Agent Enforcement on the Linux Platform
On the Linux platform, enforcement of both IPv4 and IPv6 policies is supported. The agent uses the iptables or ip6tables, and ipset to enforce network policies. After the agent is enabled on the host, by default, it controls, and programs iptables. If the IPv6 network stack is enabled, then the agent controls the IPv6 firewall using ip6tables.
Linux iptables or ip6tables
The Linux kernel has iptables and ip6tables that are used to set up, maintain, and inspect the tables of IPv4 and IPv6 packet filter rules. The iptables and ip6tables consist of many predefined tables. Each table contains predefined chains and can also contain user-defined chains. These chains contain sets of rules and each of these rules specifies the match criteria for a packet. Predefined tables include raw, mangle, filter, and NAT. Predefined chains include INPUT, OUTPUT, FORWARD, PREROUTING, and POSTROUTING.
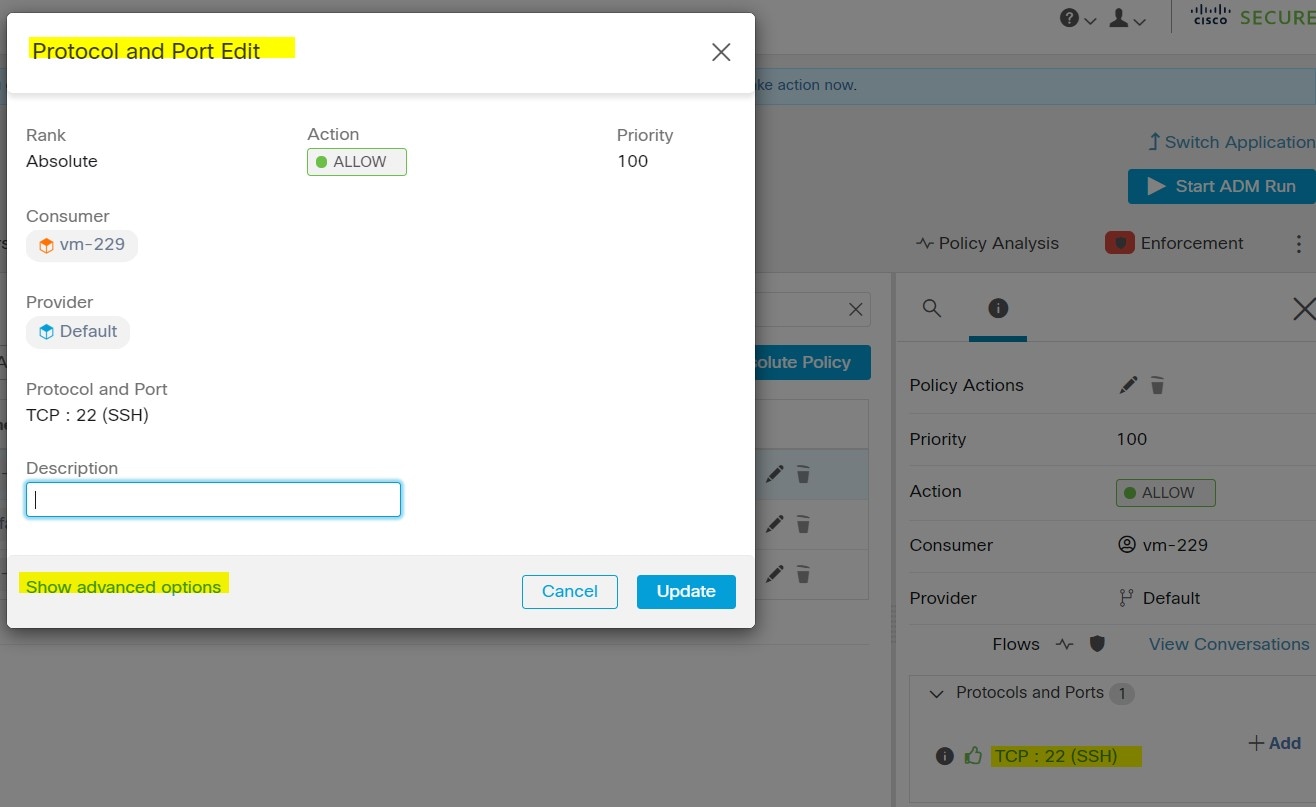
The Secure Workload agent programs a filter table that contains rules to allow or drop packets. The filter table consists of the predefined chains INPUT, OUTPUT, and FORWARD. Along with these, the agent adds custom TA chains to categorize and manage the policies from the controller. These TA chains contain Secure Workload rules that are derived from the policies along with rules that are generated by the agent. When the agent receives platform-independent rules, it parses and converts them into iptable, ip6table, or ipset rules and inserts these rules into TA defined chains in the filter table. After programming the firewall, the agent monitors the firewall for any rule or policy deviation and if so, reprograms the firewall. It keeps track of the policies that are programmed in the firewall and reports their stats periodically to the controller.
Here is an example to depict this behavior:
A typical policy in a platform-independent network policy message consists of:
source set id: “test-set-1”
destination set id: “test-set-2”
source ports: 20-30
destination ports: 40-50
ip protocol: TCP
action: ALLOW
. . .
set_id: “test-set-1”
ip_addr: 1.2.0.0
prefix_length: 16
address_family: IPv4
set_id: “test-set-2”
ip_addr: 3.4.0.0
prefix_length: 16
address_family: IPv4Along with other information, the agent processes this policy and converts it into platform-specific ipset and iptables rule:
ipset rule:
Name: ta_f7b05c30ffa338fc063081060bf3
Type: hash:net
Header: family inet hashsize 1024 maxelem 65536
Size in memory: 16784
References: 1
Members:
1.2.0.0/16
Name: ta_1b97bc50b3374829e11a3e020859
Type: hash:net
Header: family inet hashsize 1024 maxelem 65536
Size in memory: 16784
References: 1
Members:
3.4.0.0/16
iptables rule:
TA_INPUT -p tcp -m set --match-set ta_f7b05c30ffa338fc063081060bf3 src -m set --match-
˓→set ta_1b97bc50b3374829e11a3e020859 dst -m multiport --sports 20:30 -m multiport --
˓→dports 40:50 -j ACCEPTCaveats
ipset Kernel Module
When enforcement is enabled and preserve rules is disabled in the Agent Config profile, the agents running on Linux hosts ensures that the ipset kernel module has a sufficiently large max_sets configuration. In case a change is needed, the agent reloads the ipset kernel module with a new max_sets value. If Preserve Rules is enabled, the agents check the current ipset module max_sets value, but does not make any change. The current configured max_sets value can be found in cat /sys/module/ip_set/parameters/max_sets.
Host Firewall Backup
The first time that enforcement is enabled in the Agent Config profile, the agents running on Linux hosts, store the current content of ipset and ip[6]tables in /opt/cisco/tetration/backup before taking control of the host firewall.
Successive disable or enable transitions of enforcement configuration do not generate backups. The directory is not removed after agent uninstallation.

 Feedback
Feedback