To enable a fully verifiable HTTPS access to the Secure Workload UI, an SSL certificate specific to the U I’s domain name and the RSA private key that matches the SSL certificate’s public
key can be uploaded into the cluster.
An SSL Certificate can be obtained in two ways depending on the format of the Fully Qualified Domain Name (FQDN) used to refer
to the Secure Workload UI Virtual IP (VIP) address. If the Secure Workload FQDN is based on an enterprise domain name such as tetration.cisco.com, your enterprise Certificate Authority (CA) who owns
the base domain issues you an SSL Certificate. Otherwise, you may use a reputable SSL Certificate vendor to issue you an SSL
Certificate for your FQDN.

Note
|
It is important to note that although the Secure Workload UI supports Server Name Indication (SNI), subject alternative names (Sans) specified in the certificate will not be matched.
For instance, if the common name (CN) of the certificate is tetration.cisco.com and the certificate includes a SAN for tetration1.cisco.com,
HTTPS requests sent with an Incompatible browser to the cluster with tetration1.cisco.com as the host name will not be served
with that certificate. HTTPS requests made to the cluster with a host name other than the host name specified in the CN will
be served using the default, self-signed certificate that is installed on the cluster. These requests result in browser warnings.
|
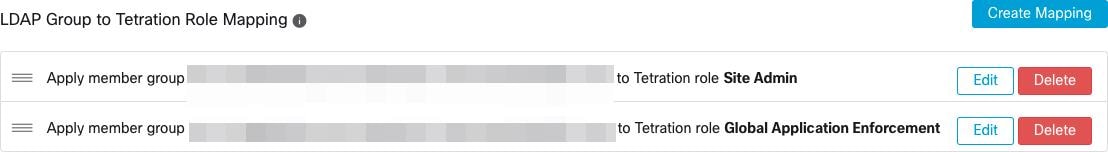
Site Admins and Customer Support users can work with SSL Certificates. From the navigation pane, click .
The Maintenance UI or set-ups, which is used for major upgrade releases and patches, has been migrated to an HTTPS URL schema. After upgrading
to a Secure Workload, Release, administrators are required to upload separate certificates for the Maintenance UI.
To import the certificate and key, click the Import New Certificate and Key button.
To generate the signing request, click the Generate New Certificate Signing Request button.

Note
|
The first import of SSL certification and the private key should be performed through a trusted network connection to the
cluster so that the private key cannot be intercepted by malicious parties who have access to the transport layer.
|
Enter the following information for your SSL certificate and key:
NAME can be any name for the certificate key pair. This name is for your benefit when looking at which SSL certificate is installed.
X509 Certificate field accepts SSL certificate string in Privacy Enhanced Mail (PEM) format. If your SSL certificate requires an intermediary
CA bundle, concatenate the CA bundle after your cert so that the SSL certificate for your Secure Workload FQDN is in the beginning of the certificate file.
It should have the following format:
-----BEGIN CERTIFICATE-----
< Certificate for Secure Workload FQDN >
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
< Intermediary CA 1 content >
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
< Intermediary CA 2 content >
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
< Root CA content >
-----END CERTIFICATE-----
RSA Private Key field should be the RSA private key of the public key that is signed in the previous certificate. It should have the following
format:
-----BEGIN RSA PRIVATE KEY-----
< private key data >
-----END RSA PRIVATE KEY-----

Note
|
RSA Private Key is required to be unencrypted. It causes a “500 Internal Server Error” if the RSA Private Key is encrypted.
|
After you import, verification steps are run to ensure that public key that is signed in the certificate and the private key
are indeed RSA key pair. If the verification is successful, we display the SHA-1 digest (SHA-1 signature and creation time)
of the certificate bundle.
Reload the browser to see that your SSL connection to the Secure Workload UI is now using the newly imported SSL certificate.


 Feedback
Feedback