|
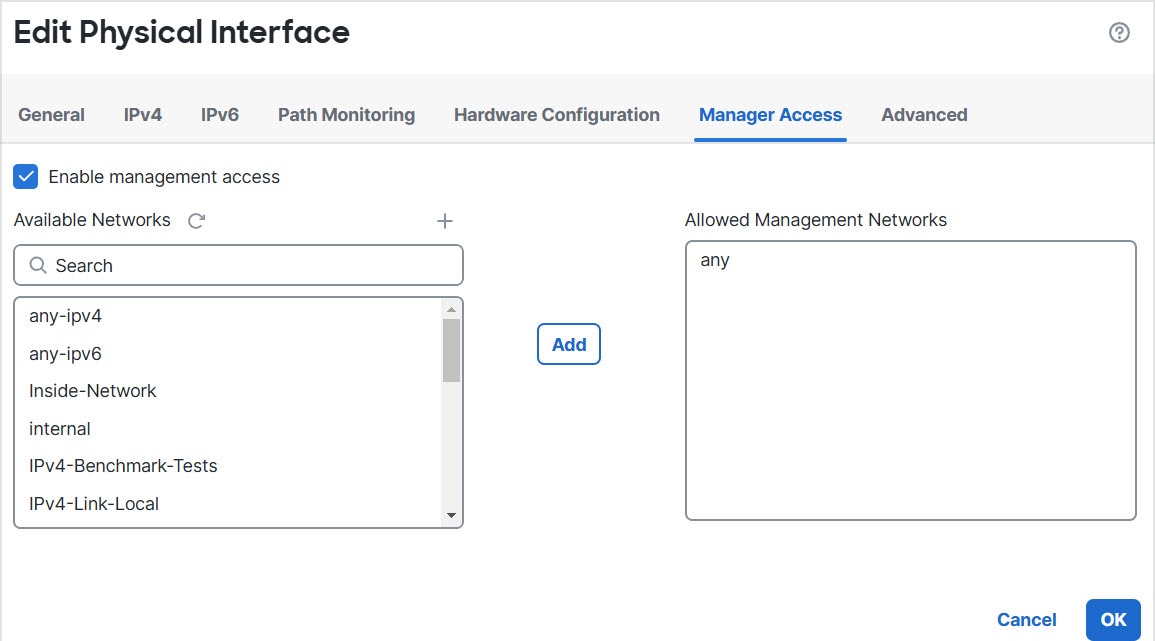
Secure Firewall 1210CP IEEE 802.3bt support (PoE++ and Hi-PoE)
|
7.7.0
|
7.7.0
|
See the following improvements related to support for IEEE
802.3bt:
-
PoE++ and Hi-PoE—Up to 90W per port.
-
Single- and dual-signature powered devices (PDs).
-
Power budgeting is done on a first-come, first-served
basis.
-
Power budget fields were added to show power
inline .
New/Modified screens:
New/Modified commands: show power
inline
|
|
For models with built-in-switches, subinterfaces can't use VLAN 1
|
7.6 |
7.6 |
For models with built-in switches, you cannot create a subinterface
using VLAN 1. VLAN 1 is reserved for the logical VLAN interface for
switch ports.
If you upgrade a 1010 to 7.6 or later, and you have assigned VLAN 1
to a subinterface, you must change the VLAN ID for your subinterface
to a new VLAN. You will not be able to deploy the configuration
using VLAN 1.
|
|
Secure Firewall supports Dual-Arm Deployment Mode on AWS with
GWLB
|
7.6 |
7.6 |
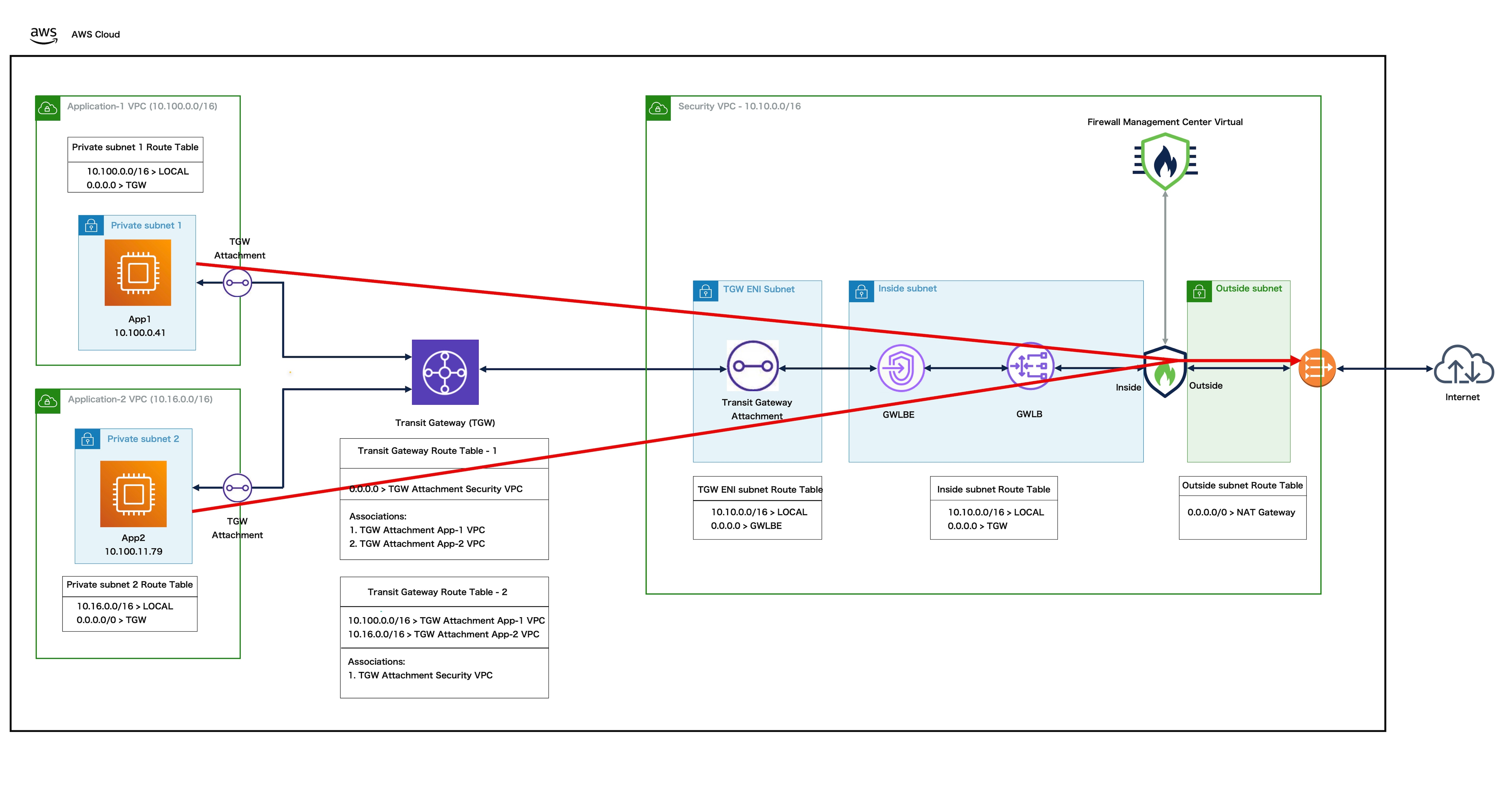
The Secure Firewall supports the dual-arm deployment
mode on AWS with GWLB. This mode enables the firewall to directly
forward internet-bound traffic to the internet through the internet
gateway after traffic inspection, while also performing network address
translation (NAT).
|
|
Secure Firewall 1210/1220 hardware switch support
|
7.6
|
7.6
|
The Secure Firewall 1210/1220 supports setting each Ethernet
interface to be a switch port or a firewall interface
|
|
Secure Firewall 1210CP PoE+ support on Ethernet ports 1/5-1/8
|
7.6 |
7.6
|
The Secure Firewall 1210CP supports Power over Ethernet+ (PoE+) on
Ethernet ports 1/5-1/8.
|
|
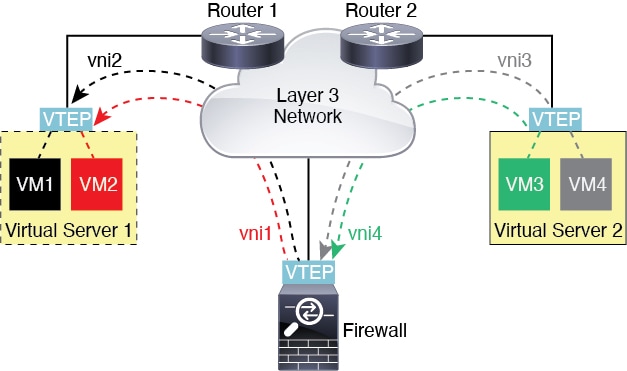
VXLAN VTEP IPv6 support
|
7.4
|
Any
|
You can now specify an IPv6 address for the VXLAN VTEP interface.
IPv6 is not supported for the threat defense virtual cluster control
link or for Geneve encapsulation.
New/Modified screens:
Requires Firewall Threat Defense version 7.4.
|
|
Loopback interface support for BGP and management traffic
|
7.4
|
Any
|
You can use a loopback interface for:
-
AAA
-
BGP
-
DNS
-
HTTP
-
ICMP
-
IPsec Flow Offload
-
NetFlow
-
SNMP
-
SSH
-
Syslog
Requires Firewall Threat Defense version 7.4.
|
|
Loopback interface support for VTI
|
7.3
|
Any
|
You can now add a loopback interface. The loopback interface helps to
overcome path failures. If an interface goes down, you can access
all interfaces through the IP address assigned to the loopback
interface. For VTI, in addition to setting a loopback interface as
the source interface, support has also been added to inherit the IP
address from a loopback interface instead of a statically configured
IP address.
New/Modified screens:
|
|
IPv6 DHCP
|
7.3
|
Any
|
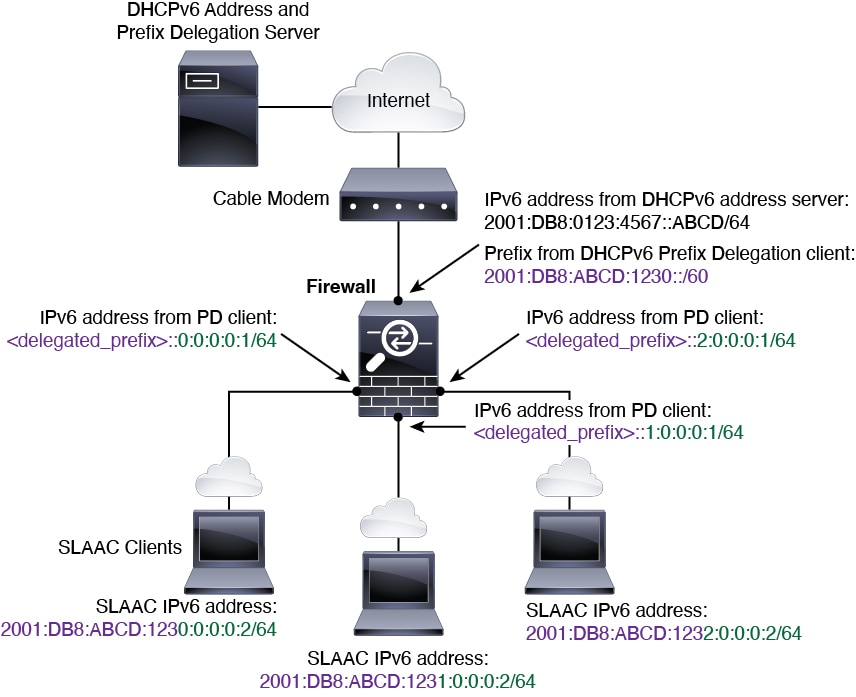
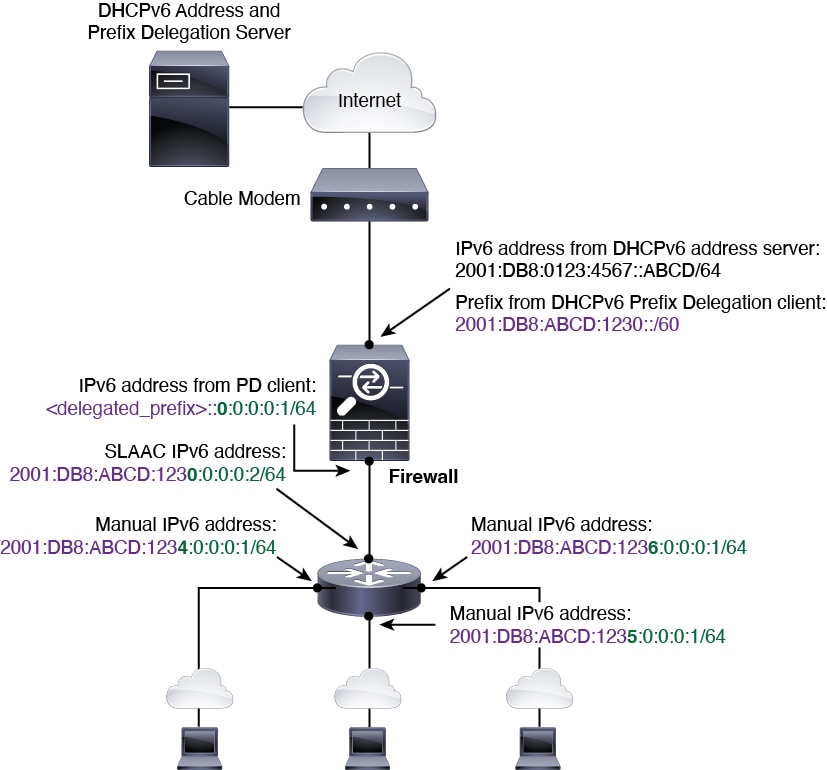
The Firewall Threat Defense now supports the following features for IPv6 addressing:
-
DHCPv6 Address client—The Firewall Threat Defense obtains an IPv6 global address and optional default route
from the DHCPv6 server.
-
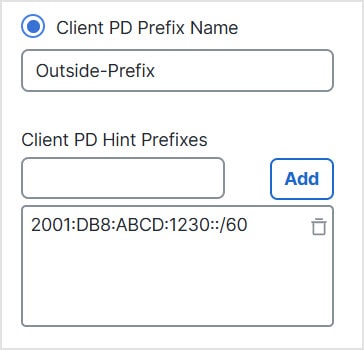
DHCPv6 Prefix Delegation client—The Firewall Threat Defense obtains delegated prefix(es) from a DHCPv6 server. The
Firewall Threat Defense can then use these prefixes to configure other Firewall Threat Defense interface addresses so that StateLess Address Auto
Configuration (SLAAC) clients can autoconfigure IPv6
addresses on the same network.
-
BGP router advertisement for delegated prefixes
-
DHCPv6 stateless server—The Firewall Threat Defense provides other information such as the domain name to
SLAAC clients when they send Information Request (IR)
packets to the Firewall Threat Defense. The Firewall Threat Defense only accepts IR packets, and does not assign addresses to
the clients.
New/Modified screens:
New/Modified commands: show bgp ipv6 unicast, show ipv6 dhcp, show
ipv6 general-prefix
|
|
Paired proxy VXLAN for the Firewall Threat Defense Virtual for the Azure Gateway Load Balancer
|
7.3
|
Any
|
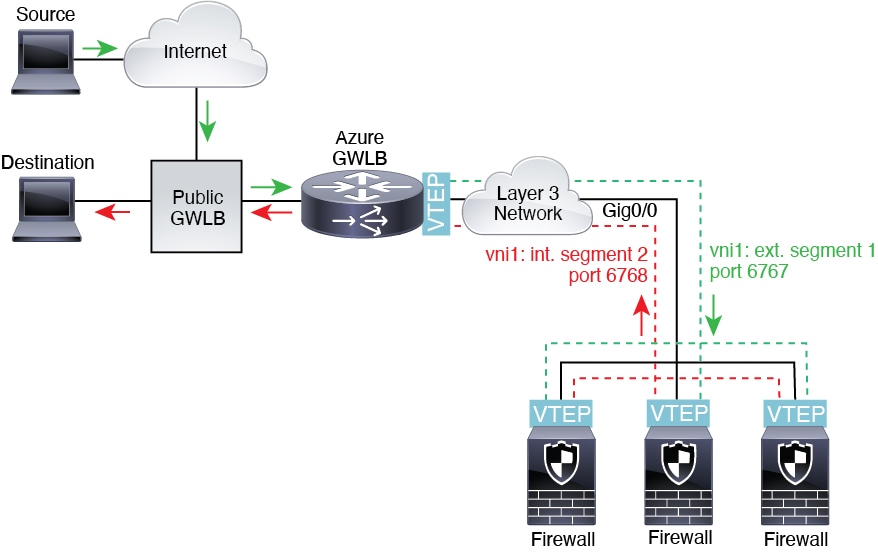
You can configure a paired proxy mode VXLAN interface for the Firewall Threat Defense Virtual in Azure for use with the Azure Gateway Load Balancer (GWLB). The
Firewall Threat Defense Virtual defines an external interface and an internal interface on a
single NIC by utilizing VXLAN segments in a paired proxy.
New/Modified screens:
Supported platforms: Firewall Threat Defense Virtual in Azure
|
|
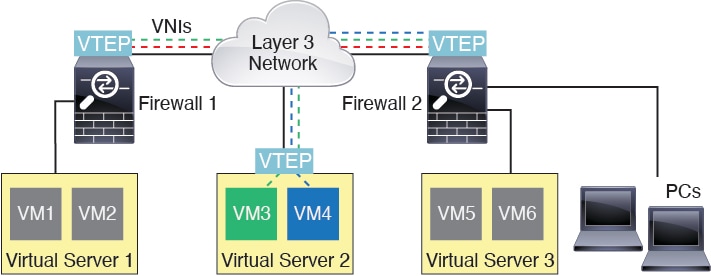
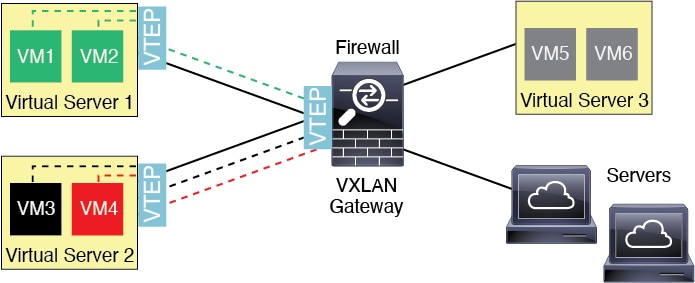
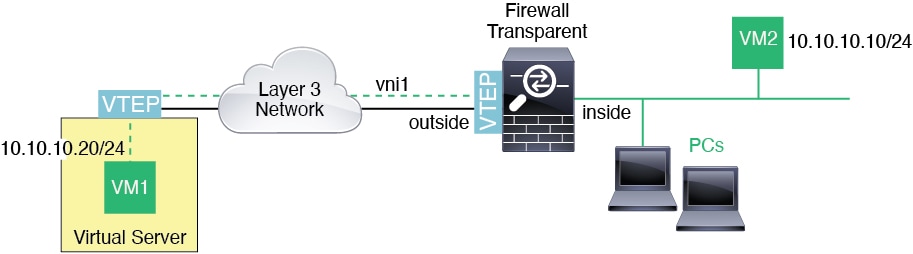
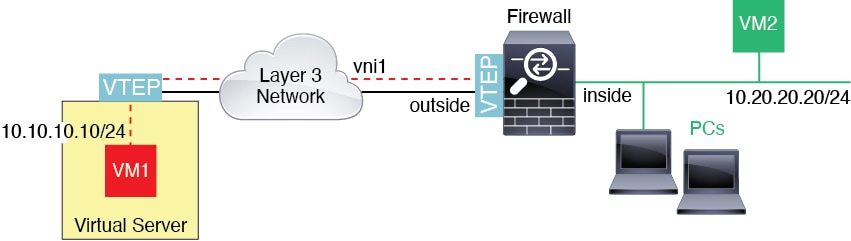
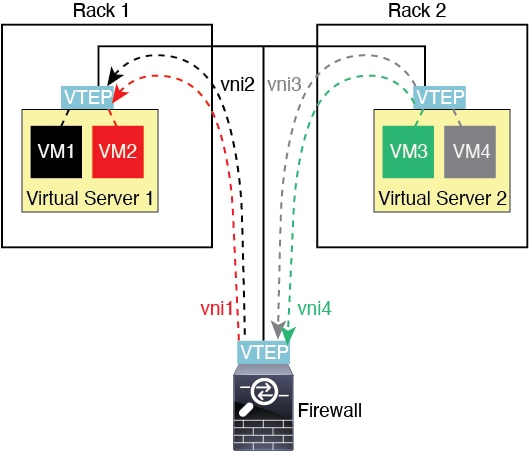
VXLAN support
|
7.2
|
Any
|
VXLAN encapsulation support was added.
New/Modified screens:
Supported platforms: All.
|
|
Geneve support for the Firewall Threat Defense Virtual
|
7.1
|
Any
|
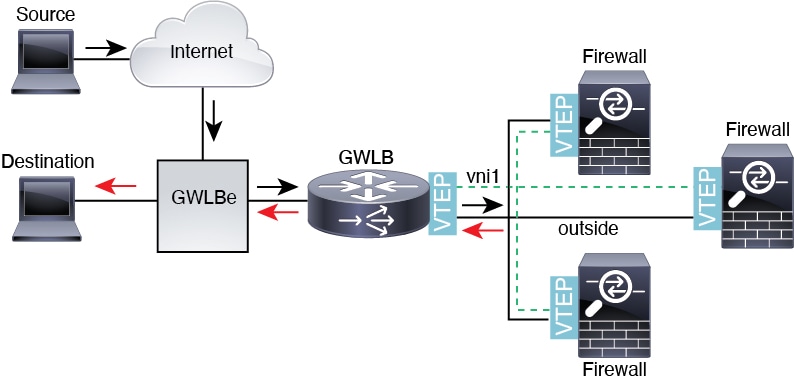
Geneve encapsulation support was added for the Firewall Threat Defense Virtual to support single-arm proxy for the Amazon Web Services (AWS)
Gateway Load Balancer. The AWS Gateway Load Balancer combines a
transparent network gateway (with a single entry and exit point for
all traffic) and a load balancer that distributes traffic and scales
Firewall Threat Defense Virtual to match the traffic demand.
This feature requires Snort 3.
New/Modified screens:
Supported platforms: Firewall Threat Defense Virtual in AWS
|
|
31-bit Subnet Mask
|
7.0
|
Any
|
For routed interfaces, you can configure an IP address on a 31-bit
subnet for point-to-point connections. The 31-bit subnet includes
only 2 addresses; normally, the first and last address in the subnet
is reserved for the network and broadcast, so a 2-address subnet is
not usable. However, if you have a point-to-point connection and do
not need network or broadcast addresses, a 31-bit subnet is a useful
way to preserve addresses in IPv4. For example, the failover link
between 2 FTDs only requires 2 addresses; any packet that is
transmitted by one end of the link is always received by the other,
and broadcasting is unnecessary. You can also have a
directly-connected management station running SNMP or Syslog. This
feature is not supported for BVIs for bridge groups or with
multicast routing.
New/Modified screens:
|
|
Synchronization between the Firewall Threat Defense operational link state and the physical link state for the
Firepower 4100/9300
|
6.7
|
Any
|
The Firepower 4100/9300 chassis can now synchronize the Firewall Threat Defense operational link state with the physical link state for data
interfaces. Currently, interfaces will be in an Up state as long as
the FXOS admin state is up and the physical link state is up. The
Firewall Threat Defense application interface admin state is not considered. Without
synchronization from Firewall Threat Defense, data interfaces can be in an Up state physically before the Firewall Threat Defense application has completely come online, for example, or can stay
Up for a period of time after you initiate an Firewall Threat Defense shutdown. For inline sets, this state mismatch can result in
dropped packets because external routers may start sending traffic
to the Firewall Threat Defense before the Firewall Threat Defense can handle it. This feature is disabled by default, and can be
enabled per logical device in FXOS.
|
Note
|
This feature is not supported for clustering, container
instances, or Firewall Threat Defense with a Radware vDP decorator. It is also not supported for
ASA.
|
New/Modified Firepower Chassis Manager screens:
New/Modified FXOS commands: set link-state-sync enabled,
show interface expand detail
Supported platforms: Firepower 4100/9300
|
|
Firepower 1010 hardware switch support
|
6.5
|
Any
|
The Firepower 1010 supports setting each
Ethernet interface to be a switch port or a firewall interface.
New/Modified screens:
|
|
Firepower 1010 PoE+ support on Ethernet 1/7 and Ethernet 1/8
|
6.5
|
Any
|
The Firepower 1010 supports Power over Ethernet+ (PoE+) on Ethernet
1/7 and Ethernet 1/8 when they are configured as switch ports.
New/Modified screens:
|
|
VLAN subinterfaces for use with container instances
|
6.3.0
|
Any
|
To provide flexible physical interface use, you can create VLAN
subinterfaces in FXOS and also share interfaces between multiple
instances.
New/Modified Secure Firewall Management Center screens:
icon > Interfaces tab
New/Modified Secure Firewall Chassis Manager screens:
drop-down menu Subinterface
New/Modified FXOS commands: create subinterface, set vlan,
show interface,show subinterface
Supported platforms: Firepower 4100/9300
|
|
Data-sharing interfaces for container instances
|
6.3.0
|
Any
|
To provide flexible physical interface use, you can share interfaces
between multiple instances.
New/Modified Secure Firewall Chassis Manager screens:
New/Modified FXOS commands: set port-type data-sharing,
show interface
Supported platforms: Firepower 4100/9300
|
|
Integrated Routing and Bridging
|
6.2.0
|
Any
|
Integrated Routing and Bridging provides the ability to route between
a bridge group and a routed interface. A bridge group is a group of
interfaces that the Firewall Threat Defense bridges instead of routes. The Firewall Threat Defense is not a true bridge in that the Firewall Threat Defense continues to act as a firewall: access control between interfaces
is controlled, and all of the usual firewall checks are in place.
Previously, you could only configure bridge groups in transparent
firewall mode, where you cannot route between bridge groups. This
feature lets you configure bridge groups in routed firewall mode,
and to route between bridge groups and between a bridge group and a
routed interface. The bridge group participates in routing by using
a Bridge Virtual Interface (BVI) to act as a gateway for the bridge
group. Integrated Routing and Bridging provides an alternative to
using an external Layer 2 switch if you have extra interfaces on the
Firewall Threat Defense to assign to the bridge group. In routed mode, the BVI can be a
named interface and can participate separately from member
interfaces in some features, such as access rules and DHCP server.
The following features that are supported in transparent mode are not
supported in routed mode: clustering. The following features are
also not supported on BVIs: dynamic routing and multicast
routing.
New/Modified screens:
Supported platforms: All except for the Firepower 2100 and the Firewall Threat Defense Virtual
|









 Feedback
Feedback