Overview of SD-WAN Wizard and Device Templates
Onboarding multiple devices on a branch network and establishing a secure network infrastructure that connects these branches to the central headquarters is challenging. Manually configuring and deploying these devices within an SD-WAN topology is time-intensive and error-prone, potentially leading to inconsistencies in network settings and security vulnerabilities across different locations.
You can mitigate these issues by using the Cisco Secure Firewall Management Center (subsequently referred to as Firewall Management Center) and Cisco Secure Firewall Threat Defense (subsequently referred to as Firewall Threat Defense devices) devices. The Secure Firewall solution streamlines the deployment of secure branch networks with the new SD-WAN VPN wizard and device templates, which are available in Firewall Management Center Version 7.6.
The SD-WAN VPN wizard simplifies the configuration of VPN tunnels between your centralized headquarters and remote branch sites. It automates the VPN and routing setup for your SD-WAN overlay network.
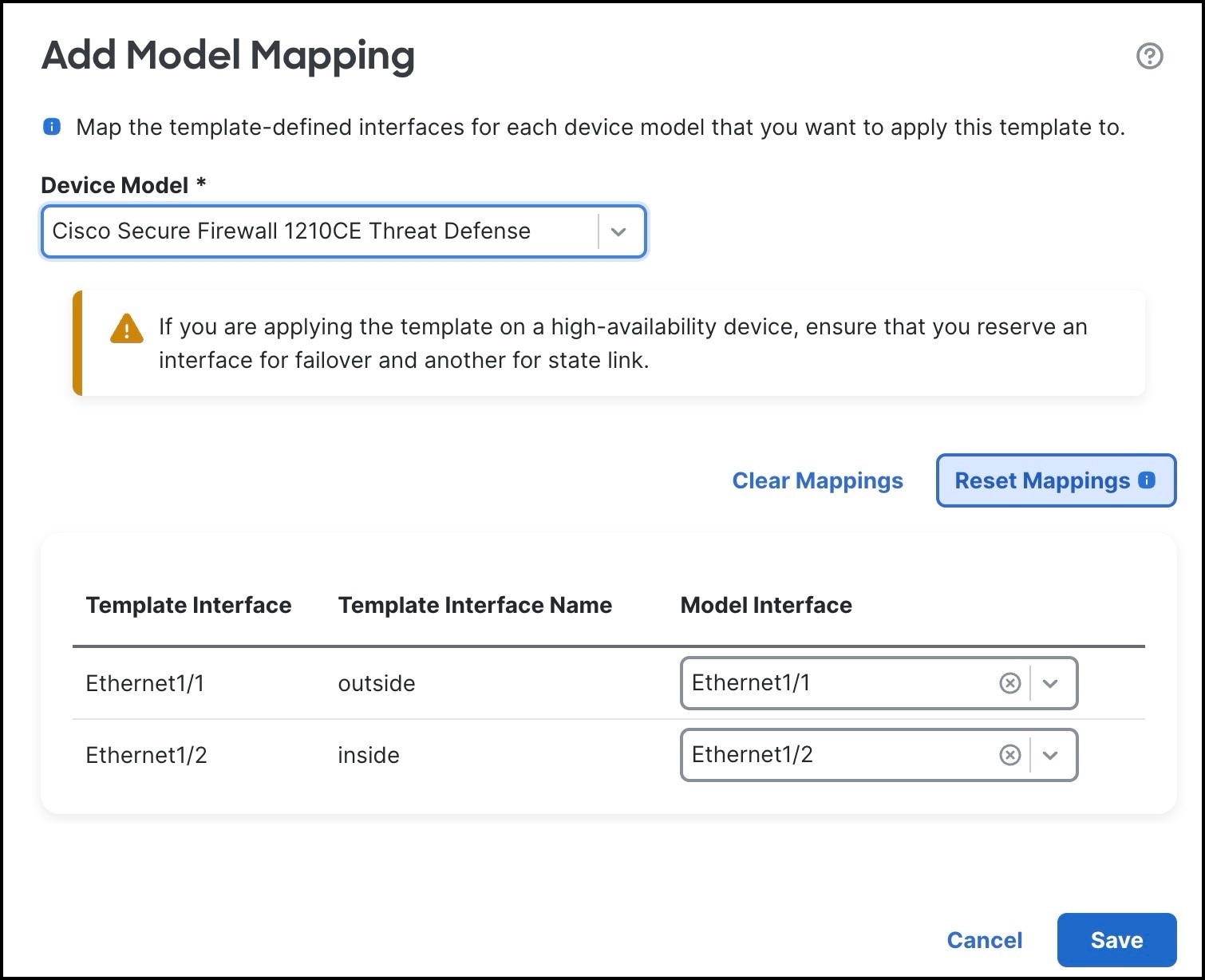
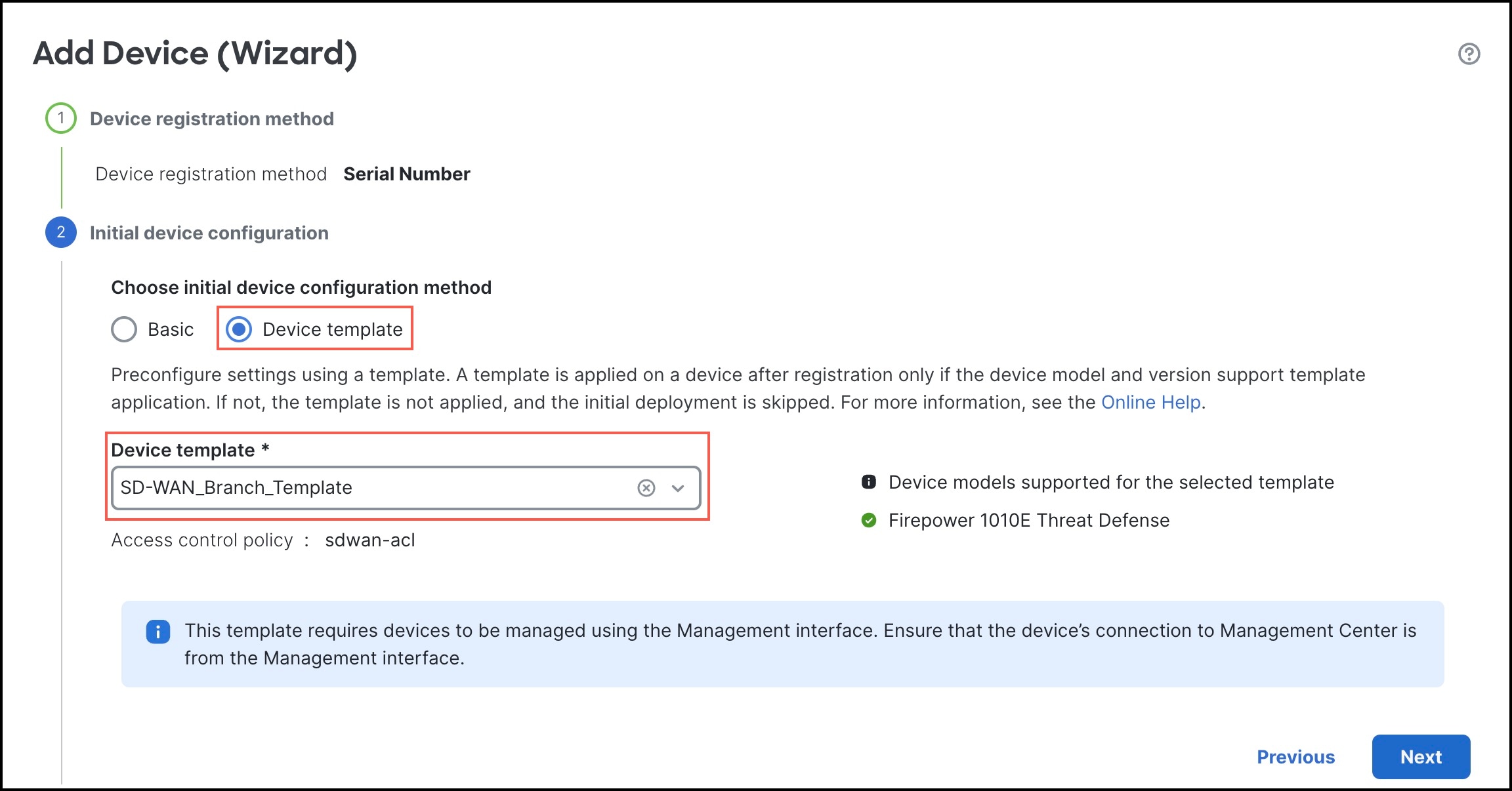
Device templates facilitate the deployment of multiple branch devices with preprovisioned initial configurations. Using these templates, you can easily configure SD-WAN VPN connections and seamlessly add spokes to your SD-WAN topologies.




















 Feedback
Feedback