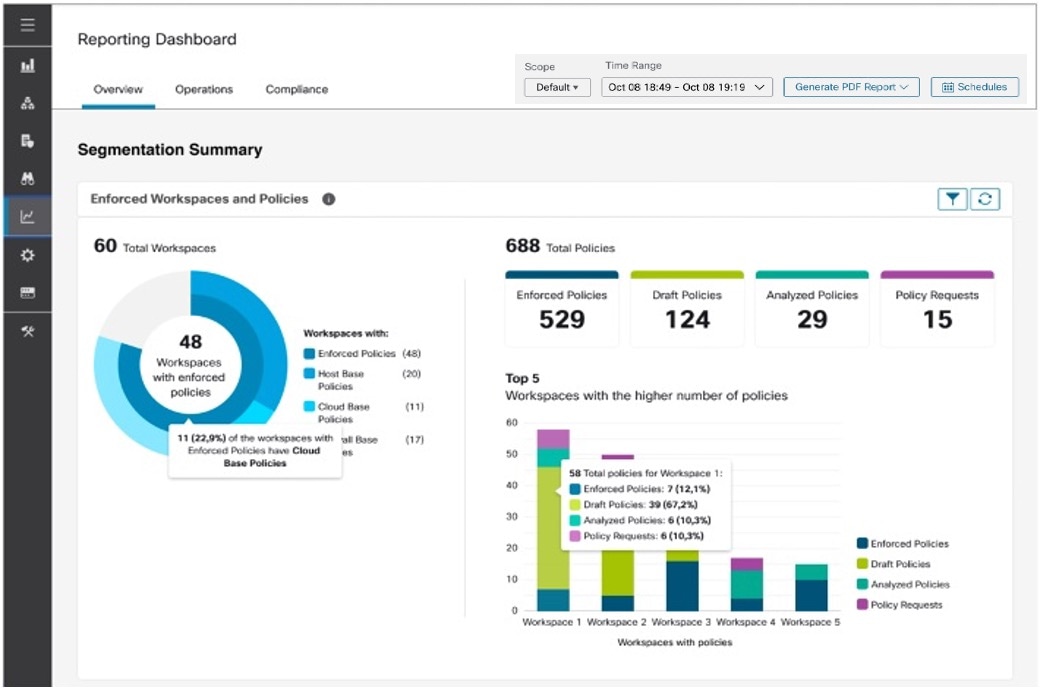
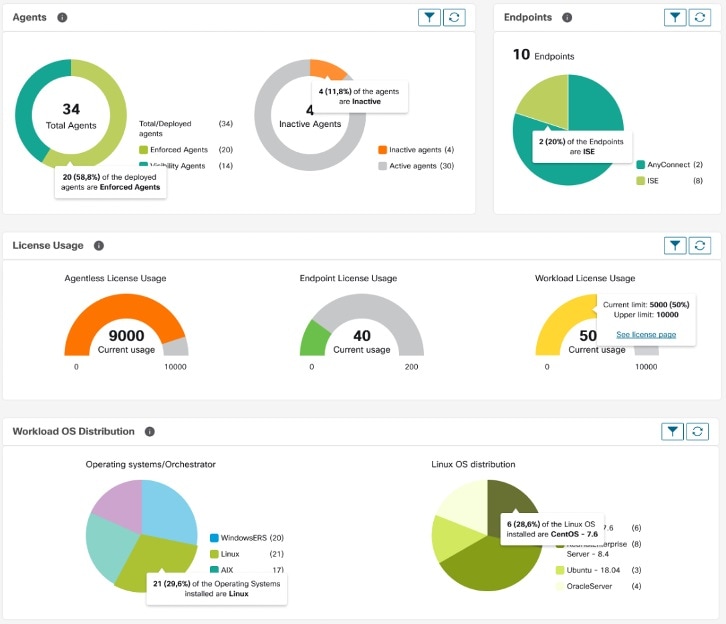
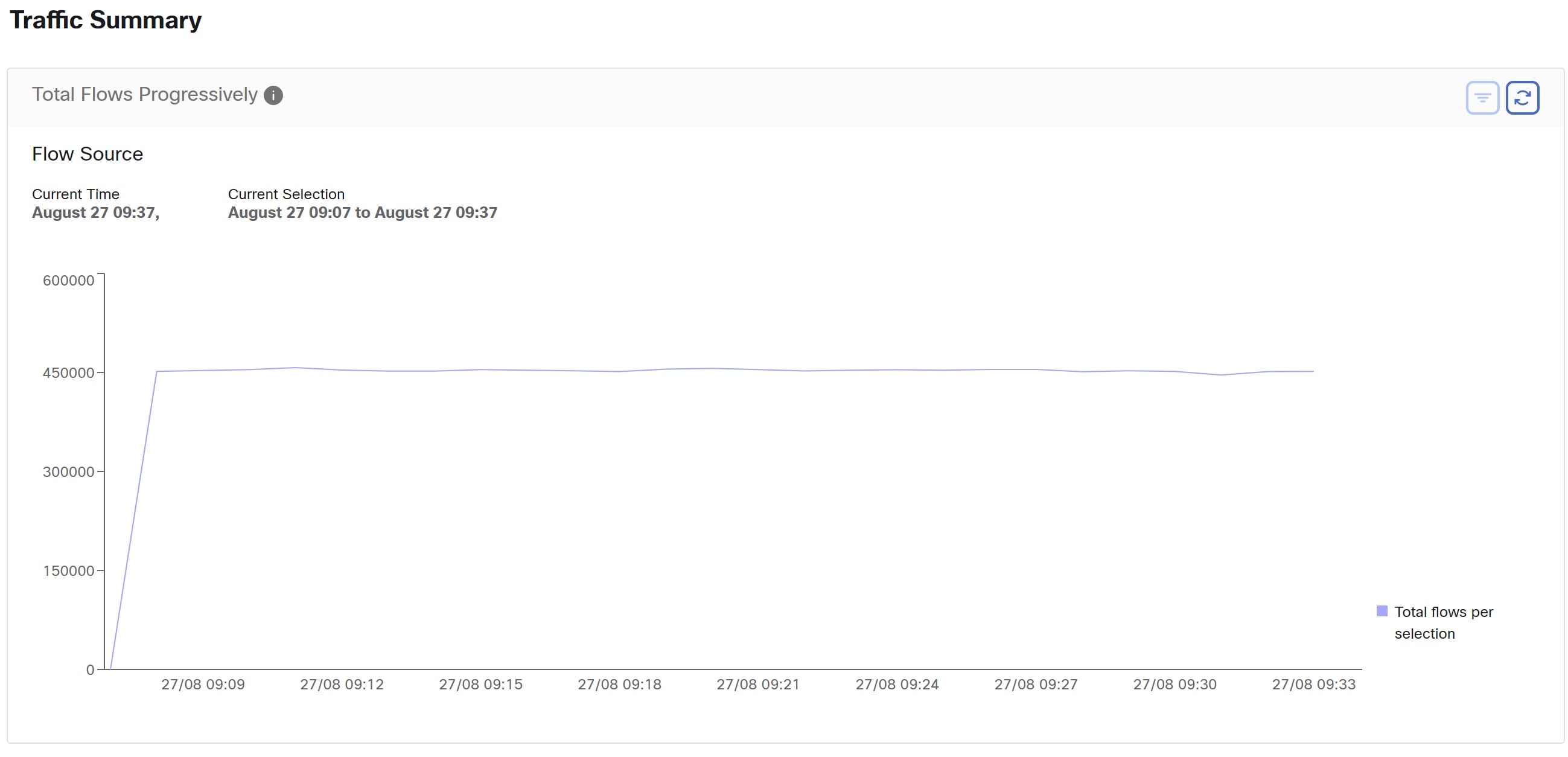
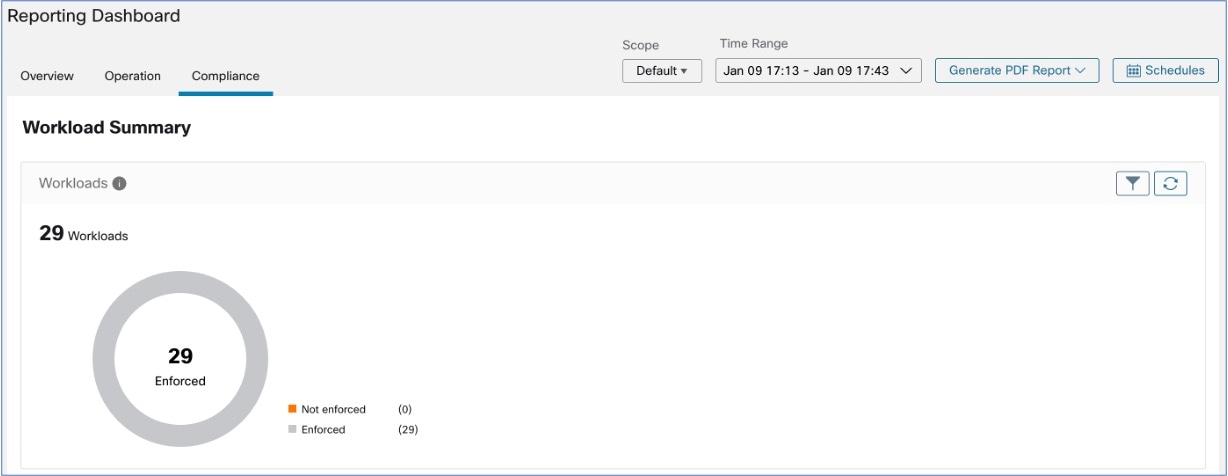
Reporting Dashboard
The Reporting dashboard provides visual representations of critical workflow status, troubleshooting capabilities, and report creation functionalities. From the navigation pane, choose to access the dashboard.
The sections below provide an overview of the reports and how to schedule and email reports.
Schedule Email Reports
To generate a report, choose from either of the options:
-
Download: After you generate a report, you can download and save a copy of the report for future reference.
-
Email: If you choose the option to email reports, an email will be triggered to recipients with the attached report.
-
Schedule: You have two options to choose from to schedule a report.
-
Daily
-
Weekly
To schedule a report, enter the schedule details to trigger the report. Select Weekly or Daily, enetr the day and time, and the email addresses of the recipients. Click Create Scheduled PDF to save the details.
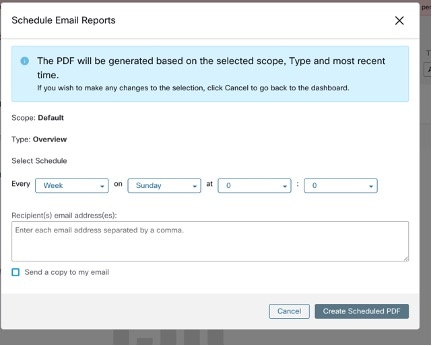
-
 Note |
If the report scheduling fails, check the schedule for any incorrect email address or incorrectly entered date and time. |
 Note |
Without SMTP server configuration, email scheduling to send reports will be affected. |
To access the report schedules that were generated earlier, choose Generated Reports > Schedules. If the report scheduling fails, check the schedule for any incorrect email address or incorrect date, time.
 Note |
The maximum number of schedules that you can store in the scheduling dashboard is five. |




 Feedback
Feedback