Certificates
A certificate is an electronic document that
-
identifies an individual, a server, a company, or an entity
-
associates the entity with a unique key, and
-
is digitally signed by an issuer (Certificate Authority or self-signed) to enable secure communication.
When a certificate is created with a public key, a matching private key is also generated. In TLS, the public key is used to encrypt data being sent to the entity and the private key is used to decrypt.
In a TLS exchange, a hierarchy of certificates is used to verify the validity of the certificate's issuer. This hierarchy is called a trust-chain and consists of three types of entities: a root CA certificate (self-signed), possibly multiple levels of intermediate CA certificates, and a server (or client) certificate (end-entity). The intermediate certificates act as a “link of trust” linking the server certificates to the CA’s root certificate and providing additional layers of security. The root certificate's private key signs and issues the next certificate in the chain. Subsequently, the private key for each certificate in the trust chain signs and issues the following certificate, continuing until the end-entity certificate is signed. The end-entity certificate is the last certificate in the chain. It is used as a client or server certificate.How are certificates used in Cisco Crosswork Planning
Cisco Crosswork Planning uses the TLS protocol for secure communication between devices and components. TLS uses X.509 certificates to securely authenticate devices and encrypt data to ensure its integrity from source to destination. Cisco Crosswork Planning uses both generated certificates and certificates uploaded by clients. Uploaded certificates can be purchased from Certificate Authorities (CA) or be self-signed. For example, the system's VM-hosted web server and the client browser-based user interface communicate with each other using the system-generated X.509 certificates exchanged over TLS.
The Certificate Management page () allows you to view, upload, and modify certificates. Certificate management page displays the default certificates provided by Cisco Crosswork Planning.
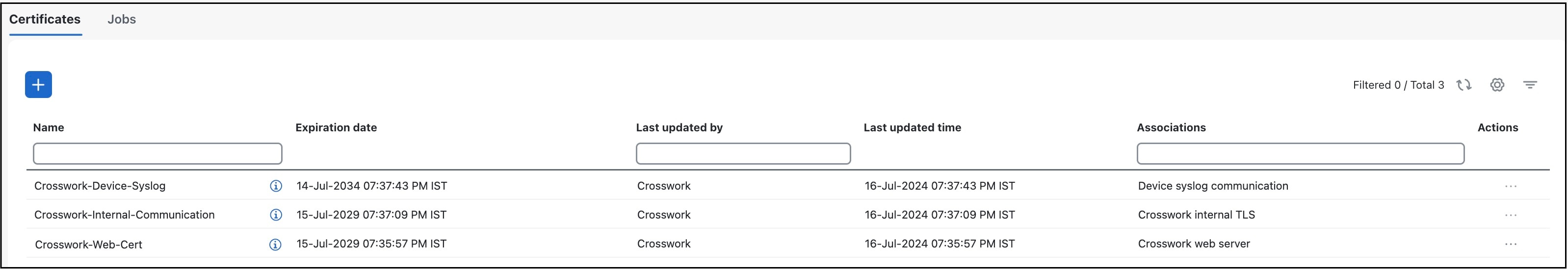
Certificate types and usage
Certificates in Cisco Crosswork Planning are classified into various roles with different properties depending on their use case as shown in this table.
|
Role |
UI name |
Description |
Server |
Client |
Allowed operations |
Default expiry |
Allowed expiry |
|---|---|---|---|---|---|---|---|
|
Crosswork Internal TLS |
Crosswork-Internal- Communication |
|
Crosswork |
Crosswork |
Download |
5 years |
— |
|
Crosswork Web Server |
Crosswork-Web-Cert Server Authentication |
|
Crosswork Web Server |
User Browser or API Client |
|
5 years |
30 days to 5 years |
|
Crosswork Device Syslog |
Crosswork-Device-Syslog |
|
Device |
Download |
5 years |
— |
There are two category roles in Crosswork:
-
Roles that allow you to upload or download trust chains only
-
Roles that allow you to upload or download both the trust chain and an intermediate certificate and key
Add a new certificate
This topic describes how to add a new certificate for the Secure LDAP communication role.
In this process, you upload the trust chain of the secure LDAP certificate. This trust chain is used by Crosswork to authenticate the secure LDAP server. Once this trust chain is uploaded and propagated within Crosswork, you can add the LDAP server (see Configure LDAP servers) and associate the certificate.
 Note |
Cisco Crosswork does not receive a web certificate directly. It accepts an intermediate CA and intermediate key to create a new web certificate, and apply it to the Web Gateway. |
Before you begin
-
Ensure that the certificate file is in Privacy Enhanced Mail (PEM) format and easily accessible.
-
Uploaded Trust chain files may contain the entire hierarchy (root CA and intermediate certificates) in the same file. In some cases, multiple chains are also allowed in the same file..
-
Ensure the intermediate keys are either in the PKCS1 or PKCS8 format.
-
Ensure that the tyk service is in a healthy state.
-
For information on certificate types and usage, see Certificate types and usage.
Procedure
|
Step 1 |
From the main menu, choose and click |
||
|
Step 2 |
In the Certificate name field, enter a unique name for the certificate. |
||
|
Step 3 |
From the Certificate role drop-down list, select Secure LDAP communication..
|
||
|
Step 4 |
Click Browse and navigate to the certificate trustchain. |
||
|
Step 5 |
Click Save. |
After you upload the certificate, the Crosswork Cert manager accepts, validates, and generates the server certificate. Upon successful validation, an alarm ("Crosswork Web Server Restart") indicates that the certificate will be applied. The Certificate Management UI then logs out automatically and applies the certificate to the Web Gateway. The new certificate can be checked by clicking the lock <Not Secure>/<secure> icon next to https://<crosswork_ip>:30603 in the URL.
Edit a certificate
This topic describes how to edit a certificate in Cisco Crosswork Planning.
You can edit a certificate to
-
add or remove connection destinations
-
upload certificates, or
-
replace expired or misconfigured certificates.
You can edit only the user-provided certificates and web certificates. You cannot modify the other system certificates provided by Cisco Crosswork, and they will not be available for selection.
Before you begin
-
Updating the certificate can disrupt the existing trust chain of certificates used for client authentication if enabled, so proceed with caution.
-
Restart the Crosswork server during this process. The restart will take several minutes to complete.
-
Set the AAA mode to Local to enable client authentication.
Procedure
|
Step 1 |
From the main menu, choose . The Certificate Management page opens. |
|
Step 2 |
To update a certificate:
|
|
Step 3 |
To enable the client certificate authentication of a web certificate: |
|
Step 4 |
To update certificate and configure client authentication in a single step: |
Download a certificate
This topic describes how to download a certificate to your local system.
Procedure
|
Step 1 |
From the main menu, choose . The Certificate Management page opens. |
|
Step 2 |
Click |
|
Step 3 |
To download the root certificate or the intermediate certificate separately, click |
|
Step 4 |
To download all the certificates at once, click Export all. |
Update a web certificate using Certificate Signing Request (CSR)
Starting with version 7.0.1, Cisco Crosswork Planning enables updating web certificates via a Certificate Signing Request (CSR) to enhance trust and security. This approach allows you to obtain a certificate signed by an Enterprise or Commercial CA without exposing the private key outside of Cisco Crosswork Planning.
Before you begin
-
Updating the certificate may disrupt the existing trust chain of certificates used for client authentication if enabled.
-
As part of this process, you need to restart the Crosswork server, which can take several minutes to complete.
-
Set the AAA mode to Local to enable client authentication.
Procedure
|
Step 1 |
From the main menu, choose . |
|
Step 2 |
Click |
|
Step 3 |
Create a CSR to submit to the CA. |
|
Step 4 |
After generating the CSR, click Download to download it. Then, use the CSR to get a signed certificate from your CA. 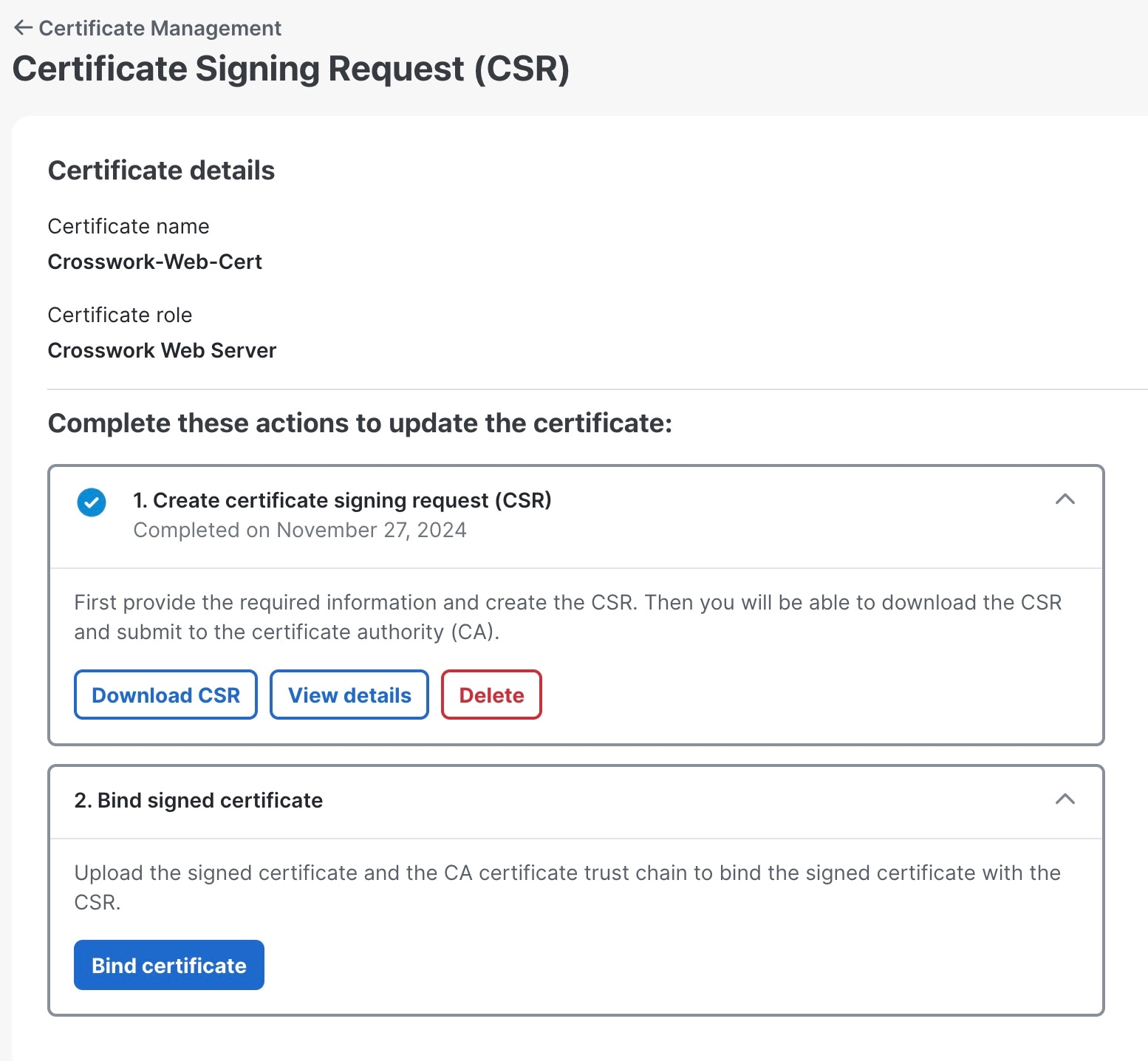
|
|
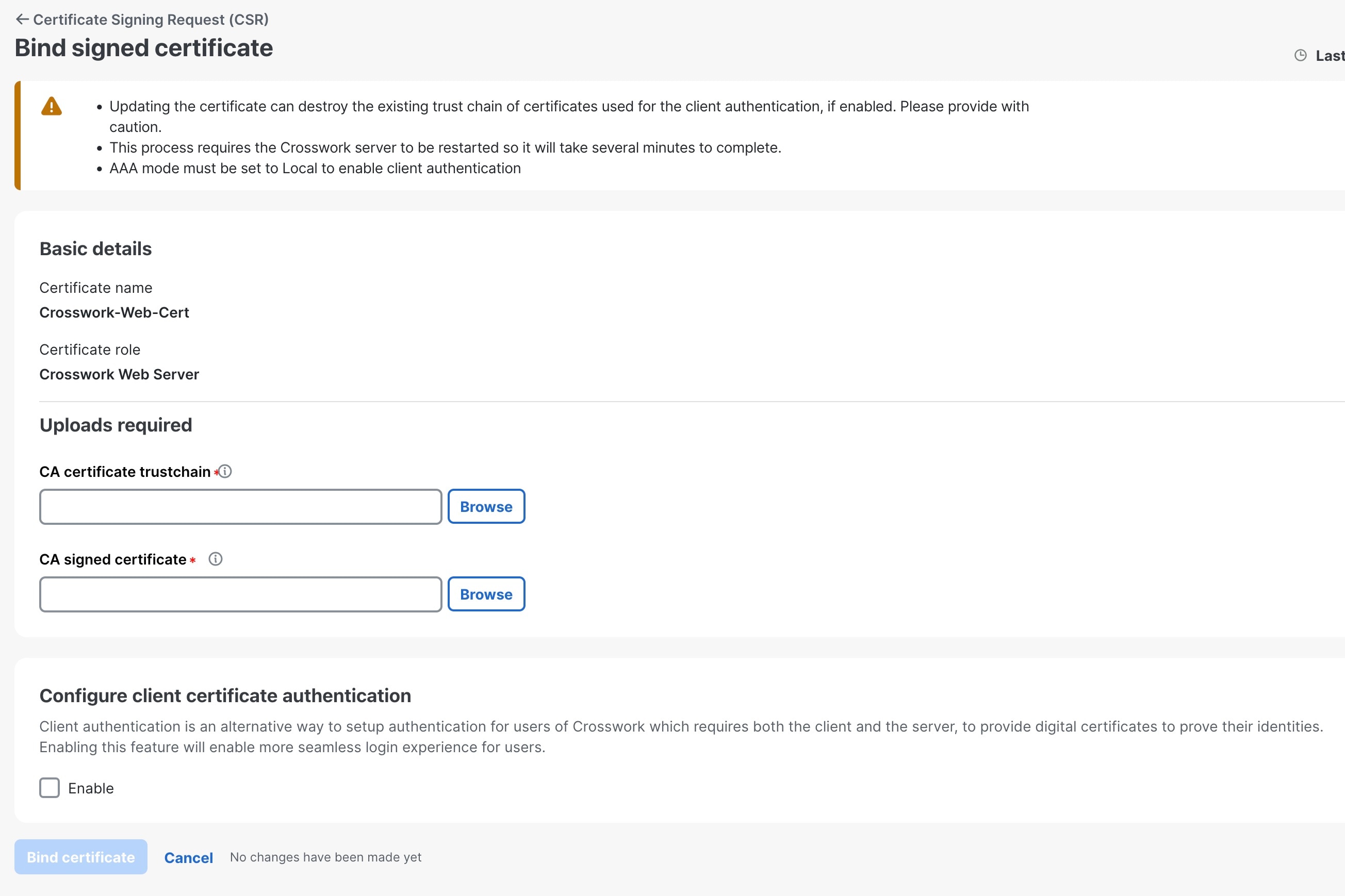
Step 5 |
Upload the CA-signed certificate and the CA certificate trust chain to bind the certificate. |
The Cisco Crosswork Planning's web certificate is updated with the CA-signed certificate and trust chain after server restart.


 Feedback
Feedback