Guidelines and Limitations
This section includes the guidelines and limitations for this feature.
Context Mode Guidelines
Supported in single and multiple context mode. In the appropriate release of the ASA General Operations CLI Configuration Guide, refer to Guidelines for Multiple Context Mode for the list of what is not supported in multiple context mode, and New Features which gives the breakdown of what was added throughout the releases.Firewall Mode Guidelines
Supported only in routed firewall mode. Transparent mode is not supported.
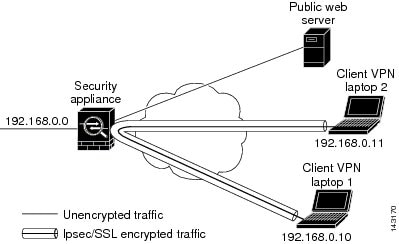
Network Address Translation (NAT)
For guidelines and information about NAT configuration, see the NAT for VPN section of the Cisco ASA Series Firewall CLI Configuration Guide.

 Feedback
Feedback