VRF leaking for EVPN E-LAN
A virtual routing and forwarding (VRF) instance is a network virtualization technology that
-
provides logical separation of network resources by creating multiple isolated virtual networks
-
operates independently with its own routing table, forwarding behavior, and network policies, and
-
enables communication among devices within the same VRF while isolating them from devices in other VRFs.
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
VRF Leaking for EVPN Single-Homing |
Release 25.1.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100]) (select variants only*) *This feature is now supported on the Cisco 8011-4G24Y4H-I routers. |
|
VRF Leaking for EVPN Single-Homing |
Release 24.4.1 |
Introduced in this release on: Fixed Systems (8700) (select variants only*) * The VRF leaking functionality is now extended to the Cisco 8712-MOD-M routers. |
|
VRF Leaking for EVPN Single-Homing |
Release 24.3.1 |
Introduced in this release on: Fixed Systems (8200, 8700); Modular Systems (8800 [LC ASIC: P100]) (select variants only*) * The VRF leaking functionality is now extended to:
|
|
VRF Leaking for EVPN Single-Homing |
Release 24.2.11 |
Introduced in this release on: Modular Systems (8800 [LC ASIC: P100]) (select variants only*) * The VRF leaking functionality is now extended to routers with the 88-LC1-36EH line cards. |
|
VRF Leaking for EVPN Single-Homing |
Release 7.11.1 |
We now allow for seamless intercommunication between different VRF instances in an EVPN domain, thus enabling controlled inter-VRF communication and resource-sharing, which is helpful in multi-tenancy environments, data center deployments, and hybrid cloud scenarios. This feature is supported only on Q200-based line cards. |
Features of Layer 2 interconnection using VRF leaking
Layer 2 interconnection using VRF leaking in an EVPN network provides these features:
-
Enables controlled Layer 2 communication between different VRF instances by selectively sharing routes.
-
Maintains VRF isolation and segmentation while allowing traffic interconnection through EVPN Route type 2 (MAC+IP) import.
-
Permits interconnection of VRFs at Layer 2 using gateways or bridges that forward traffic between VRFs.
-
Allows definition of traffic policies to control flow, including filtering based on EVPN EVI and MAC addresses.
-
Forwards Layer 2 frames between VRFs while preserving Layer 3 isolation.
Configure VRF leaking for EVPN E-LAN
This procedure enables controlled route leaking between the global routing table and a VRF routing table within an EVPN E-LAN environment. VRF leaking allows selective sharing of routes between VRFs and the global routing table, facilitating communication across different routing domains while maintaining segmentation and policy control. This is essential in multi-tenant or segmented network architectures where certain routes need to be shared securely and efficiently.
Procedure
|
Step 1 |
Configure BGP where the router performs the route leak. Example: |
|
Step 2 |
Configure the route policies. These policies help you filter which prefixes are permitted to be leaked. In this example, the route-policy GLOBAL-2-VRF and route-policy VRF-2-GLOBAL are used. Example: |
|
Step 3 |
Configure the VRF and apply the route-policy. Example: |
|
Step 4 |
Running configuration of VRF leaking. Example: |
|
Step 5 |
Use the show route command to verify the prefixes appear in the RIB and BGP tables. Example:This show output displays the information for the VRF ORANGE: |
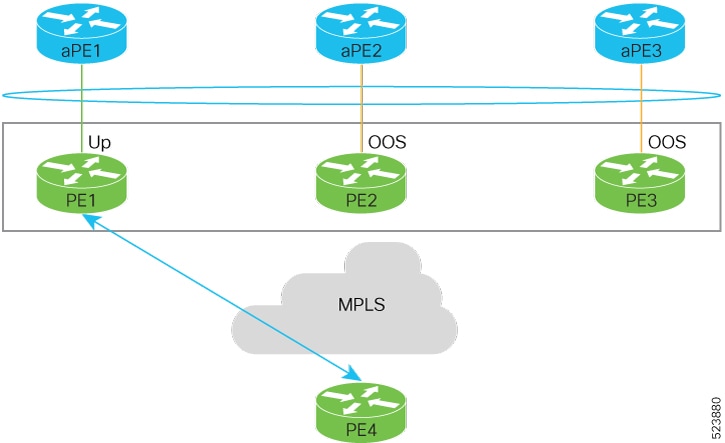
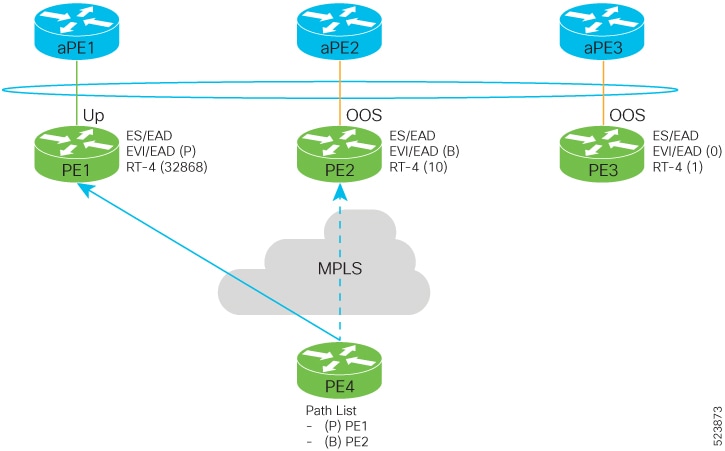
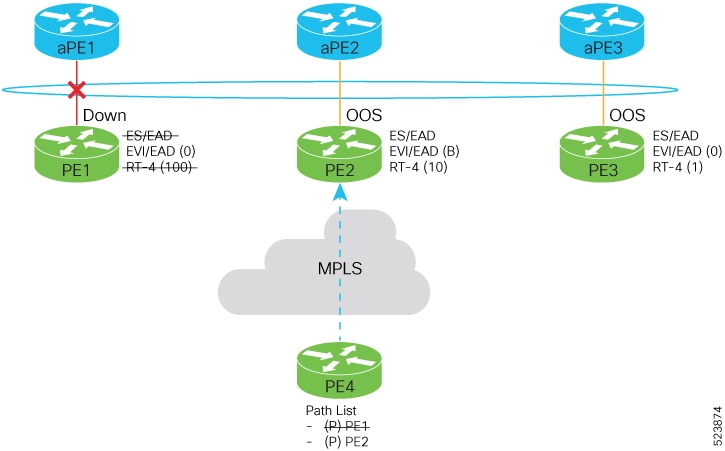
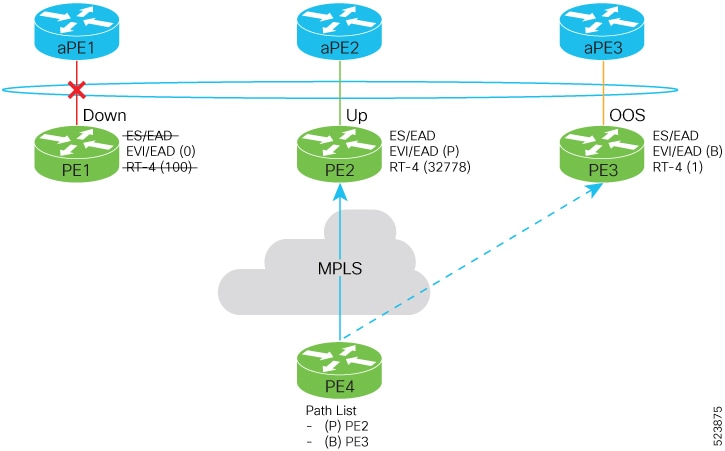
 Feedback
Feedback