisco 880 series router |
A |
Main WAN link; primary connection to Internet service provider |
|
2 |
Modem |
B |
Dial backup; serves as a failover link for Cisco 880 routers when the primary line goes down |
|
3 |
PC |
C |
Remote management; serves as dial-in access to allow changes or updates to Cisco IOS configurations |
To configure dial backup and remote management for these routers, perform these steps, beginning in global configuration mode:
1.
ip
name-server
server-address
2.
ip
dhcp
pool
name
3.
exit
4.
chat-script
script-name
expect-send
5.
interface
type
number
6.
exit
7.
interface
type
number
8.
dialer
watch-group
group-number
9.
exit
10.
ip
nat
inside
source
{list
access-list-number}
{interface
type
number
|
pool
name}
[overload]
11.
ip
route
prefix
mask
{ip-address
|
interface-type
interface-number
[ip-address]
12.
access-list
access-list-number
{deny
|
permit}
source
[source-wildcard]
13.
dialerwatch-list
group-number
{ipip-address
address-mask
|
delay
route-check
initial
seconds
14. line [aux | console | tty | vty] line-number [ending-line-number]
15.
modem
enable
16.
exit
17. line [aux | console | tty | vty] line-number [ending-line-number]
18. flowcontrol {none | software [lock] [in | out] | hardware [in | out]}
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | ip
name-server
server-address
Example: Router(config)# ip name-server 192.168.28.12 |
Enters your ISP DNS IP address.
| ||
| Step 2 | ip
dhcp
pool
name
Example: Router(config)# ip dhcp pool 1 |
Creates a DHCP address pool on the router and enters DHCP pool configuration mode. The name argument can be a string or an integer. Configure the DHCP address pool. For sample commands that you can use in DHCP pool configuration mode, see the Example for specifying an IP address for the ATM interface through PPP and IPCP address negotiation and dial backup. | ||
| Step 3 | exit
Example: Router(config-dhcp)#exit |
Exits config-dhcp mode and enters global configuration mode. | ||
| Step 4 | chat-script
script-name
expect-send
Example: Router(config)# chat-script Dialout ABORT ERROR ABORT BUSY ““ “AT” OK “ATDT 5555102 T” TIMEOUT 45 CONNECT \c |
Configures a chat script used in dial-on-demand routing (DDR) to give commands for dialing a modem and for logging in to remote systems. The defined script is used to place a call over a modem connected to the PSTN. | ||
| Step 5 | interface
type
number
Example: Router(config)# interface Async 1 |
Creates and enters configuration mode for the asynchronous interface. Configure the asynchronous interface. For sample commands that you can use in asynchronous interface configuration mode, see the Example for specifying an IP address for the ATM interface through PPP and IPCP address negotiation and dial backup. | ||
| Step 6 | exit
Example: Router(config-if)# exit |
Enters global configuration mode. | ||
| Step 7 | interface
type
number
Example: Router(config)# interface Dialer 3 |
Creates and enters configuration mode for the dilaer interface. | ||
| Step 8 | dialer
watch-group
group-number
Example:
Router(config-if)# dialer watch-group 1
|
Specifies the group number for the watch list. | ||
| Step 9 | exit
Example: Router(config-if)# exit |
Exits the interface configuration mode. | ||
| Step 10 | ip
nat
inside
source
{list
access-list-number}
{interface
type
number
|
pool
name}
[overload]
Example: Router(config)# ip nat inside source list 101 interface Dialer 3 overload |
Enables dynamic translation of addresses on the inside interface. | ||
| Step 11 | ip
route
prefix
mask
{ip-address
|
interface-type
interface-number
[ip-address]
Example: Router(config)# ip route 0.0.0.0 0.0.0.0 22.0.0.2 |
Sets the IP route to point to the dialer interface as a default gateway. | ||
| Step 12 | access-list
access-list-number
{deny
|
permit}
source
[source-wildcard]
Example: Router(config)# access-list 1 permit 192.168.0.0 0.0.255.255 any |
Defines an extended access list that indicates which addresses need translation. | ||
| Step 13 | dialerwatch-list
group-number
{ipip-address
address-mask
|
delay
route-check
initial
seconds
Example: Router(config)# dialer watch-list 1 ip 22.0.0.2 255.255.255.255 |
Evaluates the status of the primary link, based on the existence of routes to the peer. The address 22.0.0.2 is the peer IP address of the ISP. | ||
| Step 14 | line [aux
|
console
|
tty
|
vty]
line-number
[ending-line-number]
Example: Router(config)# line console 0 |
Enters configuration mode for the line interface. | ||
| Step 15 | modem
enable
Example: Router(config-line)# modem enable |
Switches the port from console to auxiliary port function. | ||
| Step 16 | exit
Example: Router(config-line)# exit |
Exits the configure interface mode. | ||
| Step 17 | line [aux
|
console
|
tty
|
vty]
line-number
[ending-line-number]
Example: Router(config)# line aux 0 |
Enters configuration mode for the auxiliary interface. | ||
| Step 18 | flowcontrol
{none
|
software
[lock]
[in
|
out]
|
hardware
[in
|
out]}
Example: Router(config)# flowcontrol hardware |
Enables hardware signal flow control. |
Example for specifying an IP address for the ATM interface through PPP and IPCP address negotiation and dial backup
The following configuration example specifies an IP address for the ATM interface through PPP and IPCP address negotiation and dial backup over the console port.
! ip name-server 192.168.28.12 ip dhcp excluded-address 192.168.1.1 ! ip dhcp pool 1 import all network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 ! ! Need to use your own correct ISP phone number. modemcap entry MY-USER_MODEM:MSC=&F1S0=1 chat-script Dialout ABORT ERROR ABORT BUSY ““ “AT” OK “ATDT 5555102\T” TIMEOUT 45 CONNECT \c ! ! ! ! interface vlan 1 ip address 192.168.1.1 255.255.255.0 ip nat inside ip tcp adjust-mss 1452 hold-queue 100 out ! ! Dial backup and remote management physical interface. interface Async1 no ip address encapsulation ppp dialer in-band dialer pool-member 3 async default routing async dynamic routing async mode dedicated ppp authentication pap callin ! interface ATM0 mtu 1492 no ip address no atm ilmi-keepalive pvc 0/35 pppoe-client dial-pool-number 1 ! dsl operating-mode auto ! ! Primary WAN link. interface Dialer1 ip address negotiated ip nat outside encapsulation ppp dialer pool 1 ppp authentication pap callin ppp pap sent-username account password 7 pass ppp ipcp dns request ppp ipcp wins request ppp ipcp mask request ! ! Dialer backup logical interface. interface Dialer3 ip address negotiated ip nat outside encapsulation ppp no ip route-cache no ip mroute-cache dialer pool 3 dialer idle-timeout 60 dialer string 5555102 modem-script Dialout dialer watch-group 1 ! ! Remote management PC IP address. peer default ip address 192.168.2.2 no cdp enable ! ! Need to use your own ISP account and password. ppp pap sent-username account password 7 pass ppp ipcp dns request ppp ipcp wins request ppp ipcp mask request ! ! IP NAT over Dialer interface using route-map. ip nat inside source route-map main interface Dialer1 overload ip nat inside source route-map secondary interface Dialer3 overload ip classless ! ! When primary link is up again, distance 50 will override 80 if dial backup ! has not timed out. Use multiple routes because peer IP addresses are alternated ! among them when the CPE is connected. ip route 0.0.0.0 0.0.0.0 64.161.31.254 50 ip route 0.0.0.0 0.0.0.0 66.125.91.254 50 ip route 0.0.0.0 0.0.0.0 64.174.91.254 50 ip route 0.0.0.0 0.0.0.0 63.203.35.136 80 ip route 0.0.0.0 0.0.0.0 63.203.35.137 80 ip route 0.0.0.0 0.0.0.0 63.203.35.138 80 ip route 0.0.0.0 0.0.0.0 63.203.35.139 80 ip route 0.0.0.0 0.0.0.0 63.203.35.140 80 ip route 0.0.0.0 0.0.0.0 63.203.35.141 80 ip route 0.0.0.0 0.0.0.0 Dialer1 150 no ip http server ip pim bidir-enable ! ! PC IP address behind CPE. access-list 101 permit ip 192.168.0.0 0.0.255.255 any access-list 103 permit ip 192.168.0.0 0.0.255.255 any ! ! Watch multiple IP addresses because peers are alternated ! among them when the CPE is connected. dialer watch-list 1 ip 64.161.31.254 255.255.255.255 dialer watch-list 1 ip 64.174.91.254 255.255.255.255 dialer watch-list 1 ip 64.125.91.254 255.255.255.255 ! ! Dial backup will kick in if primary link is not available ! 5 minutes after CPE starts up. dialer watch-list 1 delay route-check initial 300 dialer-list 1 protocol ip permit ! ! Direct traffic to an interface only if the dialer is assigned an IP address. route-map main permit 10 match ip address 101 match interface Dialer1 ! route-map secondary permit 10 match ip address 103 match interface Dialer3 ! ! Change console to aux function. line con 0 exec-timedout 0 0 modem enable stopbits 1 line aux 0 exec-timeout 0 0 ! To enable and communicate with the external modem properly. script dialer Dialout modem InOut modem autoconfigure discovery transport input all stopbits 1 speed 115200 flowcontrol hardware line vty 0 4 exec-timeout 0 0 password cisco login ! scheduler max-task-time 5000 end
Configuring Data Line Backup and Remote Management Through the ISDN S/T Port
Cisco 880 series routers can use the ISDN S/T port for remote management. Figure 1 and Figure 2 show two typical network configurations that provide remote management access and backup for the primary WAN line. In Figure 1, the dial backup link goes through a customer premises equipment (CPE) splitter, a digital subscriber line access multiplexer (DSLAM), and a central office (CO) splitter before connecting to the ISDN switch. In Figure 2, the dial backup link goes directly from the router to the ISDN switch.
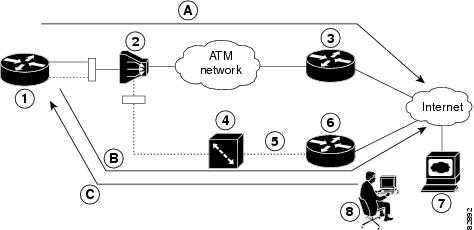
|
1 |
Cisco 880 series router |
A |
Primary DSL interface, FE interface (Cisco 881 router) |
|
2 |
DSLAM |
B |
Dial backup and remote management through the ISDN interface (ISDN S/T port); serves as a failover link when the primary line goes down |
|
3 |
ATM aggregator |
||
|
4 |
ISDN switch |
||
|
5 |
ISDN |
C |
Provides administrator with remote management capability through the ISDN interface when the primary DSL link is down; serves as dial-in access to allow changes or updates to Cisco IOS configuration |
|
6 |
ISDN peer router |
||
|
7 |
Web server |
||
|
8 |
Administrator |
— |
— |
|
1 |
PC |
A |
Primary DSL interface |
|
2 |
Cisco 880 series ISR |
B |
Dial backup and remote management through the ISDN interface (ISDN S/T port); serves as a failover link when the primary line goes down |
|
3 |
DSLAM |
||
|
4 |
Aggregator |
||
|
5 |
ISDN switch |
C |
Provides administrator with remote management capability through the ISDN interface when the primary DSL link is down; serves as dial-in access to allow changes or updates to Cisco IOS configuration |
|
6 |
Web server |
||
|
7 |
Administrator |
To configure dial backup and remote management through the ISDN S/T port of your router, perform the following procedures:
Configuring ISDN Settings
 Note | Traffic of interest must be present to activate the backup ISDN line by means of the backup interface and floating static routes methods. Traffic of interest is not needed for the dialer watch to activate the backup ISDN line. |
To configure your router ISDN interface for use as a backup interface, perform these steps, beginning in global configuration mode:
1.
isdn
switch-type
switch-type
2.
interface
type
number
3.
encapsulation
encapsulation-type
4.
dialer
pool-member
number
5.
isdn
switch-type
switch-type
6.
exit
7.
interface
dialer
dialer-rotary-group-number
8.
ip
address
negotiated
9.
encapsulation
encapsulation-type
10.
dialer
pool
number
11.
dialer
string
dial-string#[:isdn-subaddress]
12.
dialer-group
group-number
13.
exit
14.
dialer-list
dialer-group
protocol
protocol-name
{permit
|
deny
|
list
access-list-number
|
access-group}
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | isdn
switch-type
switch-type
Example: Router(config)# isdn switch-type basic-net3 |
Specifies the ISDN switch type. The example specifies a switch type used in Australia, Europe, and the United Kingdom. For details on other supported switch types, see the Cisco IOS Dial Technologies Command Reference . |
| Step 2 | interface
type
number
Example: Router(config)# interface bri 0 |
Enters configuration mode for the ISDN BRI. |
| Step 3 | encapsulation
encapsulation-type
Example: Router(config-if)# encapsulation ppp |
Sets the BRI0 interface encapsulation type. |
| Step 4 | dialer
pool-member
number
Example: Router(config-if)# dialer pool-member 1 |
Specifies the dialer pool membership. |
| Step 5 | isdn
switch-type
switch-type
Example: Router(config-if)# isdn switch-type basic-net3 |
Specifies the ISDN switch type. |
| Step 6 | exit
Example: Router(config-if)# exit |
Exits configuration interface mode and enters global configuration mode. |
| Step 7 | interface
dialer
dialer-rotary-group-number
Example: Router(config)# interface dialer 0 |
Creates a dialer interface (numbered 0 to 255) and enters interface configuration mode. |
| Step 8 | ip
address
negotiated
Example: Router(config-if)# ip address negotiated |
Specifies that the IP address for the interface is obtained through PPP/IPCP (IP Control Protocol) address negotiation. The IP address is obtained from the peer. |
| Step 9 | encapsulation
encapsulation-type
Example: Router(config-if)# encapsulation ppp |
Sets the encapsulation type to PPP for the interface. |
| Step 10 | dialer
pool
number
Example: Router(config-if)# dialer pool 1 |
Specifies the dialer pool to be used. In the example, the dialer pool 1 setting associates the dialer 0 interface with the BRI0 interface because the BRI0 dialer pool-member value is 1. |
| Step 11 | dialer
string
dial-string#[:isdn-subaddress]
Example: Router(config-if)# dialer string 384040 |
Specifies the telephone number to be dialed. |
| Step 12 | dialer-group
group-number
Example: Router(config-if)# dialer group 1 |
Assigns the dialer interface to a dialer group (1–10). |
| Step 13 | exit
Example: Router(config-if)# exit |
Exits dialer 0 interface configuration mode, and enters global configuration mode. |
| Step 14 | dialer-list
dialer-group
protocol
protocol-name
{permit
|
deny
|
list
access-list-number
|
access-group}
Example: Router(config)# dialer-list 1 protocol ip permit |
Creates a dialer list for packets of interest to be forwarded through the specified interface dialer group. In the example, dialer-list 1 corresponds to dialer-group 1. For details about this command and additional parameters that can be set, see Cisco IOS Dial Technologies Command Reference . |
Configuring Aggregator and ISDN Peer Router
The ISDN peer router is any router that has an ISDN interface and can communicate through a public ISDN network to reach your Cisco router ISDN interface. The ISDN peer router provides Internet access for your Cisco router during the ATM network downtime.
The aggregator is typically a concentrator router where your Cisco router ATM PVC terminates. In the following configuration example, the aggregator is configured as a PPPoE server.
! This portion of the example configures the aggregator. vpdn enable no vpdn logging ! vpdn-group 1 accept-dialin protocol pppoe virtual-template 1 ! interface Ethernet3 description “4700ref-1” ip address 40.1.1.1 255.255.255.0 media-type 10BaseT ! interface Ethernet4 ip address 30.1.1.1 255.255.255.0 media-type 10BaseT ! interface Virtual-Template1 ip address 22.0.0.2 255.255.255.0 ip mtu 1492 peer default ip address pool adsl ! interface ATM0 no ip address pvc 1/40 encapsulation aal5snap protocol pppoe ! no atm limi-keepalive ! ip local pool adsl 22.0.0.1 ip classless ip route 0.0.0.0 0.0.0.0 22.0.0.1 50 ip route 0.0.0.0 0.0.0.0 30.1.1.2.80 ! This portion of the example configures the ISDN peer. isdn switch-type basic-net3 ! interface Ethernet0 ip address 30.1.1.2 255.0.0.0 ! interface BRI0 description “to 836-dialbackup” no ip address encapsulation ppp dialer pool-member 1 isdn switch-type basic-net3 ! interface Dialer0 ip address 192.168.2.2 255.255.255.0 encapsulation ppp dialer pool 1 dialer string 384020 dialer-group 1 peer default ip address pool isdn ! ip local pool isdn 192.168.2.1 ip http server ip classless ip route 0.0.0.0 0.0.0.0 192.168.2.1 ip route 40.0.0.0 255.0.0.0 30.1.1.1 ! dialer-list 1 protocol ip permit!
Configuring Gigabit Ethernet Failover Media
Cisco 892F routers have a Gigabit Ethernet (GE) port that supports copper connections or a small-form-factor pluggable (SFP) port that supports fiber connections. Media can be configured for failover redundancy when the network goes down.
To assign primary and secondary failover media on the GE-SFP port, perform these steps, beginning in global configuration mode.
1.
hostname
name
2.
enable
secret
password
3.
interface
gigabitethernet
slot/port
4.
media-type
{sfp
|
rj45}
auto-failover
5.
exit
DETAILED STEPS
Configuring Auto-Detect
The Auto-Detect feature is enabled if media-type is not configured. This feature automatically detects which media is connected and links up. If both media are connected, whichever media comes up first is linked up.
 Note | The Auto-Detect feature only works with 1000 Base SFPs. This feature does not detect 100 Base SFPs. |
To configure the Auto-Detect feature, perform the following steps, starting in global configuration mode:
1.
interface
gigabitethernet
slot/port
2.
no
media-type
3.
exit
DETAILED STEPS
Configuring Third-Party SFPs
Small Form-Factor Pluggables (SFPs) that are not Cisco certified are called third-party SFPs. Cisco approved means the SFPs have undergone rigorous testing with Cisco products and the SFPs are guaranteed to have 100% compatibility.
Third-party SFPs are manufactured by companies that are not on the Cisco-approved Vendor List (AVL). Currently, Cisco ISR G2 routers support only Cisco-approved SFPs. From Release 15.3(2)T, Cisco ISR G2 routers recognize third-party SFPs.
 Note | Cisco does not provide any kind of support for the third-party SFPs because they are not validated by Cisco. |
 Note |
|
1.
enable
2.
configure
terminal
3.
service
unsupported-transceiver
4.
interface
type
slot/subslot/port
number
5.
media-type
sfp
6.
speed
value
7.
shutdown
8.
no
shutdown
9.
exit
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | enable
Example: Router> enable |
Enables the privileged EXEC mode. Enter your password if prompted. | ||
| Step 2 | configure
terminal
Example: Router# configure terminal |
Enters the global configuration mode. | ||
| Step 3 | service
unsupported-transceiver
Example: Router(config)# service unsupported-transceiver |
Enables third-party SFP support. | ||
| Step 4 | interface
type
slot/subslot/port
number
Example: Router(config)# interface ethernet 0/3/0 |
Selects an interface to configure. | ||
| Step 5 | media-type
sfp
Example: Router(config-if)# media-type sfp |
Changes media type to SFP. | ||
| Step 6 | speed
value
Example: Router(config-if)# speed 100 |
Configures the speed of the interface.
| ||
| Step 7 | shutdown
Example: Router(config-if)# shutdown |
Disables the interface, changing its state from administratively UP to administratively DOWN. | ||
| Step 8 | no
shutdown
Example: Router(config-if)# no shutdown |
Enables the interface, changing its state from administratively DOWN to administratively UP. | ||
| Step 9 | exit
Example: Router(config-if)# exit Router(config)# |
Exits the configuration mode and returns the global configuration mode. |
Example for Configuring Third-Party SFPs
This example shows how to configure a third-party SFP on a Cisco ISR G2 Series Router:
Router# configure terminal Router(config-if)# service unsupported-transceiver Router(config)# interface ethernet 0/3/0 Router(config-if)# media-type sfp Router(config-if)# speed 100 Router(config-if)# shutdown Router(config-if)# no shutdown Router(config-if)# exit Router(config)# exit
 Feedback
Feedback