The need for high-speed encryption
Importance of network infrastructure security
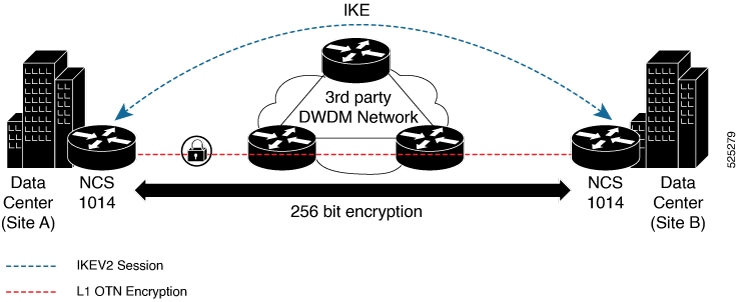
Most of the emphasis on protecting networks today is focused on securing data within data centers. However, the infrastructure of networks that connect these data centers is equally vulnerable to calculated attacks.
Vulnerability of fiber-optic networks and the necessity of data encryption
As more sensitive information is transmitted across fiber-optic networks, cyber criminals are increasingly focused on intercepting data during its transit across these networks. With the rise in network or fiber-optic hacks, data protection is paramount. Encrypting any data that leaves data centers is becoming a crucial requirement for cloud operators.
Optical encryption
Optical encryption secures all data on the communications link in and out of a facility, rendering it undecipherable to hackers tapping into the fiber strand. Protecting data at high speeds or line rates is essential for data centers today.


 Feedback
Feedback