- Preface
- Using the Command-Line Interface
-
- Configuring Spanning Tree Protocol
- Configuring Multiple Spanning-Tree Protocol
- Configuring Optional Spanning-Tree Features
- Configuring EtherChannels
- Configuring Link-State Tracking
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring UniDirectional Link Detection
- Configuring Resilient Ethernet Protocol
-
- Security Features Overview
- Preventing Unauthorized Access
- Controlling Switch Access with Passwords and Privilege Levels
- Configuring TACACS+
- Configuring RADIUS
- Configuring Kerberos
- Configuring Local Authentication and Authorization
- Configuring Secure Shell (SSH)
- Configuring Secure Socket Layer HTTP
- Configuring IPv4 ACLs
- Configuring IPv6 ACLs
- Configuring DHCP
- Configuring IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Port-Based Traffic Control
- Configuring IPv6 First Hop Security
- Configuring Cisco TrustSec
- Configuring FIPS
- Index
Consolidated Platform Configuration Guide, Cisco IOS XE 15.2(2)E (Catalyst 2960-XR Switch)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 23, 2014
Chapter: Configuring IP Unicast Routing
- Finding Feature Information
- Information About Configuring IP Unicast Routing
- Information About IP Routing
- How to Configure IP Routing
- How to Configure IP Addressing
Configuring IP Unicast Routing
- Finding Feature Information
- Information About Configuring IP Unicast Routing
- Information About IP Routing
- How to Configure IP Routing
- How to Configure IP Addressing
- Monitoring and Maintaining IP Addressing
- How to Configure IP Unicast Routing
- Information About RIP
- How to Configure RIP
- Configuration Example for Summary Addresses and Split Horizon
- Information About OSPF
- How to Configure OSPF
- Monitoring OSPF
- Configuration Examples for OSPF
- Information About EIGRP
- Configuring Unicast Reverse Path Forwarding
- Protocol-Independent Features
- Monitoring and Maintaining the IP Network
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Information About Configuring IP Unicast Routing
This module describes how to configure IP Version 4 (IPv4) unicast routing on the switch.
A switch stack operates and appears as a single router to the rest of the routers in the network. Basic routing functions, including static routing and the Routing Information Protocol (RIP), are available with IP Lite .
 Note | In addition to IPv4 traffic, you can also enable IP Version 6 (IPv6) unicast routing and configure interfaces to forward IPv6 traffic. |
Information About IP Routing
In some network environments, VLANs are associated with individual networks or subnetworks. In an IP network, each subnetwork is mapped to an individual VLAN. Configuring VLANs helps control the size of the broadcast domain and keeps local traffic local. However, network devices in different VLANs cannot communicate with one another without a Layer 3 device (router) to route traffic between the VLAN, referred to as inter-VLAN routing. You configure one or more routers to route traffic to the appropriate destination VLAN.
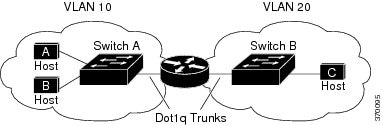
When Host A in VLAN 10 needs to communicate with Host B in VLAN 10, it sends a packet addressed to that host. Switch A forwards the packet directly to Host B, without sending it to the router.
When Host A sends a packet to Host C in VLAN 20, Switch A forwards the packet to the router, which receives the traffic on the VLAN 10 interface. The router checks the routing table, finds the correct outgoing interface, and forwards the packet on the VLAN 20 interface to Switch B. Switch B receives the packet and forwards it to Host C.
- Types of Routing
- IP Routing and Switch Stacks
- Classless Routing
- Address Resolution
- Proxy ARP
- ICMP Router Discovery Protocol
- Broadcast Packet Handling
- IP Broadcast Flooding
Types of Routing
Routers and Layer 3 switches can route packets in these ways:
Default routing refers to sending traffic with a destination unknown to the router to a default outlet or destination.
Static unicast routing forwards packets from predetermined ports through a single path into and out of a network. Static routing is secure and uses little bandwidth, but does not automatically respond to changes in the network, such as link failures, and therefore, might result in unreachable destinations. As networks grow, static routing becomes a labor-intensive liability.
Switches running the LAN base feature set support 16 user-configured static routes, in addition to any default routes used for the management interface. The LAN base image supports static routing only on SVIs.
Dynamic routing protocols are used by routers to dynamically calculate the best route for forwarding traffic. There are two types of dynamic routing protocols:
-
Routers using distance-vector protocols maintain routing tables with distance values of networked resources, and periodically pass these tables to their neighbors. Distance-vector protocols use one or a series of metrics for calculating the best routes. These protocols are easy to configure and use.
-
Routers using link-state protocols maintain a complex database of network topology, based on the exchange of link-state advertisements (LSAs) between routers. LSAs are triggered by an event in the network, which speeds up the convergence time or time required to respond to these changes. Link-state protocols respond quickly to topology changes, but require greater bandwidth and more resources than distance-vector protocols.
Distance-vector protocols supported by the switch are Routing Information Protocol (RIP), which uses a single distance metric (cost) to determine the best path. The switch also supports the Open Shortest Path First (OSPF) link-state protocol, which adds some link-state routing features to traditional Interior Gateway Routing Protocol (IGRP) to improve efficiency.
IP Routing and Switch Stacks
A switch stack appears to the network as a single switch, regardless of which switch in the stack is connected to a routing peer.
The active switch performs these functions:
-
It sends routing protocol messages and updates to other routers.
-
It processes routing protocol messages and updates received from peer routers.
-
It generates, maintains, and distributes the distributed Cisco Express Forwarding (dCEF) database to all stack members. The routes are programmed on all switches in the stack bases on this database.
-
The MAC address of the active switch is used as the router MAC address for the whole stack, and all outside devices use this address to send IP packets to the stack.
-
All IP packets that require software forwarding or processing go through the CPU of the active switch.
Stack members perform these functions:
-
They act as routing standby switches, ready to take over in case they are elected as the new active switch if the active switch fails.
If a active switch fails, the stack detects that the active switch is down and elects one of the stack members to be the new active switch. During this period, except for a momentary interruption, the hardware continues to forward packets with no active protocols.
However, even though the switch stack maintains the hardware identification after a failure, the routing protocols on the router neighbors might flap during the brief interruption before the active switch restarts. Routing protocols such as OSPF and EIGRP need to recognize neighbor transitions.
Upon election, the new active switch performs these functions:
-
It starts generating, receiving, and processing routing updates.
-
It builds routing tables, generates the CEF database, and distributes it to stack members.
-
It uses its MAC address as the router MAC address. To notify its network peers of the new MAC address, it periodically (every few seconds for 5 minutes) sends a gratuitous ARP reply with the new router MAC address.
-
It attempts to determine the reachability of every proxy ARP entry by sending an ARP request to the proxy ARP IP address and receiving an ARP reply. For each reachable proxy ARP IP address, it generates a gratuitous ARP reply with the new router MAC address. This process is repeated for 5 minutes after a new active switch election.

Caution
Partitioning of the switch stack into two or more stacks might lead to undesirable behavior in the network.
If the switch is reloaded, then all the ports on that switch go down and there is a loss of traffic for the interfaces involved in routing.
Classless Routing
By default, classless routing behavior is enabled on the Switch when it is configured to route. With classless routing, if a router receives packets for a subnet of a network with no default route, the router forwards the packet to the best supernet route. A supernet consists of contiguous blocks of Class C address spaces used to simulate a single, larger address space and is designed to relieve the pressure on the rapidly depleting Class B address space.
In the figure, classless routing is enabled. When the host sends a packet to 120.20.4.1, instead of discarding the packet, the router forwards it to the best supernet route. If you disable classless routing and a router receives packets destined for a subnet of a network with no network default route, the router discards the packet.
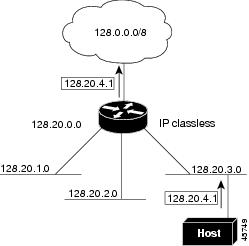
In the figure , the router in network 128.20.0.0 is connected to subnets 128.20.1.0, 128.20.2.0, and 128.20.3.0. If the host sends a packet to 120.20.4.1, because there is no network default route, the router discards the packet.
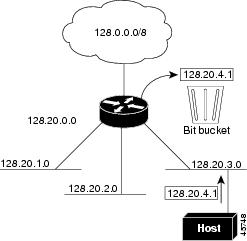
To prevent the Switch from forwarding packets destined for unrecognized subnets to the best supernet route possible, you can disable classless routing behavior.
Address Resolution
You can control interface-specific handling of IP by using address resolution. A device using IP can have both a local address or MAC address, which uniquely defines the device on its local segment or LAN, and a network address, which identifies the network to which the device belongs.
 Note | In a switch stack, network communication uses a single MAC address and the IP address of the stack. |
The local address or MAC address is known as a data link address because it is contained in the data link layer (Layer 2) section of the packet header and is read by data link (Layer 2) devices. To communicate with a device on Ethernet, the software must learn the MAC address of the device. The process of learning the MAC address from an IP address is called address resolution. The process of learning the IP address from the MAC address is called reverse address resolution.
The Switch can use these forms of address resolution:
-
Address Resolution Protocol (ARP) is used to associate IP address with MAC addresses. Taking an IP address as input, ARP learns the associated MAC address and then stores the IP address/MAC address association in an ARP cache for rapid retrieval. Then the IP datagram is encapsulated in a link-layer frame and sent over the network. Encapsulation of IP datagrams and ARP requests or replies on IEEE 802 networks other than Ethernet is specified by the Subnetwork Access Protocol (SNAP).
-
Proxy ARP helps hosts with no routing tables learn the MAC addresses of hosts on other networks or subnets. If the Switch (router) receives an ARP request for a host that is not on the same interface as the ARP request sender, and if the router has all of its routes to the host through other interfaces, it generates a proxy ARP packet giving its own local data link address. The host that sent the ARP request then sends its packets to the router, which forwards them to the intended host.
The Switch also uses the Reverse Address Resolution Protocol (RARP), which functions the same as ARP does, except that the RARP packets request an IP address instead of a local MAC address. Using RARP requires a RARP server on the same network segment as the router interface. Use the ip rarp-server address interface configuration command to identify the server.
For more information on RARP, see the Cisco IOS Configuration Fundamentals Configuration Guide
Proxy ARP
Proxy ARP, the most common method for learning about other routes, enables an Ethernet host with no routing information to communicate with hosts on other networks or subnets. The host assumes that all hosts are on the same local Ethernet and that they can use ARP to learn their MAC addresses. If a Switch receives an ARP request for a host that is not on the same network as the sender, the Switch evaluates whether it has the best route to that host. If it does, it sends an ARP reply packet with its own Ethernet MAC address, and the host that sent the request sends the packet to the Switch, which forwards it to the intended host. Proxy ARP treats all networks as if they are local and performs ARP requests for every IP address.
ICMP Router Discovery Protocol
Router discovery allows the Switch to dynamically learn about routes to other networks using ICMP router discovery protocol (IRDP). IRDP allows hosts to locate routers. When operating as a client, the Switch generates router discovery packets. When operating as a host, the Switch receives router discovery packets. The Switch can also listen to Routing Information Protocol (RIP) routing updates and use this information to infer locations of routers. The Switch does not actually store the routing tables sent by routing devices; it merely keeps track of which systems are sending the data. The advantage of using IRDP is that it allows each router to specify both a priority and the time after which a device is assumed to be down if no further packets are received.
Each device discovered becomes a candidate for the default router, and a new highest-priority router is selected when a higher priority router is discovered, when the current default router is declared down, or when a TCP connection is about to time out because of excessive retransmissions.
UDP Broadcast Packets and Protocols
User Datagram Protocol (UDP) is an IP host-to-host layer protocol, as is TCP. UDP provides a low-overhead, connectionless session between two end systems and does not provide for acknowledgment of received datagrams. Network hosts occasionally use UDP broadcasts to find address, configuration, and name information. If such a host is on a network segment that does not include a server, UDP broadcasts are normally not forwarded. You can remedy this situation by configuring an interface on a router to forward certain classes of broadcasts to a helper address. You can use more than one helper address per interface.
You can specify a UDP destination port to control which UDP services are forwarded. You can specify multiple UDP protocols. You can also specify the Network Disk (ND) protocol, which is used by older diskless Sun workstations and the network security protocol SDNS.
By default, both UDP and ND forwarding are enabled if a helper address has been defined for an interface. The description for the ip forward-protocol interface configuration command in the Cisco IOS IP Command Reference, Volume 1 of 3: Addressing and Services lists the ports that are forwarded by default if you do not specify any UDP ports.
Broadcast Packet Handling
After configuring an IP interface address, you can enable routing and configure one or more routing protocols, or you can configure the way the Switch responds to network broadcasts. A broadcast is a data packet destined for all hosts on a physical network. The Switch supports two kinds of broadcasting:
-
A directed broadcast packet is sent to a specific network or series of networks. A directed broadcast address includes the network or subnet fields.
-
A flooded broadcast packet is sent to every network.

Note
You can also limit broadcast, unicast, and multicast traffic on Layer 2 interfaces by using the storm-control interface configuration command to set traffic suppression levels.
Routers provide some protection from broadcast storms by limiting their extent to the local cable. Bridges (including intelligent bridges), because they are Layer 2 devices, forward broadcasts to all network segments, thus propagating broadcast storms. The best solution to the broadcast storm problem is to use a single broadcast address scheme on a network. In most modern IP implementations, you can set the address to be used as the broadcast address. Many implementations, including the one in the Switch, support several addressing schemes for forwarding broadcast messages.
IP Broadcast Flooding
You can allow IP broadcasts to be flooded throughout your internetwork in a controlled fashion by using the database created by the bridging STP. Using this feature also prevents loops. To support this capability, bridging must be configured on each interface that is to participate in the flooding. If bridging is not configured on an interface, it still can receive broadcasts. However, the interface never forwards broadcasts it receives, and the router never uses that interface to send broadcasts received on a different interface.
Packets that are forwarded to a single network address using the IP helper-address mechanism can be flooded. Only one copy of the packet is sent on each network segment.
To be considered for flooding, packets must meet these criteria. (Note that these are the same conditions used to consider packet forwarding using IP helper addresses.)
-
The packet must be a TFTP, DNS, Time, NetBIOS, ND, or BOOTP packet, or a UDP specified by the ip forward-protocol udp global configuration command.
-
The time-to-live (TTL) value of the packet must be at least two.
A flooded UDP datagram is given the destination address specified with the ip broadcast-address interface configuration command on the output interface. The destination address can be set to any address. Thus, the destination address might change as the datagram propagates through the network. The source address is never changed. The TTL value is decremented.
When a flooded UDP datagram is sent out an interface (and the destination address possibly changed), the datagram is handed to the normal IP output routines and is, therefore, subject to access lists, if they are present on the output interface.
In the Switch, the majority of packets are forwarded in hardware; most packets do not go through the Switch CPU. For those packets that do go to the CPU, you can speed up spanning tree-based UDP flooding by a factor of about four to five times by using turbo-flooding. This feature is supported over Ethernet interfaces configured for ARP encapsulation.
How to Configure IP Routing
By default, IP routing is disabled on the Switch, and you must enable it before routing can take place. For detailed IP routing configuration information, see the Cisco IOS IP Configuration Guide.
In the following procedures, the specified interface must be one of these Layer 3 interfaces:
-
A routed port: a physical port configured as a Layer 3 port by using the no switchport interface configuration command.
-
A switch virtual interface (SVI): a VLAN interface created by using the interface vlan vlan_id global configuration command and by default a Layer 3 interface.
-
An EtherChannel port channel in Layer 3 mode: a port-channel logical interface created by using the interface port-channel port-channel-number global configuration command and binding the Ethernet interface into the channel group. For more information, see the “Configuring Layer 3 EtherChannels” chapter in the Layer 2 Configuration Guide.

Note
The switch does not support tunnel interfaces for unicast routed traffic.
All Layer 3 interfaces on which routing will occur must have IP addresses assigned to them.
 Note | A Layer 3 switch can have an IP address assigned to each routed port and SVI. |
How to Configure IP Addressing
A required task for configuring IP routing is to assign IP addresses to Layer 3 network interfaces to enable the interfaces and allow communication with the hosts on those interfaces that use IP. The following sections describe how to configure various IP addressing features. Assigning IP addresses to the interface is required; the other procedures are optional.
- Default IP Addressing Configuration
- Assigning IP Addresses to Network Interfaces
- Configuring Address Resolution Methods
- Routing Assistance When IP Routing is Disabled
- Configuring Broadcast Packet Handling
Default IP Addressing Configuration
Assigning IP Addresses to Network Interfaces
An IP address identifies a location to which IP packets can be sent. Some IP addresses are reserved for special uses and cannot be used for host, subnet, or network addresses. RFC 1166, “Internet Numbers,” contains the official description of IP addresses.
An interface can have one primary IP address. A mask identifies the bits that denote the network number in an IP address. When you use the mask to subnet a network, the mask is referred to as a subnet mask. To receive an assigned network number, contact your Internet service provider.
Using Subnet Zero
Subnetting with a subnet address of zero is strongly discouraged because of the problems that can arise if a network and a subnet have the same addresses. For example, if network 131.108.0.0 is subnetted as 255.255.255.0, subnet zero would be written as 131.108.0.0, which is the same as the network address.
You can use the all ones subnet (131.108.255.0) and even though it is discouraged, you can enable the use of subnet zero if you need the entire subnet space for your IP address.
Use the no ip subnet-zero global configuration command to restore the default and disable the use of subnet zero.
Disabling Classless Routing
To prevent the Switch from forwarding packets destined for unrecognized subnets to the best supernet route possible, you can disable classless routing behavior.
Configuring Address Resolution Methods
You can perform the following tasks to configure address resolution.
Defining a Static ARP Cache
ARP and other address resolution protocols provide dynamic mapping between IP addresses and MAC addresses. Because most hosts support dynamic address resolution, you usually do not need to specify static ARP cache entries. If you must define a static ARP cache entry, you can do so globally, which installs a permanent entry in the ARP cache that the Switch uses to translate IP addresses into MAC addresses. Optionally, you can also specify that the Switch respond to ARP requests as if it were the owner of the specified IP address. If you do not want the ARP entry to be permanent, you can specify a timeout period for the ARP entry.
Setting ARP Encapsulation
By default, Ethernet ARP encapsulation (represented by the arpa keyword) is enabled on an IP interface. You can change the encapsulation methods to SNAP if required by your network.
To disable an encapsulation type, use the no arp arpa or no arp snap interface configuration command.
Enabling Proxy ARP
By default, the Switch uses proxy ARP to help hosts learn MAC addresses of hosts on other networks or subnets.
Routing Assistance When IP Routing is Disabled
These mechanisms allow the Switch to learn about routes to other networks when it does not have IP routing enabled:
Proxy ARP
Proxy ARP is enabled by default. To enable it after it has been disabled, see the “Enabling Proxy ARP” section. Proxy ARP works as long as other routers support it.
Default Gateway
Another method for locating routes is to define a default router or default gateway. All non-local packets are sent to this router, which either routes them appropriately or sends an IP Control Message Protocol (ICMP) redirect message back, defining which local router the host should use. The Switch caches the redirect messages and forwards each packet as efficiently as possible. A limitation of this method is that there is no means of detecting when the default router has gone down or is unavailable.
ICMP Router Discovery Protocol (IRDP)
The only required task for IRDP routing on an interface is to enable IRDP processing on that interface. When enabled, the default parameters apply.
You can optionally change any of these parameters. If you change the maxadvertinterval value, the holdtime and minadvertinterval values also change, so it is important to first change the maxadvertinterval value, before manually changing either the holdtime or minadvertinterval values.
Configuring Broadcast Packet Handling
Perform the tasks in these sections to enable these schemes:
- Enabling Directed Broadcast-to-Physical Broadcast Translation
- Forwarding UDP Broadcast Packets and Protocols
- Establishing an IP Broadcast Address
- Flooding IP Broadcasts
Enabling Directed Broadcast-to-Physical Broadcast Translation
By default, IP directed broadcasts are dropped; they are not forwarded. Dropping IP-directed broadcasts makes routers less susceptible to denial-of-service attacks.
You can enable forwarding of IP-directed broadcasts on an interface where the broadcast becomes a physical (MAC-layer) broadcast. Only those protocols configured by using the ip forward-protocol global configuration command are forwarded.
You can specify an access list to control which broadcasts are forwarded. When an access list is specified, only those IP packets permitted by the access list are eligible to be translated from directed broadcasts to physical broadcasts. For more information on access lists, see the “Information about Network Security with ACLs" section in the Security Configuration Guide.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/2 |
Enters interface configuration mode, and specifies the interface to configure. |
| Step 4 | ip directed-broadcast
[access-list-number]
Example: Switch(config-if)# ip directed-broadcast 103 |
Enables directed broadcast-to-physical broadcast translation on the interface. You can include an access list to control which broadcasts are forwarded. When an access list, only IP packets permitted by the access list can be translated. |
| Step 5 | exit
Example: Switch(config-if)# exit | |
| Step 6 | ip forward-protocol
{udp [port] |
nd |
sdns}
Example: Switch(config)# ip forward-protocol nd |
Specifies which protocols and ports the router forwards when forwarding broadcast packets. |
| Step 7 | end
Example: Switch(config)# end | |
| Step 8 | show ip interface [interface-id]
Example: Switch# show ip interface |
Verifies the configuration on the interface or all interfaces |
| Step 9 | show running-config
Example: Switch# show running-config | |
| Step 10 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Forwarding UDP Broadcast Packets and Protocols
If you do not specify any UDP ports when you configure the forwarding of UDP broadcasts, you are configuring the router to act as a BOOTP forwarding agent. BOOTP packets carry DHCP information.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the Layer 3 interface to configure. |
| Step 4 | ip
helper-address
address
Example: Switch(config-if)# ip helper address 10.1.10.1 |
Enables forwarding and specifies the destination address for forwarding UDP broadcast packets, including BOOTP. |
| Step 5 | exit
Example: Switch(config-if)# exit | |
| Step 6 | ip forward-protocol {udp [port] |
nd |
sdns}
Example: Switch(config)# ip forward-protocol sdns |
Specifies which protocols the router forwards when forwarding broadcast packets. |
| Step 7 | end
Example: Switch(config)# end | |
| Step 8 | show ip interface [interface-id]
Example: Switch# show ip interface gigabitethernet 1/0/1 |
Verifies the configuration on the interface or all interfaces. |
| Step 9 | show running-config
Example: Switch# show running-config | |
| Step 10 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Establishing an IP Broadcast Address
The most popular IP broadcast address (and the default) is an address consisting of all ones (255.255.255.255). However, the Switch can be configured to generate any form of IP broadcast address.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the interface to configure. |
| Step 4 | ip
broadcast-address
ip-address
Example: Switch(config-if)# ip broadcast-address 128.1.255.255 |
Enters a broadcast address different from the default, for example 128.1.255.255. |
| Step 5 | end
Example: Switch(config)# end | |
| Step 6 | show ip interface [interface-id]
Example: Switch# show ip interface |
Verifies the broadcast address on the interface or all interfaces. |
| Step 7 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Flooding IP Broadcasts
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip
forward-protocol spanning-tree
Example: Switch(config)# ip forward-protocol spanning-tree |
Uses the bridging spanning-tree database to flood UDP datagrams. |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show running-config
Example: Switch# show running-config | |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
| Step 7 | configure
terminal
Example: Switch# configure terminal | |
| Step 8 | ip
forward-protocol turbo-flood
Example: Switch(config)# ip forward-protocol turbo-flood |
Uses the spanning-tree database to speed up flooding of UDP datagrams. |
| Step 9 | end
Example: Switch(config)# end | |
| Step 10 | show running-config
Example: Switch# show running-config | |
| Step 11 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Monitoring and Maintaining IP Addressing
When the contents of a particular cache, table, or database have become or are suspected to be invalid, you can remove all its contents by using the clear privileged EXEC commands. The Table lists the commands for clearing contents.
|
Removes one or all entries from the hostname and the address cache. |
|
You can display specific statistics, such as the contents of IP routing tables, caches, and databases; the reachability of nodes; and the routing path that packets are taking through the network. The Table lists the privileged EXEC commands for displaying IP statistics.
|
Displays the default domain name, style of lookup service, name server hosts, and the cached list of hostnames and addresses. |
|
|
Displays the masks used for network addresses and the number of subnets using each mask. |
|
|
Displays the current state of the routing table in summary form. |
How to Configure IP Unicast Routing
Enabling IP Unicast Routing
By default, the Switch is in Layer 2 switching mode and IP routing is disabled. To use the Layer 3 capabilities of the Switch, you must enable IP routing.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip
routing
Example: Switch(config)# ip routing | |
| Step 4 | router
ip_routing_protocol
Example: Switch(config)# router rip |
Specifies an IP routing protocol. This step might include other commands, such as specifying the networks to route with the network (RIP) router configuration command. For information on specific protocols, see sections later in this chapter and to the Cisco IOS IP Configuration Guide. |
| Step 5 | end
Example: Switch(config)# end | |
| Step 6 | show running-config
Example: Switch# show running-config | |
| Step 7 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Example of Enabling IP Routing
This example shows how to enable IP routing :
Switch# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)# ip routing Switch(config-router)# end
What to Do Next
You can now set up parameters for the selected routing protocols as described in these sections:
Information About RIP
The Routing Information Protocol (RIP) is an interior gateway protocol (IGP) created for use in small, homogeneous networks. It is a distance-vector routing protocol that uses broadcast User Datagram Protocol (UDP) data packets to exchange routing information. The protocol is documented in RFC 1058. You can find detailed information about RIP in IP Routing Fundamentals, published by Cisco Press.
 Note | RIP is supported in the IP Lite. |
Using RIP, the Switch sends routing information updates (advertisements) every 30 seconds. If a router does not receive an update from another router for 180 seconds or more, it marks the routes served by that router as unusable. If there is still no update after 240 seconds, the router removes all routing table entries for the non-updating router.
RIP uses hop counts to rate the value of different routes. The hop count is the number of routers that can be traversed in a route. A directly connected network has a hop count of zero; a network with a hop count of 16 is unreachable. This small range (0 to 15) makes RIP unsuitable for large networks.
If the router has a default network path, RIP advertises a route that links the router to the pseudonetwork 0.0.0.0. The 0.0.0.0 network does not exist; it is treated by RIP as a network to implement the default routing feature. The Switch advertises the default network if a default was learned by RIP or if the router has a gateway of last resort and RIP is configured with a default metric. RIP sends updates to the interfaces in specified networks. If an interface’s network is not specified, it is not advertised in any RIP update.
Summary Addresses and Split Horizon
Routers connected to broadcast-type IP networks and using distance-vector routing protocols normally use the split-horizon mechanism to reduce the possibility of routing loops. Split horizon blocks information about routes from being advertised by a router on any interface from which that information originated. This feature usually optimizes communication among multiple routers, especially when links are broken.
How to Configure RIP
Default RIP Configuration
|
Disabled |
|
|
Receives RIP Version 1 and 2 packets; sends Version 1 packets. |
Configuring Basic RIP Parameters
To configure RIP, you enable RIP routing for a network and optionally configure other parameters. On the Switch, RIP configuration commands are ignored until you configure the network number.
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. | ||
| Step 2 | configure
terminal
Example: Switch# configure terminal | |||
| Step 3 | ip
routing
Example: Switch(config)# ip routing |
Enables IP routing. (Required only if IP routing is disabled.) | ||
| Step 4 | router
rip
Example: Switch(config)# router rip |
Enables a RIP routing process, and enter router configuration mode. | ||
| Step 5 | network
network number
Example: Switch(config)# network 12 |
Associates a network with a RIP routing process. You can specify multiple network commands. RIP routing updates are sent and received through interfaces only on these networks.
| ||
| Step 6 | neighbor
ip-address
Example: Switch(config)# neighbor 10.2.5.1 |
(Optional) Defines a neighboring router with which to exchange routing information. This step allows routing updates from RIP (normally a broadcast protocol) to reach nonbroadcast networks. | ||
| Step 7 | offset-list [access-list
number |
name] {in |
out}
offset [type number]
Example: Switch(config)# offset-list 103 in 10 |
(Optional) Applies an offset list to routing metrics to increase incoming and outgoing metrics to routes learned through RIP. You can limit the offset list with an access list or an interface. | ||
| Step 8 | timers
basic
update invalid holddown
flush
Example: Switch(config)# timers basic 45 360 400 300 |
(Optional) Adjusts routing protocol timers. Valid ranges for all timers are 0 to 4294967295 seconds.
| ||
| Step 9 | version {1 |
2}
Example: Switch(config)# version 2 |
(Optional) Configures the switch to receive and send only RIP Version 1 or RIP Version 2 packets. By default, the switch receives Version 1 and 2 but sends only Version 1. You can also use the interface commands ip rip {send | receive} version 1 | 2 | 1 2} to control what versions are used for sending and receiving on interfaces. | ||
| Step 10 | no auto
summary
Example: Switch(config)# no auto summary |
(Optional) Disables automatic summarization. By default, the switch summarizes subprefixes when crossing classful network boundaries. Disable summarization (RIP Version 2 only) to advertise subnet and host routing information to classful network boundaries. | ||
| Step 11 | no
validate-update-source
Example: Switch(config)# no validdate-update-source |
(Optional) Disables validation of the source IP address of incoming RIP routing updates. By default, the switch validates the source IP address of incoming RIP routing updates and discards the update if the source address is not valid. Under normal circumstances, disabling this feature is not recommended. However, if you have a router that is off-network and you want to receive its updates, you can use this command. | ||
| Step 12 | output-delay
delay
Example: Switch(config)# output-delay 8 |
(Optional) Adds interpacket delay for RIP updates sent. By default, packets in a multiple-packet RIP update have no delay added between packets. If you are sending packets to a lower-speed device, you can add an interpacket delay in the range of 8 to 50 milliseconds. | ||
| Step 13 | end
Example: Switch(config)# end | |||
| Step 14 | show ip
protocols
Example: Switch# show ip protocols | |||
| Step 15 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring RIP Authentication
RIP Version 1 does not support authentication. If you are sending and receiving RIP Version 2 packets, you can enable RIP authentication on an interface. The key chain specifies the set of keys that can be used on the interface. If a key chain is not configured, no authentication is performed, not even the default.
The Switch supports two modes of authentication on interfaces for which RIP authentication is enabled: plain text and MD5. The default is plain text.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the interface to configure. |
| Step 4 | ip rip
authentication key-chain
name-of-chain
Example: Switch(config-if)# ip rip authentication key-chain trees | |
| Step 5 | ip rip authentication mode {text |
md5}
Example: Switch(config-if)# ip rip authentication mode md5 |
Configures the interface to use plain text authentication (the default) or MD5 digest authentication. |
| Step 6 | end
Example: Switch(config)# end | |
| Step 7 | show running-config
Example: Switch# show running-config | |
| Step 8 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring Summary Addresses and Split Horizon
 Note | In general, disabling split horizon is not recommended unless you are certain that your application requires it to properly advertise routes. |
If you want to configure an interface running RIP to advertise a summarized local IP address pool on a network access server for dial-up clients, use the ip summary-address rip interface configuration command.
 Note | If split horizon is enabled, neither autosummary nor interface IP summary addresses are advertised. |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the Layer 3 interface to configure. |
| Step 4 | ip address
ip-address
subnet-mask
Example: Switch(config-if)# ip address 10.1.1.10 255.255.255.0 | |
| Step 5 | ip
summary-address rip ip address
ip-network mask
Example: Switch(config-if)# ip summary-address rip ip address 10.1.1.30 255.255.255.0 |
Configures the IP address to be summarized and the IP network mask. |
| Step 6 | no ip split
horizon
Example: Switch(config-if)# no ip split horizon | |
| Step 7 | end
Example: Switch(config)# end | |
| Step 8 | show ip
interface
interface-id
Example: Switch# show ip interface gigabitethernet 1/0/1 | |
| Step 9 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring Split Horizon
Routers connected to broadcast-type IP networks and using distance-vector routing protocols normally use the split-horizon mechanism to reduce the possibility of routing loops. Split horizon blocks information about routes from being advertised by a router on any interface from which that information originated. This feature can optimize communication among multiple routers, especially when links are broken.
 Note | In general, we do not recommend disabling split horizon unless you are certain that your application requires it to properly advertise routes. |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the interface to configure. |
| Step 4 | ip address
ip-address
subnet-mask
Example: Switch(config-if)# ip address 10.1.1.10 255.255.255.0 | |
| Step 5 | no ip
split-horizon
Example: Switch(config-if)# no ip split-horizon | |
| Step 6 | end
Example: Switch(config)# end | |
| Step 7 | show ip
interface
interface-id
Example: Switch# show ip interface gigabitethernet 1/0/1 | |
| Step 8 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuration Example for Summary Addresses and Split Horizon
In this example, the major net is 10.0.0.0. The summary address 10.2.0.0 overrides the autosummary address of 10.0.0.0 so that 10.2.0.0 is advertised out interface Gigabit Ethernet port 2, and 10.0.0.0 is not advertised. In the example, if the interface is still in Layer 2 mode (the default), you must enter a no switchport interface configuration command before entering the ip address interface configuration command.
 Note | If split horizon is enabled, neither autosummary nor interface summary addresses (those configured with the ip summary-address rip router configuration command) are advertised. Switch(config)# router rip Switch(config-router)# interface gigabitethernet1/0/2 Switch(config-if)# ip address 10.1.5.1 255.255.255.0 Switch(config-if)# ip summary-address rip 10.2.0.0 255.255.0.0 Switch(config-if)# no ip split-horizon Switch(config-if)# exit Switch(config)# router rip Switch(config-router)# network 10.0.0.0 Switch(config-router)# neighbor 2.2.2.2 peer-group mygroup Switch(config-router)# end |
Information About OSPF
OSPF is an Interior Gateway Protocol (IGP) designed expressly for IP networks, supporting IP subnetting and tagging of externally derived routing information. OSPF also allows packet authentication and uses IP multicast when sending and receiving packets. The Cisco implementation supports RFC 1253, OSPF management information base (MIB).
The Cisco implementation conforms to the OSPF Version 2 specifications with these key features:
-
Routes learned through any IP routing protocol can be redistributed into another IP routing protocol. At the intradomain level, this means that OSPF can import routes learned through EIGRP and RIP. OSPF routes can also be exported into RIP.
-
Plain text and MD5 authentication among neighboring routers within an area is supported.
-
Configurable routing interface parameters include interface output cost, retransmission interval, interface transmit delay, router priority, router dead and hello intervals, and authentication key.
OSPF typically requires coordination among many internal routers, area border routers (ABRs) connected to multiple areas, and autonomous system boundary routers (ASBRs). The minimum configuration would use all default parameter values, no authentication, and interfaces assigned to areas. If you customize your environment, you must ensure coordinated configuration of all routers.
OSPF for Routed Access
 Note | OSPF is supported in IP Lite. OSPF for Routed Access supports only one OSPFv2 and one OSPFv3 instance with a combined total of 200 dynamically learned routes. The IP Lite image provides OSPF for routed access. However, these restrictions are not enforced in this release. |
With the typical topology (hub and spoke) in a campus environment, where the wiring closets (spokes) are connected to the distribution switch (hub) that forwards all nonlocal traffic to the distribution layer, the wiring closet switch need not hold a complete routing table. A best practice design, where the distribution switch sends a default route to the wiring closet switch to reach interarea and external routes (OSPF stub or totally stub area configuration) should be used when OSPF for Routed Access is used in the wiring closet.
For more details, see the “High Availability Campus Network Design—Routed Access Layer using EIGRP or OSPF” document.
OSPF Area Parameters
You can optionally configure several OSPF area parameters. These parameters include authentication for password-based protection against unauthorized access to an area, stub areas, and not-so-stubby-areas (NSSAs). Stub areas are areas into which information on external routes is not sent. Instead, the area border router (ABR) generates a default external route into the stub area for destinations outside the autonomous system (AS). An NSSA does not flood all LSAs from the core into the area, but can import AS external routes within the area by redistribution.
Route summarization is the consolidation of advertised addresses into a single summary route to be advertised by other areas. If network numbers are contiguous, you can use the area range router configuration command to configure the ABR to advertise a summary route that covers all networks in the range.
Other OSPF Parameters
You can optionally configure other OSPF parameters in router configuration mode.
-
Route summarization: When redistributing routes from other protocols. Each route is advertised individually in an external LSA. To help decrease the size of the OSPF link state database, you can use the summary-address router configuration command to advertise a single router for all the redistributed routes included in a specified network address and mask.
-
Virtual links: In OSPF, all areas must be connected to a backbone area. You can establish a virtual link in case of a backbone-continuity break by configuring two Area Border Routers as endpoints of a virtual link. Configuration information includes the identity of the other virtual endpoint (the other ABR) and the nonbackbone link that the two routers have in common (the transit area). Virtual links cannot be configured through a stub area.
-
Default route: When you specifically configure redistribution of routes into an OSPF routing domain, the route automatically becomes an autonomous system boundary router (ASBR). You can force the ASBR to generate a default route into the OSPF routing domain.
-
Domain Name Server (DNS) names for use in all OSPF show privileged EXEC command displays makes it easier to identify a router than displaying it by router ID or neighbor ID.
-
Default Metrics: OSPF calculates the OSPF metric for an interface according to the bandwidth of the interface. The metric is calculated as ref-bw divided by bandwidth, where ref is 10 by default, and bandwidth (bw) is specified by the bandwidth interface configuration command. For multiple links with high bandwidth, you can specify a larger number to differentiate the cost on those links.
-
Administrative distance is a rating of the trustworthiness of a routing information source, an integer between 0 and 255, with a higher value meaning a lower trust rating. An administrative distance of 255 means the routing information source cannot be trusted at all and should be ignored. OSPF uses three different administrative distances: routes within an area (interarea), routes to another area (interarea), and routes from another routing domain learned through redistribution (external). You can change any of the distance values.
-
Passive interfaces: Because interfaces between two devices on an Ethernet represent only one network segment, to prevent OSPF from sending hello packets for the sending interface, you must configure the sending device to be a passive interface. Both devices can identify each other through the hello packet for the receiving interface.
-
Route calculation timers: You can configure the delay time between when OSPF receives a topology change and when it starts the shortest path first (SPF) calculation and the hold time between two SPF calculations.
-
Log neighbor changes: You can configure the router to send a syslog message when an OSPF neighbor state changes, providing a high-level view of changes in the router.
LSA Group Pacing
The OSPF LSA group pacing feature allows the router to group OSPF LSAs and pace the refreshing, check-summing, and aging functions for more efficient router use. This feature is enabled by default with a 4-minute default pacing interval, and you will not usually need to modify this parameter. The optimum group pacing interval is inversely proportional to the number of LSAs the router is refreshing, check-summing, and aging. For example, if you have approximately 10,000 LSAs in the database, decreasing the pacing interval would benefit you. If you have a very small database (40 to 100 LSAs), increasing the pacing interval to 10 to 20 minutes might benefit you slightly.
Loopback Interfaces
OSPF uses the highest IP address configured on the interfaces as its router ID. If this interface is down or removed, the OSPF process must recalculate a new router ID and resend all its routing information out its interfaces. If a loopback interface is configured with an IP address, OSPF uses this IP address as its router ID, even if other interfaces have higher IP addresses. Because loopback interfaces never fail, this provides greater stability. OSPF automatically prefers a loopback interface over other interfaces, and it chooses the highest IP address among all loopback interfaces.
How to Configure OSPF
Default OSPF Configuration
|
Retransmit interval: 5 seconds. |
|
|
Disabled. When enabled, the default metric setting is 10, and the external route type default is Type 2. |
|
|
Built-in, automatic metric translation, as appropriate for each routing protocol. |
|
|
dist1 (all routes within an area): 110. dist2 (all routes from one area to another): 110. and dist3 (routes from other routing domains): 110. |
|
|
Disabled. All outgoing link-state advertisements (LSAs) are flooded to the interface. |
|
|
No area ID or router ID defined. Retransmit interval: 5 seconds. |
Configuring Basic OSPF Parameters
To enable OSPF, create an OSPF routing process, specify the range of IP addresses to associate with the routing process, and assign area IDs to be associated with that range.
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |||
| Step 2 | router
ospf process-id
Example: Switch(config)# router ospf 15 |
Enables OSPF routing, and enter router configuration mode. The process ID is an internally used identification parameter that is locally assigned and can be any positive integer. Each OSPF routing process has a unique value.
| ||
| Step 3 | network address wildcard-mask
area area-id
Example: Switch(config)# network 10.1.1.1 255.240.0.0 area 20 |
Define an interface on which OSPF runs and the area ID for that interface. You can use the wildcard-mask to use a single command to define one or more multiple interfaces to be associated with a specific OSPF area. The area ID can be a decimal value or an IP address. | ||
| Step 4 | end
Example: Switch(config)# end | |||
| Step 5 | show ip
protocols
Example: Switch# show ip protocols | |||
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring OSPF Interfaces
You can use the ip ospf interface configuration commands to modify interface-specific OSPF parameters. You are not required to modify any of these parameters, but some interface parameters (hello interval, dead interval, and authentication key) must be consistent across all routers in an attached network. If you modify these parameters, be sure all routers in the network have compatible values.
 Note | The ip ospf interface configuration commands are all optional. |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | interface interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the Layer 3 interface to configure. |
| Step 3 | ip
ospf cost
Example: Switch(config-if)# ip ospf 8 |
(Optional) Explicitly specifies the cost of sending a packet on the interface. |
| Step 4 | ip ospf
retransmit-interval seconds
Example: Switch(config-if)# ip ospf transmit-interval 10 |
(Optional) Specifies the number of seconds between link state advertisement transmissions. The range is 1 to 65535 seconds. The default is 5 seconds. |
| Step 5 | ip ospf
transmit-delay seconds
Example: Switch(config-if)# ip ospf transmit-delay 2 |
(Optional) Sets the estimated number of seconds to wait before sending a link state update packet. The range is 1 to 65535 seconds. The default is 1 second. |
| Step 6 | ip ospf
priority number
Example: Switch(config-if)# ip ospf priority 5 |
(Optional) Sets priority to help find the OSPF designated router for a network. The range is from 0 to 255. The default is 1. |
| Step 7 | ip ospf
hello-interval seconds
Example: Switch(config-if)# ip ospf hello-interval 12 |
(Optional) Sets the number of seconds between hello packets sent on an OSPF interface. The value must be the same for all nodes on a network. The range is 1 to 65535 seconds. The default is 10 seconds. |
| Step 8 | ip ospf
dead-interval seconds
Example: Switch(config-if)# ip ospf dead-interval 8 |
(Optional) Sets the number of seconds after the last device hello packet was seen before its neighbors declare the OSPF router to be down. The value must be the same for all nodes on a network. The range is 1 to 65535 seconds. The default is 4 times the hello interval. |
| Step 9 | ip ospf
authentication-key key
Example: Switch(config-if)# ip ospf authentication-key password |
(Optional) Assign a password to be used by neighboring OSPF routers. The password can be any string of keyboard-entered characters up to 8 bytes in length. All neighboring routers on the same network must have the same password to exchange OSPF information. |
| Step 10 | ip ospf message
digest-key keyid
md5 key
Example: Switch(config-if)# ip ospf message digest-key 16 md5 your1pass | |
| Step 11 | ip ospf
database-filter all out
Example: Switch(config-if)# ip ospf database-filter all out |
(Optional) Block flooding of OSPF LSA packets to the interface. By default, OSPF floods new LSAs over all interfaces in the same area, except the interface on which the LSA arrives. |
| Step 12 | end
Example: Switch(config)# end | |
| Step 13 | show ip ospf interface [interface-name]
Example: Switch# show ip ospf interface | |
| Step 14 | show ip ospf
neighbor detail
Example: Switch# show ip ospf neighbor detail |
Displays NSF awareness status of neighbor switch. The output matches one of these examples: |
| Step 15 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring OSPF Area Parameters
 Note | The OSPF area router configuration commands are all optional. |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router
ospf process-id
Example: Switch(config)# router ospf 109 | |
| Step 3 | area
area-id
authentication
Example: Switch(config-router)# area 1 authentication |
(Optional) Allow password-based protection against unauthorized access to the identified area. The identifier can be either a decimal value or an IP address. |
| Step 4 | area
area-id
authentication
message-digest
Example: Switch(config-router)# area 1 authentication message-digest | |
| Step 5 | area
area-id
stub [no-summary]
Example: Switch(config-router)# area 1 stub |
(Optional) Define an area as a stub area. The no-summary keyword prevents an ABR from sending summary link advertisements into the stub area. |
| Step 6 | area
area-id
nssa [no-redistribution] [default-information-originate] [no-summary]
Example: Switch(config-router)# area 1 nssa default-information-originate |
(Optional) Defines an area as a not-so-stubby-area. Every router within the same area must agree that the area is NSSA. Select one of these keywords:
|
| Step 7 | area
area-id
range
address mask
Example: Switch(config-router)# area 1 range 255.240.0.0 |
(Optional) Specifies an address range for which a single route is advertised. Use this command only with area border routers. |
| Step 8 | end
Example: Switch(config)# end | |
| Step 9 | show ip ospf
[process-id]
Example: Switch# show ip ospf |
Displays information about the OSPF routing process in general or for a specific process ID to verify configuration. |
| Step 10 | show ip ospf [process-id
[area-id]]
database
Example: Switch# show ip osfp database |
Displays lists of information related to the OSPF database for a specific router. |
| Step 11 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring Other OSPF Parameters
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router ospf
process-id
Example: Switch(config)# router ospf 10 | |
| Step 3 | summary-address
address mask
Example: Switch(config)# summary-address 10.1.1.1 255.255.255.0 |
(Optional) Specifies an address and IP subnet mask for redistributed routes so that only one summary route is advertised. |
| Step 4 | area
area-id
virtual-link
router-id [hello-interval
seconds] [retransmit-interval
seconds] [trans] [[authentication-key
key] |
message-digest-key
keyid
md5
key]]
Example: Switch(config)# area 2 virtual-link 192.168.255.1 hello-interval 5 |
(Optional) Establishes a virtual link and set its parameters. |
| Step 5 | default-information originate [always] [metric
metric-value] [metric-type
type-value] [route-map
map-name]
Example: Switch(config)# default-information originate metric 100 metric-type 1 |
(Optional) Forces the ASBR to generate a default route into the OSPF routing domain. Parameters are all optional. |
| Step 6 | ip ospf
name-lookup
Example: Switch(config)# ip ospf name-lookup |
(Optional) Configures DNS name lookup. The default is disabled. |
| Step 7 | ip auto-cost
reference-bandwidth
ref-bw
Example: Switch(config)# ip auto-cost reference-bandwidth 5 |
(Optional) Specifies an address range for which a single route will be advertised. Use this command only with area border routers. |
| Step 8 | distance ospf {[inter-area
dist1] [inter-area
dist2] [external
dist3]}
Example: Switch(config)# distance ospf inter-area 150 |
(Optional) Changes the OSPF distance values. The default distance for each type of route is 110. The range is 1 to 255. |
| Step 9 | passive-interface
type number
Example: Switch(config)# passive-interface gigabitethernet 1/0/6 |
(Optional) Suppresses the sending of hello packets through the specified interface. |
| Step 10 | timers throttle
spf
spf-delay spf-holdtime
spf-wait
Example: Switch(config)# timers throttle spf 200 100 100 |
(Optional) Configures route calculation timers.
|
| Step 11 | ospf
log-adj-changes
Example: Switch(config)# ospf log-adj-changes |
(Optional) Sends syslog message when a neighbor state changes. |
| Step 12 | end
Example: Switch(config)# end | |
| Step 13 | show ip ospf [process-id [area-id]]
database
Example: Switch# show ip ospf database |
Displays lists of information related to the OSPF database for a specific router. |
| Step 14 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Changing LSA Group Pacing
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router ospf
process-id
Example: Switch(config)# router ospf 25 | |
| Step 3 | timers
lsa-group-pacing
seconds
Example: Switch(config-router)# timers lsa-group-pacing 15 | |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show running-config
Example: Switch# show running-config | |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring a Loopback Interface
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | interface
loopback 0
Example: Switch(config)# interface loopback 0 |
Creates a loopback interface, and enter interface configuration mode. |
| Step 3 | ip
address address mask
Example: Switch(config-if)# ip address 10.1.1.5 255.255.240.0 | |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show ip
interface
Example: Switch# show ip interface | |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Monitoring OSPF
You can display specific statistics such as the contents of IP routing tables, caches, and databases.
|
show ip ospf [process-id] database [router] [link-state-id] show ip ospf [process-id] database [router] [self-originate] show ip ospf [process-id] database [router] [adv-router [ip-address]] show ip ospf [process-id] database [network] [link-state-id] show ip ospf [process-id] database [summary] [link-state-id] show ip ospf [process-id] database [asbr-summary] [link-state-id] show ip ospf [process-id] database [external] [link-state-id] show ip ospf [process-id area-id] database [database-summary] |
|
|
Displays the internal OSPF routing ABR and ASBR table entries. |
|
Configuration Examples for OSPF
Example: Configuring Basic OSPF Parameters
This example shows how to configure an OSPF routing process and assign it a process number of 109:
Switch(config)# router ospf 109 Switch(config-router)# network 131.108.0.0 255.255.255.0 area 24
Information About EIGRP
Enhanced IGRP (EIGRP) is a Cisco proprietary enhanced version of the IGRP. EIGRP uses the same distance vector algorithm and distance information as IGRP; however, the convergence properties and the operating efficiency of EIGRP are significantly improved.
The convergence technology employs an algorithm referred to as the Diffusing Update Algorithm (DUAL), which guarantees loop-free operation at every instant throughout a route computation and allows all devices involved in a topology change to synchronize at the same time. Routers that are not affected by topology changes are not involved in recomputations.
IP EIGRP provides increased network width. With RIP, the largest possible width of your network is 15 hops. Because the EIGRP metric is large enough to support thousands of hops, the only barrier to expanding the network is the transport-layer hop counter. EIGRP increments the transport control field only when an IP packet has traversed 15 routers and the next hop to the destination was learned through EIGRP. When a RIP route is used as the next hop to the destination, the transport control field is incremented as usual.
EIGRP Stub Routing
The EIGRP stub routing feature reduces resource utilization by moving routed traffic closer to the end user.
 Note | The IP Lite feature set contains EIGRP stub routing capability, which only advertises connected or summary routes from the routing tables to other Switches in the network. The Switch uses EIGRP stub routing at the access layer to eliminate the need for other types of routing advertisements. |
In a network using EIGRP stub routing, the only allowable route for IP traffic to the user is through a Switch that is configured with EIGRP stub routing. The Switch sends the routed traffic to interfaces that are configured as user interfaces or are connected to other devices.
When using EIGRP stub routing, you need to configure the distribution and remote routers to use EIGRP and to configure only the Switch as a stub. Only specified routes are propagated from the Switch. The Switch responds to all queries for summaries, connected routes, and routing updates.
Any neighbor that receives a packet informing it of the stub status does not query the stub router for any routes, and a router that has a stub peer does not query that peer. The stub router depends on the distribution router to send the proper updates to all peers.
In the figure given below, Switch B is configured as an EIGRP stub router. Switches A and C are connected to the rest of the WAN. Switch B advertises connected, static, redistribution, and summary routes to Switch A and C. Switch B does not advertise any routes learned from Switch A (and the reverse).
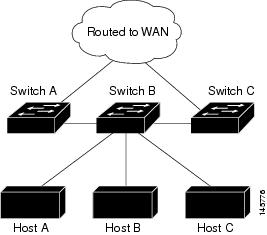
For more information about EIGRP stub routing, see “Configuring EIGRP Stub Routing” section of the Cisco IOS IP Configuration Guide, Volume 2 of 3: Routing Protocols.
Configuring Unicast Reverse Path Forwarding
The unicast reverse path forwarding (unicast RPF) feature helps to mitigate problems that are caused by the introduction of malformed or forged (spoofed) IP source addresses into a network by discarding IP packets that lack a verifiable IP source address. For example, a number of common types of denial-of-service (DoS) attacks, including Smurf and Tribal Flood Network (TFN), can take advantage of forged or rapidly changing source IP addresses to allow attackers to thwart efforts to locate or filter the attacks. For Internet service providers (ISPs) that provide public access, Unicast RPF deflects such attacks by forwarding only packets that have source addresses that are valid and consistent with the IP routing table. This action protects the network of the ISP, its customer, and the rest of the Internet.
 Note |
For detailed IP unicast RPF configuration information, see the Other Security Features chapter in the Cisco IOS Security Configuration Guide.
Protocol-Independent Features
This section describes IP routing protocol-independent features that are available on switches running the IP Lite feature set . For a complete description of the IP routing protocol-independent commands in this chapter, see the “IP Routing Protocol-Independent Commands” chapter of the Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols.
- Distributed Cisco Express Forwarding
- Number of Equal-Cost Routing Paths
- Static Unicast Routes
- Default Routes and Networks
- Route Maps to Redistribute Routing Information
- Policy-Based Routing
- Filtering Routing Information
- Managing Authentication Keys
Distributed Cisco Express Forwarding
Information About Cisco Express Forwarding
Cisco Express Forwarding (CEF) is a Layer 3 IP switching technology used to optimize network performance. CEF implements an advanced IP look-up and forwarding algorithm to deliver maximum Layer 3 switching performance. CEF is less CPU-intensive than fast switching route caching, allowing more CPU processing power to be dedicated to packet forwarding. In a switch stack, the hardware uses distributed CEF (dCEF) in the stack. In dynamic networks, fast switching cache entries are frequently invalidated because of routing changes, which can cause traffic to be process switched using the routing table, instead of fast switched using the route cache. CEF and dCEF use the Forwarding Information Base (FIB) lookup table to perform destination-based switching of IP packets.
The two main components in CEF and dCEF are the distributed FIB and the distributed adjacency tables.
The FIB is similar to a routing table or information base and maintains a mirror image of the forwarding information in the IP routing table. When routing or topology changes occur in the network, the IP routing table is updated, and those changes are reflected in the FIB. The FIB maintains next-hop address information based on the information in the IP routing table. Because the FIB contains all known routes that exist in the routing table, CEF eliminates route cache maintenance, is more efficient for switching traffic, and is not affected by traffic patterns.
Nodes in the network are said to be adjacent if they can reach each other with a single hop across a link layer. CEF uses adjacency tables to prepend Layer 2 addressing information. The adjacency table maintains Layer 2 next-hop addresses for all FIB entries.
Because the switch or switch stack uses Application Specific Integrated Circuits (ASICs) to achieve Gigabit-speed line rate IP traffic, CEF or dCEF forwarding applies only to the software-forwarding path, that is, traffic that is forwarded by the CPU.
How to Configure Cisco Express Forwarding
CEF or distributed CEF is enabled globally by default. If for some reason it is disabled, you can re-enable it by using the ip cef or ip cef distributed global configuration command.
The default configuration is CEF or dCEF enabled on all Layer 3 interfaces. Entering the no ip route-cache cef interface configuration command disables CEF for traffic that is being forwarded by software. This command does not affect the hardware forwarding path. Disabling CEF and using the debug ip packet detail privileged EXEC command can be useful to debug software-forwarded traffic. To enable CEF on an interface for the software-forwarding path, use the ip route-cache cef interface configuration command.
 Caution | Although the no ip route-cache cef interface configuration command to disable CEF on an interface is visible in the CLI, we strongly recommend that you do not disable CEF or dCEF on interfaces except for debugging purposes. |
To enable CEF or dCEF globally and on an interface for software-forwarded traffic if it has been disabled:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | ip cef
Example: Switch(config)# ip cef |
Enables CEF operation on a non-stacking switch. Go to Step 4. |
| Step 3 | ip cef distributed
Example: Switch(config)# ip cef distributed |
Enables CEF operation on a active switch. |
| Step 4 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1 |
Enters interface configuration mode, and specifies the Layer 3 interface to configure. |
| Step 5 | ip route-cache cef
Example: Switch(config-if)# ip route-cache cef |
Enables CEF on the interface for software-forwarded traffic. |
| Step 6 | end
Example: Switch(config-if)# end |
Returns to privileged EXEC mode. |
| Step 7 | show ip cef
Example: Switch# show ip cef |
Displays the CEF status on all interfaces. |
| Step 8 | show cef linecard [detail]
Example: Switch# show cef linecard detail |
(Optional) Displays CEF-related interface information on a non-stacking switch. |
| Step 9 | show cef linecard
[slot-number] [detail]
Example: Switch# show cef linecard 5 detail |
(Optional) Displays CEF-related interface information on a switch by stack member for all switches in the stack or for the specified switch. (Optional) For slot-number, enter the stack member switch number. |
| Step 10 | show cef interface
[interface-id]
Example: Switch# show cef interface gigabitethernet 1/0/1 |
Displays detailed CEF information for all interfaces or the specified interface. |
| Step 11 | show
adjacency
Example: Switch# show adjacency |
Displays CEF adjacency table information. |
| Step 12 | copy running-config
startup-config
Example: Switch# copy running-config startup-config |
(Optional) Saves your entries in the configuration file. |
Number of Equal-Cost Routing Paths
Information About Equal-Cost Routing Paths
When a router has two or more routes to the same network with the same metrics, these routes can be thought of as having an equal cost. The term parallel path is another way to see occurrences of equal-cost routes in a routing table. If a router has two or more equal-cost paths to a network, it can use them concurrently. Parallel paths provide redundancy in case of a circuit failure and also enable a router to load balance packets over the available paths for more efficient use of available bandwidth. Equal-cost routes are supported across switches in a stack.
Even though the router automatically learns about and configures equal-cost routes, you can control the maximum number of parallel paths supported by an IP routing protocol in its routing table. Although the switch software allows a maximum of 32 equal-cost routes, the switch hardware will never use more than 16 paths per route.
How to Configure Equal-Cost Routing Paths
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure terminal
Example: Switch# configure terminal | |
| Step 2 | router {rip | ospf
| eigrp}
Example: Switch(config)# router eigrp 10 | |
| Step 3 | maximum-paths
maximum
Example: Switch(config-router)# maximum-paths 2 |
Sets the maximum number of parallel paths for the protocol routing table. The range is from 1 to 16; the default is 4 for most IP routing protocols. |
| Step 4 | end
Example: Switch(config-router)# end | |
| Step 5 | show ip protocols
Example: Switch# show ip protocols | |
| Step 6 | copy running-config
startup-config
Example: Switch# copy running-config startup-config |
Static Unicast Routes
Information About Static Unicast Routes
Static unicast routes are user-defined routes that cause packets moving between a source and a destination to take a specified path. Static routes can be important if the router cannot build a route to a particular destination and are useful for specifying a gateway of last resort to which all unroutable packets are sent.
The switch retains static routes until you remove them. However, you can override static routes with dynamic routing information by assigning administrative distance values. Each dynamic routing protocol has a default administrative distance, as listed in Table 41-16. If you want a static route to be overridden by information from a dynamic routing protocol, set the administrative distance of the static route higher than that of the dynamic protocol.
Static routes that point to an interface are advertised through RIP, IGRP, and other dynamic routing protocols, whether or not static redistribute router configuration commands were specified for those routing protocols. These static routes are advertised because static routes that point to an interface are considered in the routing table to be connected and hence lose their static nature. However, if you define a static route to an interface that is not one of the networks defined in a network command, no dynamic routing protocols advertise the route unless a redistribute static command is specified for these protocols.
When an interface goes down, all static routes through that interface are removed from the IP routing table. When the software can no longer find a valid next hop for the address specified as the forwarding router's address in a static route, the static route is also removed from the IP routing table.
Configuring Static Unicast Routes
Static unicast routes are user-defined routes that cause packets moving between a source and a destination to take a specified path. Static routes can be important if the router cannot build a route to a particular destination and are useful for specifying a gateway of last resort to which all unroutable packets are sent.
Follow these steps to configure a static route:
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip route
prefix mask {address |
interface} [distance]
Example: Switch(config)# ip route prefix mask gigabitethernet 1/0/4 | |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show ip
route
Example: Switch# show ip route |
Displays the current state of the routing table to verify the configuration. |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Use the no ip route prefix mask {address| interface} global configuration command to remove a static route. The switch retains static routes until you remove them.
Default Routes and Networks
Information About Default Routes and Networks
A router might not be able to learn the routes to all other networks. To provide complete routing capability, you can use some routers as smart routers and give the remaining routers default routes to the smart router. (Smart routers have routing table information for the entire internetwork.) These default routes can be dynamically learned or can be configured in the individual routers. Most dynamic interior routing protocols include a mechanism for causing a smart router to generate dynamic default information that is then forwarded to other routers.
If a router has a directly connected interface to the specified default network, the dynamic routing protocols running on that device generate a default route. In RIP, it advertises the pseudonetwork 0.0.0.0.
A router that is generating the default for a network also might need a default of its own. One way a router can generate its own default is to specify a static route to the network 0.0.0.0 through the appropriate device.
When default information is passed through a dynamic routing protocol, no further configuration is required. The system periodically scans its routing table to choose the optimal default network as its default route. In IGRP networks, there might be several candidate networks for the system default. Cisco routers use administrative distance and metric information to set the default route or the gateway of last resort.
If dynamic default information is not being passed to the system, candidates for the default route are specified with the ip default-network global configuration command. If this network appears in the routing table from any source, it is flagged as a possible choice for the default route. If the router has no interface on the default network, but does have a path to it, the network is considered as a possible candidate, and the gateway to the best default path becomes the gateway of last resort.
How to Configure Default Routes and Networks
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | ip
default-network
network number
Example: Switch(config)# ip default-network 1 | |
| Step 3 | end
Example: Switch(config)# end | |
| Step 4 | show ip
route
Example: Switch# show ip route |
Displays the selected default route in the gateway of last resort display. |
| Step 5 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Route Maps to Redistribute Routing Information
Information About Route Maps
The switch can run multiple routing protocols simultaneously, and it can redistribute information from one routing protocol to another. Redistributing information from one routing protocol to another applies to all supported IP-based routing protocols.
You can also conditionally control the redistribution of routes between routing domains by defining enhanced packet filters or route maps between the two domains. The match and set route-map configuration commands define the condition portion of a route map. The match command specifies that a criterion must be matched. The set command specifies an action to be taken if the routing update meets the conditions defined by the match command. Although redistribution is a protocol-independent feature, some of the match and set route-map configuration commands are specific to a particular protocol.
One or more match commands and one or more set commands follow a route-map command. If there are no match commands, everything matches. If there are no set commands, nothing is done, other than the match. Therefore, you need at least one match or set command.
 Note | A route map with no set route-map configuration commands is sent to the CPU, which causes high CPU utilization. |
You can also identify route-map statements as permit or deny. If the statement is marked as a deny, the packets meeting the match criteria are sent back through the normal forwarding channels (destination-based routing). If the statement is marked as permit, set clauses are applied to packets meeting the match criteria. Packets that do not meet the match criteria are forwarded through the normal routing channel.
How to Configure a Route Map
Although each of Steps 3 through 14 in the following section is optional, you must enter at least one match route-map configuration command and one set route-map configuration command.
 Note | The keywords are the same as defined in the procedure to control the route distribution. |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure terminal
Example: Switch# configure terminal | |
| Step 2 | route-map map-tag [permit |
deny] [sequence
number]
Example: Switch(config)# route-map rip-to-ospf permit 4 |
Defines any route maps used to control redistribution and enter route-map configuration mode. map-tag—A meaningful name for the route map. The redistribute router configuration command uses this name to reference this route map. Multiple route maps might share the same map tag name. (Optional) If permit is specified and the match criteria are met for this route map, the route is redistributed as controlled by the set actions. If deny is specified, the route is not redistributed. sequence number (Optional)— Number that indicates the position a new route map is to have in the list of route maps already configured with the same name. |
| Step 3 | match metric metric-value
Example: Switch(config-route-map)# match metric 2000 |
Matches the specified route metric. The metric-value can be an EIGRP metric with a specified value from 0 to 4294967295. |
| Step 4 | match ip next-hop
{access-list-number |
access-list-name}
[...access-list-number | ...access-list-name]
Example: Switch(config-route-map)# match ip next-hop 8 45 |
Matches a next-hop router address passed by one of the access lists specified (numbered from 1 to 199). |
| Step 5 | match tag tag value [...tag-value]
Example: Switch(config-route-map)# match tag 3500 |
Matches the specified tag value in a list of one or more route tag values. Each can be an integer from 0 to 4294967295. |
| Step 6 | match
interface type number [...type number]
Example: Switch(config-route-map)# match interface gigabitethernet 1/0/1 |
Matches the specified next hop route out one of the specified interfaces. |
| Step 7 | match ip route-source
{access-list-number |
access-list-name}
[...access-list-number
| ...access-list-name]
Example: Switch(config-route-map)# match ip route-source 10 30 |
Matches the address specified by the specified advertised access lists. |
| Step 8 | match route-type
{local |
internal |
external [type-1 |
type-2]}
Example: Switch(config-route-map)# match route-type local | |
| Step 9 | set metric
metric value
Example: Switch(config-route-map)# set metric 100 |
Sets the metric value to give the redistributed routes (for EIGRP only). The metric value is an integer from -294967295 to 294967295. |
| Step 10 | set metric
bandwidth delay reliability loading mtu
Example: Switch(config-route-map)# set metric 10000 10 255 1 1500 |
Sets the metric value to give the redistributed routes (for EIGRP only):
|
| Step 11 | set metric-type {type-1 |
type-2}
Example: Switch(config-route-map)# set metric-type type-2 |
Sets the OSPF external metric type for redistributed routes. |
| Step 12 | end
Example: Switch(config-route-map)# end | |
| Step 13 | show
route-map
Example: Switch# show route-map |
Displays all route maps configured or only the one specified to verify configuration. |
| Step 14 | copy running-config
startup-config
Example: Switch# copy running-config startup-config |
How to Control Route Distribution
Although each of Steps 3 through 14 in the following section is optional, you must enter at least one match route-map configuration command and one set route-map configuration command.
 Note | The keywords are the same as defined in the procedure to configure the route map for redistritbution. |
The metrics of one routing protocol do not necessarily translate into the metrics of another. For example, the RIP metric is a hop count, and the IGRP metric is a combination of five qualities. In these situations, an artificial metric is assigned to the redistributed route. Uncontrolled exchanging of routing information between different routing protocols can create routing loops and seriously degrade network operation.
If you have not defined a default redistribution metric that replaces metric conversion, some automatic metric translations occur between routing protocols:
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router {
rip |
ospf |
eigrp}
Example: Switch(config)# router eigrp 10 | |
| Step 3 | redistribute
protocol [process-id] {level-1 |
level-1-2 |
level-2} [metric
metric-value] [metric-type
type-value] [match internal |
external
type-value] [tag
tag-value] [route-map
map-tag] [weight
weight] [subnets]
Example: Switch(config-router)# redistribute eigrp 1 |
Redistributes routes from one routing protocol to another routing protocol. If no route-maps are specified, all routes are redistributed. If the keyword route-map is specified with no map-tag, no routes are distributed. |
| Step 4 | default-metric
number
Example: Switch(config-router)# default-metric 1024 |
Cause the current routing protocol to use the same metric value for all redistributed routes ( RIP and OSPF). |
| Step 5 | default-metric bandwidth delay reliability loading
mtu
Example: Switch(config-router)# default-metric 1000 100 250 100 1500 |
Cause the EIGRP routing protocol to use the same metric value for all non-EIGRP redistributed routes. |
| Step 6 | end
Example: Switch(config-router)# end | |
| Step 7 | show
route-map
Example: Switch# show route-map |
Displays all route maps configured or only the one specified to verify configuration. |
| Step 8 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Policy-Based Routing
Information About Policy-Based Routing
You can use policy-based routing (PBR) to configure a defined policy for traffic flows. By using PBR, you can have more control over routing by reducing the reliance on routes derived from routing protocols. PBR can specify and implement routing policies that allow or deny paths based on:
You can use PBR to provide equal-access and source-sensitive routing, routing based on interactive versus batch traffic, or routing based on dedicated links. For example, you could transfer stock records to a corporate office on a high-bandwidth, high-cost link for a short time while transmitting routine application data such as e-mail over a low-bandwidth, low-cost link.
With PBR, you classify traffic using access control lists (ACLs) and then make traffic go through a different path. PBR is applied to incoming packets. All packets received on an interface with PBR enabled are passed through route maps. Based on the criteria defined in the route maps, packets are forwarded (routed) to the appropriate next hop.
- Route map statement marked as
permit is processed as follows:
- A match command can match on
length or multiple ACLs. A route map statement can contain multiple match
commands. Logical or algorithm function is performed across all the match
commands to reach a permit or deny decision.
For example:
match length A B
match ip address acl1 acl2
match ip address acl3
A packet is permitted if it is permitted by match length A B or acl1 or acl2 or acl3
- If the decision reached is permit, then the action specified by the set command is applied on the packet .
- If the decision reached is deny, then the PBR action (specified in the set command) is not applied. Instead the processing logic moves forward to look at the next route-map statement in the sequence (the statement with the next higher sequence number). If no next statement exists, PBR processing terminates, and the packet is routed using the default IP routing table.
- A match command can match on
length or multiple ACLs. A route map statement can contain multiple match
commands. Logical or algorithm function is performed across all the match
commands to reach a permit or deny decision.
- For PBR, route-map statements marked as deny are not supported.
You can use standard IP ACLs to specify match criteria for a source address or extended IP ACLs to specify match criteria based on an application, a protocol type, or an end station. The process proceeds through the route map until a match is found. If no match is found, normal destination-based routing occurs. There is an implicit deny at the end of the list of match statements.
If match clauses are satisfied, you can use a set clause to specify the IP addresses identifying the next hop router in the path.
For details about PBR commands and keywords, see the Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols .
How to Configure PBR
-
To use PBR, you must have the IP Lite feature set enabled on the switch or stack master.
-
Multicast traffic is not policy-routed. PBR applies to only to unicast traffic.
-
You can apply a policy route map to an EtherChannel port channel in Layer 3 mode, but you cannot apply a policy route map to a physical interface that is a member of the EtherChannel. If you try to do so, the command is rejected. When a policy route map is applied to a physical interface, that interface cannot become a member of an EtherChannel.
-
You can define a maximum of 128 IP policy route maps on the switch or switch stack.
-
You can define a maximum of 512 access control entries (ACEs) for PBR on the switch or switch stack.
-
When configuring match criteria in a route map, follow these guidelines:
-
VRF and PBR are mutually exclusive on a switch interface. You cannot enable VRF when PBR is enabled on an interface. The reverse is also true, you cannot enable PBR when VRF is enabled on an interface.
-
The number of hardware entries used by PBR depends on the route map itself, the ACLs used, and the order of the ACLs and route-map entries.
-
PBR based on TOS, DSCP and IP Precedence are not supported.
-
Set interface, set default next-hop and set default interface are not supported.
-
Policy-maps with no set actions are supported. Matching packets are routed normally.
-
Policy-maps with no match clauses are supported. Set actions are applied to all packets.
By default, PBR is disabled on the switch. To enable PBR, you must create a route map that specifies the match criteria and the resulting action. Then, you must enable PBR for that route map on an interface. All packets arriving on the specified interface matching the match clauses are subject to PBR.
Packets that are generated by the switch, or local packets, are not normally policy-routed. When you globally enable local PBR on the switch, all packets that originate on the switch are subject to local PBR. Local PBR is disabled by default.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
configure terminal
Example: Switch# configure terminal
|
Enters global configuration mode. |
| Step 2 | route-mapmap-tag [permit] [sequence number]
Example: Switch(config)# route-map pbr-map permit | Define any route maps used to control where packets are
output, and enter route-map configuration mode.
|
| Step 3 | match ip address
{access-list-number |
access-list-name}
[access-list-number |...access-list-name]
Example: Switch(config-route-map)# match ip address 110 140
|
Match the source and destination IP address that is permitted by one or more standard or extended access lists. ACLs can match on more than source and destination IP addresses. If you do not specify a match command, the route map applies to all packets. |
| Step 4 |
match
length min max
Example: Switch(config-route-map)# match length 64 1500
|
Matches against the length of the packet. |
| Step 5 | set ip next-hop
ip-address
[...ip-address]
Example: Switch(config-route-map)# set ip next-hop 10.1.6.2
| Specifies the action to take on the packets that match the criteria. Sets next hop to which to route the packet (the next hop must be adjacent). |
| Step 6 | exit
Example: Switch(config-route-map)# exit
|
Returns to global configuration mode. |
| Step 7 | interface
interface-id
Example: Switch(config)# interface gigabitethernet 1/0/1
| Enters interface configuration mode, and specifies the interface to configure. |
| Step 8 | ip policy route-map
map-tag
Example: Switch(config-if)# ip policy route-map pbr-map
|
Enables PBR on a Layer 3 interface, and identify the route map to use. You can configure only one route map on an interface. However, you can have multiple route map entries with different sequence numbers. These entries are evaluated in sequence number order until the first match. If there is no match, packets are routed as usual. |
| Step 9 | ip route-cache
policy
Example: Switch(config-if)# ip route-cache policy
| (Optional) Enables fast-switching PBR. You must first enable PBR before enabling fast-switching PBR. |
| Step 10 | exit
Example: Switch(config-if)# exit
| Returns to global configuration mode. |
| Step 11 | ip local policy route-map
map-tag
Example: Switch(config)# ip local policy route-map local-pbr
|
(Optional) Enables local PBR to perform policy-based routing on packets originating at the switch. This applies to packets generated by the switch and not to incoming packets. |
| Step 12 | end
Example: Switch(config)# end
|
Returns to privileged EXEC mode. |
| Step 13 | show route-map [map-name]
Example: Switch# show route-map
|
(Optional) Displays all route maps configured or only the one specified to verify configuration. |
| Step 14 | show ip
policy
Example: Switch# show ip policy
|
(Optional) Displays policy route maps attached to interface |
| Step 15 | show ip local
policy
Example: Switch# show ip local policy
|
(Optional) Displays whether or not local policy routing is enabled and, if so, the route map being used. |
Filtering Routing Information
You can filter routing protocol information by performing the tasks described in this section.
 Note | When routes are redistributed between OSPF processes, no OSPF metrics are preserved. |
- Setting Passive Interfaces
- Controlling Advertising and Processing in Routing Updates
- Filtering Sources of Routing Information
Setting Passive Interfaces
To prevent other routers on a local network from dynamically learning about routes, you can use the passive-interface router configuration command to keep routing update messages from being sent through a router interface. When you use this command in the OSPF protocol, the interface address you specify as passive appears as a stub network in the OSPF domain. OSPF routing information is neither sent nor received through the specified router interface.
In networks with many interfaces, to avoid having to manually set them as passive, you can set all interfaces to be passive by default by using the passive-interface default router configuration command and manually setting interfaces where adjacencies are desired.
Use a network monitoring privileged EXEC command such as show ip ospf interface to verify the interfaces that you enabled as passive, or use the show ip interface privileged EXEC command to verify the interfaces that you enabled as active.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router {
rip |
ospf |
eigrp}
Example: Switch(config)# router ospf | |
| Step 3 | passive-interface
interface-id
Example: Switch(config-router)# passive-interface gigabitethernet 1/0/1 |
Suppresses sending routing updates through the specified Layer 3 interface. |
| Step 4 | passive-interface
default
Example: Switch(config-router)# passive-interface default | |
| Step 5 | no
passive-interface
interface type
Example: Switch(config-router)# no passive-interface gigabitethernet1/0/3 gigabitethernet 1/0/5 |
(Optional) Activates only those interfaces that need to have adjacencies sent. |
| Step 6 | network
network-address
Example: Switch(config-router)# network 10.1.1.1 |
(Optional) Specifies the list of networks for the routing process. The network-address is an IP address. |
| Step 7 | end
Example: Switch(config-router)# end | |
| Step 8 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Controlling Advertising and Processing in Routing Updates
You can use the distribute-list router configuration command with access control lists to suppress routes from being advertised in routing updates and to prevent other routers from learning one or more routes. When used in OSPF, this feature applies to only external routes, and you cannot specify an interface name.
You can also use a distribute-list router configuration command to avoid processing certain routes listed in incoming updates. (This feature does not apply to OSPF.)
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router {
rip |
eigrp}
Example: Switch(config)# router eigrp 10 | |
| Step 3 | distribute-list {access-list-number |
access-list-name}
out [interface-name |
routing process |
autonomous-system-number]
Example: Switch(config-router)# distribute 120 out gigabitethernet 1/0/7 |
Permits or denies routes from being advertised in routing updates, depending upon the action listed in the access list. |
| Step 4 | distribute-list {access-list-number |
access-list-name}
in [type-number]
Example: Switch(config-router)# distribute-list 125 in | |
| Step 5 | end
Example: Switch(config-router)# end | |
| Step 6 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Filtering Sources of Routing Information
Because some routing information might be more accurate than others, you can use filtering to prioritize information coming from different sources. An administrative distance is a rating of the trustworthiness of a routing information source, such as a router or group of routers. In a large network, some routing protocols can be more reliable than others. By specifying administrative distance values, you enable the router to intelligently discriminate between sources of routing information. The router always picks the route whose routing protocol has the lowest administrative distance.
Because each network has its own requirements, there are no general guidelines for assigning administrative distances.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | router {
rip |
ospf |
eigrp}
Example: Switch(config)# router eigrp 10 | |
| Step 3 | distance
weight
{ip-address {ip-address mask}}
[ip access list]
Example: Switch(config-router)# distance 50 10.1.5.1 |
Defines an administrative distance. weight—The administrative distance as an integer from 10 to 255. Used alone, weight specifies a default administrative distance that is used when no other specification exists for a routing information source. Routes with a distance of 255 are not installed in the routing table. (Optional) ip access list—An IP standard or extended access list to be applied to incoming routing updates. |
| Step 4 | end
Example: Switch(config-router)# end | |
| Step 5 | show ip
protocols
Example: Switch# show ip protocols |
Displays the default administrative distance for a specified routing process. |
| Step 6 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Managing Authentication Keys
Key management is a method of controlling authentication keys used by routing protocols. Not all protocols can use key management. Authentication keys are available for EIGRP and RIP Version 2.
Prerequisites
Before you manage authentication keys, you must enable authentication. See the appropriate protocol section to see how to enable authentication for that protocol. To manage authentication keys, define a key chain, identify the keys that belong to the key chain, and specify how long each key is valid. Each key has its own key identifier (specified with the key number key chain configuration command), which is stored locally. The combination of the key identifier and the interface associated with the message uniquely identifies the authentication algorithm and Message Digest 5 (MD5) authentication key in use.
How to Configure Authentication Keys
You can configure multiple keys with life times. Only one authentication packet is sent, regardless of how many valid keys exist. The software examines the key numbers in order from lowest to highest, and uses the first valid key it encounters. The lifetimes allow for overlap during key changes. Note that the router must know these lifetimes.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | key chain
name-of-chain
Example: Switch(config)# key chain key10 |
Identifies a key chain, and enter key chain configuration mode. |
| Step 3 | key
number
Example: Switch(config-keychain)# key 2000 | |
| Step 4 | key-string
text
Example: Switch(config-keychain)# Room 20, 10th floor |
Identifies the key string. The string can contain from 1 to 80 uppercase and lowercase alphanumeric characters, but the first character cannot be a number. |
| Step 5 | accept-lifetime
start-time {infinite |
end-time |
duration
seconds}
Example: Switch(config-keychain)# accept-lifetime 12:30:00 Jan 25 1009 infinite |
(Optional) Specifies the time period during which the key can be received. The start-time and end-time syntax can be either hh:mm:ss Month date year or hh:mm:ss date Month year. The default is forever with the default start-time and the earliest acceptable date as January 1, 1993. The default end-time and duration is infinite. |
| Step 6 | send-lifetime
start-time {infinite |
end-time |
duration
seconds}
Example: Switch(config-keychain)# accept-lifetime 23:30:00 Jan 25 1019 infinite |
(Optional) Specifies the time period during which the key can be sent. The start-time and end-time syntax can be either hh:mm:ss Month date year or hh:mm:ss date Month year. The default is forever with the default start-time and the earliest acceptable date as January 1, 1993. The default end-time and duration is infinite. |
| Step 7 | end
Example: Switch(config-keychain)# end | |
| Step 8 | show key
chain
Example: Switch# show key chain | |
| Step 9 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Monitoring and Maintaining the IP Network
You can remove all contents of a particular cache, table, or database. You can also display specific statistics.
|
Displays the parameters and state of the active routing protocol process. |
|
|
show ip route [address [mask] [longer-prefixes]] | [protocol [process-id]] |
|
|
Displays the current state of the routing table in summary form. |
|
|
Displays all route maps configured or only the one specified. |
 Feedback
Feedback