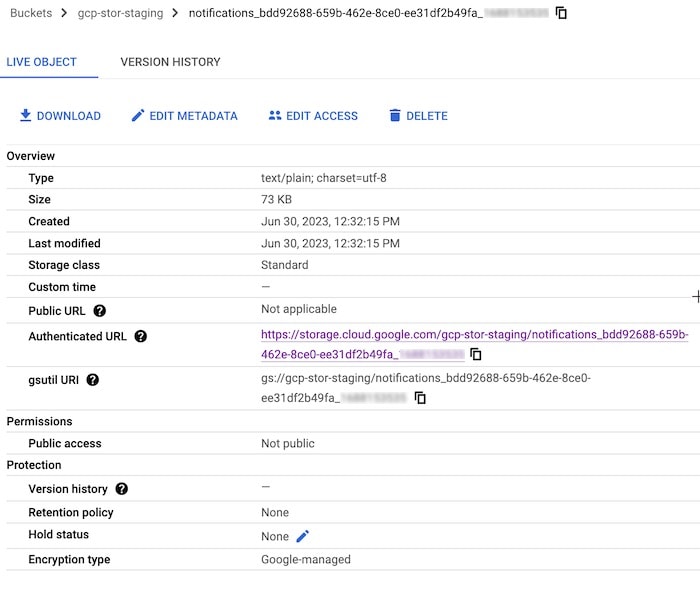
The following is an Amazon S3 notification and Google Storage log message example for a New AS Path Edge alarm.
{
"activatedAt": "2023-02-04T03:11:17Z",
"alarmId": "4b9eb669-774d-4a6d-bed5-d559248953e8",
"expected": {
"numPeersToTrigger": 1
},
"monitoredPrefix": "88.88.109.0/24",
"observed": {
"allViolationPeers": [
{
"asPath": [
916,
700,
620,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 1,
"peerIp": "10.11.12.1",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 620
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 620,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
621,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 19,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 621
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 621,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
619,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 2,
"peerIp": "10.11.12.2",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 619
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 619,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
622,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 20,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 622
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 622,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
623,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 21,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 623
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 623,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
624,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 22,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 624
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 624,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
618,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 3,
"peerIp": "10.11.12.3",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 618
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 618,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
617,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 4,
"peerIp": "10.11.12.4",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 617
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 617,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
616,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 5,
"peerIp": "10.11.12.5",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 616
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 616,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
}
]
},
{
"asPath": [
916,
700,
615,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 7,
"peerIp": "10.31.32.1",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 615
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 615,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
}
],
"allViolationPeersCount": 10
},
"orgName": "AutomationOnly5",
"policyId": "3755ed13-6498-4cc6-9798-a1264d03b402",
"policyName": "04 - New AS Path Edge",
"rule": "ALARM_RULE_NEW_AS_PATH_EDGE",
"severity": "ALARM_SEVERITY_RED",
"state": "ALARM_STATE_ACTIVE",
"tags": [
"common tag",
"prefix policy",
"04 - New AS Path Edge"
],
"transitionedAt": "2023-02-04T03:11:17Z"
}
{
"activatedAt": "2023-02-04T03:11:17Z",
"alarmId": "9a1ab970-144b-4256-a864-4eb26e698844",
"expected": {
"numPeersToTrigger": 1
},
"monitoredPrefix": "2002:5858:6d00::/48",
"observed": {
"allViolationPeers": [
{
"asPath": [
916,
700,
616,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 23,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 616
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 616,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
}
]
},
{
"asPath": [
916,
700,
618,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 24,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 618
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 618,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
619,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 25,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 619
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 619,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
620,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 26,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 620
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 620,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
621,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 27,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 621
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 621,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
622,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 28,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 622
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 622,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
623,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 29,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 623
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"2002:5858:6d00::/48",
"88.88.109.0/24"
]
},
{
"edgeId": {
"fromAs": 623,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
624,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 30,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 624
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 624,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
625,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 31,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 625
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 1,
"prefixCount": 1,
"prefixList": [
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 625,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 1,
"prefixCount": 1,
"prefixList": [
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
626,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 32,
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 626
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 1,
"prefixCount": 1,
"prefixList": [
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 626,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 1,
"prefixCount": 1,
"prefixList": [
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
617,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 6,
"peerIp": "2000::20:100:10",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 617
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 617,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
},
{
"asPath": [
916,
700,
615,
36
],
"asn": 36,
"at": "2023-02-04T01:34:59Z",
"peerId": 8,
"peerIp": "2000::30:100:10",
"suspiciousEdges": [
{
"edgeId": {
"fromAs": 36,
"toAs": 615
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
},
{
"edgeId": {
"fromAs": 615,
"toAs": 700
},
"firstSeen": "2023-02-04T01:34:59Z",
"lastSeen": "2023-02-04T01:34:59Z",
"peerCount": 2,
"prefixCount": 2,
"prefixList": [
"88.88.109.0/24",
"2002:5858:6d00::/48"
]
}
]
}
],
"allViolationPeersCount": 12
},
"orgName": "AutomationOnly5",
"policyId": "3755ed13-6498-4cc6-9798-a1264d03b402",
"policyName": "04 - New AS Path Edge",
"rule": "ALARM_RULE_NEW_AS_PATH_EDGE",
"severity": "ALARM_SEVERITY_RED",
"state": "ALARM_STATE_ACTIVE",
"tags": [
"common tag",
"prefix policy",
"04 - New AS Path Edge"
],
"transitionedAt": "2023-02-04T03:11:17Z"
}
 Feedback
Feedback