Alert Types and Publishers
Alerts in Secure Workload categorizes alerts into various types, including critical system alerts, policy violations, and anomalies detected in workload behavior. Each type serves a specific purpose in maintaining security integrity. Processes are defined for setting up Alerts, from defining alert criteria to specifying notification methods (for example, email or SMS). Alerts are integrated with existing monitoring solutions to provide a comprehensive view of the security landscape.
Alerts in Secure Workload consist of the following components:
-
Alert Visibility
-
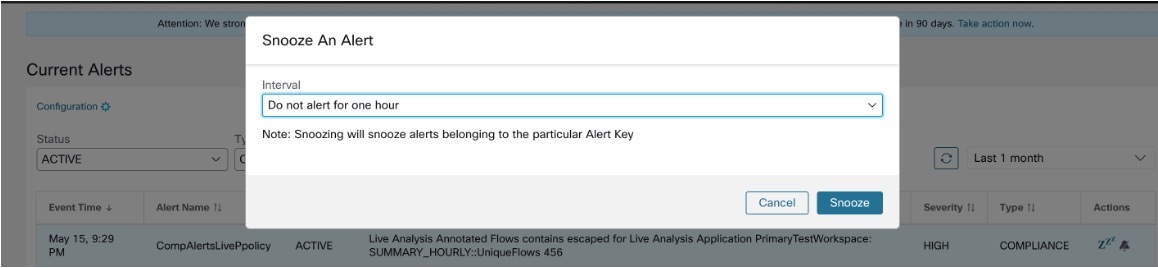
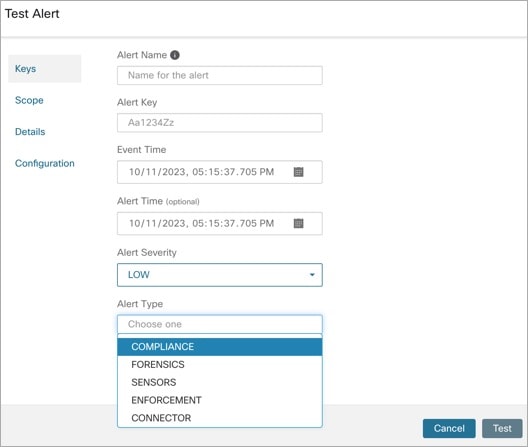
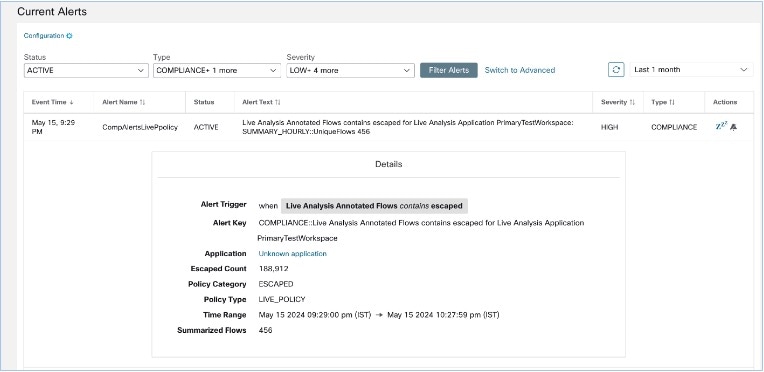
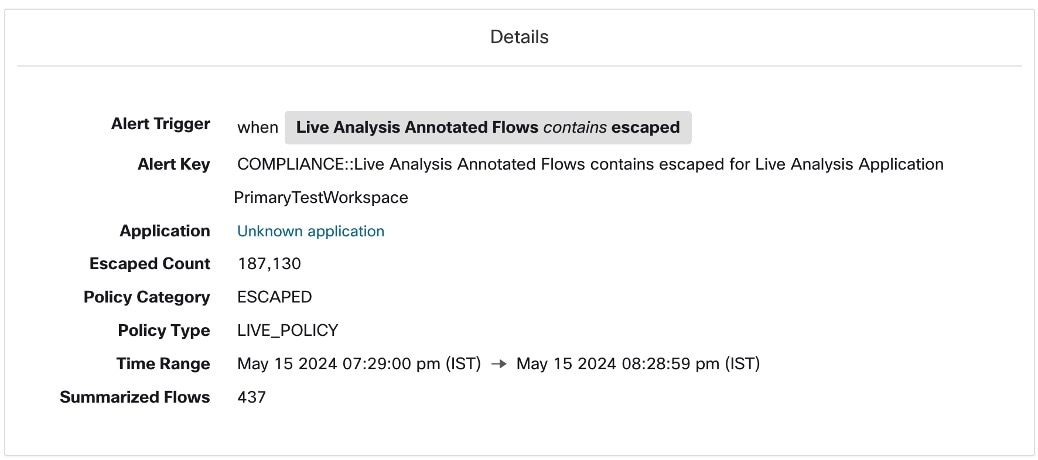
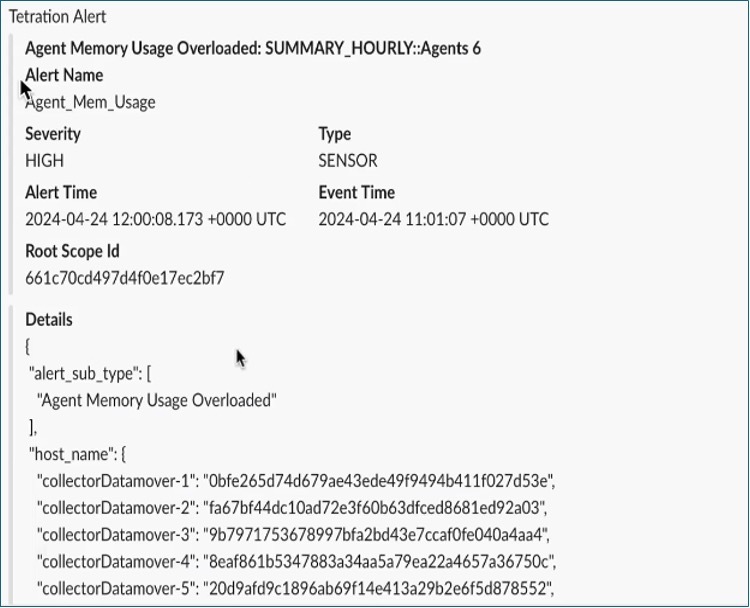
Current Alerts: From the navigation pane, choose . Preview of alerts is sent to a Data Tap.
Figure 1. Current Alerts 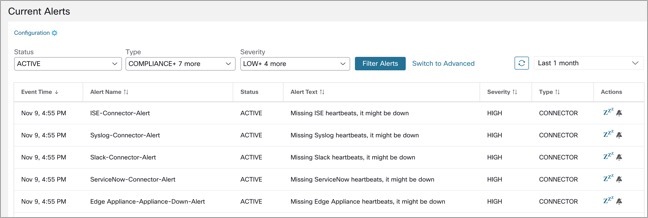
-
-
Alert Sources and Configuration:
-
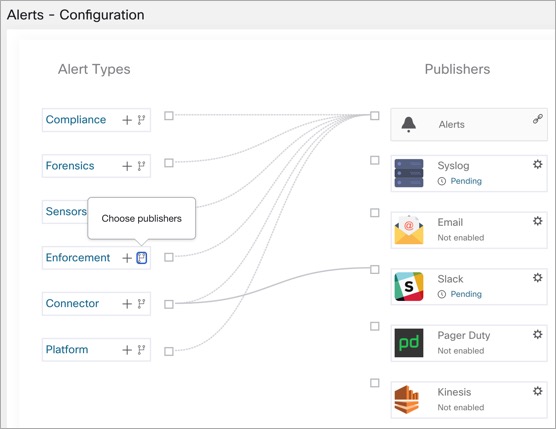
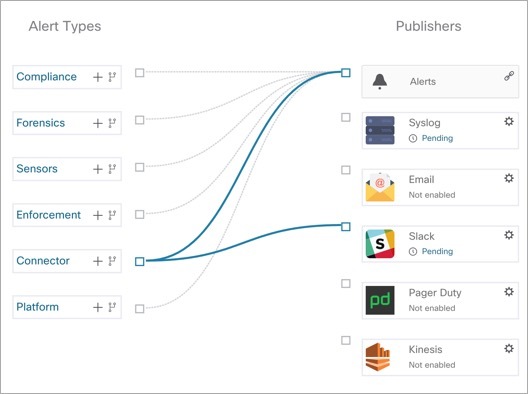
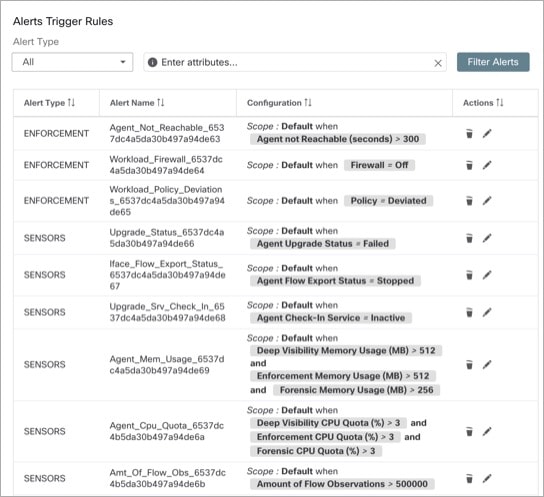
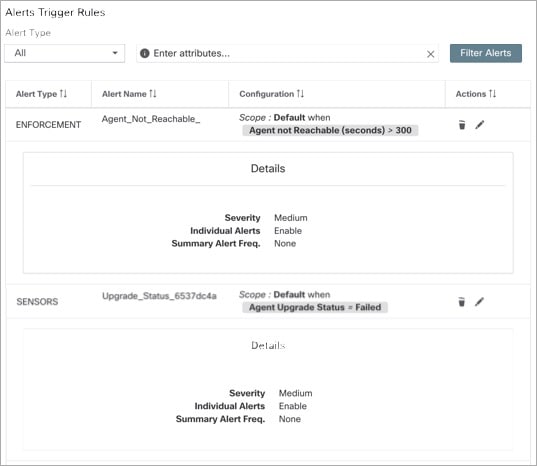
Alerts - Configuration: From the navigation pane, choose . Both alert configurations that are configured using the common modal and alert publisher, and notifier settings are displayed.
Figure 2. Alerts - Configuration 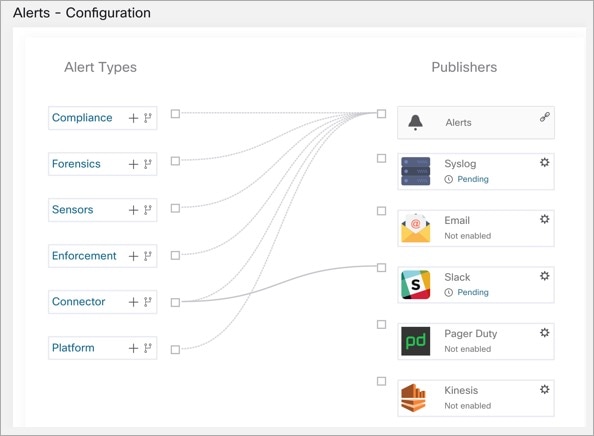
-
-
Send Alerts:
-
Alerts App: An implicit Secure Workload app that sends generated alerts to a configured Data Tap. The Alerts App handles features such as Snooze and Mute.
-
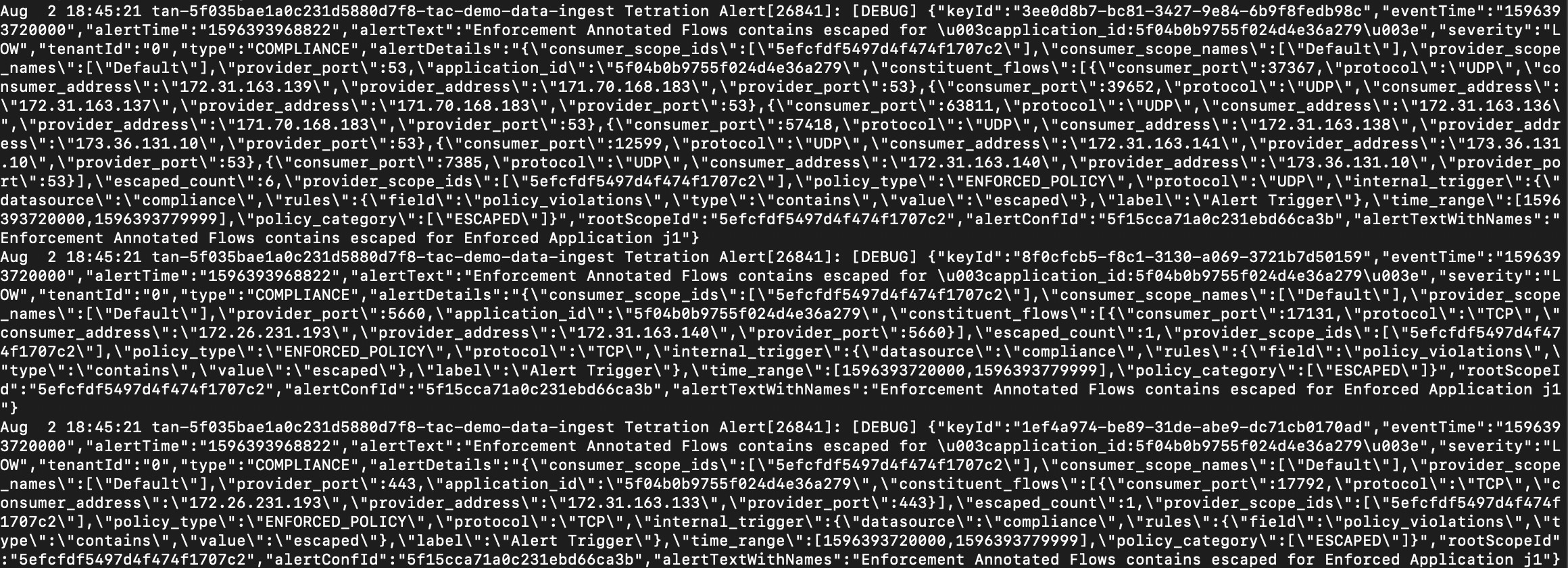
Alerts Publisher: Limits the number of alerts that are displayed and pushes alerts to Kafka (MDT or DataTap) for external consumption.
-
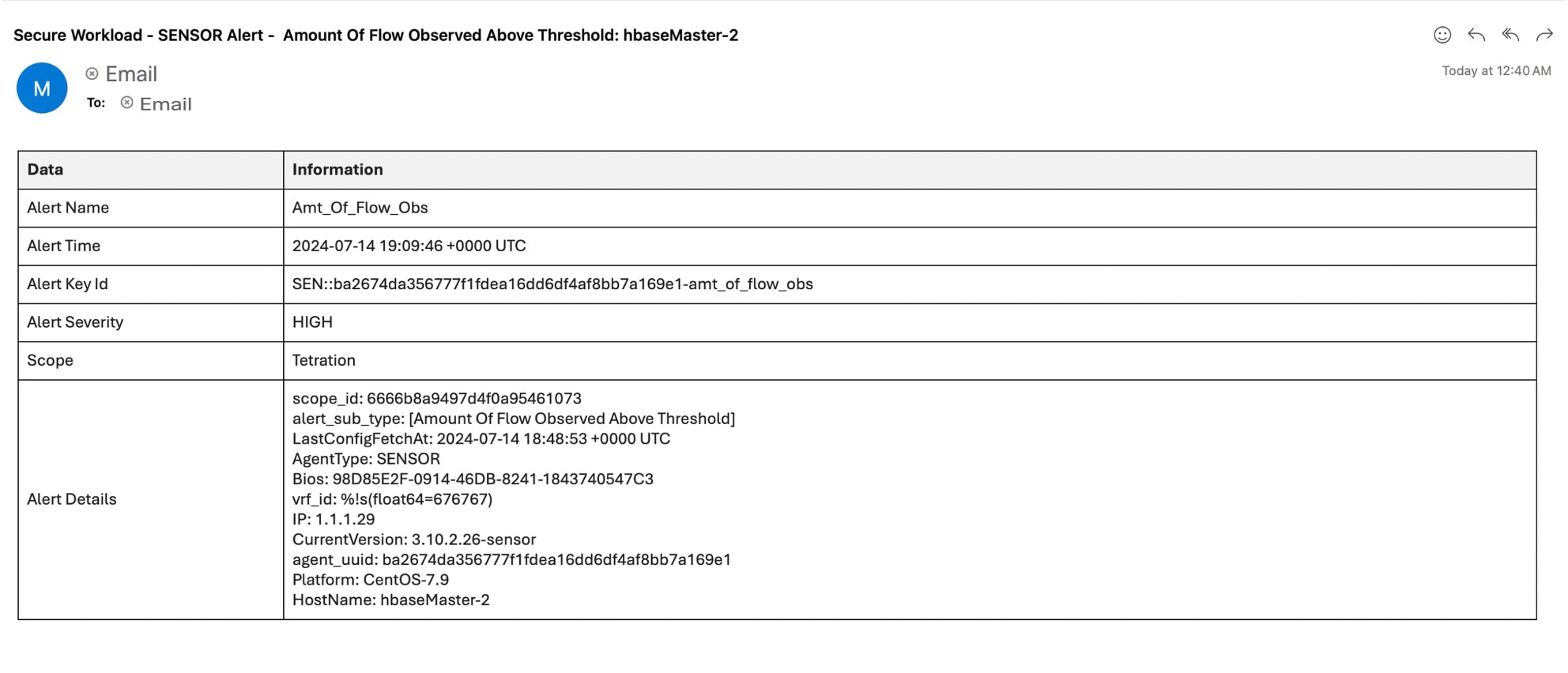
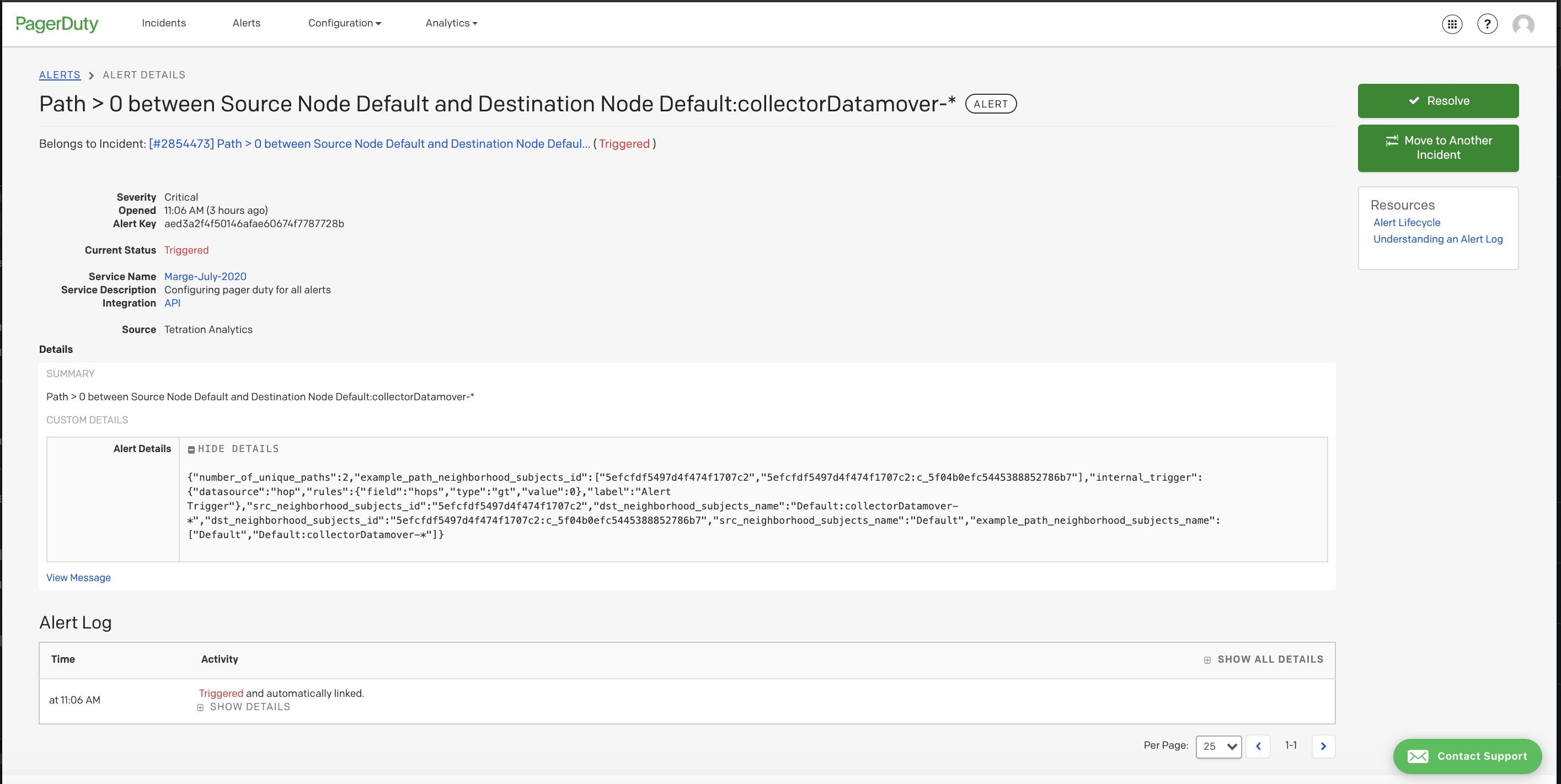
Edge Appliance: Pushes alerts to other systems such as Slack, PagerDuty, Email, and so on.
-

 Feedback
Feedback