Overview of Encrypting Communication with Other MTAs
Enterprise Gateways (or Message Transfer Agents, i.e. MTAs) normally communicate “in the clear” over the Internet. That is, the communications are not encrypted. In several scenarios, malicious agents can intercept this communication without the knowledge of the sender or the receiver. Communications can be monitored and even altered by a third party.
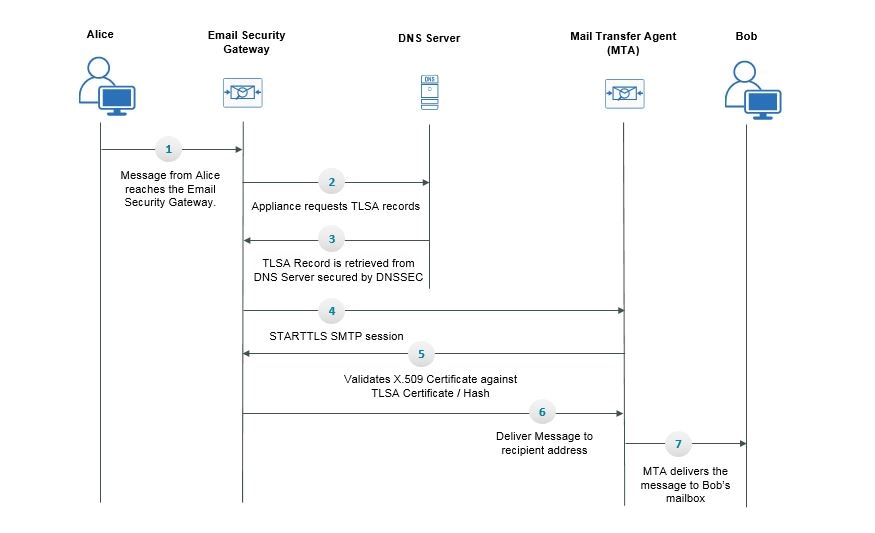
Transport Layer Security (TLS) is an improved version of the Secure Socket Layer (SSL) technology. It is a widely used mechanism for encrypting SMTP conversations over the Internet. AsyncOS supports the STARTTLS extension to SMTP (Secure SMTP over TLS), described in RFC 3207 (which obsoletes RFC 2487).
The TLS implementation in AsyncOS provides privacy through encryption. It allows you to import an X.509 certificate and private key from a certificate authority service or create a self-signed certificate to use on the email gateway. AsyncOS supports separate TLS certificates for public and private listeners, secure HTTP (HTTPS) management access on an interface, the LDAP interface, and all outgoing TLS connections.
Related Topics
How to Encrypt SMTP Conversations using TLS
How to Encrypt SMTP Conversations using TLS
|
Do This |
More Info |
|
|---|---|---|
|
Step 1 |
Obtain an X.509 certificate and private key from a recognized certificate authority. |
|
|
Step 2 |
Install the certificate on the email gateway |
Install a certificate by either: |
|
Step 3 |
Enable TLS for receiving messages, delivering messages, or both |
|
|
Step 4 |
(Optional) Customize the list of trusted certificate authorities that the appliance uses to verify a certificate from a remote domain to establish the domain’s credentials. |
|
|
Step 5 |
(Optional) Configure the email gateway to send an alert when it’s unable to deliver messages to a domain that requires a TLS connection. |


 Feedback
Feedback