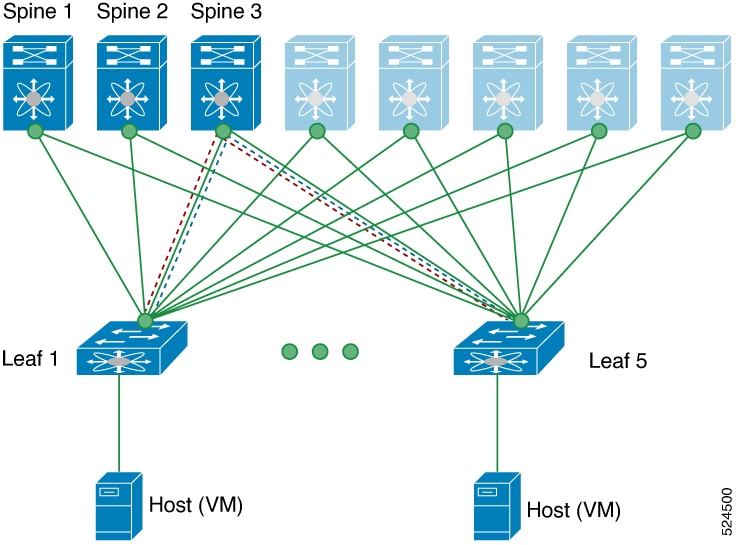
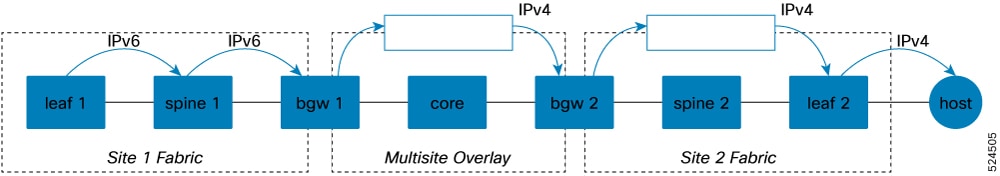
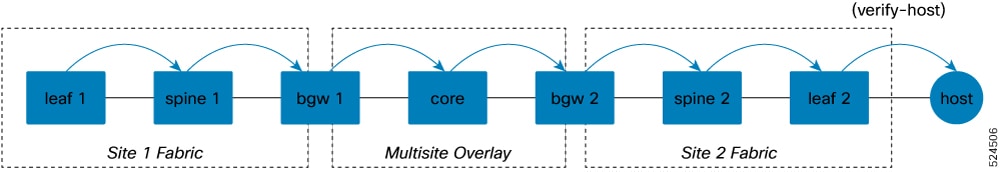
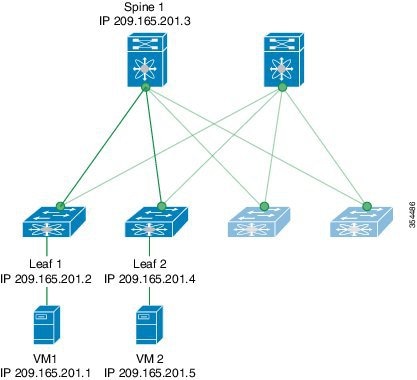
VXLAN OAM protocols
A VXLAN OAM protocol is a network protocol that
-
enhances the management of VXLAN overlay networks during installation, monitoring, and troubleshooting
-
provides tools similar to ping, traceroute, or pathtrace to help diagnose problems in VXLAN networks, and
-
uses diagnostic channels to trace destinations and carry vital information.
VXLAN OAM is also referred to as NGOAM (Next Generation OAM).
VXLAN OAM Tools
The VXLAN OAM tools are categorized as shown in the table. For more information on OAM tools, see Fault isolation and verification tools.
|
Category |
Tools |
|---|---|
|
Fault Verification |
Loopback Message |
|
Fault Isolation |
Pathtrace Message |
VXLAN OAM Payloads
A VXLAN OAM payload is a network protocol element that
-
supports operations, administration, and maintenance functions in overlay networks
-
includes multiple channel types to enable identification of packet payloads, and
-
utilizes reserved identifiers for accurate protocol recognition.
The VXLAN OAM payload supports channel types such as:
-
Conventional ICMP channel: Enables communication with devices using standard ICMP.
-
NVO3 draft Tissa channel: Facilitates advanced diagnostics and communications with supported hosts or switches.
-
Reserved OAM Ether-Type: Identifies OAM packets by protocol encapsulation.
-
Reserved source MAC address: Uses a well-known MAC value for packet recognition.
-
A VXLAN OAM payload using the reserved OAM Ether-Type field to transmit diagnostic data between overlay network endpoints.
A VXLAN data packet carrying user application data rather than OAM information is not considered a VXLAN OAM payload.
VXLAN OAM payloads are like specialized envelopes used for official system communications, distinct from regular mail carrying personal messages.
Supported platforms and releases for VXLAN NGOAM
This topic lists the Cisco Nexus platforms and the minimum software releases that support VXLAN NGOAM and their limitations if any.
Guidelines and limitations for VXLAN NGOAM
Beginning with Cisco NX-OS Release 10.2(3)F, you do not have to enable the VXLAN feature using the feature nv overlay command to use the NGOAM feature on intermediate nodes.
Supported platforms and releases
|
Supported Release |
Supported Platform |
|---|---|
|
9.3(3) and later |
Cisco Nexus 9300-FX/FX2/GX Series switches |
|
9.3(5) and later |
Cisco Nexus 9300-FX3 Series switches |
|
10.2(3)F and later |
Cisco Nexus 9300-GX2 Series switches |
|
10.4(1)F and later |
Cisco Nexus 9332D-H2R switches |
|
10.4(2)F and later |
Cisco Nexus 93400LD-H1 switches |
|
10.4(3)F and later |
Cisco Nexus 9364C-H1 switches Cisco Nexus 9800 Series switches |
|
10.5(2)F and later |
Cisco Nexus 9500 platform switches with N9K-X9736C-FX3 line card |
|
10.5(3)F and later |
Cisco Nexus 9364E-SG2-Q and 9364E-SG2-O switches |
|
Platform |
Release |
|---|---|
|
Cisco Nexus 9336C-SE1 switches |
10.6(1)F |
|
Cisco Nexus 9396Y12C-SE1 and N9396T12C-SE1 switches |
10.6(2)F |
|
Platform |
Release |
|---|---|
|
Cisco N9324C-SE1U and N9348Y2C6D-SE1U Smart switches |
10.6(2)F |
Configure the VXLAN NGOAM
Enable VXLAN Network Operations, Administration, and Maintenance (NGOAM) on a Cisco Nexus switch to support OAM operations and monitoring for VXLAN deployments.
Follow these steps to configure the VXLAN NGOAM on Cisco Nexus switches.
Before you begin
Before you begin, ensure that the VXLAN configuration is complete.
Procedure
|
Step 1 |
Enable the NGOAM feature in global configuration mode using the Example: |
|
Step 2 |
(Optional) Verify the NGOAM configuration with the Example: |
Configure an NGOAM profile
Enable and configure a Network Generic OAM (NGOAM) profile on Cisco Nexus switches for network monitoring and diagnostics.
Perform this task to implement NGOAM features for advanced monitoring and service operations within your Cisco Nexus environment.
Before you begin
Before you begin, ensure the feature ngoam configuration is enabled.
Procedure
|
Step 1 |
Run the ngoam profile profile-id command in global configuration mode to create and enable an NGOAM profile. Example:Profile ID range: 1 to 1023. |
|
Step 2 |
Configure the required NGOAM profile options using the relevant sub-commands.
Example: |
|
Step 3 |
Run the show running-config ngoam command to verify the NGOAM profile configuration. Example:NGOAM configuration placement in show running-config command output has been updated. Previously, NGOAM configurations appeared before interface configurations. Beginning with Cisco NX-OS Release, 10.6(1)F NGOAM configurations appears after interface-level configurations in the show running-config command output.
|
The NGOAM profile is configured and ready for network monitoring operations.
What to do next
Review the NGOAM configuration in the running config and proceed with additional OAM diagnostics as needed.


 Feedback
Feedback