Vulnerability Dashboard
Select a scoring system and the scope to view the CVEs according to the severity and other attribute details.
The different scoring systems used in Secure Workload are:
-
Common Vulnerability Scoring System (CVSS): CVSS is a qualitative measurement of severity of the CVEs, from low to critical. The scores help you to prioritize responses for the most critical severities. CVSS V3 is the most recent version of the CVSS scoring mechanism.
-
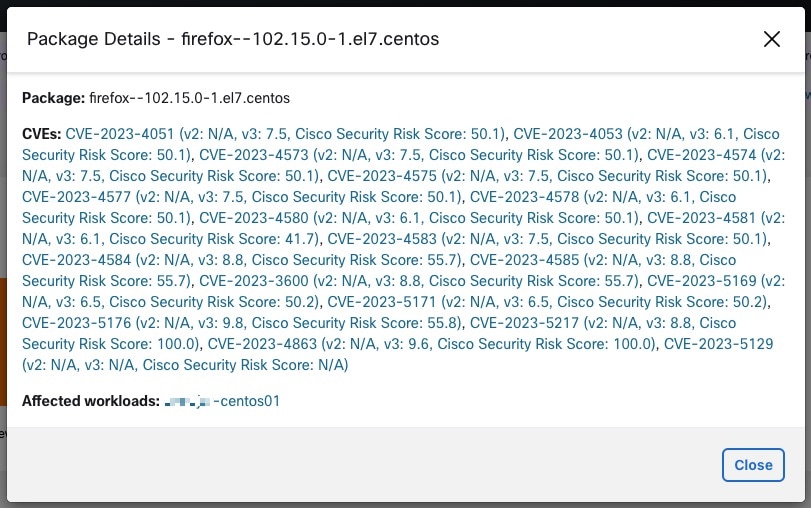
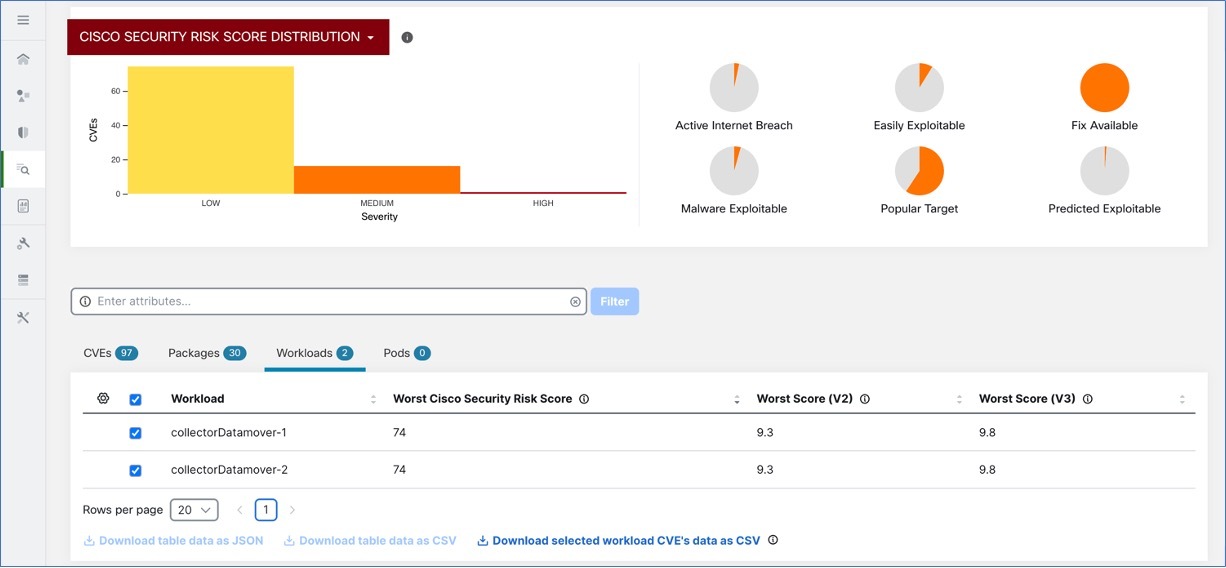
Cisco Security Risk Score: The Cisco Security Risk Score provides accurate risk assessments of the CVEs in your workloads. The risk scores help you to comprehend your organization’s risk profile and help your security team prioritize remediation strategies.
|
Scoring System |
Attributes |
|---|---|
|
Cisco Security Risk Score |
|
|
CVSS V3 |
|
|
CVSS V2 |
|
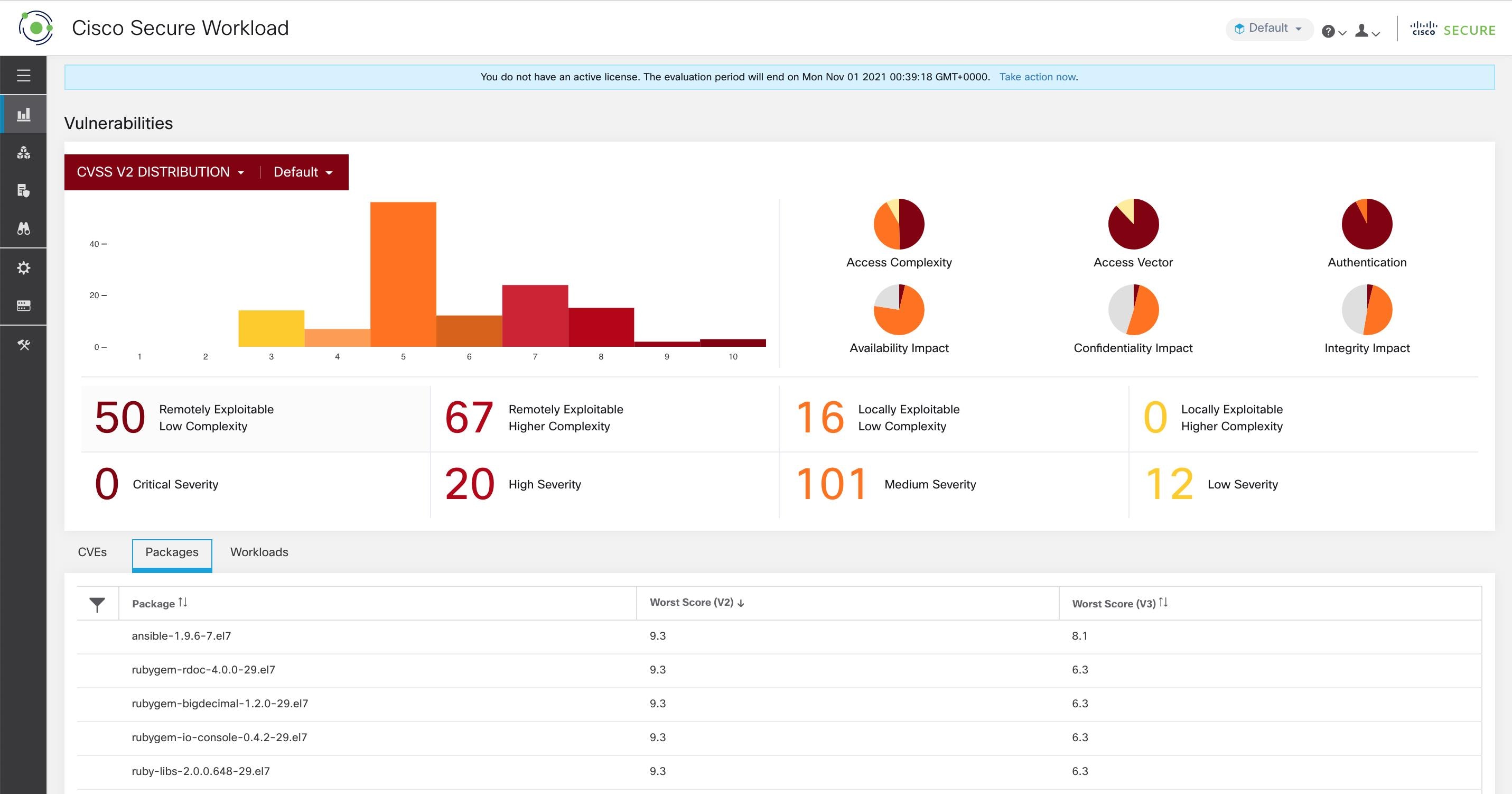
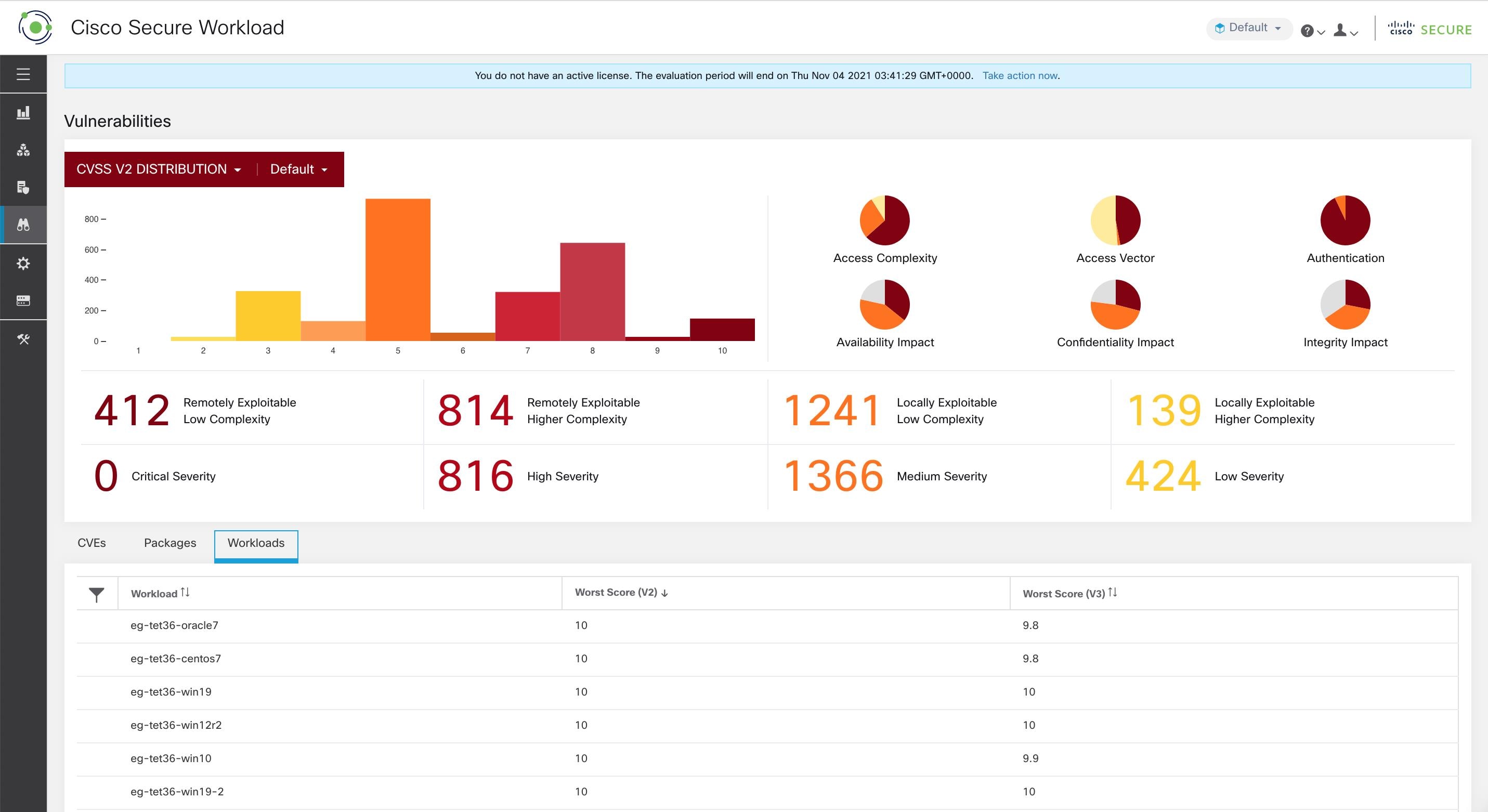
The dashboard highlights the distribution of vulnerabilities in the chosen scope and displays vulnerabilities by different attributes, for example, complexity of exploits, can the vulnerabilities be exploited over the network or does attacker need local access to the workload. Furthermore, the statistics can filter out vulnerabilities that are remotely exploitable and have lowest complexity to exploit.
The CVE threat databases in Secure Workload are updated every 24 hours by retrieving the latest CVE details from popular sources such as NIST, Microsoft, Oracle, and Cisco Vulnerability Management. If the Secure Workload cluster is in an air-gapped environment, the CVE threat data packs must be downloaded from https://updates.tetrationcloud.com and uploaded in Secure Workload.
The CVE threat databases in Secure Workload are updated every 24 hours by retrieving the latest CVE details from popular sources such as NIST, Microsoft, and Oracle. If the Secure Workload cluster is in an air-gapped environment, the CVE threat data packs must be downloaded from https://updates.tetrationcloud.com and uploaded in Secure Workload.
By using the scores and the required attributes of the known CVEs in your workloads, you can:
-
Create inventory filters. See Inventory Filters.
-
Configure microsegmentation policies to block the external communication from the impacted workloads and publish virtual patching rules to Cisco Secure Firewall Management Center.
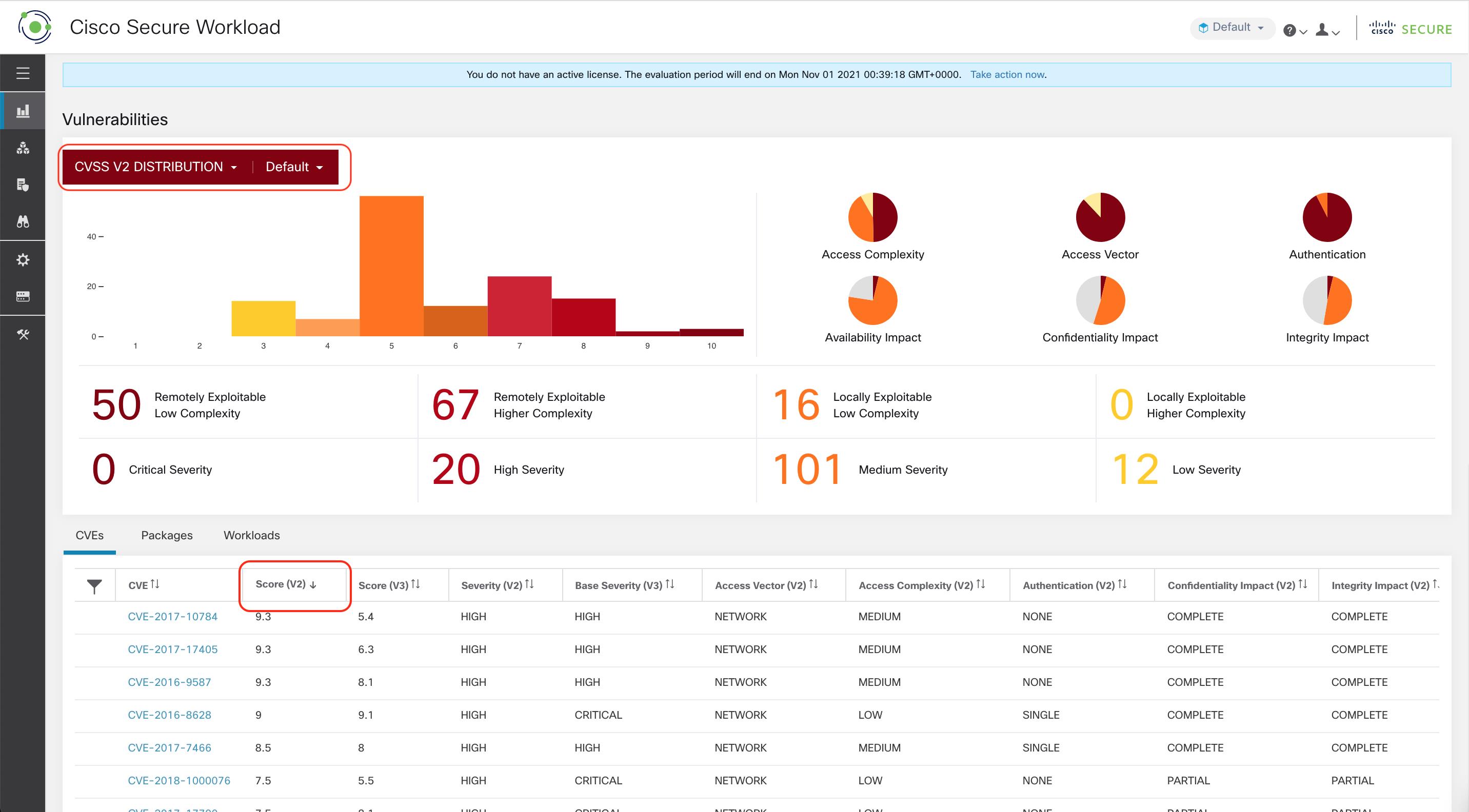
To view the Vulnerabilities page, from the navigation pane, choose . The vulnerabilities identified using the different scoring system are displayed. The graphs and widgets display the number of vulnerabilities with the associated risk level and attributes depending on the scoring systemts to identify workloads which requires immediate attention and the packages which needs to be patched immediately to reduce the risks.
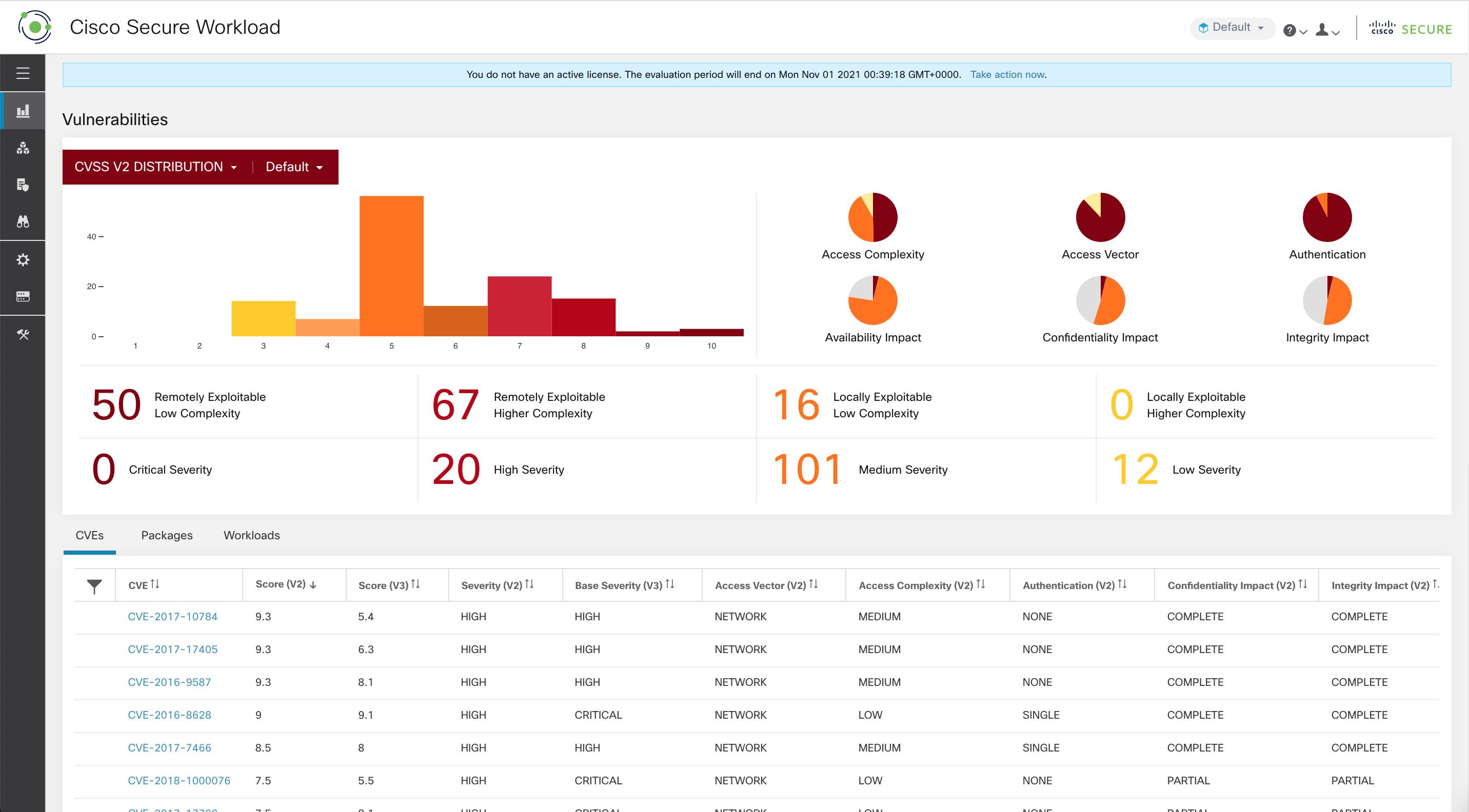
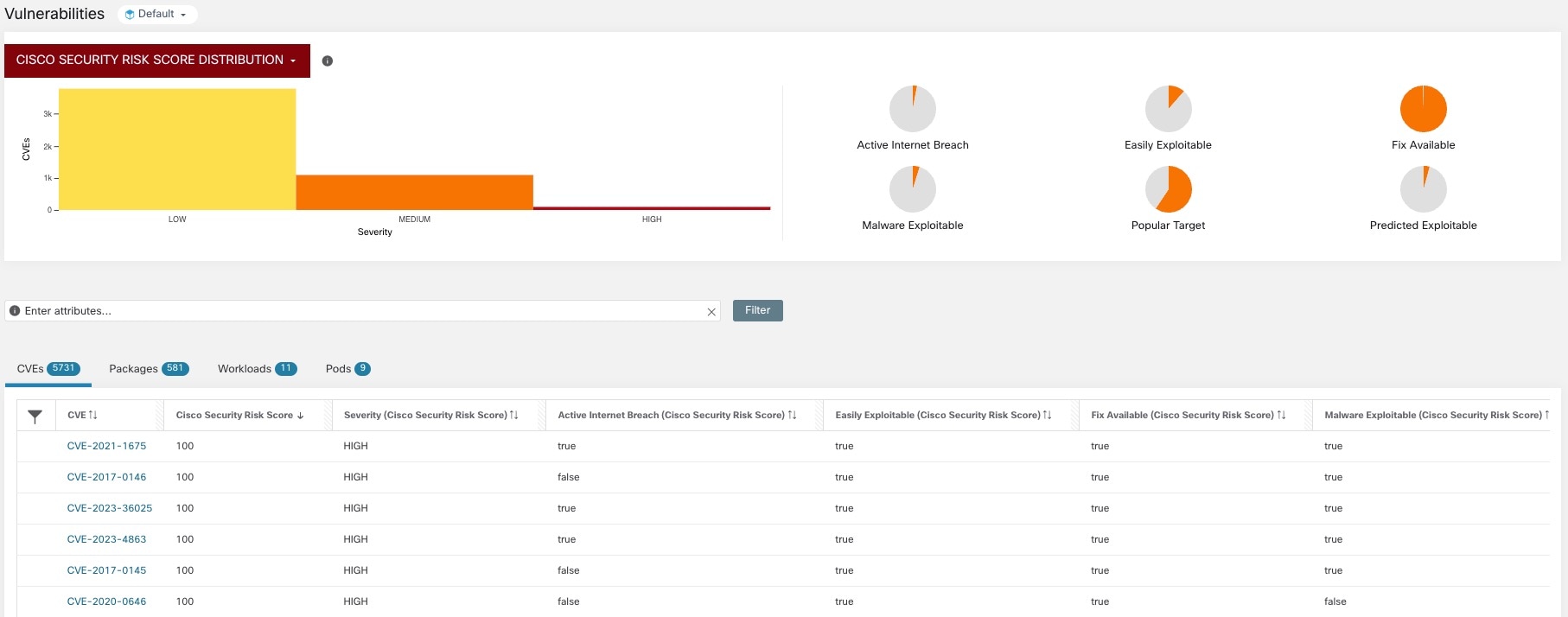
The following tabs are filtered based on the selected portion of the graphs or widgets:
-
The CVEs tab highlight the vulnerabilities that requires attention in the selected scope.
-
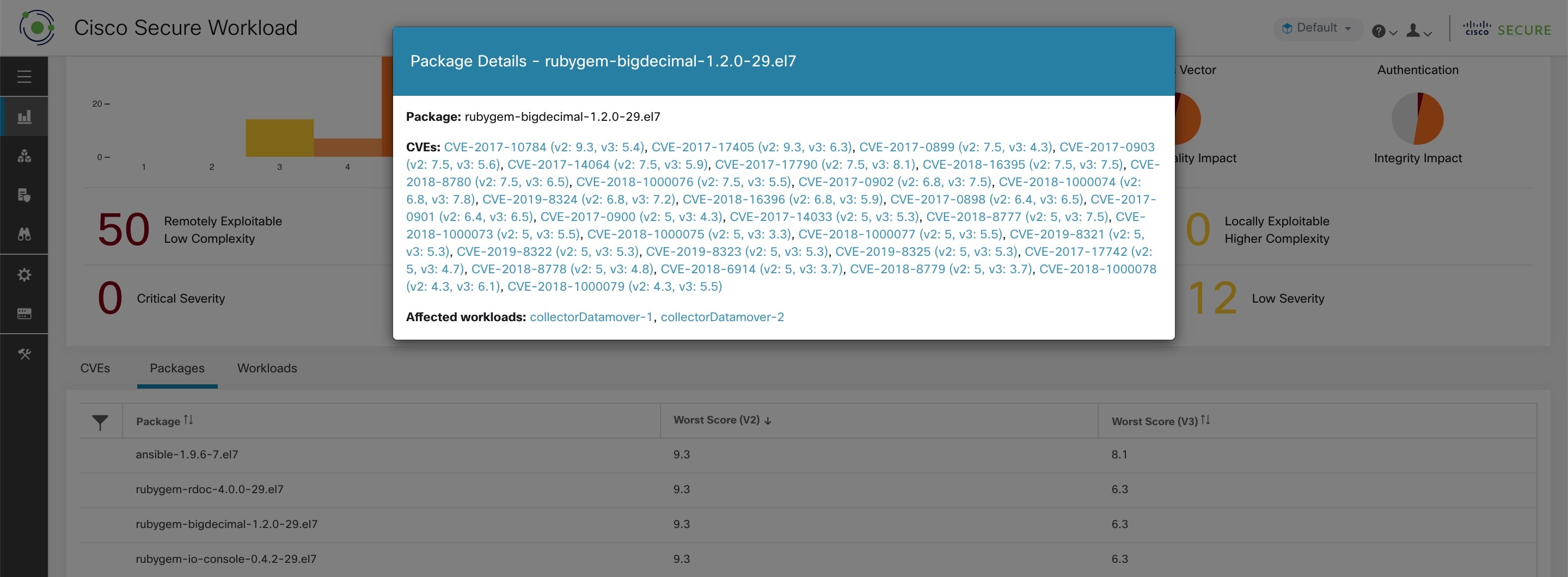
The Packages tab lists the packages that must be patched.
-
The Workloads tab lists the impacted workloads in the selected scope.
-
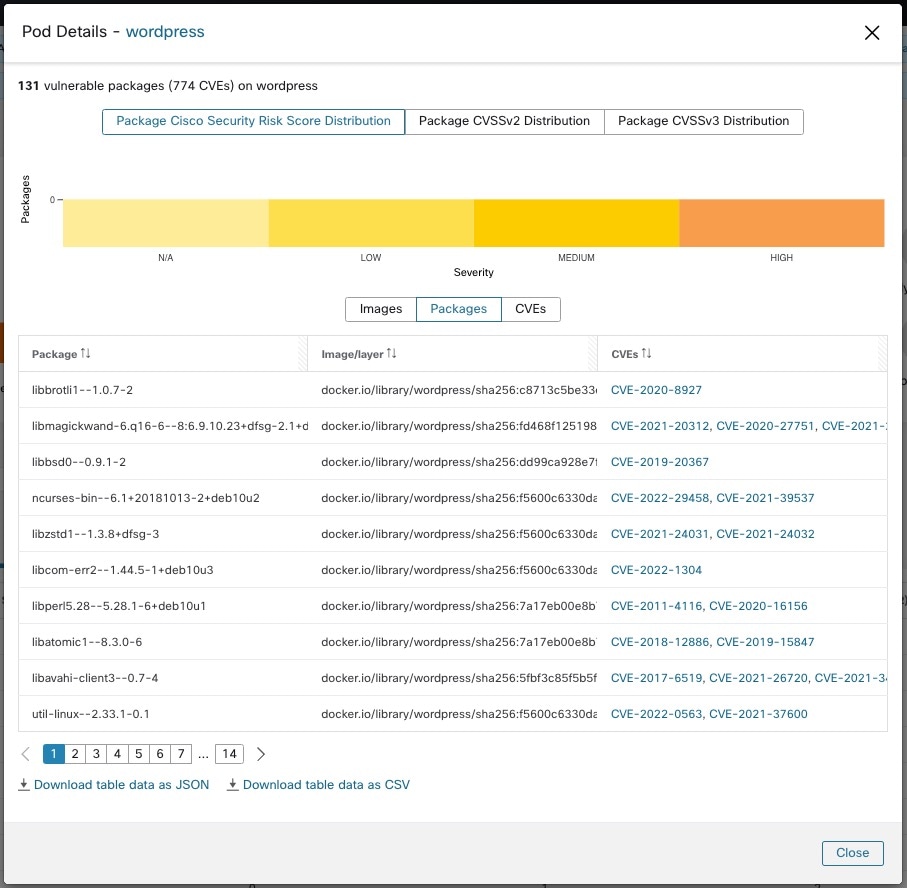
The Pods tabs lists the impacted Kubernetes pods in the selected scope.
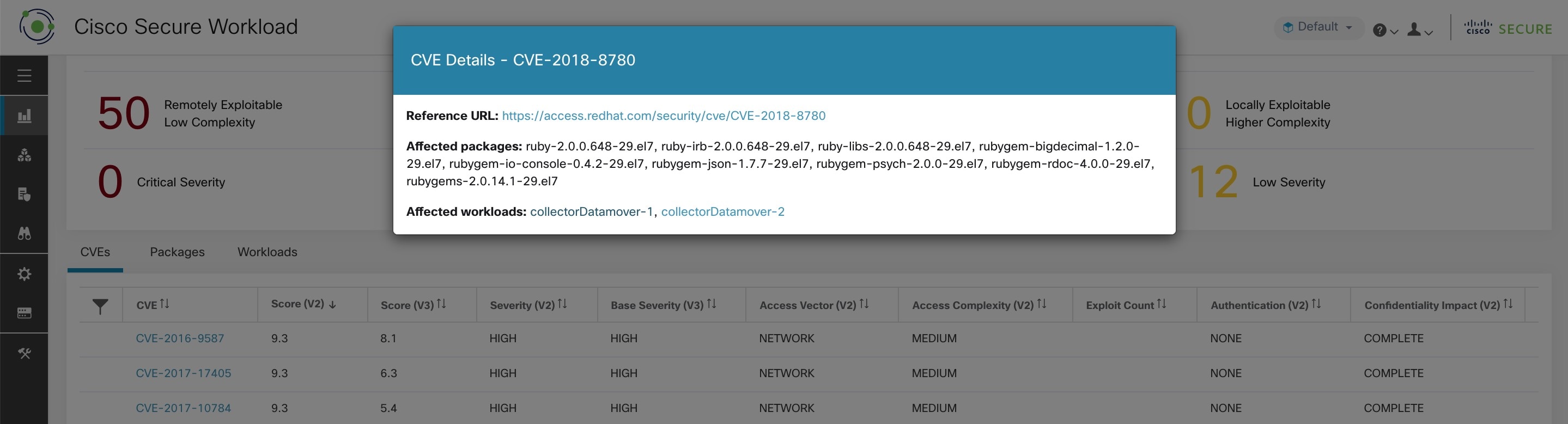
For details, click the required row in the tabs. For example, click a row in the Packages tab to view the workloads where the package or version is installed and the associated vulnerabilities for the package. The displayed lists can be downloaded as a JSON or CSV file using the download links.

 Feedback
Feedback