Overview of LDAP Queries
If you store user information within LDAP directories in your network infrastructure — for example, in Microsoft Active Directory, SunONE Directory Server, or OpenLDAP directories — you can configure the email gateway to query your LDAP servers to accept, route, and authenticate messages. You can configure the email gateway to work with one or multiple LDAP servers.
The following section provides an overview on the types of LDAP queries you can perform; how LDAP works with the email gateway to authenticate, accept, and route messages; and how to configure your email gateway to work with LDAP.
Related Topics
- Understanding LDAP Queries
- Understanding How LDAP Works with AsyncOS
- Configuring the Email Gateway to Work with an LDAP Server
- Creating LDAP Server Profiles to Store Information About the LDAP Server
- Testing LDAP Servers
- Enabling LDAP Queries to Run on a Particular Listener
- Enhanced Support for Microsoft Exchange 5.5
Understanding LDAP Queries
If you store user information within LDAP directories in your network infrastructure, you can configure the email gateway to query your LDAP server for the following purposes:
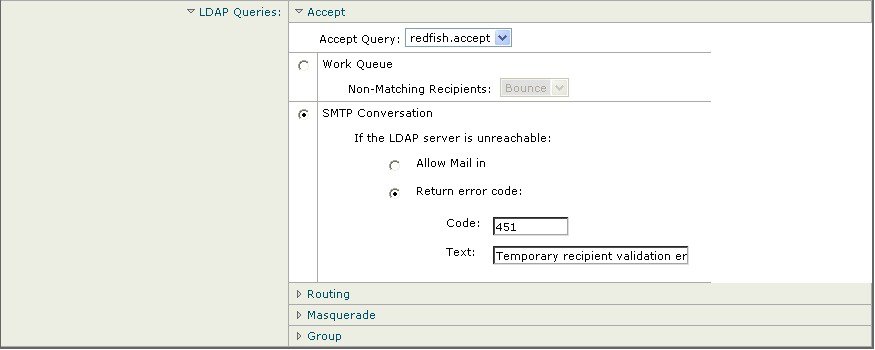
- Acceptance Queries. You can use your existing LDAP infrastructure to define how the recipient email address of incoming messages (on a public listener) should be handled. For more information, see Using Acceptance Queries For Recipient Validation.
- Routing (Aliasing). You can configure the email gateway to route messages to the appropriate address and/or mail host based upon the information available in LDAP directories on your network. For more information, see Using Routing Queries to Send Mail to Multiple Target Addresses.
- Certificate Authentication. You can create a query that checks the validity of a client certificate in order to authenticate an SMTP session between the user’s mail client and the email gateway. For more information, see Checking the Validity of a Client Certificate.
- Masquerading. You can masquerade Envelope Senders (for outgoing mail) and message headers (for incoming mail, such as To:, Reply To:, From: or CC:). For more information about masquerading, see Using Masquerading Queries to Rewrite the Envelope Sender.
- Group Queries. You can configure the email gateway to perform actions on messages based on the groups in the LDAP directory. You do this by associating a group query with a message filter. You can perform any message action available for message filters on messages that match the defined LDAP group. For more information, see Using Group LDAP Queries to Determine if a Recipient is a Group Member.
- Domain-based Queries. You can create domain-based queries to allow the email gateway to perform different queries for different domains on a single listener. When the email gateway runs the domain-based queries, it determines the query to use based on the domain, and it queries the LDAP server associated with that domain.
- Chain Queries. You can create a chain query to enable the email gateway to perform a series of queries in sequence. When you configure a chain query, the email gateway runs each query in sequence until the LDAP appliance returns a positive result. For chained routing queries, the email gateway re-runs the same configured chain query in sequence for each rewritten email address.
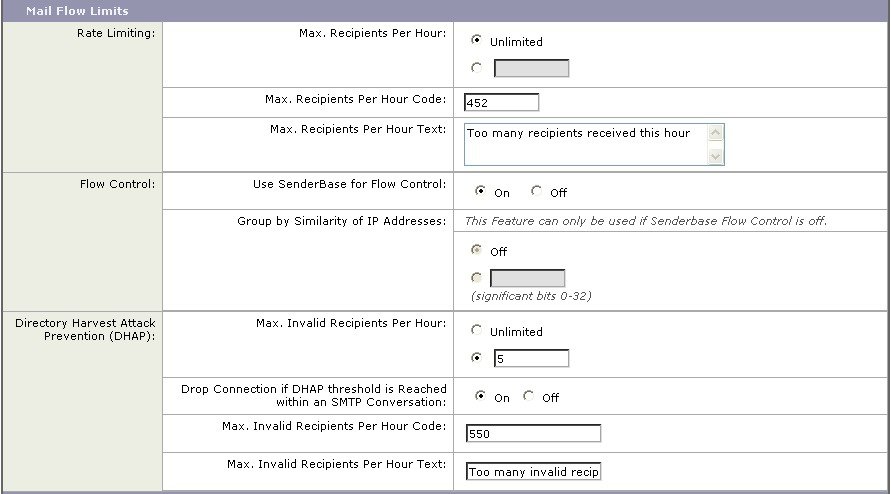
- Directory Harvest Prevention. You can configure the email gateway to combat directory harvest attacks using your LDAP directories. You can configure directory harvest prevention during the SMTP conversation or within the work queue. If the recipient is not found in the LDAP directory, you can configure the system to perform a delayed bounce or drop the message entirely. Consequently, spammers are not able to differentiate between valid and invalid email addresses. See Using LDAP For Directory Harvest Attack Prevention.
- SMTP Authentication. AsyncOS provides support for SMTP authentication. SMTP Auth is a mechanism for authenticating clients connected to an SMTP server. You can use this functionality to enable users at your organization to send mail using your mail servers even if they are connecting remotely (e.g. from home or while traveling). For more information, see Configuring AsyncOS for SMTP Authentication.
- External Authentication. You can configure your email gateway to use your LDAP directory to authenticate users logging in to the email gateway. For more information, see Configuring External LDAP Authentication for Users.
- Spam Quarantine End-User Authentication. You can configure your email gateway to validate users when they log in to the end-user quarantine. For more information, see Authenticating End-Users of the Spam Quarantine.
- Spam Quarantine Alias Consolidation. If you use email notifications for spam, this query consolidates the end-user aliases so that end-users do not receive quarantine notices for each aliased email address. For more information, see Spam Quarantine Alias Consolidation Queries.
Understanding How LDAP Works with AsyncOS
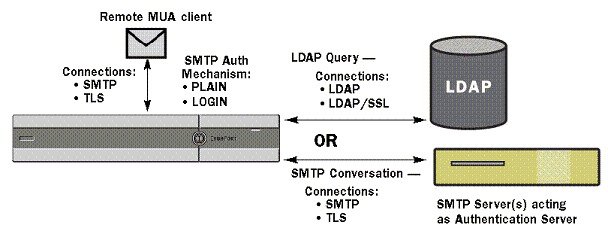
When you work with LDAP directories, the email gateway can be used in conjunction with an LDAP directory server to accept recipients, route messages, and/or masquerade headers. LDAP group queries can also be used in conjunction with message filters to create rules for handling messages as they are received by the email gateway.
The following figure demonstrates how the email gateway works with LDAP:
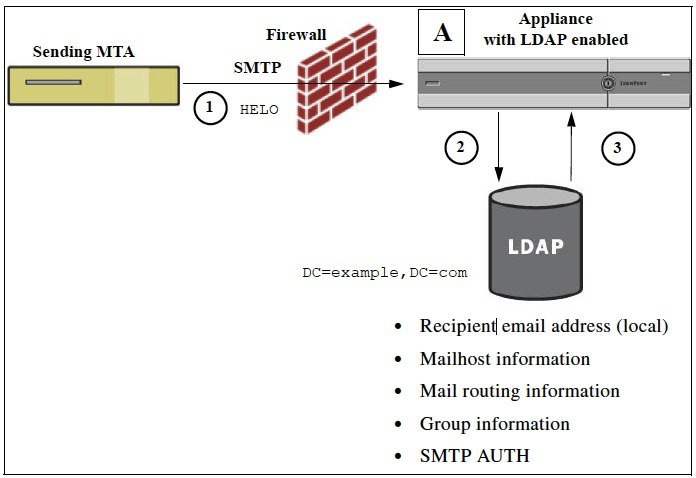
- The sending MTA sends a message to the public listener “A” via SMTP.
- The email gateway queries the LDAP server defined via the System Administration > LDAP page (or by the global ldapconfig command).
- Data is received from the
LDAP directory, and, depending on the queries defined on the
System
Administration > LDAP page (or in the
ldapconfig command) that are used by the listener:
- the message is routed to the new recipient address, or dropped or bounced
- the message is routed to the appropriate mailhost for the new recipient
- From:, To:, and CC: message headers are re-written based upon the query
- further actions as defined by rcpt-to-group or mail-from-group message filter rules (used in conjunction with configured group queries).
 Note |
You can configure your email gateway to connect to multiple LDAP servers. When you do this, you can configure the LDAP profile settings for load-balancing or failover. For more information about working with multiple LDAP servers, see Configuring AsyncOS To Work With Multiple LDAP Servers. |
Configuring the Email Gateway to Work with an LDAP Server
When you configure your email gateway to work with an LDAP directory, you must complete the following steps to configure your AsyncOS email gateway for acceptance, routing, aliasing, and masquerading:
Procedure
| Step 1 |
Configure LDAP server profiles. The server profile contains information to enable AsyncOS to connect to the LDAP server (or servers), such as:
For more information about configuring a server profile, see Creating LDAP Server Profiles to Store Information About the LDAP Server. When you configure the LDAP server profile, you can configure AsyncOS to connect to one or multiple LDAP servers. For information about configuring AsyncOS to connect to multiple servers, see Configuring AsyncOS To Work With Multiple LDAP Servers. |
||
| Step 2 |
Configure the LDAP query. You configure the LDAP queries on the LDAP server profile. The query you configure should be tailored to your particular LDAP implementation and schema. For information on the types of LDAP queries you can create, see Understanding LDAP Queries. For information on writing queries, see Working with LDAP Queries. |
||
| Step 3 |
Enable the LDAP server profile on a public listener or on a private listener. You must enable the LDAP server profile on a listener to instruct the listener to run the LDAP query when accepting, routing, or sending a message. For more information, see Enabling LDAP Queries to Run on a Particular Listener.
|
Creating LDAP Server Profiles to Store Information About the LDAP Server
When you configure AsyncOS to use LDAP directories, you create an LDAP server profile to store the information about the LDAP server.
Procedure
| Step 1 |
On the System Administration > LDAP page, click Add LDAP Server Profile. |
||||
| Step 2 |
Enter a name for the server profile. |
||||
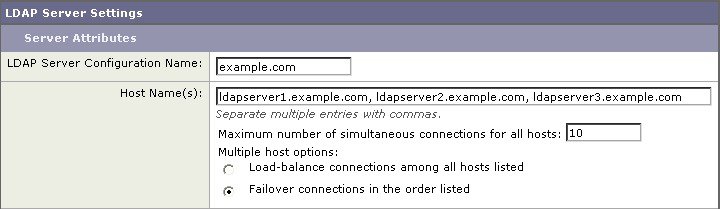
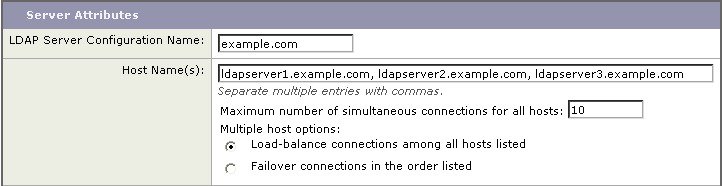
| Step 3 |
Enter the host name for the LDAP server. You can enter multiple host names to configure the LDAP servers for failover or load-balancing. Separate multiple entries with commas. For more information, see Configuring AsyncOS To Work With Multiple LDAP Servers. |
||||
| Step 4 |
Select an authentication method. You can use anonymous authentication or specify a username and passphrase. |
||||
| Step 5 |
Select the LDAP server type: Active Directory, OpenLDAP, or Unknown or Other. |
||||
| Step 6 |
Enter a port number. The default port is 3268 without SSL and 3269 with SSL for Active Directory or any Unknown / Other server types. The default port is 389 without SSL and 636 with SSL, for Open LDAP server types. |
||||
| Step 7 |
Enter a Base DN (distinguishing name) for the LDAP server. If you authenticate with a username and a passphrase, the username must include the full DN to the entry that contains the passphrase. For example, a user is a member of the marketing group with an email address of joe@example.com. The entry for this user would look like the following entry:
|
||||
| Step 8 |
Select whether to use SSL when communicating with the LDAP server.
|
||||
| Step 9 |
Under Advanced, enter cache time-to-live. This value represents the amount of time to retain caches. |
||||
| Step 10 |
Enter the maximum number of retained cache entries.
|
||||
| Step 11 |
Enter the number of simultaneous connections.
|
||||
| Step 12 |
Test the connection to the server by clicking the Test Server(s) button. If you specified multiple LDAP servers, they are all tested. The results of the test appear in the Connection Status field. For more information, see Testing LDAP Servers. |
||||
| Step 13 |
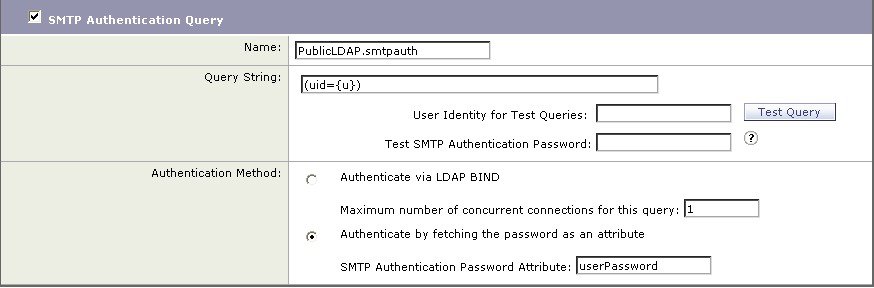
Create queries by marking the checkbox and completing the fields. You can select Accept, Routing, Masquerade, Group, SMTP Authentication, External Authentication, Spam Quarantine End-User Authentication, and Spam Quarantine Alias Consolidation.
|
||||
| Step 14 |
Test a query by clicking the Test Query button. Enter the test parameters and click Run Test. The results of the test appear in the Connection Status field. If you make any changes to the query definition or attributes, click Update. For more information, see Testing LDAP Servers.
|
||||
| Step 15 |
Submit and commit your changes.
|
Testing LDAP Servers
Use the Test Server(s) button on the Add/Edit LDAP Server Profile page (or the test subcommand of the ldapconfig command in the CLI) to test the connection to the LDAP server. AsyncOS displays a message stating whether the connection to the server port succeeded or failed. If you configured multiple LDAP servers, AsyncOS tests each server and displays individual results.
Enabling LDAP Queries to Run on a Particular Listener
To allow the email gateway to run LDAP queries when you receive or send messages, you must enable the LDAP query on the appropriate listener.
Related Topics
Configuring Global Settings for LDAP Queries
The LDAP global settings define how the email gateway handles all LDAP traffic.
Procedure
| Step 1 |
On the System Administration > LDAP page, click Edit Settings. |
| Step 2 |
Select the IP interface to use for LDAP traffic. The email gateway automatically chooses an interface by default. |
| Step 3 |
Select the TLS certificate to use for the LDAP interface (TLS certificates added via the Network > Certificates page or the certconfig command in the CLI are available in the list, see Overview of Encrypting Communication with Other MTAs). |
| Step 4 |
Select appropriate option, if you want to validate the LDAP server certificate. |
| Step 5 |
Submit and commit your changes. |
Example of Creating an LDAP Server Profile
In the following example, the System Administration > LDAP page is used to define an LDAP server for the email gateway to bind to, and queries for recipient acceptance, routing, and masquerading are configured.
 Note |
There is a 60 second connection attempt time-out for LDAP connections (which covers the DNS lookup, the connection itself, and, if applicable, the authentication bind for the email gateway itself). After the first failure, AsyncOS immediately starts trying other hosts in the same server (if you specified more than one in the comma separated list). If you only have one host in the server, AsyncOS continues attempting to connect to it. |
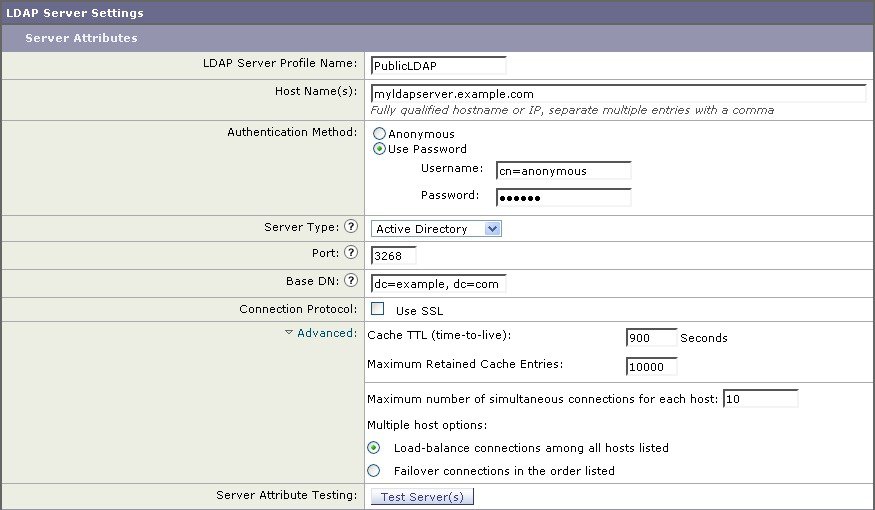
First, the nickname of “PublicLDAP” is given for the myldapserver.example.com LDAP server. The number of connections is set to 10 (the default), and the multiple LDAP server (hosts) load balance option is left as the default. You can specify multiple hosts here by providing a comma separated list of names. Queries are directed to port 3268 (the default). SSL is not enabled as the connection protocol for this host. The base DN of example.com is defined ( dc=example,dc=com ). The cache time-to-live is set to 900 seconds, the maximum number of cache entries is 10000, and the authentication method is set to passphrase.
Queries for recipient acceptance, mail routing, and masquerading are defined. Remember that query names are case-sensitive and must match exactly in order to return the proper results.

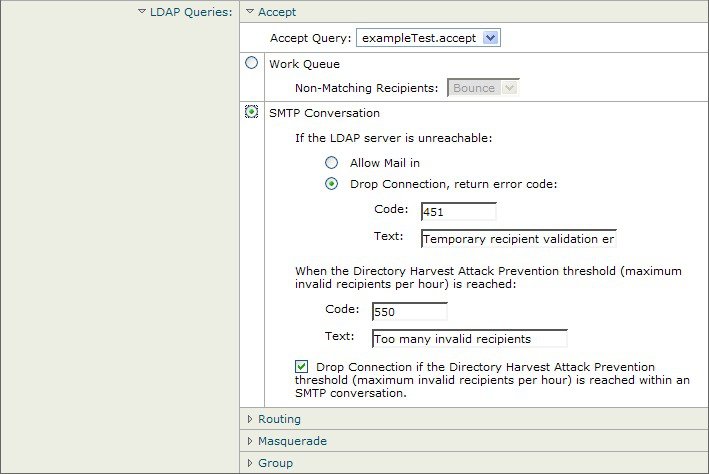
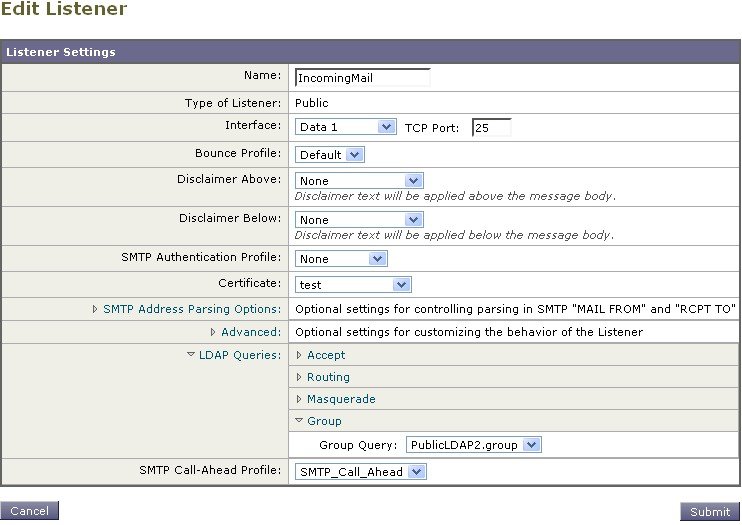
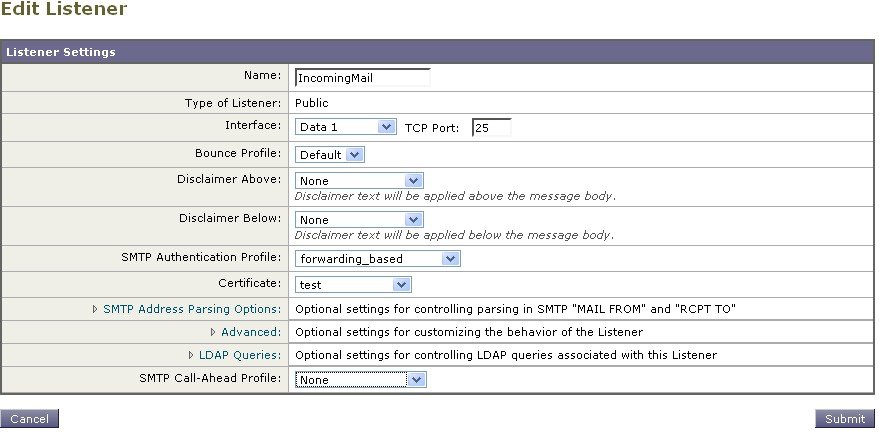
Enabling LDAP Queries on a Public Listener
In this example, the public listener “InboundMail” is updated to use LDAP queries for recipient acceptance. Further, recipient acceptance is configured to happen during the SMTP conversation (for more information, see Using Acceptance Queries For Recipient Validation for more information).
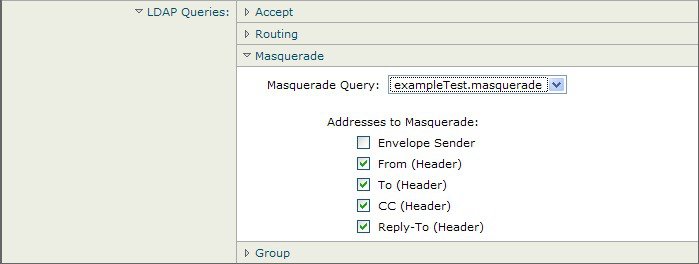
Enabling LDAP Queries on a Private Listener
In this example, the private listener “OutboundMail” is updated to use LDAP queries for masquerading. The masqueraded fields include: From, To, CC, and Reply-To.
Enhanced Support for Microsoft Exchange 5.5
AsyncOS includes a
configuration option to provide support for Microsoft Exchange 5.5. If you use
a later version of Microsoft Exchange, you do not need to enable this option.
When configuring an LDAP server, you can elect to enable Microsoft Exchange 5.5
support by answering “y” when prompted in the
ldapconfig -> edit -> server -> compatibility
subcommand (this is only available via the CLI):
mail3.example.com> ldapconfig
Current LDAP server configurations:
1. PublicLDAP: (ldapexample.com:389)
Choose the operation you want to perform:
- NEW - Create a new server configuration.
- EDIT - Modify a server configuration.
- DELETE - Remove a server configuration.
[]> edit
Enter the name or number of the server configuration you wish to edit.
[]> 1
Name: PublicLDAP
Hostname: ldapexample.com Port 389
Authentication Type: anonymous
Base: dc=ldapexample,dc=com
Choose the operation you want to perform:
- SERVER - Change the server for the query.
- LDAPACCEPT - Configure whether a recipient address should be accepted or
bounced/dropped.
- LDAPROUTING - Configure message routing.
- MASQUERADE - Configure domain masquerading.
- LDAPGROUP - Configure whether a sender or recipient is in a specified group.
- SMTPAUTH - Configure SMTP authentication.
[]> server
Name: PublicLDAP
Hostname: ldapexample.com Port 389
Authentication Type: anonymous
Base: dc=ldapexample,dc=com
Microsoft Exchange 5.5 Compatibility Mode: Disabled
Choose the operation you want to perform:
- NAME - Change the name of this configuration.
- HOSTNAME - Change the hostname used for this query.
- PORT - Configure the port.
- AUTHTYPE - Choose the authentication type.
- BASE - Configure the query base.
- COMPATIBILITY - Set LDAP protocol compatibility options.
[]> compatibility
Would you like to enable Microsoft Exchange 5.5 LDAP compatibility mode? (This is not
recommended for versions of Microsoft Exchange later than 5.5, or other LDAP servers.)
[N]> y
Do you want to configure advanced LDAP compatibility settings? (Typically not required)
[N]>
Name: PublicLDAP
Hostname: ldapexample.com Port 389
Authentication Type: anonymous
Base: dc=ldapexample,dc=com
Microsoft Exchange 5.5 Compatibility Mode: Enabled (attribute "objectClass")
Choose the operation you want to perform:
- NAME - Change the name of this configuration.
- HOSTNAME - Change the hostname used for this query.
- PORT - Configure the port.
- AUTHTYPE - Choose the authentication type.
- BASE - Configure the query base.
- COMPATIBILITY - Set LDAP protocol compatibility options.
[]>
 Feedback
Feedback