Network Time Protocol
Network Time Protocol (NTP) is a networking protocol that synchronizes the clocks of devices in a network to Coordinated Universal Time (UTC). It plays a crucial role in ensuring that systems maintain accurate and synchronized time, which is essential for various applications such as time-stamping, logging, and network coordination.
NTP operates on UDP port 123 for accurate time synchronization, and even greater precision within a local area network (LAN). It uses a hierarchical stratum system to distribute time synchronization across devices.
A stratum refers to the level of hierarchy in the time synchronization process, indicating a device's distance from the primary reference clock (Stratum 0):
-
Stratum 0 : These are highly accurate reference clocks, such as atomic clocks, GPS clocks, or radio clocks. They are not network devices themselves but provide the most precise time source.
-
Stratum 1 : These are servers directly connected to a Stratum 0 reference clock. They act as the primary time sources for other devices in the network.
-
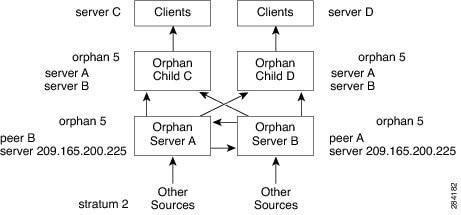
Stratum 2 and beyond : These devices synchronize their clocks with a Stratum 1 server (or higher stratum server) over the network. As the stratum level increases, the device is further away from the reference clock, and the potential for reduced accuracy and increased latency grows.
-
Stratum 15 : The lowest level in the NTP hierarchy, indicating the furthest distance from the reference clock. Devices beyond Stratum 15 are considered unsynchronized.
The stratum system ensures a scalable and distributed approach to time synchronization, preventing overloading of primary time sources and maintaining a clear hierarchy.

 Feedback
Feedback