Feature History for SGACL
This table provides release and platform support information for the features explained in this module.
These features are available in all the releases subsequent to the one they were introduced in, unless noted otherwise.
|
Release |
Feature Name and Description |
Supported Platform |
|---|---|---|
|
Cisco IOS XE 17.18.1 |
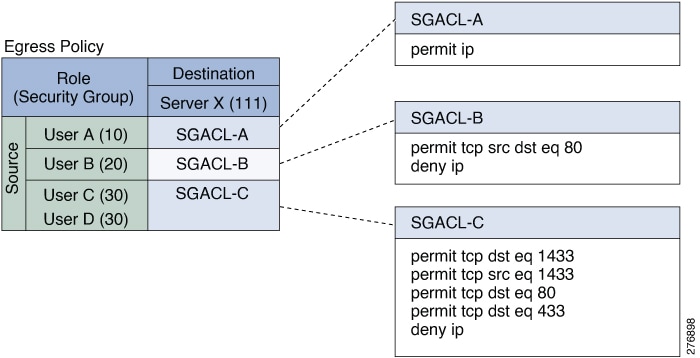
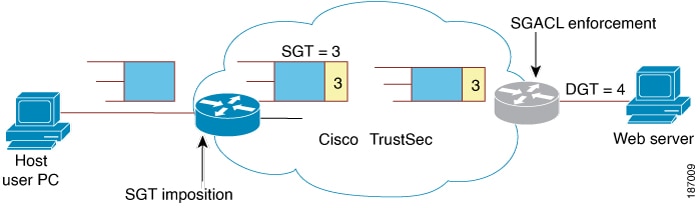
SGACL: Security Group Access Control Lists (SGACLs) enable administrators to enforce policies that control what operations users can perform based on their assigned security groups and the resources they are accessing. |
Cisco C9350 Series Smart Switches Cisco C9610 Series Smart Switches |

 Feedback
Feedback