BGP flowspec
The BGP flowspec is a routing feature that
-
dynamically distributes traffic filtering and policing rules
-
enables granular control over network traffic, and
-
automates threat mitigation across BGP-speaking routers.
You use BGP flowspec primarily to quickly and automatically respond to network threats, especially Distributed Denial-of-Service (DDoS) attacks. This feature allows you to deploy filtering rules rapidly across many routers, stopping attack traffic closer to its source. It provides granular control over traffic, letting you define precise matching criteria and actions. By automating rule deployment through BGP updates, you reduce manual configuration effort and ensure consistent policy enforcement across your network.
|
Feature Name |
Release Information |
Feature Description |
|
BGP Flowspec |
Release 25.4.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100])(select variants only*) *This feature is supported on:
|
|
BGP Flowspec |
Release 25.3.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100])(select variants only*) *This feature is supported on Cisco 8011-4G24Y4H-I routers. |
|
BGP Flowspec |
Release 25.1.1 |
Introduced in this release on: Fixed Systems (8700 [ASIC: K100])(select variants only*) *This feature is supported on Cisco 8712-MOD-M routers. |
|
BGP Flowspec |
Release 24.4.1 |
Introduced in this release on: Fixed Systems (8700) (select variants only*); Modular Systems (8800 [LC ASIC: P100])(select variants only*) You can now rapidly deploy and propagate filtering and policing functionality across many BGP peer routers, which helps to mitigate the effects of a distributed denial-of-service (DDoS) attack on your network. This feature allows you to create detailed instructions for matching specific traffic flows based on various parameters (for example, IP addresses, ports, and packet specifics) and to define actions (such as dropping, policing, or redirecting the traffic) through BGP updates. This helps in effectively managing and mitigating unwanted traffic. *This feature is supported on:
|
How BGP flowspec client-server controller models work
The BGP flowspec model operates with a controller (often a server) and clients (BGP speakers). The controller originates and injects the flowspec NLRI entries, while the clients receive these entries and program their hardware accordingly.
The BGP flowspec model operates with a controller (often a server) and clients (BGP speakers). The controller originates and injects the Flowspec NLRI entries, while the clients receive these entries and program their hardware accordingly. This model is often visualized with the controller on the left-hand side (refer to the figure: BGP flowspec Controller) and the client on the right-hand side (refer to the figure: BGP flowspec Client), illustrating the flow of information.
Summary
The BGP Flowspec process describes how a controller defines and distributes traffic management rules to client routers, which then enforce these rules on network traffic. This ensures dynamic and granular control over data flows.
Workflow
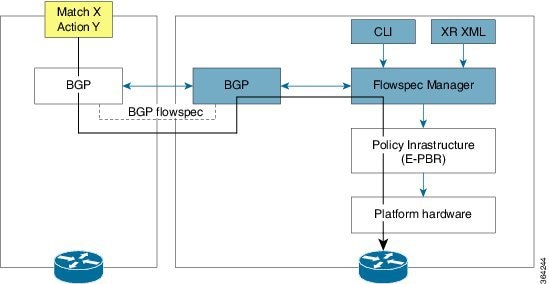

These stages describe the BGP flowspec client-server controller model:
-
Rule construction:
- Actor: The controller
- Action: The controller defines specific traffic flow rules. These rules include both detailed matching criteria (what traffic to identify) and the actions the network takes (what to do with that traffic). The controller is typically configured using commands to provide these entries for NLRI injection.
-
BGP propagation:
- Actor: The controller
- Action: The controller encodes these rules. It uses BGP NLRI for the matching criteria and BGP extended communities for the actions.
-
- Actor: The BGP flowspec-enabled controller
- Action: The controller originates these rules and advertises them to its BGP peers, which function as clients or speakers.
-
Local enforcement:
- Actor: The receiving BGP Flowspec Client routers
- Action: The client routers install these rules into their local forwarding plane. The client receives the information, sends it to its internal flowspec manager, and configures the enhanced Policy-based Routing (ePBR) infrastructure, which in turn programs the underlying hardware.
-
Traffic processing:
- Actor: The client router's active Layer 3 interfaces.
- Action: Once installed and programmed in the applicable line cards, the interfaces start processing ingress traffic. They apply the specified actions to any traffic flows that match the defined rules.
Result
This process results in network devices actively identifying and applying predefined actions (such as filtering, policing, or redirection) to specific traffic flows in real-time, based on the rules distributed via BGP.
Restrictions for BGP flowspec
These are the specific restrictions for configuring of BGP flowspec. You should be aware of them when deploying and managing the BGP flowspec:
-
Flowspec statistics are supported only when a policer rate limit is configured.
-
The policer action scale is limited to a maximum of 128 per slice.
-
Statistics for the Redirect action are supported only if a policer is attached; statistics are not supported for Redirect action alone.
-
Redirects from a VRF to the default VRF are not supported.
-
Flowspec is not supported when using multi-instance BGP.
Understanding these limitations helps you design and operate Flowspec policies effectively and avoid unsupported configurations.
Configure BGP flowspec on the client
This section provides configuration examples for a scenario where a BGP flowspec controller (server) with IP address 10.2.3.4 sends flowspec NLRI to a client with IP address 10.2.3.3. The NLRI contains matching criteria, and the Client processes traffic based on these criteria. Traffic is then dropped or accepted based on the configured criteria.
Before you begin
You must enable and configure the Border Gateway Protocol (BGP) routing process on both the client and server routers.
This task describes how you configure a BGP Flowspec client to receive and process flowspec NLRI from a BGP flowspec server.
Procedure
|
Step 1 |
Define a Virtual Routing and Forwarding (VRF) instance named vrf1 and set up import and export route targets for different address families. Example: |
|
Step 2 |
Configure BGP flowspec for various address families to allow local installation of rules on all interfaces. Example: |
|
Step 3 |
Configure route policies to accept all routes (pass-all) and to reject all routes (drop-all). Example: |
|
Step 4 |
Configure the BGP process and define the neighbor relationship with the Flowspec server (10.2.3.4), applying the defined route policies for inbound and outbound Flowspec NLRI. Example: |
|
Step 5 |
Disable BGP flowspec. Example: |
This configuration establishes a VRF instance named vrf1 within BGP AS 140, defining import and export route targets for IPv4, IPv6, and VPN address families, enabling its participation
in an MPLS VPN environment. Additionally, it configures the router as a BGP flowspec client that locally installs received
flowspec rules on all interfaces, accepting rules from neighbor 10.2.3.4 (a flowspec server) while preventing the advertisement
of its own flowspec rules.
Configure BGP flowspec on the server
This task describes how you configure a BGP Flowspec server to define and advertise Flowspec NLRI to a BGP flowspec client.
Before you begin
Procedure
|
Step 1 |
Configure route policies to accept all routes (pass-all) and to reject all routes (drop-all). Example: |
|
Step 2 |
Configure the BGP process and define the neighbor relationship with the flowspec client (10.2.3.3), applying the defined route policies for inbound and outbound flowspec NLRI. Example: |
|
Step 3 |
Define IPv4 traffic classes and associate them with a policy-map to specify actions. Example: |
|
Step 4 |
Define IPv6 traffic classes and associate them with a policy-map for service policies. Example: |
|
Step 5 |
Define a class map to match traffic based on DSCP values and a policy map to redirect IPv4 traffic to a next-hop with a specific police rate. Example: |
This configuration establishes the router as a BGP flowspec server, allowing it to fully exchange flowspec rules for various traffic types with its client (10.2.3.3). It then defines specific traffic patterns for IPv4 and IPv6, applying actions such as dropping, redirecting, or rate-limiting these flows based on received rules, both globally and within a VPN.
Verify running configuration for BGP flowspec
The purpose of this running configuration is to verify a functional BGP flowspec client-server deployment. This setup enables a centralized server (Controller) to dynamically define, propagate, and enforce granular traffic filtering and policing rules across a client router, thereby providing a robust mechanism for network-wide traffic management and DDoS mitigation.
This configuration details the setup for two routers: a BGP Flowspec client (router ID 10.2.3.3) and a BGP Flowspec server (router ID 10.2.3.4), both within AS 1.
Procedure
|
Running configuration. Example: |
Verify flowspec flow information, statistics, and NLRI data, and related policy maps
Verify the information about BGP Flowspec routes, including their attributes, status, and operational metrics. These outputs help users monitor and verify the distribution and application of Flowspec rules within the BGP routing environment, facilitating effective traffic filtering and mitigation of network threats.
Procedure
|
Step 1 |
Use the show flowspec ipv4 detail command to verify the Flowspec flow information and traffic statistics for IPv4. Example: |
|
Step 2 |
Use the show flowspec ipv6 detail command to verify the Flowspec flow information and traffic statistics for IPv6. Example: |
|
Step 3 |
Use the show flowspec vrf customer_1 ipv4 detail command to verify the Flowspec flow information and statistics for IPv4 within the specified VRF. Example: |
|
Step 4 |
Use the show flowspec vrf customer_1 ipv6 detail command to verify the Flowspec flow information and statistics for IPv6 within the specified VRF. Example: |
|
Step 5 |
Use the show flowspec ipv4 nlri command to verify the NLRI in hex format for IPv4 Flowspec routes. Example: |
|
Step 6 |
Use the show flowspec ipv6 nlri command to verify the NLRI in hex format for IPv6 Flowspec routes. Example: |
|
Step 7 |
Use the show flowspec vrf customer_1 ipv4 nlri command to verify the NLRI in hex format for IPv4 Flowspec routes within the specified VRF. Example: |
|
Step 8 |
Use the show flowspec vrf customer_1 ipv6 nlri command to verify the NLRI in hex format for IPv6 Flowspec routes within the specified VRF. Example: |
|
Step 9 |
Use the show policy-map transient type pbr command to verify the policy-map dynamically created for Flowspec-based traffic policies. Example: |
The show outputs provides the user with the visibility into the Flowspec environment, facilitating validation and maintenance of security policies within the BGP routing framework.
Verify the BGP flowspec on the client
Verify the correct reception, installation, and propagation of BGP Flowspec routes for IPv4, IPv6, VPNv4, and VPNv6 address families. Confirm that Flowspec information exchanges properly with BGP peers.
Before you begin
Ensure that you have appropriate user privileges to execute privileged EXEC mode commands.
Follow these steps to verify the BGP flowspec on the client.
Procedure
|
Step 1 |
Use the show bgp ipv4 flowspec command to verify BGP Flowspec routes for the IPv4 address family. Example: |
|
Step 2 |
Use the show bgp ipv6 flowspec command to verify BGP Flowspec routes for the IPv6 address family. Example: |
|
Step 3 |
Use the show bgp vpnv4 flowspec command to verify BGP Flowspec routes for VPNv4 address families. Example: |
|
Step 4 |
Use the show bgp vpnv6 flowspec command to verify BGP Flowspec routes for VPNv6 address families. Example: |
|
Step 5 |
Use the show bgp ipv6 flowspec summary command to view a summary of BGP Flowspec information for IPv6. Example: |
|
Step 6 |
Use the show bgp vpnv4 flowspec summary command to view a summary of BGP Flowspec information for VPNv4. Example: |
|
Step 7 |
Use the show bgp vpnv6 flowspec summary command to view a summary of BGP Flowspec information for VPNv6. Example: |
|
Step 8 |
Use the show flowspec vrf all afi-all summary command to view a summary of Flowspec routes and service policies across all VRFs and address families. Example: |
|
Step 9 |
Use the show policy-map transient targets type pbr command to view a summary of interfaces which have Flowspec policies programmed. Example: |
The show outputs confirm that BGP Flowspec routes for IPv4, IPv6, VPNv4, and VPNv6 address families are present and match the expected destinations and policies. Additionally, the summary commands show that Flowspec routes are being successfully received from specific BGP neighbors, verifying correct propagation and peering.



 Feedback
Feedback