-
Cisco MDS 9000 Family Fabric Manager Configuration Guide, Release 3.x
-
Index
-
New and Changed Information
-
Preface
- Getting Started
- Installation and Switch Management
- Switch Configuration
-
Fabric Configuration
-
Configuring and Managing VSANs
-
SAN Device Virtualization
-
Creating Dynamic VSANs
-
Configuring Inter-VSAN Routing
-
Distributing Device Alias Services
-
Configuring and Managing Zones
-
Configuring Fibre Channel Routing Services and Protocols
-
Dense Wavelength Division Multiplexing
-
Managing FLOGI, Name Server, FDMI, and RSCN Databases
-
Discovering SCSI Targets
-
Configuring FICON
-
Advanced Features and Concepts
-
-
Security
-
Configuring FIPS
-
Configuring Users and Common Roles
-
Configuring SNMP
-
Configuring RADIUS and TACACS+
-
Configuring IPv4 Access Control Lists
-
Configuring Certificate Authorities and Digital Certificates
-
Configuring IPsec Network Security
-
Configuring FC-SP and DHCHAP
-
Configuring Port Security
-
Configuring Fabric Binding
-
- IP Services
- Intelligent Storage Services
- Network and Switch Monitoring
- Traffic Management
- Troubleshooting
-
Launching Fabric Manager in Cisco SAN-OS Releases Prior to 3.2(1)
-
Cisco Fabric Manager Unsupported Feature List
-
Interface Nonoperational Reason Codes
-
Managing Cisco FabricWare
-
Configuration Limits for Cisco MDS SAN-OS Release 3.1(x) and 3.2(x)
-
Table Of Contents
Assigning SNMP Switch Contact and Location Information
SNMPv3 CLI User Management and AAA Integration
CLI and SNMP User Synchronization
About AES Encryption-Based Privacy
Enforcing SNMPv3 Message Encryption
Assigning SNMPv3 Users to Multiple Roles
SNMP Trap and Inform Notifications
Configuring SNMPv2c Notifications
Configuring SNMPv3 Notifications
Configuring the Notification Target User
Configuring SNMP
The CLI and SNMP use common roles in all switches in the Cisco MDS 9000 Family. You can use SNMP to modify a role that was created using the CLI and vice versa.
Users, passwords, and roles for all CLI and SNMP users are the same. A user configured through the CLI can access the switch using SNMP (for example, the Fabric Manager or the Device Manager) and vice versa.
This chapter includes the following sections:
•
SNMPv3 CLI User Management and AAA Integration
•
SNMP Trap and Inform Notifications
About SNMP Security
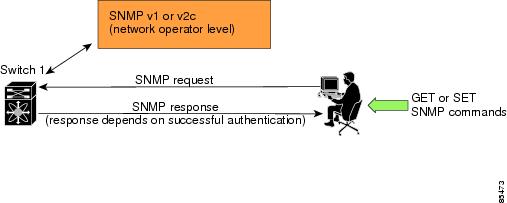
SNMP is an application layer protocol that facilitates the exchange of management information between network devices. In all Cisco MDS 9000 Family switches, three SNMP versions are available: SNMPv1, SNMPv2c, and SNMPv3 (see Figure 31-1).
Figure 31-1 SNMP Security
This section includes the following topics:
•
SNMP Version 1 and Version 2c
•
Assigning SNMP Switch Contact and Location Information
SNMP Version 1 and Version 2c
SNMP Version 1 (SNMPv1) and SNMP Version 2c (SNMPv2c) use a community string match for user authentication. Community strings provided a weak form of access control in earlier versions of SNMP. SNMPv3 provides much improved access control using strong authentication and should be preferred over SNMPv1 and SNMPv2c wherever it is supported.
SNMP Version 3
SNMP Version 3 (SNMPv3) is an interoperable standards-based protocol for network management. SNMPv3 provides secure access to devices by a combination of authenticating and encrypting frames over the network. The security features provided in SNMPv3 are:
•
Message integrity—Ensures that a packet has not been tampered with in-transit.
•
Authentication—Determines the message is from a valid source.
•
Encryption—Scrambles the packet contents to prevent it from being seen by unauthorized sources.
SNMPv3 provides for both security models and security levels. A security model is an authentication strategy that is set up for a user and the role in which the user resides. A security level is the permitted level of security within a security model. A combination of a security model and a security level determines which security mechanism is employed when handling an SNMP packet.
Assigning SNMP Switch Contact and Location Information
You can assign the switch contact information, which is limited to 32 characters (without spaces) and the switch location.
To configure contact and location information, using Fabric Manager, follow these steps
Step 1
Expand Switches from the Physical Attributes pane. You see the switch settings in the Information pane.
Step 2
Fill in the Location and Contact fields for each switch.
Step 3
Click Apply Changes to save these changes or click Undo Changes to discard any unsaved changes.
SNMPv3 CLI User Management and AAA Integration
The Cisco SAN-OS software implements RFC 3414 and RFC 3415, including user-based security model (USM) and role-based access control. While SNMP and the CLI have common role management and share the same credentials and access privileges, the local user database was not synchronized in earlier releases.
SNMPv3 user management can be centralized at the AAA server level. This centralized user management allows the SNMP agent running on the Cisco MDS switch to leverage the user authentication service of the AAA server. Once user authentication is verified, the SNMP PDUs are processed further. Additionally, the AAA server is also used to store user group names. SNMP uses the group names to apply the access/role policy that is locally available in the switch.
This section includes the following topics:
•
CLI and SNMP User Synchronization
CLI and SNMP User Synchronization
Any configuration changes made to the user group, role, or password results in database synchronization for both SNMP and AAA.
Users are synchronized as follows:
•
Deleting a user using either command results in the user being deleted for both SNMP and the CLI.
•
User-role mapping changes are synchronized in SNMP and the CLI.
Note
When the passphrase/password is specified in localized key/encrypted format, the password is not synchronized.
Note
Starting in 3.0(1), the temporary SNMP login created for FM is no longer 24 hours. It is one hour.
•
Existing SNMP users continue to retain the
authandprivpassphrases without any changes.•
If the management station creates an SNMP user in the usmUserTable, the corresponding CLI user is created without any password (login is disabled) and will have the network-operator role.
Restricting Switch Access
You can restrict access to a Cisco MDS 9000 Family switch using IP Access Control Lists (IP-ACLs). See the Chapter 33, "Configuring IPv4 and IPv6 Access Control Lists"..
Group-Based SNMP Access
Note
Because group is a standard SNMP term used industry-wide, we refer to role(s) as group(s) in this SNMP section.
SNMP access rights are organized by groups. Each group in SNMP is similar to a role through the CLI. Each group is defined with three accesses: read access, write access, and notification access. Each access can be enabled or disabled within each group.
You can begin communicating with the agent once your user name is created, your roles are set up by your administrator, and you are added to the roles.
Creating and Modifying Users
You can create users or modify existing users using SNMP, Fabric Manager, or the CLI.
•
SNMP—Create a user as a clone of an existing user in the usmUserTable on the switch. Once you have created the user, change the cloned secret key before activating the user. Refer to RFC 2574.
•
Fabric Manager—See the "Configuring Users" section on page 39-12.
•
CLI—Create a user or modify an existing user using the snmp-server user command.
A network-operator and network-admin roles are available in a Cisco MDS 9000 Family switch. There is also a default-role if you want to use the GUI (Fabric Manager and Device Manager). You can also use any role that is configured in the Common Roles database (see the "User Accounts" section on page 39-10).
Tip
All updates to the CLI security database and the SNMP user database are synchronized. You can use the SNMP password to log into either Fabric Manager or Device Manager. However, after you use the CLI password to log into Fabric Manager or Device Manager, you must use the CLI password for all future logins. If a user exists in both the SNMP database and the CLI database before upgrading to Cisco MDS SAN-OS Release 2.0(1b), then the set of roles assigned to the user becomes the union of both sets of roles after the upgrade.
This section includes the following topics:
•
About AES Encryption-Based Privacy
•
Enforcing SNMPv3 Message Encryption
•
Assigning SNMPv3 Users to Multiple Roles
About AES Encryption-Based Privacy
The Advanced Encryption Standard (AES) is the symmetric cipher algorithm. The Cisco SAN-OS software uses AES as one of the privacy protocols for SNMP message encryption and conforms with RFC 3826.
The priv option offers a choice of DES or 128-bit AES encryption for SNMP security encryption. The priv option along with the aes-128 token indicates that this privacy password is for generating a 128-bit AES key.The AES priv password can have a minimum of eight characters. If the passphrases are specified in clear text, you can specify a maximum of 64 characters. If you use the localized key, you can specify a maximum of 130 characters.
Note
For an SNMPv3 operation using the external AAA server, user configurations in the external AAA server require AES to be the privacy protocol to use SNMP PDU encryption.
Enforcing SNMPv3 Message Encryption
By default the SNMP agent allows the securityLevel parameters of authNoPriv and authPriv for the SNMPv3 messages that use user-configured SNMPv3 message encryption with auth and priv keys.
To enforce the message encryption for a user using Fabric Manager, follow these steps:
Step 1
Expand Switches > Security and then select Users and Roles from the Physical Attributes pane.
Step 2
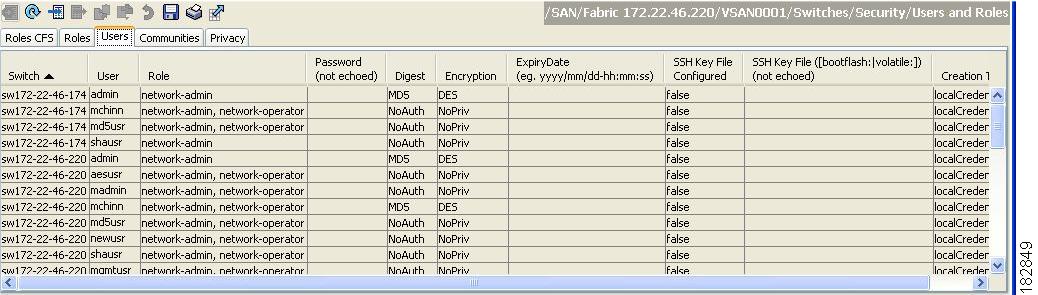
Click the Users tab in the Information pane to see a list of users like the one shown in Figure 31-2.
Figure 31-2 User Information Under the User Tab
Step 3
Click Create Row.
You see the Create Users dialog box.
Step 4
Enter the user name in the New User field.
Step 5
Select the role from the Role drop-down menu. You can enter a new role name in the field if you do not want to select one from the drop-down menu. If you do this, you must go back and configure this role appropriately (see the "User Accounts" section on page 39-10).
Step 6
Enter a password for the user in Password field.
Step 7
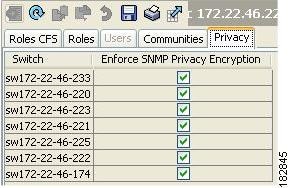
Click the Privacy tab (see Figure 31-3).
Figure 31-3 Privacy Tab
Step 8
Check the Enforce SNMP Privacy Encryption check box to encrypt management traffic.
Step 9
Click Create to create the new entry.
To enforce the SNMPv3 message encryption globally on all the users using Fabric Manager, follow these steps:
Step 1
Select a VSAN in the Logical Domains pane. This will not work if you select All VSANS.
Step 2
Expand Switches > Security and then select Users and Roles in the Physical Attributes pane. Click the Global tab in the Information pane.
Step 3
Check the GlobalEnforcePriv check box.
Step 4
Click the Apply Changes icon to save these changes.
Assigning SNMPv3 Users to Multiple Roles
The SNMP server user configuration is enhanced to accommodate multiple roles (groups) for SNMPv3 users. After the initial SNMPv3 user creation, you can map additional roles for the user.
Note
Only users belonging to a network-admin role can assign roles to other users.
To add multiple roles to a new user using Fabric Manager, follow these steps:
Step 1
Expand Switches > Security and then select Users and Roles from the Physical Attributes pane.
Step 2
Click the Users tab in the Information pane to see a list of users like the one in Figure 31-2.
Step 3
Click Create Row.
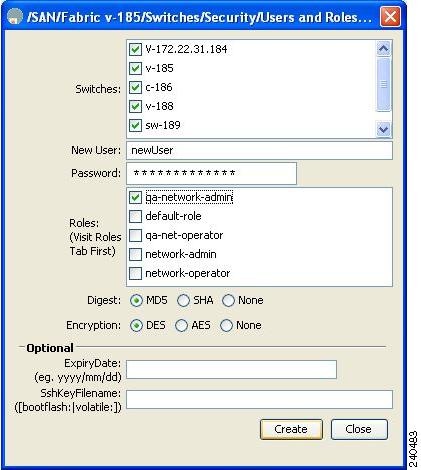
You see the Create Users dialog box shown in Figure 31-4.
Figure 31-4 Create Users Dialog Box
Step 4
Choose roles using the check boxes.
Step 5
Choose an option for Digest and one for Encryption.
Step 6
Optionally provide an expiration date for the user and the file name of an SSH key.
Step 7
Click Create to create the new roles.
Adding Communities
You can configure read-only or read-write access for SNMPv1 and SNMPv2 users. Refer to RFC 2576.
To create an SNMPv1 or SNMPv2c community string using Fabric Manager, follow these steps:
Step 1
Expand Switches > Security and then select Users and Roles from the Physical Attributes pane.
Step 2
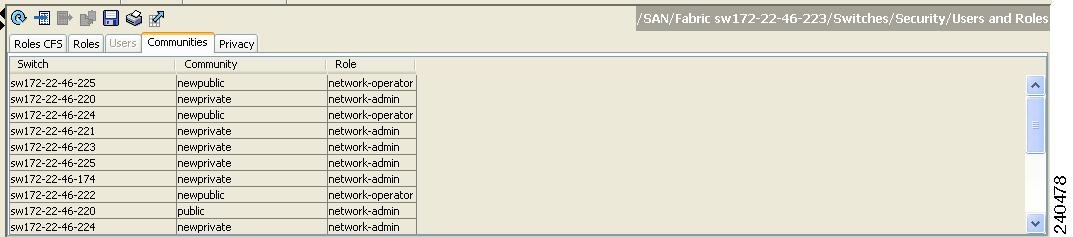
Click the Communities tab in the Information pane.
You see the existing communities (see Figure 31-5).
Figure 31-5 Communities Tab Under Users and Roles
Step 3
Click Create Row.
You see the Create Community String dialog box.
Step 4
Check the Switch check boxes to specify one or more switches.
Step 5
Enter the community name in the Community field.
Step 6
Select the role from Role drop-down list.
Note
You can enter a new role name in the field if you do not want to select one from the drop-down list. If you do this, you must go back and configure this role appropriately (see the "Role-Based Authorization" section on page 39-1).
Step 7
Click Create to create the new entry.
Deleting a Community String
To delete a community string using Fabric Manager, follow these steps:
Step 1
Expand Switches > Security and then select Users and Roles from the Physical Attributes pane.
Step 2
Click the Communities tab in the Information pane.
Step 3
Click the name of the community you want to delete.
Step 4
Click Delete Row to delete this community.
SNMP Trap and Inform Notifications
You can configure the Cisco MDS switch to send notifications to SNMP managers when particular events occur.
Note
Use the SNMP-TARGET-MIB to obtain more information on the destinations to which notifications are to be sent either as traps or as informs. Refer to the Cisco MDS 9000 Family MIB Quick Reference.
This section includes the following topics:
•
Configuring SNMPv2c Notifications
•
Configuring SNMPv3 Notifications
•
Configuring the Notification Target User
Configuring SNMPv2c Notifications
To configure SNMPv2c notifications using Fabric Manager, follow these steps:
Step 1
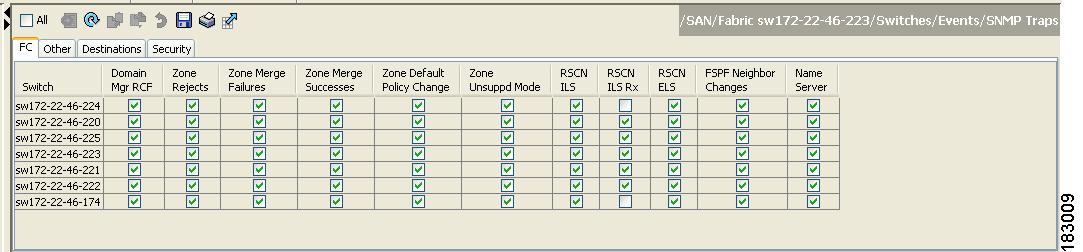
Expand Switches > Events and then select SNMP Traps in the Physical Attributes pane.
You see the SNMP notification configuration in the Information pane shown in Figure 31-6.
Figure 31-6 SNMP Notifications
Step 2
Click the Destinations tab to add or modify a receiver for SNMP notifications.
Step 3
Click Create Row to create a new notification destination.
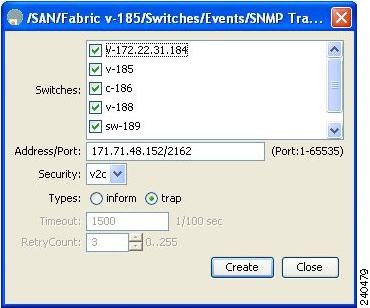
You see the Create Destinations dialog box shown in Figure 31-7.
Figure 31-7 Create Destinations Dialog Box
Step 4
Check the switches for which you want to configure a new destination.
Step 5
Set the destination IP address and UDP port.
Step 6
Choose either the trap or inform radio button.
Step 7
Optionally, set the timeout or retry count values.
Step 8
Click Create to add this destination to the selected switches.
Step 9
Optionally, click the Other tab to enable specific notification types per switch.
Step 10
Click the Apply changes icon to create the entry.
Note
Switches can forward events (SNMP traps and informs) up to 10 destinations.
Configuring SNMPv3 Notifications
Note
To configure SNMPv3 notifications using IPv4 using Fabric Manager, selct v3 from the Security drop-down list in the Create Destinations dialog box (see Figure 31-7). Optionally, set the inform time out and retry values. Click Create to add this destination to the selected switches.
Note
In the case of SNMPv3 notifications, the SNMP manager is expected to know the user credentials (authKey/PrivKey) based on the switch's engineID to authenticate and decrypt the SNMP messages.
Enabling SNMP Notifications
Notifications (traps and informs) are system alerts that the switch generates when certain events occur. You can enable or disable notifications. By default, no notification is defined or issued. If a notification name is not specified, all notifications are disabled or enabled.
Table 31-1 lists the Fabric Manager procedures that enable the notifications for Cisco MDS MIBs. Choose Switches > Events > SNMP Traps to see the check boxes listed in this table.
Note
Choosing Switches > Events > SNMP Traps enables both traps and informs, depending on how you configured notifications. See the "Configuring SNMPv3 Notifications" section .
The following notifications are enabled by default:
•
entity fru
•
license
•
link ietf-extended
All other notifications are disabled by default.
To enable individual notifications using Fabric Manager, follow these steps:
Step 1
Expand Switches > Events and then select SNMP Traps in the Physical Attributes pane.
You see the SNMP notification configuration in the Information pane.
Step 2
Click the FC tab to enable Fibre Channel related notifications.
Step 3
Check each notification check box that you want to enable.
Step 4
Click the Other tab to enable other notifications.
Step 5
Check each notification check box that you want to enable.
Step 6
Click the Apply changes icon to create the entry.
Configuring the Notification Target User
You must configure a notification target user on the switch for sending SNMPv3 inform notifications to the SNMP manager.
To configure the notification target user, refer to the Cisco MDS 9000 Family CLI Configuration Guide.
The credentials of the notification target user are used for encrypting the SNMPv3 inform notification messages to the configured SNMP .
Note
For authenticating and decrypting the received INFORM PDU, the SNMP manager should have the same user credentials in its local configuration data store of users.
Configuring Event Security
CautionThis is an advanced function that should only be used by administrators having experience with SNMPv3.
SNMP events can be secured against interception or eavesdropping in the same way that SNMP messages are secured. Fabric Manager or Device Manager allow you to configure the message processing model, the security model, and the security level for the SNMP events that the switch generates.
To configure SNMP event security using Fabric Manager, follow these steps:
Step 1
Expand Switches > Events and then select SNMP Traps.
Step 2
Click the Security tab in the Information pane.
You see the security information for SNMP notifications.
Step 3
Set the message protocol model (MPModel), security model, security name, and security level.
Step 4
Click the Apply Changes icon to save and apply your changes.
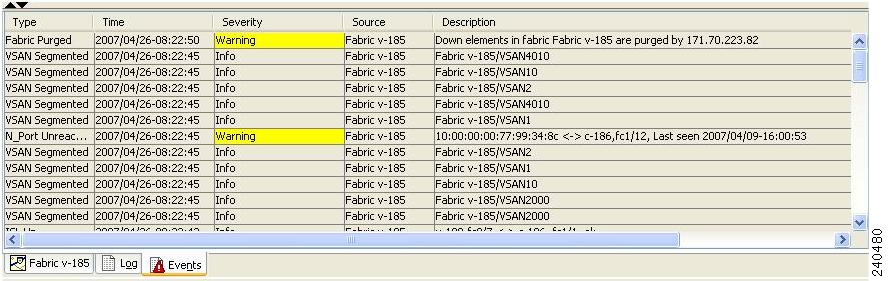
Viewing the SNMP Events Log
To view the SNMP events log from Fabric Manager, click the Events tab (see Figure 31-8). You see the Events listed with a log of events for a single switch.
Figure 31-8 Events Information
Note
The MDS syslog manager must be set up before you can view the event logs.
CautionChanging these values from different Fabric Manager workstations at the same time may cause unpredictable results.
Default Settings
Table 31-2 lists the default settings for all SNMP features in any switch.
Table 31-2 Default SNMP Settings
User account
No expiry (unless configured).
Password
None.

 Feedback
Feedback