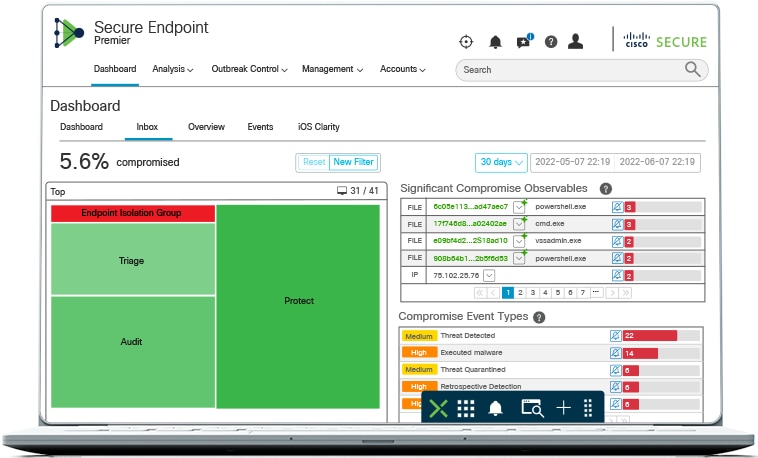
Detect and respond to threats fast with unified protection
Reduce user security risk by tackling threats quickly and prepping in advance for the next attack, while boosting visibility across users and devices.
Streamline access
When usernames and passwords fall into the wrong hands, you're vulnerable to attack. Unify user access to get to zero-trust security.
Gain insights into critical threats
Take advantage of world-class threat intelligence to equip yourself to face current and future threats.
Sharpen visibility
Monitor activity across devices—managed or unmanaged, fixed or mobile—to make sure nothing falls through the cracks and enhancing user security.
Stay agile with cloud-based solutions
Keep up with the security demands of hybrid work through cloud–based solutions that offer exceptional flexibility and industry–leading defense.
Cisco Duo
See more to safeguard more. Protect users, devices, and applications anywhere.
Cisco Secure Email
Rapidly detect, quarantine, investigate, and remediate cyberattacks that target your email.
Find a solution
Add value to security solutions
Cisco Security Enterprise Agreement
Instant savings
Experience security software buying flexibility with one easy-to-manage agreement.
Services for security
Let the experts secure your business
Get more from your investments and enable constant vigilance to protect your organization.