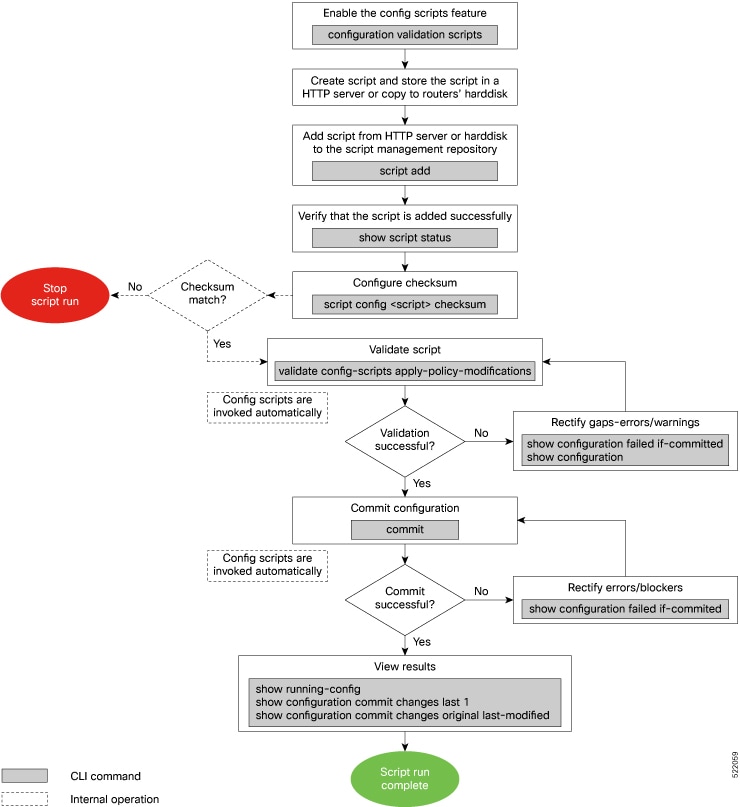
Config scripts
A config script is an automated script that
-
validates, enforces rules, and can modify device configuration changes during the commit process,
-
analyzes proposed configuration changes, blocks invalid configurations, or issues warnings as needed, and
-
can automatically adjust or supplement configuration items to ensure compliance and reduce repetitive manual tasks.
Config scripts generate system log messages that aid in auditing and troubleshooting configuration changes.
Functions of config scripts
When you commit or validate a configuration change, the system invokes each of the active scripts to validate that change. Config scripts can perform these actions:
-
Analyze the proposed new configuration.
-
If the configuration is invalid, block the commit by returning an error message along with the set of configuration items to which it relates.
-
Return a warning message with the related details but does not block the commit operation.
-
Modify the configuration to be included in the commit operation to make the configuration valid, or to simplify certain repetitive configuration tasks. For example, where a value needs duplicating between one configuration item and another configuration item.
-
Generate system log messages for in-depth analysis of the configuration change. This log also helps in troubleshooting a failed commit operation.

 Feedback
Feedback