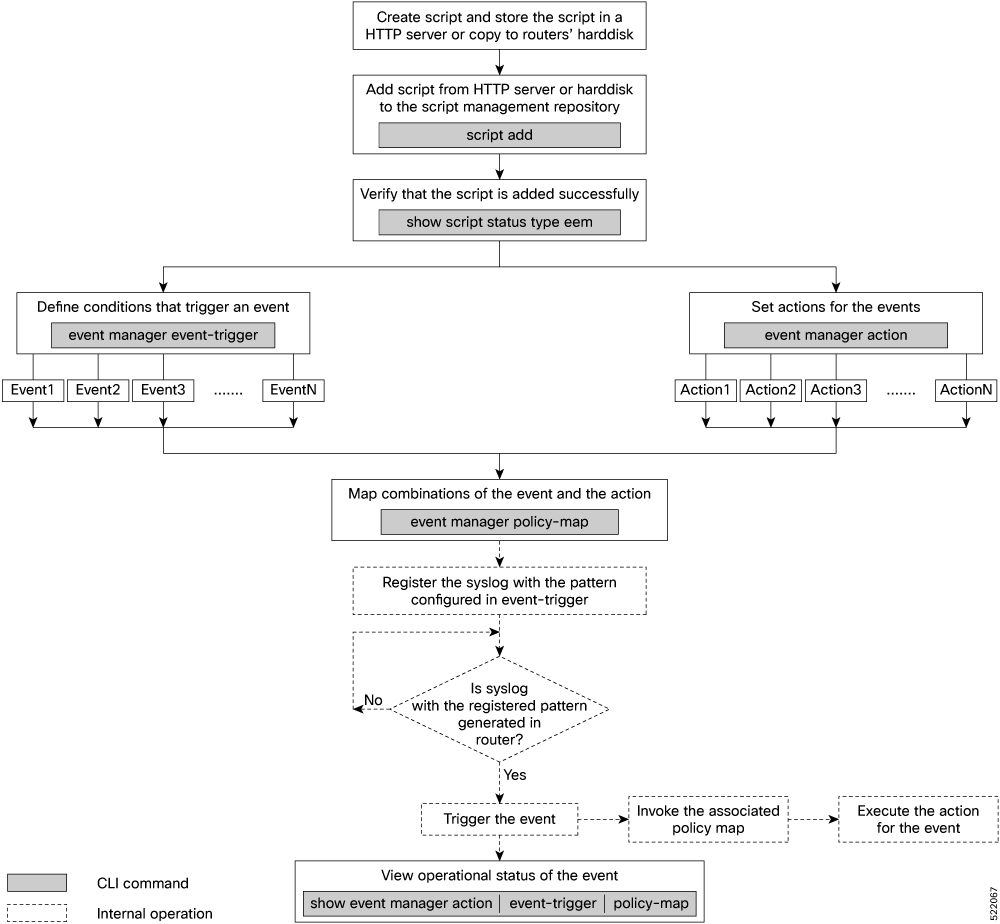
EEM scripts
A EEM script is an automation tool that
-
monitors real-time system activity and events,
-
executes defined actions when specific conditions are met, and
-
streamlines troubleshooting and operational workflows.
EEM scripts act based on significant system occurrences—such as log messages, interface states, or telemetry changes—not limited to errors. For example, you can automate actions like enforcing LACP dampening if a bundle interface flaps multiple times within seconds by temporarily disabling the interface.
Administrators can define events and actions separately, then link them together using policy maps. A single event and action pair can be reused across multiple policies, and a policy map can contain up to five actions. EEM scripts may be written in Python 3.5 or TCL; script policies can be configured using either Command Line Interface (CLI) or NETCONF RPCs.
-
Scripts are stored and managed in subdirectories based on type within the router's script management repository.
-
You can map the same event and action in up to 64 policy maps for extensive automation reuse.
-
For python scripting, only specific packages are supported; TCL scripts are also an option for event managers.
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
EEM script execution logs |
Release 26.1.1 |
Introduced in this release on: Fixed Systems (8200 [ASIC: Q100, Q200, P100], 8700 [ASIC: P100, K100], 8010 [ASIC: A100]); Centralized Systems (8600 [ASIC: Q200]); Modular Systems (8800 [LC ASIC: Q100, Q200, P100]) Timely and successful execution of an EEM script ensures that intended network actions are effectively carried out, allowing the network to respond appropriately to changing conditions. A newly added syslog entry now indicates the start of an EEM script execution, including the script's name and process ID. |
|
EEM scripts |
Release 25.4.1 |
Introduced in this release on: Fixed Systems (8700 [ASIC: K100])(select variants only*) This feature enables you to automate system monitoring and responses using EEM scripts, streamlining troubleshooting and operational workflows. EEM scripts monitor real-time events—such as log messages, interface changes, or telemetry updates—and execute predefined actions when specific conditions are met. Events and actions are defined separately and linked in policy maps, with each map supporting up to five actions. You can reuse the same event-action pair in up to 64 policy maps. Scripts are stored by type on the router and can be written in Python 3.5 or TCL, managed via CLI or NETCONF RPCs. This feature is now supported on:
|
 Feedback
Feedback